Endpoints and Systems Post-Assessment | CBROPS 2025
Endpoints and Systems Post-Assessment | CBROPS 2025
-
On an infected Windows host, what command can be used to verify if the host has an established HTTP connection to the command and control server?
- tracert
- netstat
- net
- packet-capture
- route
Explanation & Hint: Certainly, let’s walk through how to use the Windows Command Prompt to verify established HTTP connections to a command and control server.
- Open Command Prompt:
- Press
Windows Key + Rto open the “Run” dialog. - Type
cmdand press Enter to open the Command Prompt.
- Press
- Use the
netstatcommand:Thenetstatcommand displays active network connections on your Windows system. You can use it to check for established HTTP connections.Here’s the command to use:netstat -an | find "ESTABLISHED" | find ":80"netstat -an: This part of the command displays all active network connections, both listening and established.|: It’s a pipe operator, used to send the output of one command as input to another.find "ESTABLISHED": This filters the results to show only established connections.find ":80": This further narrows down the results to connections on port 80, which is the default port for HTTP.
- Interpret the results:The output of the
netstatcommand will display a list of established connections on port 80 (HTTP). Look for any connections that are established to the IP address or domain of the command and control server.If you see a line that matches the IP address or domain of your command and control server and the port 80, it indicates that an HTTP connection to the command and control server is established.Keep in mind that this method is only useful for checking established network connections. It won’t provide details about the content or the nature of the communication between the infected Windows host and the command and control server.
- Open Command Prompt:
-
With Windows version 8 or higher, which utility can be used to display the users who are currently logged in to the system, and the resources that are consumed by the applications and processes that belong to each user?
- task manager
- msconfig
- netstat
- device manager
Explanation & Hint: With Windows version 8 or higher, you can use the “Task Manager” utility to display the users who are currently logged in to the system and view the resources consumed by the applications and processes that belong to each user.
Here’s how to access Task Manager:
- Press
Ctrl + Shift + Escon your keyboard. - Alternatively, you can press
Ctrl + Alt + Delete, then select “Task Manager” from the options presented.
Within Task Manager, you can navigate to the “Users” tab to see the list of logged-in users and their respective processes and resource consumption. This tab allows you to monitor and manage running applications and processes, including their CPU, memory, disk, and network usage, on a per-user basis.
- Press
-
What is the correct path to access on the example.txt file using Windows file share where the servername is “rwc” and the sharename is “users”?
- \rwc\users\example.txt
- \\rwc\users\example.txt
- \\rwc\users\\example.txt
- .rwc\users\example.txt
- ..rwc\users\example.txt
Explanation & Hint: The correct path to access the “example.txt” file on a Windows file share where the server name is “rwc” and the share name is “users” is:
\\rwc\users\example.txtDouble backslashes (
\\) are used to specify the network path, followed by the server name and then the share name.
-
Why is malware that runs as a Windows service more difficult for the average end user to detect?
- because services run in the background and do not interact with the users
- because services run in the Kernel mode
- because services run in the User mode
- because all services run automatically when the system boots up
Explanation & Hint: Malware that runs as a Windows service is more difficult for the average end user to detect primarily because:
Services run in the background and do not interact with the users.
This means that services operate without a visible user interface or direct interaction, making them less noticeable to the average end user. They can perform their malicious activities silently and persistently, without drawing attention to themselves. Users typically interact with applications that have graphical interfaces, whereas services are background processes designed for tasks that don’t require user interaction, such as system management, network services, and automation. As a result, users are less likely to notice their presence or suspicious behavior.
-
What can be used to make a malicious file to appear to have 0 byte size in the dir command output?
- using AES to encrypt the file
- using winzip to compress the file
- using the Master File Table to alter the true file size
- using NTFS Alternate Data Streams to attach the data to the file
Explanation & Hint: To make a malicious file appear to have a 0-byte size in the
dircommand output on Windows, you can use NTFS Alternate Data Streams (ADS). Alternate Data Streams allow you to attach additional data to a file without changing its size, as reported by thedircommand. The file will still have its actual content, but the ADS can be used to hide or store additional information.By attaching the data to an ADS, the file size, as reported by
dir, will remain 0 bytes, while the actual data remains hidden within the stream. This technique is often used for various purposes, including hiding data or malicious content. However, it’s important to note that this is a technique that can be used for both legitimate and malicious purposes.
-
Which Windows registry hive would be used to track the history of USB storage devices?
- HKEY_LOCAL_MACHINE (HKLM)
- HKEY_CURRENT_USER (HKCU)
- HKEY_CLASSES_ROOT (HKCR)
- HKEY_CURRENT_CONFIG (HKCC)
Explanation & Hint: To track the history of USB storage devices on a Windows system, you would typically examine the Windows Registry under the HKEY_LOCAL_MACHINE (HKLM) hive. This is where information about hardware and system-wide configurations, including USB device history, is stored.
In particular, you can look into the
SYSTEMsubkey within HKLM, which contains information about device installations, including USB devices. However, please note that accessing and interpreting the Windows Registry should be done with caution and is typically performed by experienced IT professionals or forensics experts due to its sensitivity and complexity.
-
Microsoft has operating systems that are targeted for which two kinds of devices? (Choose two.)
- servers
- network routers
- network switches
- personal printers
- personal computers
Explanation & Hint: Microsoft offers operating systems targeted for the following two kinds of devices:
- Servers: Microsoft Windows Server is designed for servers, providing features and capabilities suitable for managing network services, databases, virtualization, and more on server hardware.
- Personal Computers: Microsoft Windows, including versions like Windows 10 and Windows 11, is designed for personal computers (PCs) and laptops. These operating systems are meant for general-purpose computing on individual user devices.
The other options mentioned, such as network routers, network switches, and personal printers, typically do not run Microsoft Windows as their primary operating system. These devices often use specialized embedded operating systems or firmware for their intended purposes.
-
Which two of the following statements are true about Windows virtual memory? (Choose two.)
- Virtual memory combines the RAM memory with the hard disk space to compensate for lack of RAM.
- Adding a larger disk drive to a system automatically increases its virtual memory allocation.
- A virtual address does not represent the actual physical location of an object in memory. Instead, the system maintains a page table for each process, which is
- an internal data structure that is used to translate virtual addresses into their corresponding physical addresses.
- Adding more RAM to a system automatically increases the need for more virtual memory on the system.
Explanation & Hint: The two true statements about Windows virtual memory are:
- Virtual memory combines the RAM memory with the hard disk space to compensate for the lack of RAM.
This statement is accurate. Virtual memory is a memory management technique used by operating systems, including Windows, to provide the illusion of having more physical memory (RAM) than is actually available. It does this by using a combination of RAM and space on the hard disk as a temporary storage area for data that cannot fit in RAM. - A virtual address does not represent the actual physical location of an object in memory. Instead, the system maintains a page table for each process, which is an internal data structure that is used to translate virtual addresses into their corresponding physical addresses.
This statement is also true. In a virtual memory system, applications work with virtual addresses, which do not directly correspond to the physical location of data in RAM. The system uses a page table to map virtual addresses to physical addresses, allowing for efficient management of memory resources and facilitating the illusion of a contiguous address space for each process.
The other two statements are not accurate:
- Adding a larger disk drive to a system does not automatically increase its virtual memory allocation. Virtual memory is typically managed by the operating system, and the size of the virtual memory space is determined by system settings and available disk space.
- Adding more RAM to a system does not automatically increase the need for more virtual memory. In fact, adding more RAM can reduce the reliance on virtual memory because there is more physical memory available for applications and processes.
- Virtual memory combines the RAM memory with the hard disk space to compensate for the lack of RAM.
-
Which two of the following options are ways to launch the Windows Task Manager application? (Choose two.)
- In the Windows Start menu, type Go Task Manager.
- Right-click the taskbar and choose the Start Task Manager option.
- Run the taskmgr command from the Windows command line.
- Launch the task manager hyperlink from the Internet Explorer browser.
Explanation & Hint: The two ways to launch the Windows Task Manager application are:
- Right-click the taskbar and choose the “Start Task Manager” option.
This is a common and straightforward method to open Task Manager. - Run the “taskmgr” command from the Windows command line.
You can open Task Manager by running the “taskmgr” command from the Command Prompt or the Run dialog.
The other options mentioned, such as typing “Go Task Manager” in the Start menu and launching Task Manager from Internet Explorer, are not standard methods for opening Task Manager in Windows.
- Right-click the taskbar and choose the “Start Task Manager” option.
-
Which two statements are true about Windows operating systems? (Choose two.)
- Windows operating systems are used exclusively for desktop computing.
- Windows server platforms offer numerous services.
- Some Windows operating systems support Active Directory services for managing domain-based networks.
- Windows operating systems offer NFS, SMB, and UFS file services.
Explanation & Hint: Which two statements are true about Windows operating systems? (Choose two.) Windows operating systems are used exclusively for desktop computing. Windows server platforms offer numerous services. Some Windows operating systems support Active Directory services for managing domain-based networks. Windows operating systems offer NFS, SMB, and UFS file services.ChatGPTThe two true statements about Windows operating systems are:
- Some Windows operating systems support Active Directory services for managing domain-based networks.
Active Directory is a directory service and authentication framework used in Windows Server platforms for managing domain-based networks. Not all Windows operating systems support Active Directory, but it is a key feature of Windows Server editions. - Windows server platforms offer numerous services.
Windows Server editions are designed to provide a wide range of services and features for network and server management, including services like file sharing, web services, DNS, DHCP, and more. These server platforms are not limited to desktop computing and are intended for server and network infrastructure purposes.
The other two statements are not true:
- Windows operating systems are not used exclusively for desktop computing. While Windows desktop editions are popular for personal computers, Windows Server editions are used extensively for server and enterprise environments.
- Windows operating systems primarily use the SMB (Server Message Block) file services protocol, not NFS (Network File System) and UFS (Unix File System), which are more commonly associated with Unix and Linux-based operating systems.
- Some Windows operating systems support Active Directory services for managing domain-based networks.
-
Which one of the following options is most likely to provide fair and accurate information about operating systems and their known vulnerabilities?
- www.cisco.com
- www.microsoft.com
- www.apple.com
- nvd.nist.gov
Explanation & Hint: The most reliable source for fair and accurate information about operating systems and their known vulnerabilities is nvd.nist.gov (National Vulnerability Database by the National Institute of Standards and Technology, NIST). This database provides comprehensive and up-to-date information on known vulnerabilities for a wide range of operating systems and software, making it a trusted resource for security professionals and researchers. It’s not affiliated with a specific vendor like Cisco, Microsoft, or Apple, so it offers a more neutral and comprehensive view of vulnerabilities across various platforms.
-
Match each tool or application with its description:
- enables you to remotely access a host’s shell or command line ==> PuTTY
- used to securely copy files to and from a remote host ==> WinSCP
- provides the ability to capture network traffic for further analysis ==> Wireshark
- specifically designed for the Windows OS to overcome shortcomings of Windows monitoring and management tools ==> Sysinternals
- shows processes that are communicating with other hosts ==> TCPView
Explanation & Hint: - PuTTY: PuTTY is a widely used open-source terminal emulator that enables you to remotely access a host’s shell or command line. It’s commonly used for secure remote access to servers or network devices via protocols like SSH, Telnet, and others.
- WinSCP: WinSCP is a file transfer client for Windows that is used to securely copy files to and from a remote host. It supports multiple file transfer protocols, including SCP, SFTP, FTPS, and WebDAV, making it a useful tool for securely transferring files between your local system and a remote server.
- Wireshark: Wireshark is a network protocol analyzer that provides the ability to capture network traffic for further analysis. It allows you to inspect and analyze the data flowing over a network in real-time, making it a valuable tool for network administrators and security professionals to troubleshoot and investigate network issues.
- Sysinternals: Sysinternals is a suite of advanced system utilities specifically designed for the Windows operating system. These tools help overcome some of the shortcomings of native Windows monitoring and management tools. They provide in-depth information about system processes, file system activities, registry changes, and more, making them valuable for system administrators and IT professionals.
- TCPView: TCPView is a Windows utility that shows processes that are communicating with other hosts over the network. It displays a list of all network connections, both incoming and outgoing, along with the corresponding processes and the remote hosts they are communicating with. It’s useful for monitoring network activity on a Windows system.
-
Which Windows structure is used to map each process virtual address into the corresponding physical address?
- route table
- memory table
- page table
- cache table
- CPU table
Explanation & Hint: The structure used to map each process’s virtual address into the corresponding physical address is the page table. Page tables are an essential component of virtual memory systems and memory management in modern operating systems, including Windows. They provide the mapping between virtual addresses used by processes and the actual physical memory locations where data is stored. This mapping allows for memory isolation, efficient memory usage, and the ability to handle larger memory spaces than the physical RAM available.
-
Which Windows directory stores the 64-bit system DLL files?
- Program Files (x86)
- Program Files
- System
- System32
Explanation & Hint: On a 64-bit version of Windows, the directory that stores the 64-bit system DLL (Dynamic Link Library) files is the System32 directory. This might seem counterintuitive since the name contains “32,” but it’s a historical naming convention. The “System32” directory contains 64-bit system files, while the “SysWOW64” directory is used to store 32-bit system files on 64-bit Windows.
-
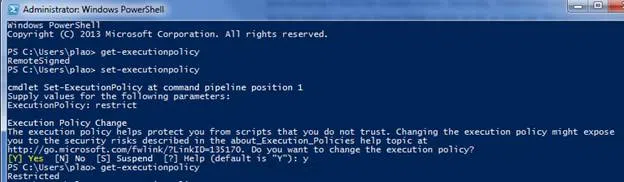
According to the output shown below, what did the user do? (Choose two.)
Endpoints and Systems Post-Assessment CBROPS 01 - Configured the system to require digital signing only of externally-downloaded
- PowerShell scripts
- Changed the PowerShell execution policy to the default setting
- Ran PowerShell with administrative privileges
- Removed all restrictions on running PowerShell scripts
Explanation & Hint: - Changed the PowerShell execution policy to the default setting: Initially, the execution policy was set to “Unrestricted.” However, the user initiated the
Set-ExecutionPolicycmdlet without specifying a particular policy, and the system prompted them to provide a value. The user chose “restrict,” which is the default execution policy for PowerShell. This action effectively reverted the execution policy back to the default setting. - Configured the system to require digital signing only of externally-downloaded PowerShell scripts: This can be inferred from the user’s decision to change the execution policy to the default “restrict” policy. The “restrict” policy allows the execution of local scripts but requires digitally signed scripts when they are downloaded from external sources. This change is for enhanced security to protect against potentially malicious scripts.
- Changed the PowerShell execution policy to the default setting: Initially, the execution policy was set to “Unrestricted.” However, the user initiated the
-
What is required for a Windows user to perform a task with administrator-level access?
- use the “Run as Administrator” option
- enter the kernel mode
- boot the system into the safe mode
- log in as a domain user then switch to the “Admin” group
Explanation & Hint: For a Windows user to perform a task with administrator-level access, they typically need to:
Use the “Run as Administrator” option: This option allows a user to temporarily elevate their privileges to perform a specific task with administrator rights. It is a common method to run applications or commands as an administrator without the need to log in as a full-time administrator. The user would need to have the necessary permissions or provide administrator credentials when prompted.
-
Which one of the following best describes the output that the
netstatcommand displays?- all the active mapped network drives
- all the active connected users on the device
- all the active TCP connections, ports on which the computer is listening
- all the TCPdump statistics
Explanation & Hint: The
netstatcommand displays:All the active TCP connections and the ports on which the computer is listening.
It provides information about network connections, both incoming and outgoing, and the status of the network ports on the computer. This information includes details about established connections, listening ports, and more, which can be useful for network troubleshooting and monitoring.
-
What statement best describes the process that can be used to edit the windows registry?
- You cannot manually edit the registry.
- Run the
regeditcommand from the command line. - Double-click the task manager icon
- Expand
regeditfrom the system tray and edit the registry from the GUI.
Explanation & Hint: The statement that best describes the process for editing the Windows Registry is:
Run the
regeditcommand from the command line.The Windows Registry can be edited using the
regeditcommand, which opens the Registry Editor, allowing users to make changes to the system’s registry. Editing the registry should be done with caution, as it can affect the stability and functionality of the operating system, so it’s important to be knowledgeable about the changes you’re making and to back up the registry before making any modifications.
-
What netstat command would best allow an administrator to determine the service responsible for a listening socket?
sudo netstat -tnsudo netstat -lnpnetstat -tnnetstat lnp
Explanation & Hint: The
netstatcommand that would best allow an administrator to determine the service responsible for a listening socket, including the associated process, is:sudo netstat -lnpThe
-lflag shows listening sockets, the-nflag displays numerical addresses and ports, and the-pflag shows the associated process and its process ID (PID). By running this command with superuser privileges (sudo), you can see the service responsible for each listening socket, as well as the process associated with it.
-
An administrator believes that an attacker is overwhelming a database server by causing intensive queries to be run. Which log file should the administrator check first?
/var/log/mysql/mysql.log/var/log/mysql/mysql_error.log/var/log/mysql/mysql_warning.log/var/log/mysql/mysql-slow.log
Explanation & Hint: To check for intensive queries and performance-related issues on a MySQL database server, the administrator should check the
/var/log/mysql/mysql-slow.logfile. Themysql-slow.logcontains records of slow queries, which can help identify and address performance problems caused by resource-intensive or inefficient queries running on the database server.
-
What command would you use to save a packet capture in PCAP format?
sudo tcpdump -s 0 -n >evidence.pcapsudo tcpdump -s 0 -n >>evidence.pcapsudo tcpdump -s 0 -n -w evidence.pcapsudo tcpdump -s 0 -n --writeevidence.pcap
Explanation & Hint: The command you would use to save a packet capture in PCAP format is:
sudo tcpdump -s 0 -n -w evidence.pcapThe
-woption is used to specify the output file in PCAP format, and in this case, it’s named “evidence.pcap.” This command captures network traffic, and the captured packets are written to the specified file in PCAP format.
-
What is the most efficient Linux command for determining whether there is a running process named runme?
- netstat –a > runme
- netstat –a < runme
- netstat –a | grep runme
- ps -ef > runme
- ps -ef < runme
- ps –ef | grep runme
Explanation & Hint: The most efficient Linux command for determining whether there is a running process named “runme” is:
ps -ef | grep runmeThis command lists all processes using the
pscommand and then pipes the output togrep, which searches for the process name “runme” in the list. If there is a running process named “runme,” it will be displayed in the output.
-
Given the following netstat output, which three statements about the local machine are true? (Choose three.)
Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN tcp 0 0 192.168.0.254:49536 203.0.113.77:80 ESTABLISHED
- It is acting as an HTTP client.
- It is acting as an HTTP server.
- It is acting as an SSH server.
- It is acting as an SSH client.
- It is hosting a service that is accessible on all interfaces.
Explanation & Hint: From the provided
netstatoutput, the following three statements about the local machine are true:- It is acting as an SSH server.
- The first line indicates that the local machine is listening on port 22, which is the default port for SSH. Therefore, it is acting as an SSH server.
- It is acting as an HTTP client.
- The second line shows an established connection from the local machine (192.168.0.254) to a remote host on port 80, which is commonly used for HTTP. This indicates that the local machine is acting as an HTTP client.
- It is hosting a service that is accessible on all interfaces.
- The first line specifies the local address as “0.0.0.0,” which means that the service (SSH server) is bound to all network interfaces and is accessible from any network interface. Therefore, it is hosting a service accessible on all interfaces.
The other two statements about acting as an HTTP server and acting as an SSH client are not supported by the given
netstatoutput. - It is acting as an SSH server.
-
What are the two primary Linux processes that are used for managing services? (Choose two.)
- System V init
- Systemd
- Task Manager
- Service Control Manager
Explanation & Hint: The two primary Linux processes used for managing services are:
- System V init: System V init is a traditional init system used in many older Linux distributions. It is responsible for initializing the system and starting and stopping services. However, it has been largely replaced by more modern init systems like systemd.
- Systemd: Systemd is a modern init system used in many current Linux distributions. It is a comprehensive init and service management system that is responsible for starting, stopping, and managing services. It has become the standard for managing services on most Linux systems.
“Task Manager” and “Service Control Manager” are terms more commonly associated with Windows operating systems, and they are not part of the primary service management processes in Linux.
-
Which file is an executable used to troubleshoot DNS issues?
- /etc/hosts
- /usr/bin/nslookup
- /bin/resolve
- /sys/domain/lookup
Explanation & Hint: The executable used to troubleshoot DNS (Domain Name System) issues on a Linux system is typically
/usr/bin/nslookupor a similar utility likedig. These tools allow you to query DNS servers to obtain information about domain names, IP addresses, and various DNS records, which is essential for troubleshooting and diagnosing DNS-related problems.The other paths and files mentioned do not serve as primary DNS troubleshooting tools. The
/etc/hostsfile is used for local hostname-to-IP address resolution, and the other paths mentioned are not standard utilities for DNS troubleshooting.
-
Given the ls command output that is shown below, what command will permit only the user owner and members of the “staff” group to read or modify the testpcap file?
$ ls -l test -rw-r--r-- 1 jdoe staff 57 Nov 3 10:13 testpcap
chmod 660 testpcapchmod 550 testpcapchmod o+rw testpcapchmod staff+rw testpcap
Explanation & Hint: To permit only the user owner (jdoe) and members of the “staff” group to read or modify the
testpcapfile, you should use thechmodcommand as follows:chmod 660 testpcapThis command sets the permissions as follows:
6: Read and write permission for the user owner (jdoe).6: Read and write permission for the members of the “staff” group.0: No permission for others (those not the owner or in the “staff” group).
So, with these permissions, the user owner (jdoe) and members of the “staff” group can read and modify the file, while others have no access.
-
Which of the following is the most appropriate structure of an LDAP entry?
- cn=bobsmith,dc=cisco,dc=com
- dc=bobsmith,cn=cisco,cn=com
- cn=bob,cn=smith,dc=cisco.com
- dc=bob,dc=smith,cn=cisco.com
Explanation & Hint: The most appropriate structure of an LDAP (Lightweight Directory Access Protocol) entry is typically in the form:
cn=bobsmith,dc=cisco,dc=com
In this structure:
cnrepresents the Common Name attribute, often used for the name of the entry or the person’s name.dcrepresents the Domain Component attribute, which is used to structure the directory in a hierarchical manner.
This format adheres to the common LDAP naming conventions where the Common Name (cn) is typically associated with the individual’s or entity’s name, and the Domain Component (dc) is used to represent the domain components in a hierarchical structure.
-
How would you copy a file that is called evidence from the local system to a Linux host at 192.168.1.33?
scp evidence user@192.168.1.33:evidencescp user@192.168.1.33:evidence evidencessh evidence user@192.168.1.33:evidencessh user@192.168.1.33:evidence evidence
Explanation & Hint: To copy a file called “evidence” from the local system to a Linux host at 192.168.1.33, you should use the
scp(Secure Copy Protocol) command with the correct syntax. The correct command is:scp evidence user@192.168.1.33:This command will copy the “evidence” file from the local system to the home directory of the user on the remote Linux host at IP address 192.168.1.33. The remote filename will remain the same, “evidence.”
-
A junior analyst is trying to use the
tcpdump –i eth1command on an Ubuntu system, but it is not working. What could be the problem?- The
tcpdumpcommand requires root level privilege. - The
tcpdumpcommand requires the Ethernet adapter to be in non-promiscuous mode. - The
tcpdumpcommand–ioption used to specify the interface is an invalid option. - The
tcpdumpcommand used is missing some of the required options (such as –n and –v).
Explanation & Hint: The most likely issue is that:
The
tcpdumpcommand requires root-level privilege.Running
tcpdumptypically requires superuser (root) privileges because it involves capturing and analyzing network packets, which is a sensitive operation. You can usesudoto runtcpdumpwith elevated privileges:sudo tcpdump -i eth1The other options mentioned are not common reasons for the
tcpdumpcommand to fail. In fact, specifying the interface with the-ioption is valid, and the-nand-voptions are not required for the basic operation oftcpdump. The Ethernet adapter being in non-promiscuous mode doesn’t typically preventtcpdumpfrom running.
- The
-
When a host name is being translated to an IP address, where will the operating system look first?
- /etc/hosts
- /etc/hostname
- /etc/resolv.conf
- It depends on the configuration of /etc/nsswitch.conf.
Explanation & Hint: When a host name is being translated to an IP address, the operating system will typically look first in the
/etc/hostsfile. This file is used to specify static mappings of host names to IP addresses and is checked before other methods.The order in which the operating system looks up host name resolutions may be influenced by the configuration specified in the
/etc/nsswitch.conffile, which defines the order of sources for name service lookups, such as/etc/hosts, DNS, and other methods. The order can be customized innsswitch.conf, but by default,/etc/hostsis usually the first place checked for host name resolution.
-
If the parent process is terminated before its children, what will the PPID column show in the ps command?
- N/A
- –
- 0
- 1
Explanation & Hint: If the parent process is terminated before its children, the PPID (Parent Process ID) column in the
pscommand will typically show 1.In Unix-like operating systems, when a parent process terminates before its children, the orphaned child processes are typically adopted by the init process, which has a process ID (PID) of 1. As a result, the PPID of these orphaned child processes becomes 1 to indicate that they are now under the care of the init process.
-
Where is the sda block device stored in the file system?
- /sys
- /dev
- /proc
- /tmp
Explanation & Hint: The
sdablock device is typically stored in the/devdirectory in the file system. In Unix-like operating systems,/devis where device files representing various hardware devices, including hard drives and partitions, are located. Thesdadevice file often represents the first SCSI or SATA hard disk drive in the system.
-
Which method is a permissive security control in which only specified applications can run on an end host, while all other applications are prevented?
- application blocked lists
- application allowed lists
- application deep packets inspection
- application recognition and detection
Explanation & Hint: The method that represents a permissive security control in which only specified applications can run on an end host while all other applications are prevented is:
Application allowed lists.
In this approach, a list of approved or allowed applications is defined, and only those applications on the list are permitted to run. All other applications are blocked or prevented from executing on the end host. This is also sometimes referred to as an “application whitelist.”
-
During incident investigations, what does the AMP for endpoints device trajectory feature show?
- hosts that have seen the malicious file
- the signature that triggered the malicious file alert
- actions that have been performed on the victim’s host
- how the malware file was packed (compressed or encrypted)
Explanation & Hint: The AMP for Endpoints device trajectory feature shows:
Actions that have been performed on the victim’s host.
Device trajectory provides a timeline or history of actions that have occurred on a host, especially actions related to potential security incidents. It allows incident investigators to track and understand the sequence of events on the affected host, which is valuable for identifying and responding to security incidents. This can include information about file activity, process execution, network connections, and other events related to potential threats. The device trajectory feature doesn’t typically show how the malware file was packed or compressed; that information may be available through other analysis tools.
-
When Cisco AMP for Endpoints detects that an unknown file has been received on an endpoint, what does it do with the file?
- submits the file to the cloud for future analysis
- deletes the file
- executes the file to determine if it is malicious or not
- performs a file trajectory to determine which other systems have seen the same file
Explanation & Hint: When Cisco AMP for Endpoints detects that an unknown file has been received on an endpoint, it typically submits the file to the cloud for future analysis. This allows the system to analyze the file and determine its nature, whether it’s malicious or not. The cloud-based analysis can include running the file in a sandboxed environment to assess its behavior and potential threats. The analysis results can then be used to make informed decisions about the file’s reputation and whether it poses a security risk.
-
After a file disposition changes from unknown to malicious, what is the next step that should be taken?
- Run the file in a sandbox to verify if it is malicious and to determine the file behaviors.
- Create a new IPS signature to detect the malicious file.
- Go back to the system where the file was previously seen and quarantine the malicious file.
- Run a file retrospective analysis in the cloud using machine learning to determine the file SHA.
Explanation & Hint: After a file disposition changes from unknown to malicious in a security system like Cisco AMP for Endpoints, the next step that should be taken is to go back to the system where the file was previously seen and quarantine the malicious file.
Quarantining the file helps prevent it from causing further harm within the network or on the affected system. The file can be isolated and prevented from executing, spreading, or causing damage. After the file is quarantined, further investigation and analysis may be conducted to understand the scope of the incident and take appropriate remediation steps.
-
What can a HIPS do that a NIPS cannot? (Choose two.)
- Detect malware delivered to the host via an encrypted channel.
- Protect a mobile host while connected to non-secured networks.
- Block malware as it is carried across the network.
- Inspect traffic crossing a link in the network.
Explanation & Hint: Host Intrusion Prevention Systems (HIPS) and Network Intrusion Prevention Systems (NIPS) serve different roles in network security. Here are two things that a HIPS can do that a NIPS cannot:
Detect malware delivered to the host via an encrypted channel:
- HIPS is positioned on the host itself and can inspect the activities and behavior of processes running on the host, regardless of whether the communication is encrypted or not. It can detect malware that might be delivered to the host via an encrypted channel, such as through encrypted connections or downloads.
Protect a mobile host while connected to non-secured networks:
- HIPS provides security protection directly on the host, making it suitable for protecting mobile hosts (e.g., laptops, smartphones) even when they are connected to non-secured or untrusted networks. It can monitor and defend against threats at the endpoint, which is valuable for devices that are frequently used outside of secure network environments.
NIPS, on the other hand, is primarily focused on network traffic inspection and monitoring for threats crossing the network links, so it may not have the same level of visibility or control over the host as a HIPS does. It excels at blocking malware as it traverses the network, inspecting traffic on the network wire or in transit.
-
File integrity checking tools work by calculating hash values of important files, storing the hash values, and periodically comparing those hash values to hash values that it calculates later. If a file hash value comparison results in a mismatch, what does that indicate?
- It means nothing; it is a mismatch because the files hashes were compiled on different days.
- It means that one file did not calculate correctly and need to be recalculated.
- It indicates that the file has been changed in some way and there may be an issue to be resolved.
- It indicates that your organization has suffered a security breach and a full-scale investigation is needed as soon as possible.
Explanation & Hint: If a file hash value comparison results in a mismatch, it typically indicates that:
The file has been changed in some way, and there may be an issue to be resolved.
File integrity checking tools are used to detect unauthorized or unintended changes to files. When the hash value of a file no longer matches the stored or expected hash value, it suggests that the file has been altered since the last hash calculation was performed. This can be an important indicator of file tampering or corruption, and further investigation is typically warranted to determine the cause of the mismatch and to take appropriate action, which may include restoring the original file from a known good source or investigating for potential security breaches.
-
What is the primary difference between a host-based firewall and a traditional firewall?
- The host-based firewall can block traffic based on application or file type.
- The traditional firewall can identify and protect against malicious HTTP exploits.
- There is no difference between the functional aspects of host-based and traditional firewalls.
- Host-based firewalls protect an individual machine while traditional firewalls control traffic arriving at and leaving networks.
Explanation & Hint: The primary difference between a host-based firewall and a traditional firewall is:
Host-based firewalls protect an individual machine while traditional firewalls control traffic arriving at and leaving networks.
- Host-based firewall: This type of firewall is installed on a specific host or individual machine and protects that host from unwanted network traffic. It operates at the host level and can block or allow traffic based on the rules and policies configured specifically for that host. Host-based firewalls are primarily designed to protect the local machine from malicious activities.
- Traditional firewall: Traditional firewalls are network-level devices or software solutions that control traffic between different network segments or between an internal network and external networks, like the internet. They primarily focus on controlling traffic that arrives at and leaves the network as a whole. They are responsible for filtering and managing traffic based on predefined rules and policies for the entire network, rather than for individual hosts.
So, the key distinction is in the scope of protection and control: host-based firewalls are focused on individual hosts, while traditional firewalls are network-wide.
-
Which statement is true about sandboxing?
- Using a sandbox technique ensures that no malware infected files can get in the network.
- Running a file in a sandbox guarantees that the disposition will show the threat that it poses to your environment.
- Malware authors deploy several techniques to bypass sandbox analysis.
- Using a sandbox replaces the need for expensive antivirus and firewall software.
Explanation & Hint: The statement that is true about sandboxing is:
Malware authors deploy several techniques to bypass sandbox analysis.
Sandboxing is a security technique that isolates and runs untrusted or potentially malicious code in a controlled environment to analyze its behavior and potential threats. However, malware authors are aware of sandboxing techniques and have developed various evasion and detection avoidance mechanisms to make it more difficult for sandbox environments to detect and analyze their malware. These evasion techniques may include checks for the presence of typical sandbox indicators, delays in malicious activities, and other tactics to bypass or confuse sandbox analysis.
The other statements are not accurate:
- Using a sandbox technique does not guarantee that no malware-infected files can enter the network; it helps with analysis but doesn’t prevent all infections.
- Running a file in a sandbox doesn’t guarantee the disposition; it provides analysis and behavioral insight, but the disposition depends on the analysis results.
- Using a sandbox doesn’t replace the need for antivirus and firewall software; it’s a complementary security measure.
-
An end user’s host becomes infected with a virus because the end user browsed to a malicious website. Which endpoint security technology can be used to best prevent such an incident?
- personal firewall
- personal antivirus
- endpoint malware protection
- file sandboxing
- file integrity checks
Explanation & Hint: To best prevent an incident where an end user’s host becomes infected with a virus from a malicious website, the most relevant endpoint security technology is:
Personal antivirus.
Personal antivirus software is specifically designed to detect and prevent a wide range of malware threats, including viruses, Trojans, worms, and other malicious software that can be encountered while browsing the web or downloading files. It can provide real-time scanning and protection to detect and block threats before they infect the host. While other security technologies like personal firewalls and file sandboxing can be important, personal antivirus is particularly focused on identifying and mitigating viruses and malware that can be encountered while browsing the internet.
-
Which endpoint security technology should be used to prevent any incoming connections to the host?
- host-based personal firewall
- host-based antivirus
- host-based IDS
- host-based malware protection
Explanation & Hint: To prevent any incoming connections to a host, the most appropriate endpoint security technology to use is:
Host-based personal firewall.
A host-based personal firewall is designed to control and restrict network connections to and from an individual host. It can be configured to block incoming connections and traffic, providing protection against unauthorized access and potential threats. This is especially important for preventing unauthorized or malicious incoming connections to the host. Host-based personal firewalls allow users to define rules and policies to control network access, making them an effective choice for this purpose.