PCNSE : Palo Alto Networks Certified Network Security Engineer : Part 04
-
Which CLI command can be used to export the tcpdump capture?
- scp export tcpdump from mgmt.pcap to < username@host:path>
- scp extract mgmt-pcap from mgmt.pcap to < username@host:path>
- scp export mgmt-pcap from mgmt.pcap to < username@host:path>
- download mgmt-pcap
Explanation:
Reference:
https://live.paloaltonetworks.com/t5/Management-Articles/How-To-Packet-Capture-tcpdump-On-Management-Interface/ta-p/55415
-
An administrator has configured the Palo Alto Networks NGFW’s management interface to connect to the internet through a dedicated path that does not traverse back through the NGFW itself.
Which configuration setting or step will allow the firewall to get automatic application signature updates?
- A scheduler will need to be configured for application signatures.
- A Security policy rule will need to be configured to allow the update requests from the firewall to the update servers.
- A Threat Prevention license will need to be installed.
- A service route will need to be configured.
Explanation:
The firewall uses the service route to connect to the Update Server and checks for new content release versions and, if there are updates available, displays them at the top of the list.
Reference:https://www.paloaltonetworks.com/documentation/80/pan-os/web-interface-help/device/device-dynamic-updates -
Which three options are supported in HA Lite? (Choose three.)
- Virtual link
- Active/passive deployment
- Synchronization of IPsec security associations
- Configuration synchronization
- Session synchronization
Explanation:Reference:https://www.paloaltonetworks.com/documentation/80/pan-os/web-interface-help/device/device-high-availability/ha-lite -
Which CLI command enables an administrator to view details about the firewall including uptime, PAN-OS® version, and serial number?
- debug system details
- show session info
- show system info
- show system details
Explanation:Reference:https://live.paloaltonetworks.com/t5/Learning-Articles/Quick-Reference-Guide-Helpful-Commands/ta-p/56511 -
During the packet flow process, which two processes are performed in application identification? (Choose two.)
- Pattern based application identification
- Application override policy match
- Application changed from content inspection
- Session application identified
-
Which tool provides an administrator the ability to see trends in traffic over periods of time, such as threats detected in the last 30 days?
- Session Browser
- Application Command Center
- TCP Dump
- Packet Capture
Explanation:Reference:https://live.paloaltonetworks.com/t5/Management-Articles/Tips-amp-Tricks-How-to-Use-the-Application-Command-Center-ACC/ta-p/67342 -
The certificate information displayed in the following image is for which type of certificate?
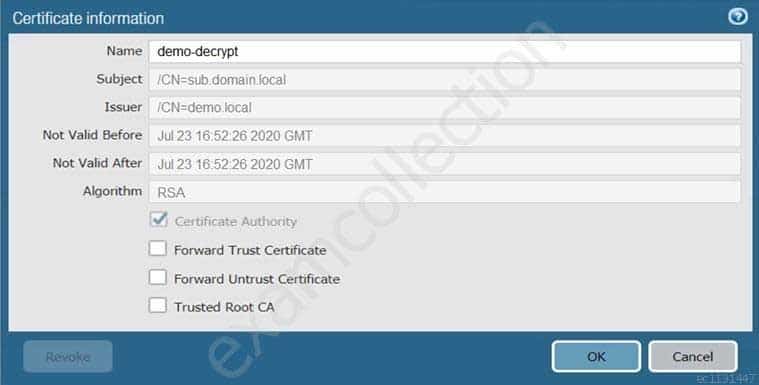
PCNSE Palo Alto Networks Certified Network Security Engineer Part 04 Q07 021 - Forward Trust certificate
- Self-Signed Root CA certificate
- Web Server certificate
- Public CA signed certificate
-
Which three steps will reduce the CPU utilization on the management plane? (Choose three.)
- Disable SNMP on the management interface.
- Application override of SSL application.
- Disable logging at session start in Security policies.
- Disable predefined reports.
- Reduce the traffic being decrypted by the firewall.
-
Which feature must you configure to prevent users from accidentally submitting their corporate credentials to a phishing website?
- URL Filtering profile
- Zone Protection profile
- Anti-Spyware profile
- Vulnerability Protection profile
Explanation:Reference:https://www.paloaltonetworks.com/documentation/80/pan-os/pan-os/threat-prevention/prevent-credential-phishing -
How can a candidate or running configuration be copied to a host external from Panorama?
- Commit a running configuration.
- Save a configuration snapshot.
- Save a candidate configuration.
- Export a named configuration snapshot.
Explanation:Reference: https://www.paloaltonetworks.com/documentation/71/panorama/panorama_adminguide/administer-panorama/back-up-panorama-and-firewall-configurations -
If an administrator does not possess a website’s certificate, which SSL decryption mode will allow the Palo Alto Networks NGFW to inspect traffic when users browse to HTTP(S) websites?
- SSL Forward Proxy
- SSL Inbound Inspection
- SSL Reverse Proxy
- SSL Outbound Inspection
-
An administrator sees several inbound sessions identified as unknown-tcp in the Traffic logs. The administrator determines that these sessions are form external users accessing the company’s proprietary accounting application. The administrator wants to reliably identify this traffic as their accounting application and to scan this traffic for threats.
Which option would achieve this result?
- Create a custom App-ID and enable scanning on the advanced tab.
- Create an Application Override policy.
- Create a custom App-ID and use the “ordered conditions” check box.
- Create an Application Override policy and a custom threat signature for the application.
-
The administrator has enabled BGP on a virtual router on the Palo Alto Networks NGFW, but new routes do not seem to be populating the virtual router.
Which two options would help the administrator troubleshoot this issue? (Choose two.)
- View the System logs and look for the error messages about BGP.
- Perform a traffic pcap on the NGFW to see any BGP problems.
- View the Runtime Stats and look for problems with BGP configuration.
- View the ACC tab to isolate routing issues.
-
An administrator has enabled OSPF on a virtual router on the NGFW. OSPF is not adding new routes to the virtual router.
Which two options enable the administrator to troubleshoot this issue? (Choose two.)
- View Runtime Stats in the virtual router.
- View System logs.
- Add a redistribution profile to forward as BGP updates.
- Perform a traffic pcap at the routing stage.
-
Which three firewall states are valid? (Choose three.)
- Active
- Functional
- Pending
- Passive
- Suspended
Explanation:Reference:https://www.paloaltonetworks.com/documentation/71/pan-os/pan-os/high-availability/ha-firewall-states -
Which virtual router feature determines if a specific destination IP address is reachable?
- Heartbeat Monitoring
- Failover
- Path Monitoring
- Ping-Path
Explanation:Reference:https://www.paloaltonetworks.com/documentation/80/pan-os/pan-os/policy/policy-based-forwarding/pbf/path-monitoring-for-pbf -
An administrator has a requirement to export decrypted traffic from the Palo Alto Networks NGFW to a third-party, deep-level packet inspection appliance.
Which interface type and license feature are necessary to meet the requirement?
- Decryption Mirror interface with the Threat Analysis license
- Virtual Wire interface with the Decryption Port Export license
- Tap interface with the Decryption Port Mirror license
- Decryption Mirror interface with the associated Decryption Port Mirror license
Explanation:Reference:https://www.paloaltonetworks.com/documentation/80/pan-os/pan-os/decryption/decryption-concepts/decryption-mirroring -
When is the content inspection performed in the packet flow process?
- after the application has been identified
- before session lookup
- before the packet forwarding process
- after the SSL Proxy re-encrypts the packet
Explanation:Reference:
https://live.paloaltonetworks.com/t5/Learning-Articles/Packet-Flow-Sequence-in-PAN-OS/ta-p/56081 -
An administrator has created an SSL Decryption policy rule that decrypts SSL sessions on any port.
Which log entry can the administrator use to verify that sessions are being decrypted?
- In the details of the Traffic log entries
- Decryption log
- Data Filtering log
- In the details of the Threat log entries
Explanation:Reference:https://live.paloaltonetworks.com/t5/Configuration-Articles/How-to-Implement-and-Test-SSL-Decryption/ta-p/59719 -
An administrator has been asked to configure a Palo Alto Networks NGFW to provide protection against external hosts attempting to exploit a flaw in an operating system on an internal system.
Which Security Profile type will prevent this attack?
- Vulnerability Protection
- Anti-Spyware
- URL Filtering
- Antivirus
Explanation:Reference:https://www.paloaltonetworks.com/documentation/80/pan-os/web-interface-help/objects/objects-security-profiles-vulnerability-protection
Subscribe
0 Comments
Newest