PSE Strata : Palo Alto Networks System Engineer Professional – Strata : Part 02
-
Which three features are used to prevent abuse of stolen credentials? (Choose three.)
- multi-factor authentication
- URL Filtering Profiles
- WildFire Profiles
- Prisma Access
- SSL decryption rules
Explanation:
Reference:
https://www.paloaltonetworks.com/company/press/2017/palo-alto-networks-delivers-industry-first-capabilities-to-prevent-credential-theft-and-abuse
-
A customer has business-critical applications that rely on the general web-browsing application. Which security profile can help prevent drive-by-downloads while still allowing web-browsing traffic?
- File Blocking Profile
- DoS Protection Profile
- URL Filtering Profile
- Vulnerability Protection Profile
Explanation:Reference:https://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=&ved=2ahUKEwjaw53CvdHyAhUPy4UKHXT5D-MQFnoECAMQAQ&url=https%3A%2F%2Fknowledgebase.paloaltonetworks.com%2Fservlet%2FfileField%3FentityId%3Dka10g000000U0roAAC%26field%3DAttachment_1__Body__s&usg=AOvVaw3DCBM7-FwWInkWYANLrzUt (32) -
Which three settings must be configured to enable Credential Phishing Prevention? (Choose three.)
- validate credential submission detection
- enable User-ID
- define an SSL decryption rulebase
- define URL Filtering Profile
- Enable App-ID
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/threat-prevention/prevent-credential-phishing.html -
A customer with a legacy firewall architecture is focused on port and protocol level security, and has heard that next generation firewalls open all ports by default.
What is the appropriate rebuttal that positions the value of a NGFW over a legacy firewall?
- Palo Alto Networks does not consider port information, instead relying on App-ID signatures that do not reference ports
- Default policies block all interzone traffic. Palo Alto Networks empowers you to control applications by default ports or a configurable list of approved ports on a per-policy basis
- Palo Alto Networks keep ports closed by default, only opening ports after understanding the application request, and then opening only the application-specified ports
- Palo Alto Networks NGFW protects all applications on all ports while leaving all ports opened by default
Explanation:Reference:https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClVwCAK -
Which four actions can be configured in an Anti-Spyware profile to address command-and-control traffic from compromised hosts? (Choose four.)
- Reset
- Quarantine
- Drop
- Allow
- Redirect
- Alert
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/policy/security-profiles -
What are three valid sources that are supported for user IP address mapping in Palo Alto Networks NGFW? (Choose three.)
- RADIUS
- Client Probing
- Lotus Domino
- Active Directory monitoring
- TACACS
- eDirectory monitoring
-
Which CLI allows you to view the names of SD-WAN policy rules that send traffic to the specified virtual SD-WAN interface, along with the performance metrics?
- >show sdwan connection all |
- >show sdwan path-monitor stats vif
- >show sdwan rule vif sdwan.x
- >show sdwan session distribution policy-name
Explanation:Reference:https://docs.paloaltonetworks.com/sd-wan/1-0/sd-wan-admin/troubleshooting/use-cli-commands-for-sd-wan-tasks.html -
Which two actions can be taken to enforce protection from brute force attacks in the security policy? (Choose two.)
- Create a log forwarding object to send logs to Panorama and a third-party syslog server event correlation
- Install content updates that include new signatures to protect against emerging threats
- Attach the vulnerability profile to a security rule
- Add the URL filtering profile to a security rule
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/threat-prevention/prevent-brute-force-attacks.html -
A customer is concerned about zero-day targeted attacks against its intellectual property.
Which solution informs a customer whether an attack is specifically targeted at them?
- Cortex XDR Prevent
- AutoFocus
- Cortex XSOAR Community edition
- Panorama Correlation Report
-
Which three actions should be taken before deploying a firewall evaluation unit in the customer’s environment? (Choose three.)
- Reset the evaluation unit to factory default to ensure that data from any previous customer evaluation is removed
- Request that the customer make port 3978 available to allow the evaluation unit to communicate with Panorama
- Upgrade the evaluation unit to the most current recommended firmware, unless a demo of the upgrade process is planned
- Inform the customer that they will need to provide a SPAN port for the evaluation unit assuming a TAP mode deployment
- Set expectations around which information will be presented in the Security Lifecycle Review because sensitive information may be made visible
-
Which three activities can the botnet report track? (Choose three.)
- Accessing domains registered in the last 30 days
- Visiting a malicious URL
- Launching a P2P application
- Detecting malware within a one-hour period
- Initiating API calls to other applications
- Using dynamic DNS domain providers
Explanation:Reference:https://media.paloaltonetworks.com/documents/Controlling-Botnets.pdf -
A customer requires protections and verdicts for PE (portable executable) and ELF (executable and linkable format) as well as integration with products and services can also access the immediate verdicts to coordinate enforcement to prevent successful attacks.
What competitive feature does Palo Alto Networks provide that will address this requirement?
- File Blocking Profile
- Dynamic Unpacking
- WildFire
- DNS Security
Explanation:Reference:https://docs.paloaltonetworks.com/wildfire/u-v/wildfire-whats-new/latest-wildfire-cloud-features/real-time-wildfire-verdicts-and-signatures-for-pe-and-elf-files.html -
Which statement is true about Deviating Devices and metrics?
- A metric health baseline is determined by averaging the health performance for a given metric over seven days plus the standard deviation
- Deviating Device Tab is only available with a SD-WAN Subscription
- An Administrator can set the metric health baseline along with a valid standard deviation
- Deviating Device Tab is only available for hardware-based firewalls
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-web-interface-help/panorama-web-interface/panorama-managed-devices-summary/panorama-managed-devices-health.html -
DRAG DROP
Match the WildFire Inline Machine Learning Model to the correct description for that model.
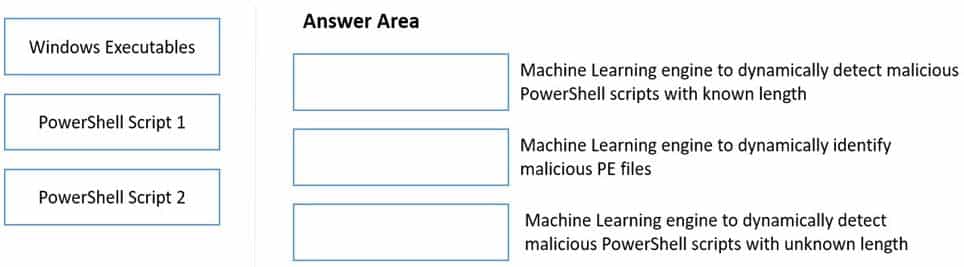
PSE Strata Palo Alto Networks System Engineer Professional – Strata Part 02 Q14 001 Question 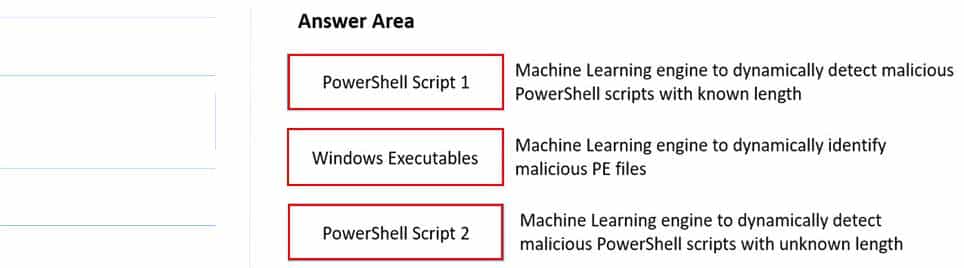
PSE Strata Palo Alto Networks System Engineer Professional – Strata Part 02 Q14 001 Answer Explanation:Reference:https://docs.paloaltonetworks.com/wildfire/u-v/wildfire-whats-new/wildfire-features-in-panos-100/configure-wildfire-inline-ml.html -
Palo Alto Networks publishes updated Command-and-Control signatures.
How frequently should the related signatures schedule be set?
- Once an hour
- Once a day
- Once a week
- Once every minute
-
Which two methods will help avoid Split Brain when running HA in Active/Active mode? (Choose two.)
- Configure a Backup HA1 Interface
- Configure a Heartbeat Backup
- Create a loopback IP address and use that as a Source Interface
- Place your management interface in an Aggregate Interface Group configuration
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/high-availability/set-up-activeactive-ha/configure-activeactive-ha.html -
Which three script types can be analyzed in WildFire? (Choose three.)
- JScript
- PythonScript
- PowerShell Script
- VBScript
- MonoScript
Explanation:Reference:https://docs.paloaltonetworks.com/wildfire/u-v/wildfire-whats-new/wildfire-features-in-panos-90/wildfire-appliance-script-support.html -
What helps avoid split brain in active/passive HA pair deployment?
- Use a standard traffic interface as the HA2 backup
- Enable preemption on both firewalls in the HA pair
- Use the management interface as the HA1 backup link
- Use a standard traffic interface as the HA3 link
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/high-availability/set-up-activepassive-ha/configure-activepassive-ha.html -
DRAG DROP
Match the functions to the appropriate processing engine within the dataplane.

PSE Strata Palo Alto Networks System Engineer Professional – Strata Part 02 Q19 002 Question 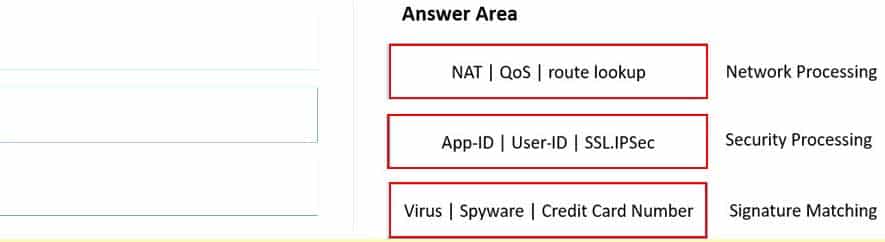
PSE Strata Palo Alto Networks System Engineer Professional – Strata Part 02 Q19 002 Answer -
What are three considerations when deploying User-ID? (Choose three.)
- Specify included and excluded networks when configuring User-ID
- Only enable User-ID on trusted zones
- Use a dedicated service account for User-ID services with the minimal permissions necessary
- User-ID can support a maximum of 15 hops
- Enable WMI probing in high security networks
Explanation:Reference:https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClVPCA0
Subscribe
0 Comments
Newest