PSE Strata : Palo Alto Networks System Engineer Professional – Strata : Part 03
-
Which three considerations should be made prior to installing a decryption policy on the NGFW? (Choose three.)
- Include all traffic types in decryption policy
- Inability to access websites
- Exclude certain types of traffic in decryption policy
- Deploy decryption setting all at one time
- Ensure throughput is not an issue
-
Which three components are specific to the Query Builder found in the Custom Report creation dialog of the firewall? (Choose three.)
- Connector
- Database
- Recipient
- Operator
- Attribute
- Schedule
Explanation:
Reference:
https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/monitoring/view-and-manage-reports/generate-custom-reports
-
Which CLI commands allows you to view SD-WAN events such as path selection and path quality measurements?
- >show sdwan connection all
- >show sdwan event
- >show sdwan path-monitor stats vif
- >show sdwan session distribution policy-name
Explanation:Reference:https://docs.paloaltonetworks.com/sd-wan/1-0/sd-wan-admin/troubleshooting/use-cli-commands-for-sd-wan-tasks.html -
Which three steps in the cyberattack lifecycle does Palo Alto Networks Security Operating Platform prevent? (Choose three.)
- recon the target
- deliver the malware
- exfiltrate data
- weaponize vulnerabilities
- lateral movement
Explanation:Reference:https://www.exclusive-networks.com/ch-fr/praevention-cyber-attack-lifecycle-palo-alto/ -
Which profile or policy should be applied to protect against port scans from the internet?
- An App-ID security policy rule to block traffic sourcing from the untrust zone
- Zone protection profile on the zone of the ingress interface
- Security profiles to security policy rules for traffic sourcing from the untrust zone
- Interface management profile on the zone of the ingress interface
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-web-interface-help/network/network-network-profiles-zone-protection/reconnaissance-protection.html -
Which two products are included in the Prisma Brand? (Choose two.)
- Prisma Cloud Compute
- Panorama
- NGFW
- Prisma Cloud Enterprise
Explanation:Reference:https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin-compute/welcome/pcee_vs_pcce.html -
Which three platform components can identify and protect against malicious email links? (Choose three.)
- WildFire hybrid cloud solution
- WildFire public cloud
- WF-500
- M-200
- M-600
-
When having a customer pre-sales call, which aspects of the NGFW should be covered?
- The NGFW simplifies your operations through analytics and automation while giving you consistent protection through exceptional visibility and control across the data center, perimeter, branch, mobile and cloud networks
- The Palo Alto Networks-developed URL filtering database, PAN-DB provides high-performance local caching for maximum inline performance on URL lookups, and offers coverage against malicious URLs and IP addresses. As WildFire identifies unknown malware, zero-day exploits, and advanced persistent threats (APTs), the PAN-DB database is updated with information on malicious URLs so that you can block malware downloads and disable Command and Control (C2) communications to protect your network from cyberthreats. URL categories that identify confirmed malicious content — malware, phishing, and C2 are updated every five minutes — to ensure that you can manage access to these sites within minutes of categorization
- The NGFW creates tunnels that allow users/systems to connect securely over a public network, as if they were connecting over a local area network (LAN). To set up a VPN tunnel you need a pair of devices that can authenticate each other and encrypt the flow of information between them The devices can be a pair of Palo Alto Networks firewalls, or a Palo Alto Networks firewall along with a VPN-capable device from another vendor
- Palo Alto Networks URL Filtering allows you to monitor and control the sites users can access, to prevent phishing attacks by controlling the sites to which users can submit valid corporate credentials, and to enforce safe search for search engines like Google and Bing
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/url-filtering -
What aspect of PAN-OS allows for the NGFW admin to create a policy that provides auto-remediation for anomalous user behavior and malicious activity while maintaining user visibility?
- Remote Device UserID Agent
- user-to-tag mapping
- Dynamic User Groups
- Dynamic Address Groups
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-new-features/user-id-features/dynamic-user-groups -
You have enabled the WildFire ML for PE files in the antivirus profile and have added the profile to the appropriate firewall rules. When you go to Palo Alto Networks WildFire test av file and attempt to download the test file it is allowed through. In order to verify that the machine learning is working from the command line, which command returns a valid result?
- show mlav cloud-status
- show wfml cloud-status
- show ml cloud-status
- show wfav cloud-status
-
What action would address the sub-optimal traffic path shown in the figure?
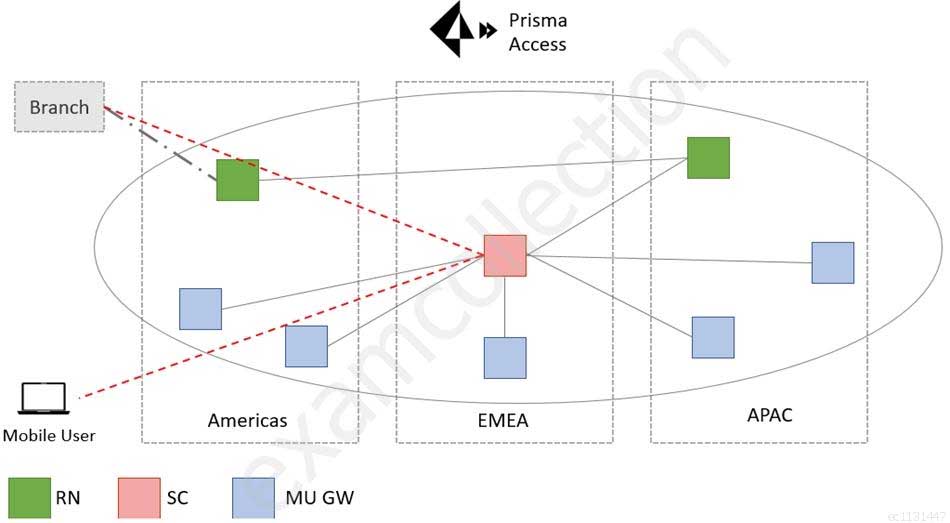
PSE Strata Palo Alto Networks System Engineer Professional – Strata Part 03 Q11 003 Key:
RN – Remote Network
SC – Service Connection
MU GW – Mobile User Gateway- Onboard a Service Connection in the Americas region
- Remove the Service Connection in the EMEA region
- Onboard a Service Connection in the APAC region
- Onboard a Remote Network location in the EMEA region
-
What are the three possible verdicts in WildFire Submissions log entries for a submitted sample? (Choose four.)
- Benign
- Spyware
- Malicious
- Phishing
- Grayware
Explanation:Reference:https://docs.paloaltonetworks.com/wildfire/9-1/wildfire-admin/monitor-wildfire-activity/use-the-firewall-to-monitor-malware/monitor-wildfire-submissions-and-analysis-reports.html -
What two types of traffic should you exclude from a decryption policy? (Choose two.)
- All Business and regulatory traffic
- All outbound traffic
- All Mutual Authentication traffic
- All SSL/TLS 1.3 traffic
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/decryption/decryption-exclusions -
Which functionality is available to firewall users with an active Threat Prevention subscription, but no WildFire license?
- Access to the WildFire API
- WildFire hybrid deployment
- PE file upload to WildFire
- 5 minute WildFire updates to threat signatures
-
What is the recommended way to ensure that firewalls have the most current set of signatures for up-to-date protection?
- Run a Perl script to regularly check for updates and alert when one is released
- Store updates on an intermediary server and point all the firewalls to it
- Utilize dynamic updates with an aggressive update schedule
- Monitor update announcement and manually push updates to firewalls
-
What three Tabs are available in the Detailed Device Health on Panorama for hardware-based firewalls? (Choose three.)
- Errors
- Environments
- Interfaces
- Mounts
- Throughput
- Sessions
- Status
Explanation:Reference:https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-web-interface-help/panorama-web-interface/panorama-managed-devices-summary/detailed-device-health-in-panorama.html -
What component is needed if there is a large scale deployment of Next Generation Firewalls with multiple Panorama Management Servers?
- M-600 Appliance
- Panorama Large Scale VPN Plugin
- Panorama Interconnect Plugin
- Palo Alto Networks Cluster License
Explanation:Reference:https://savantsolutions.net/wp-content/uploads/woocommerce_uploads/2019/05/pcnse-study-guide-v9.pdf (27) -
Which is the smallest Panorama solution that can be used to manage up to 2500 Palo Alto Networks Next Generation firewalls?
- M-200
- M-600
- M-100
- Panorama VM-Series
Explanation:Reference:https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000boF1CAI -
XYZ Corporation has a legacy environment with asymmetric routing. The customer understands that Palo Alto Networks firewalls can support asymmetric routing with redundancy.
Which two features must be enabled to meet the customer’s requirements? (Choose two.)
- Virtual systems
- HA active/active
- HA active/passive
- Policy-based forwarding
Subscribe
0 Comments
Newest