| Network Security 1.0 | |
| Final Exam & Lab PT Skills | |
| Practice Final Answers | Online Test |
| Final PT Skills Assessment (PTSA) Answers | NA |
| Course Feedback Answers | Online Test |
| Final Exam Answers | Online Test |
Refer to the exhibit. The ip verify source command is applied on untrusted interfaces. Which type of attack is mitigated by using this configuration?
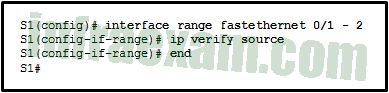
- DHCP starvation
- DHCP spoofing
- STP manipulation
- MAC and IP address spoofing
Answers Explanation & Hints: To protect against MAC and IP address spoofing, apply the IP Source Guard security feature, using the ip verify source command, on untrusted ports.
| Network Security 1.0 | |
| Final Exam & Lab PT Skills | |
| Practice Final Answers | Online Test |
| Final PT Skills Assessment (PTSA) Answers | NA |
| Course Feedback Answers | Online Test |
| Final Exam Answers | Online Test |