PCNSE : Palo Alto Networks Certified Network Security Engineer : Part 08
-
Which three file types can be forwarded to WildFire for analysis as a part of the basic WildFire service? (Choose three.)
- .dll
- .exe
- .fon
- .apk
- .jar
-
An administrator has been asked to configure active/active HA for a pair of firewalls. The firewalls use Layer 3 interfaces to send traffic to a single gateway IP for the pair.
Which configuration will enable this HA scenario?
- The two firewalls will share a single floating IP and will use gratuitous ARP to share the floating IP.
- Each firewall will have a separate floating IP, and priority will determine which firewall has the primary IP.
- The firewalls do not use floating IPs in active/active HA.
- The firewalls will share the same interface IP address, and device 1 will use the floating IP if device 0 fails.
Explanation:
Reference:
https://www.paloaltonetworks.com/documentation/71/pan-os/pan-os/high-availability/floating-ip-address-and-virtual-mac-address
-
Which version of GlobalProtect supports split tunneling based on destination domain, client process, and HTTP/HTTPS video streaming application?
- GlobalProtect version 4.0 with PAN-OS 8.1
- GlobalProtect version 4.1 with PAN-OS 8.1
- GlobalProtect version 4.1 with PAN-OS 8.0
- GlobalProtect version 4.0 with PAN-OS 8.0
Explanation:Reference:https://www.paloaltonetworks.com/documentation/41/globalprotect/globalprotect-app-new-features/new-features-released-in-gp-agent-4_1/split-tunnel-for-public-applications -
How does Panorama prompt VMWare NSX to quarantine an infected VM?
- HTTP Server Profile
- Syslog Server Profile
- Email Server Profile
- SNMP Server Profile
Explanation:Reference: https://www.paloaltonetworks.com/documentation/80/virtualization/virtualization/set-up-the-vm-series-firewall-on-vmware-nsx/dynamically-quarantine-infected-guests -
An administrator accidentally closed the commit window/screen before the commit was finished. Which two options could the administrator use to verify the progress or success of that commit task? (Choose two.)
-
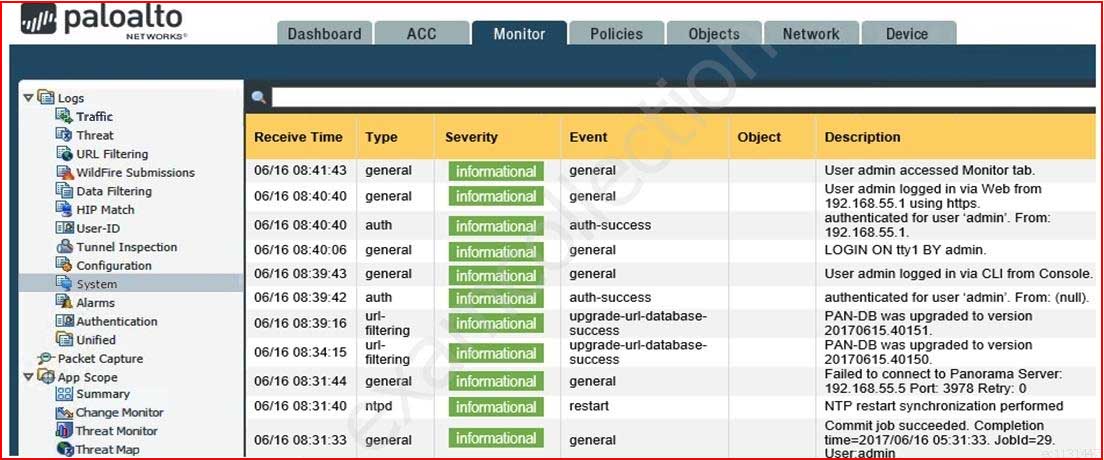
PCNSE Palo Alto Networks Certified Network Security Engineer Part 08 Q05 030 -
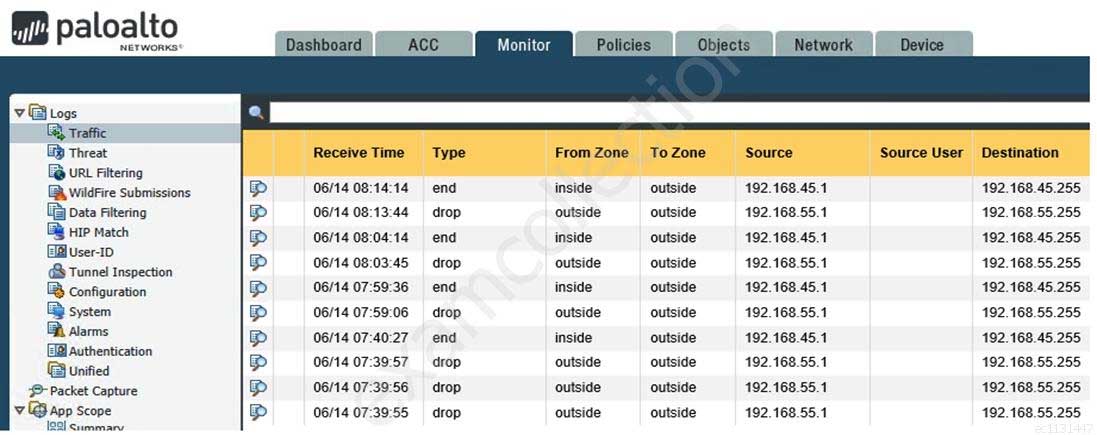
PCNSE Palo Alto Networks Certified Network Security Engineer Part 08 Q05 031 -
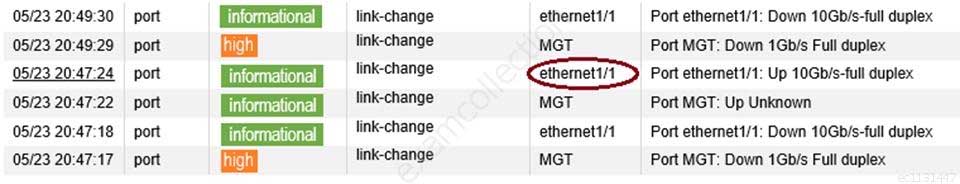
PCNSE Palo Alto Networks Certified Network Security Engineer Part 08 Q05 032 -
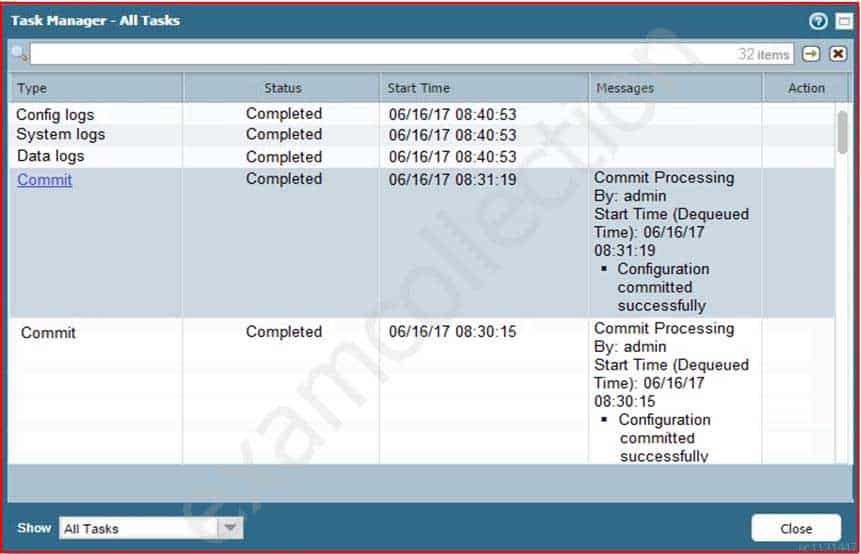
PCNSE Palo Alto Networks Certified Network Security Engineer Part 08 Q05 033
-
-
Which two actions would be part of an automatic solution that would block sites with untrusted certificates without enabling SSL Forward Proxy? (Choose two.)
- Create a no-decrypt Decryption Policy rule.
- Configure an EDL to pull IP addresses of known sites resolved from a CRL.
- Configure a Dynamic Address Group for untrusted sites.
- Create a Security Policy rule with a vulnerability Security Profile attached.
- Enable the “Block sessions with untrusted issuers” setting.
Explanation:Reference:https://www.paloaltonetworks.com/documentation/71/pan-os/web-interface-help/objects/objects-decryption-profile -
An administrator is defining protection settings on the Palo Alto Networks NGFW to guard against resource exhaustion. When platform utilization is considered, which steps must the administrator take to configure and apply packet buffer protection?
- Enable and configure the Packet Buffer Protection thresholds.
Enable Packet Buffer Protection per ingress zone. - Enable and then configure Packet Buffer thresholds.
Enable Interface Buffer protection. - Create and Apply Zone Protection Profiles in all ingress zones.
Enable Packet Buffer Protection per ingress zone. - Configure and apply Zone Protection Profiles for all egress zones.
Enable Packet Buffer Protection per egress zone. - Enable per-vsys Session Threshold alerts and triggers for Packet Buffer Limits.
Enable Zone Buffer Protection per zone.
Explanation:Reference:https://www.paloaltonetworks.com/documentation/80/pan-os/pan-os/zone-protection-and-dos-protection/configure-zone-protection-to-increase-network-security/configure-packet-buffer-protection - Enable and configure the Packet Buffer Protection thresholds.
-
What is the purpose of the firewall decryption broker?
- decrypt SSL traffic and then send it as cleartext to a security chain of inspection tools.
- force decryption of previously unknown cipher suites
- reduce SSL traffic to a weaker cipher before sending it to a security chain of inspection tools.
- inspect traffic within IPsec tunnels
Explanation:Reference:https://www.paloaltonetworks.com/documentation/81/pan-os/newfeaturesguide/decryption-features/decryption-broker -
SAML SLO is supported for which two firewall features? (Choose two.)
- GlobalProtect Portal
- CaptivePortal
- WebUI
- CLI
Explanation:Reference:https://www.paloaltonetworks.com/documentation/80/pan-os/pan-os/authentication/configure-saml-authentication -
What are the two behavior differences between Highlight Unused Rules and the Rule Usage Hit counter when a firewall is rebooted? (Choose two.)
- Rule Usage Hit counter will not be reset.
- Highlight Unused Rules will highlight all rules.
- Highlight Unused Rules will highlight zero rules.
- Rule Usage Hit counter will reset.
-
Which is not a valid reason for receiving a decrypt-cert-validation error?
- Unsupported HSM
- Unknown certificate status
- Client authentication
- Untrusted issuer
Explanation:Reference:https://www.paloaltonetworks.com/documentation/71/pan-os/newfeaturesguide/networking-features/ssl-ssh-session-end-reasons -
In the following image from Panorama, why are some values shown in red?
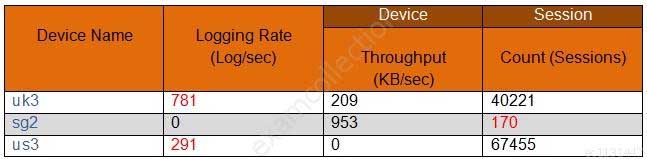
PCNSE Palo Alto Networks Certified Network Security Engineer Part 08 Q12 034 - sg2 session count is the lowest compared to the other managed devices.
- us3 has a logging rate that deviates from the administrator-configured thresholds.
- uk3 has a logging rate that deviates from the seven-day calculated baseline.
- sg2 has misconfigured session thresholds.
Explanation:Reference:https://www.paloaltonetworks.com/documentation/81/pan-os/newfeaturesguide/panorama-features/device-monitoring-through-panorama -
The firewall is not downloading IP addresses from MineMeld. Based on the image, what most likely is wrong?
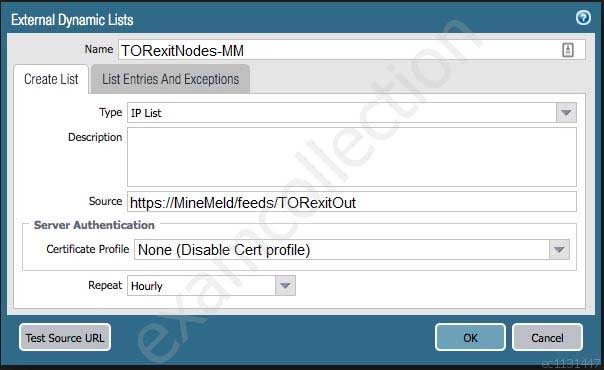
PCNSE Palo Alto Networks Certified Network Security Engineer Part 08 Q13 035 - A Certificate Profile that contains the client certificate needs to be selected.
- The source address supports only files hosted with an ftp://<address/file>.
- External Dynamic Lists do not support SSL connections.
- A Certificate Profile that contains the CA certificate needs to be selected.
Explanation:Reference:https://live.paloaltonetworks.com/t5/MineMeld-Articles/Connecting-PAN-OS-to-MineMeld-using-External-Dynamic-Lists/ta-p/190414 -
Which three split tunnel methods are supported by a GlobalProtect Gateway? (Choose three.)
- video streaming application
- Client Application Process
- Destination Domain
- Source Domain
- Destination user/group
- URL Category
Explanation:Reference: https://www.paloaltonetworks.com/documentation/81/pan-os/newfeaturesguide/globalprotect-features/split-tunnel-for-public-applications -
Which two are valid ACC GlobalProtect Activity tab widgets? (Choose two.)
- Successful GlobalProtect Deployed Activity
- GlobalProtect Deployment Activity
- Successful GlobalProtect Connection Activity
- GlobalProtect Quarantine Activity
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-new-features/globalprotect-features/enhanced-logging-for-globalprotect.html -
Which two features can be used to tag a username so that it is included in a dynamic user group? (Choose two.)
- log forwarding auto-tagging
- XML API
- GlobalProtect agent
- User-ID Windows-based agent
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-new-features/user-id-features/dynamic-user-groups.html -
SD-WAN is designed to support which two network topology types? (Choose two.)
- point-to-point
- hub-and-spoke
- full-mesh
- ring
-
Which option describes the operation of the automatic commit recovery feature?
- It enables a firewall to revert to the previous configuration if rule shadowing is detected.
- It enables a firewall to revert to the previous configuration if application dependency errors are found.
- It enables a firewall to revert to the previous configuration if a commit causes HA partner connectivity failure.
- It enables a firewall to revert to the previous configuration if a commit causes Panorama connectivity failure.
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-new-features/panorama-features/automatic-panorama-connection-recovery.html -
Which three items are important considerations during SD-WAN configuration planning? (Choose three.)
- branch and hub locations
- link requirements
- name of the ISP
- IP Addresses
Explanation:Reference:https://docs.paloaltonetworks.com/sd-wan/1-0/sd-wan-admin/sd-wan-overview/plan-sd-wan-configuration -
Starting with PAN-OS version 9.1, application dependency information is now reported in which two locations? (Choose two.)
- on the App Dependency tab in the Commit Status window
- on the Policy Optimizer’s Rule Usage page
- on the Application tab in the Security Policy Rule creation window
- on the Objects > Applications browser pages
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/app-id/use-application-objects-in-policy/resolve-application-dependencies
Subscribe
0 Comments
Newest