PCSAE : Palo Alto Networks Certified Security Automation Engineer : Part 02
-
Which investigation element is best suited for collaboration among users?
- Work Plan
- Related Incidents
- War Room
- Context Data
Explanation:
Reference:
https://blog.paloaltonetworks.com/2020/01/cortex-security-operations/
-
Which three support types are included in the Marketplace Content Packs? (Choose three.)
- Customer supported
- Contex XSOAR supported
- Community supported
- Partner supported
- Prisma Cloud supported
Explanation:Reference:https://docs.paloaltonetworks.com/cortex/cortex-xsoar/6-0/cortex-xsoar-admin/marketplace/marketplace-overview/content-packs-support-types.html -
Which three authentication methods are supported when logging into XSOAR? (Choose three.)
- OTP token
- User name and password
- SAML
- Active Directory authentication
- RADIUS
Explanation:Reference:https://www.paloguard.com/GlobalProtect.asp -
Which two components have their own context data? (Choose two.)
- Sub-playbook
- Task
- Field
- Incident
-
What are two main uses of context data? (Choose two.)
- Store incident information in JSON format
- Store incident information in XML format
- Pass data between playbook tasks
- Pass data between to-do tasks
Explanation:Reference:https://xsoar.pan.dev/docs/integrations/context-and-outputs#:~:text=The%20main%20use%20of%20the,the%20Context%20and%20uses%20it. -
Multiple company assets were reported by vulnerability scanners as being vulnerable to CVE-2017-11882. This vulnerability affects applications installed on workstations. The SOC team needs to take action and apply the new vulnerability patch that was just released. The team must first create a cause for each of the identified assets in ServiceNow IT Service Management (ITSM), in order to notify the IT department. Next, the team creates a task in the main playbook, which extracts the list of assets from the scanner report.
After the list of assets are created, what are the two solutions that the SOC team could take so that a case could be created and a patch installed? (Choose two.)
- Create a sub-playbook with a single input containing the computer names that will loop until the last item from the asset list (Condition:
AreValuesEqual – Exit on yes – left:1, right 1) and perform the following tasks:
– Active Directory User Enrichment based on thecomputerName
– Create the ServiceNow Record by adding the enrichment information
– Mark the ticket severity as Urgent - Create a sub-playbook with a single input containing the computer names that will loop ‘For Each Input’ and perform the following tasks:
– Active Directory User Enrichment based on thecomputerName
– Create the ServiceNow Record by adding the enrichment information
– Mark the ticket severity as Urgent - Set a key for storing the iteration number and create a sub-playbook with a single input containing the computer names that will loop until the last item from the asset list (Exit condition:
iterator contains the count of the number of items in the list) and perform the following tasks:
– Active Directory User Enrichment based on the computerName
– Create the ServiceNow Record by adding the enrichment information
– Mark the ticket severity as Urgent - Set a key for storing the iteration number and create a sub-playbook with a single input containing the computer names that will loop until the last item from the asset list (Exit
condition: iterator equal to count of the number of item in the list) and perform the following tasks:
– Increase the iterator value by one each time
– Active Directory User Enrichment based on thecomputerName
– Create the ServiceNow Record by adding the enrichment information
– Mark the ticket severity as Urgent
- Create a sub-playbook with a single input containing the computer names that will loop until the last item from the asset list (Condition:
-
When creating a new tab in the layout, which section cannot be added?
- Retrieve widget chart based on script
- Related incidents
- War room entries picked by entry query
- Incident team members
-
In which two ways can data be transferred between playbooks and sub-playbooks? (Choose two.)
- Inputs and outputs
- Through integration context
- Automatically extracted by sub-playbooks
- From context data, if context is shared globally
-
By default, which components does an XSOAR implementation include?
- XSOAR server, XSOAR engine
- Application server, distributed DB server
- Application server, distributed DB server, Backup server
- All in one server
Explanation:Reference:https://docs.paloaltonetworks.com/cortex/cortex-xsoar/6-0/cortex-xsoar-admin/installation/install-demisto-on-a-physical-or-virtual-server.html -
DRAG DROP
Match the operations with the appropriate context.
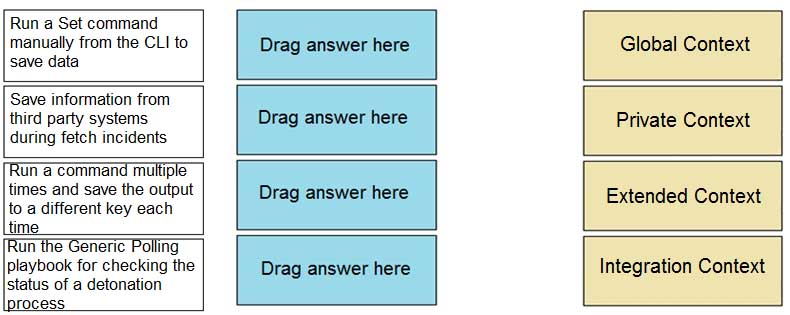
PCSAE Palo Alto Networks Certified Security Automation Engineer Part 02 Q10 003 Question 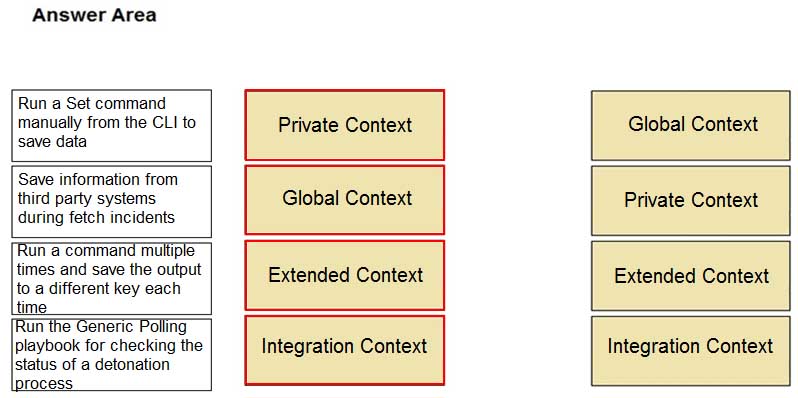
PCSAE Palo Alto Networks Certified Security Automation Engineer Part 02 Q10 003 Answer -
Which three statements are true about the Marketplace? (Choose three.)
- Allows reverting back to a previous version of a content pack
- Enables users to participate in the community by sharing content
- Publishes content without additional review from the Cortex XSOAR team
- Allows uploading of content in additional languages
- Offers granularity in installation through content packs
-
What can be added to offload integration instance processing from the main server?
- Database node
- Application server
- Engine
- Development server
-
Which XSOAR architecture would be recommended for Managed Security Service Providers (MSSP)?
- Multi-region
- Dev-Prod
- Multi-tenant
- Distributed database
Explanation:Reference:https://www.ncsi.com/wp-content/uploads/2020/11/cortex-xsoar.pdf -
An incident field is created having the display name as Source_IP.
How can the field be accessed?
-
${incident.sourceip} -
${incident.Source_IP} -
${incident.srcip} -
${incident.Source IP}
-
-
DRAG DROP
Arrange these steps in the order that they occur during an incident fetch.
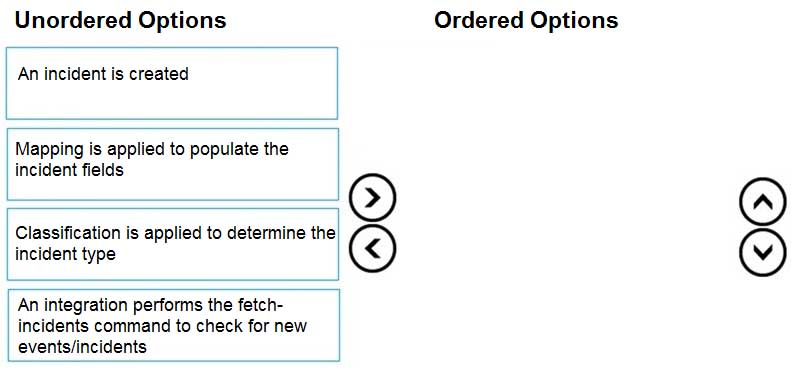
PCSAE Palo Alto Networks Certified Security Automation Engineer Part 02 Q15 004 Question 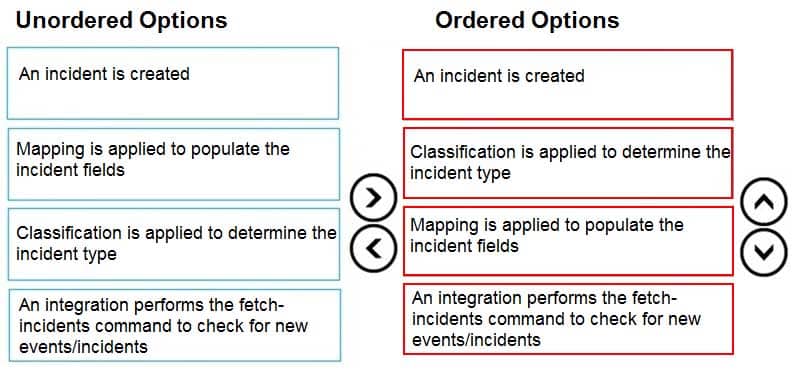
PCSAE Palo Alto Networks Certified Security Automation Engineer Part 02 Q15 004 Answer -
An engineer deployed two different instances of Active Directory for each organization site. As part of account enrichment use case, the engineer would like to delete a user from one specific site.
Which command will accomplish this?
-
run ‘ad-delete-user’ command with ‘user-dn’ arg and using-brand=“Active Directory Query v2” -
run ‘ad-delete-user’ command with ‘user-dn’ arg and raw-response=true
-
run ‘ad-delete-user’ command with ‘user-dn’ arg and ignore-outputs=true
-
run ‘ad-delete-user’ command with ‘user-dn’ arg and using=“Active Directory Query v2_instance_1”
-
-
An engineer is developing a playbook that will be run multiple times for testing purposes.
What is the recommended first task to be used in the playbook?
- DeleteContext
- GenerateTest
- PrintContext
- SetContext
Explanation:Reference:https://xsoar.pan.dev/docs/integrations/test-playbooks -
What is the most effective way to correlate multiple raw events coming from a SIEM and link them together?
- Process all alerts by running the respective playbook and link related incidents during post-processing
- Ingest all raw events, run a custom script to find the relationship between them and proceed to link them together
- Configure a pre-process rule to link related events as they are ingested
- Manually go through the incidents created by the raw events and link related incidents
-
Which two incident search queries are valid? (Choose two.)
-
created:>=”7 days” -
owner===admin
-
role is Analyst
-
status:closed –category:job
Explanation:Reference:https://docs.paloaltonetworks.com/cortex/cortex-xsoar/5-5/cortex-xsoar-admin/cortex-xsoar-overview/how-to-search-in-cortex-xsoar.html -
-
What is the correct expression to use when filtering only PDF files?
- Use File.Extension that does not equal (string comparison) PDF
- Use File.Name contains PDF
- Use File.Extension contains (general) PDF
- Use File.Extension equals (string comparison) PDF
Subscribe
0 Comments
Newest