|
Explanation & Hint:
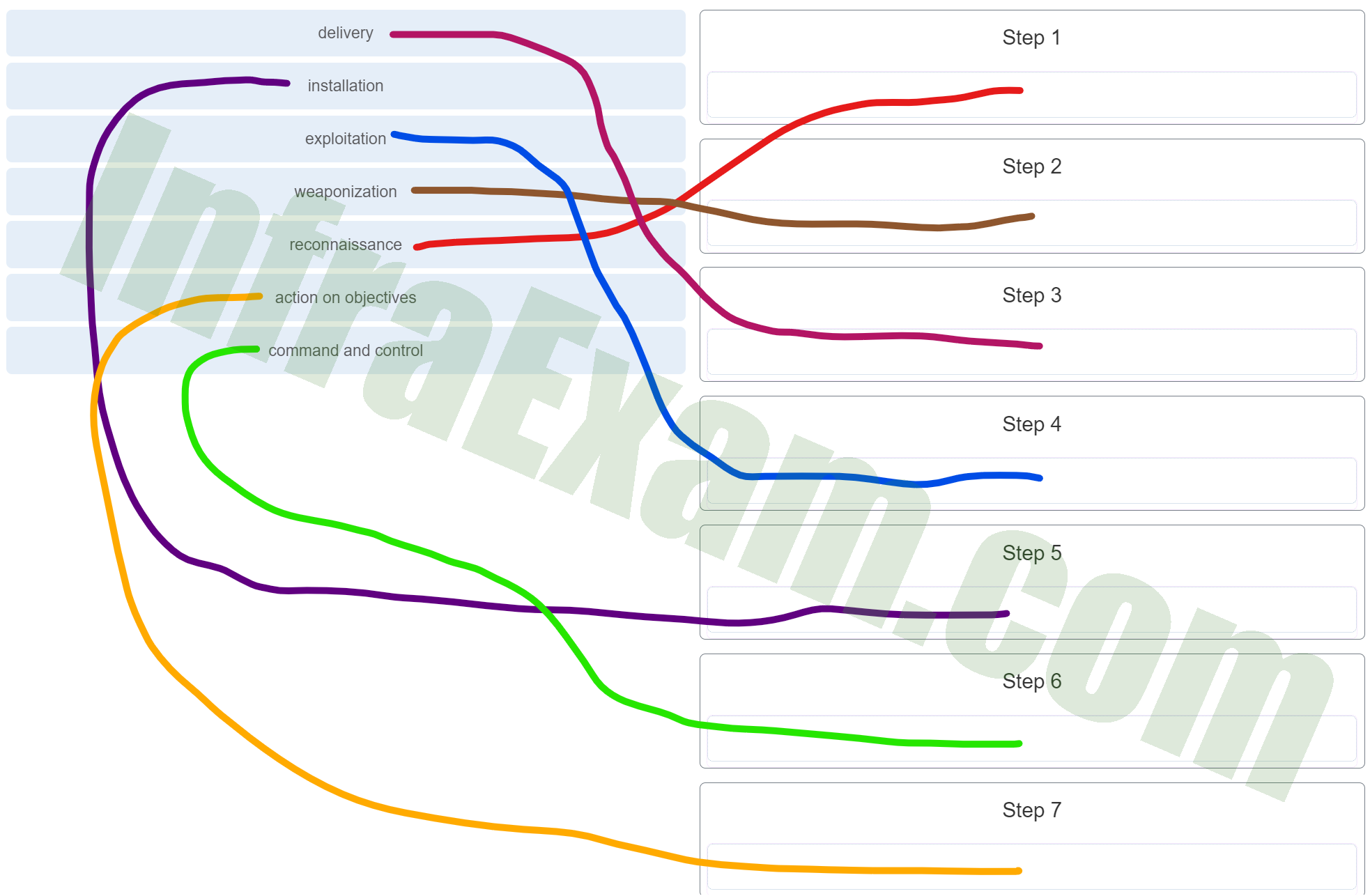
- Reconnaissance: The attacker gathers information on the target before launching an attack.
- Weaponization: The attacker creates malware designed to exploit the vulnerabilities of the target’s system.
- Delivery: The attacker transmits the weaponized bundle to the victim via email, USB, etc.
- Exploitation: The attacker’s code exploits a vulnerability in the victim’s system.
- Installation: The malware is installed on the victim’s system, allowing the attacker to maintain presence.
- Command and Control (C2): The attacker establishes a command and control channel to remotely manipulate the compromised system.
- Actions on Objectives: The attacker accomplishes their end goal, which could be data exfiltration, destruction of data, or any other malicious outcome.
|