PCNSE : Palo Alto Networks Certified Network Security Engineer : Part 03
-
Which Palo Alto Networks VM-Series firewall is valid?
- VM-25
- VM-800
- VM-50
- VM-400
Explanation:
Reference:
https://www.paloaltonetworks.com/products/secure-the-network/virtualized-next-generation-firewall/vm-series
-
An administrator wants multiple web servers in the DMZ to receive connections initiated from the internet. Traffic destined for 206.15.22.9 port 80/TCP needs to be forwarded to the server at 10.1.1.22
Based on the information shown in the image, which NAT rule will forward web-browsing traffic correctly?
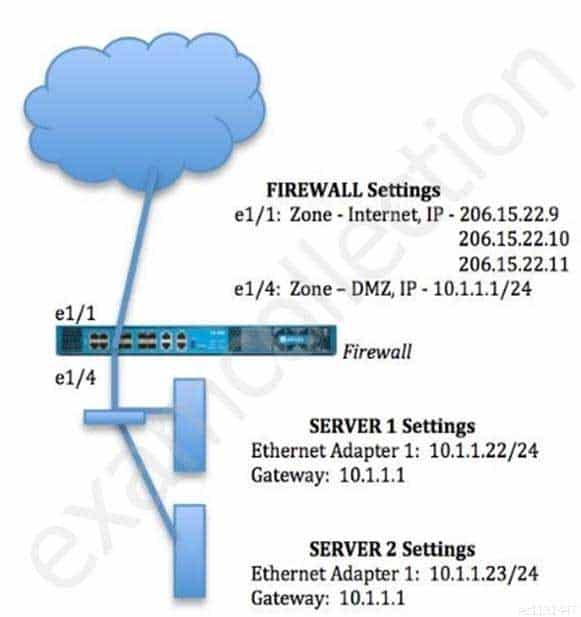
PCNSE Palo Alto Networks Certified Network Security Engineer Part 03 Q02 014 -
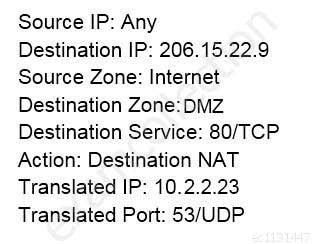
PCNSE Palo Alto Networks Certified Network Security Engineer Part 03 Q02 015 -
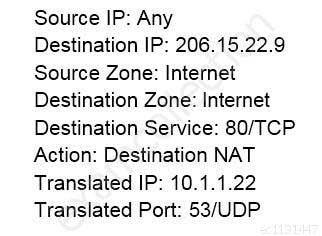
PCNSE Palo Alto Networks Certified Network Security Engineer Part 03 Q02 016 -
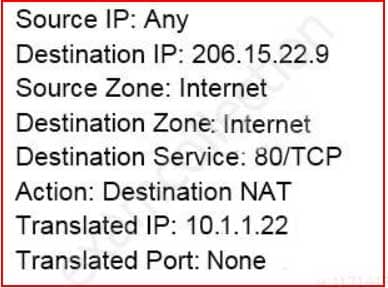
PCNSE Palo Alto Networks Certified Network Security Engineer Part 03 Q02 017 -
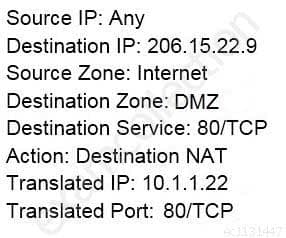
PCNSE Palo Alto Networks Certified Network Security Engineer Part 03 Q02 018
-
-
An administrator creates a custom application containing Layer 7 signatures. The latest application and threat dynamic update is downloaded to the same NGFW. The update contains an application that matches the same traffic signatures as the custom application.
Which application should be used to identify traffic traversing the NGFW?
- Custom application
- System logs show an application error and neither signature is used.
- Downloaded application
- Custom and downloaded application signature files are merged and both are used
-
Starting with PAN-OS version 9.1, GlobalProtect logging information is now recorded in which firewall log?
- GlobalProtect
- System
- Authentication
- Configuration
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-new-features/globalprotect-features/enhanced-logging-for-globalprotect.html -
Refer to the exhibit.
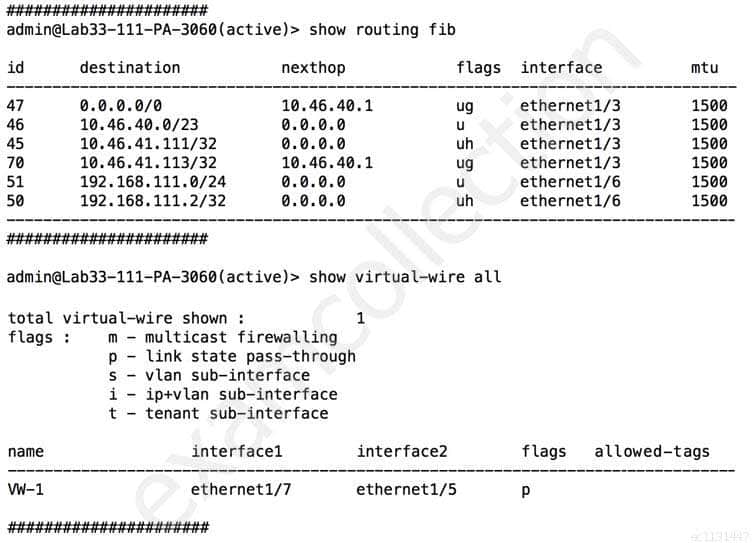
PCNSE Palo Alto Networks Certified Network Security Engineer Part 03 Q05 019 Which will be the egress interface if the traffic’s ingress interface is ethernet1/7 sourcing from 192.168.111.3 and to the destination 10.46.41.113?
- ethernet1/6
- ethernet1/3
- ethernet1/7
- ethernet1/5
-
Which three authentication services can an administrator use to authenticate admins into the Palo Alto Networks NGFW without defining a corresponding admin account on the local firewall? (Choose three.)
- Kerberos
- PAP
- SAML
- TACACS+
- RADIUS
- LDAP
-
Which event will happen if an administrator uses an Application Override Policy?
- Threat-ID processing time is decreased.
- The Palo Alto Networks NGFW stops App-ID processing at Layer 4.
- The application name assigned to the traffic by the security rule is written to the Traffic log.
- App-ID processing time is increased.
Explanation:Reference:https://live.paloaltonetworks.com/t5/Learning-Articles/Tips-amp-Tricks-How-to-Create-an-Application-Override/ta-p/65513 -
Which Security policy rule will allow an admin to block facebook chat but allow Facebook in general?
- Deny application facebook-chat before allowing application facebook
- Deny application facebook on top
- Allow application facebook on top
- Allow application facebook before denying application facebook-chat
Explanation:Reference:https://live.paloaltonetworks.com/t5/Configuration-Articles/Failed-to-Block-Facebook-Chat-Consistently/ta-p/115673 -
A client is concerned about resource exhaustion because of denial-of-service attacks against their DNS servers.
Which option will protect the individual servers?
- Enable packet buffer protection on the Zone Protection Profile.
- Apply an Anti-Spyware Profile with DNS sinkholing.
- Use the DNS App-ID with application-default.
- Apply a classified DoS Protection Profile.
-
If the firewall is configured for credential phishing prevention using the “Domain Credential Filter” method, which login will be detected as credential theft?
- Mapping to the IP address of the logged-in user.
- First four letters of the username matching any valid corporate username.
- Using the same user’s corporate username and password.
- Matching any valid corporate username.
Explanation:Reference:https://www.paloaltonetworks.com/documentation/80/pan-os/newfeaturesguide/content-inspection-features/credential-phishing-prevention -
An administrator has users accessing network resources through Citrix XenApp 7.x.
Which User-ID mapping solution will map multiple users who are using Citrix to connect to the network and access resources?
- Client Probing
- Terminal Services agent
- GlobalProtect
- Syslog Monitoring
-
An administrator needs to upgrade a Palo Alto Networks NGFW to the most current version of PAN-OS® software. The firewall has internet connectivity through an Ethernet interface, but no internet connectivity from the management interface. The Security policy has the default security rules and a rule that allows all web-browsing traffic from any to any zone.
What must the administrator configure so that the PAN-OS® software can be upgraded?
- Security policy rule
- CRL
- Service route
- Scheduler
Explanation:Reference:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000Clp3CAC -
Which feature prevents the submission of corporate login information into website forms?
- Data filtering
- User-ID
- File blocking
- Credential phishing prevention
Explanation:Reference:https://www.paloaltonetworks.com/cyberpedia/how-the-next-generation-security-platform-contributes-to-gdpr-compliance -
Which option is part of the content inspection process?
- Packet forwarding process
- SSL Proxy re-encrypt
- IPsec tunnel encryption
- Packet egress process
-
In a virtual router, which object contains all potential routes?
- MIB
- RIB
- SIP
- FIB
Explanation:Reference:https://www.paloaltonetworks.com/documentation/80/pan-os/pan-os/networking/virtual-routers -
An administrator creates an SSL decryption rule decrypting traffic on all ports. The administrator also creates a Security policy rule allowing only the applications DNS, SSL, and web-browsing.
The administrator generates three encrypted BitTorrent connections and checks the Traffic logs. There are three entries. The first entry shows traffic dropped as application Unknown. The next two entries show traffic allowed as application SSL.
Which action will stop the second and subsequent encrypted BitTorrent connections from being allowed as SSL?
- Create a decryption rule matching the encrypted BitTorrent traffic with action “No-Decrypt,” and place the rule at the top of the Decryption policy.
- Create a Security policy rule that matches application “encrypted BitTorrent” and place the rule at the top of the Security policy.
- Disable the exclude cache option for the firewall.
- Create a Decryption Profile to block traffic using unsupported cyphers, and attach the profile to the decryption rule.
-
Refer to the exhibit.
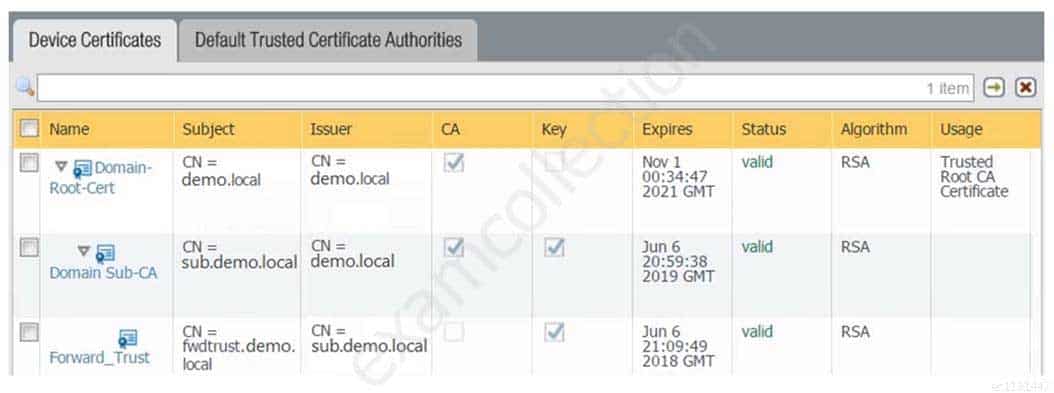
PCNSE Palo Alto Networks Certified Network Security Engineer Part 03 Q07 020 Which certificates can be used as a Forward Trust certificate?
- Certificate from Default Trust Certificate Authorities
- Domain Sub-CA
- Forward-Trust
- Domain-Root-Cert
-
Which option would an administrator choose to define the certificate and protocol that Panorama and its managed devices use for SSL/TLS services?
- Configure a Decryption Profile and select SSL/TLS services.
- Set up SSL/TLS under Policies > Service/URL Category > Service.
- Set up Security policy rule to allow SSL communication.
- Configure an SSL/TLS Profile.
Explanation:Reference:https://www.paloaltonetworks.com/documentation/80/pan-os/web-interface-help/device/device-certificate-management-ssltls-service-profile -
Which menu item enables a firewall administrator to see details about traffic that is currently active through the NGFW?
- ACC
- System Logs
- App Scope
- Session Browser
-
Which protection feature is available only in a Zone Protection Profile?
- SYN Flood Protection using SYN Flood Cookies
- ICMP Flood Protection
- Port Scan Protection
- UDP Flood Protections
Subscribe
0 Comments
Newest