3.8.8 Lab – Explore DNS Traffic Answers
Lab – Explore DNS Traffic (Answers Version)
Answers Note: Red font color or gray highlights indicate text that appears in the instructor copy only.
Objectives
Part 1: Capture DNS Traffic
Part 2: Explore DNS Query Traffic
Part 3: Explore DNS Response Traffic
Background / Scenario
Wireshark is an open source packet capture and analysis tool. Wireshark gives a detailed breakdown of the network protocol stack. Wireshark allows you to filter traffic for network troubleshooting, investigate security issues, and analyze network protocols. Because Wireshark allows you to view the packet details, it can be used as a reconnaissance tool for an attacker.
In this lab, you will install Wireshark on a Windows system and use Wireshark to filter for DNS packets and view the details of both DNS query and response packets.
Required Resources
- 1 Windows PC with internet access and Wireshark installed
Answers Note: Using a packet sniffer such as Wireshark may be considered a breach of the security policy of the school. It is recommended that permission is obtained before running Wireshark for this lab. If using a packet sniffer such as Wireshark is an issue, the instructor may wish to assign the lab as homework or perform a walk-through demonstration.
Instructions
Step 1: Capture DNS traffic.
- Open Wireshark and start a Wireshark capture by double clicking a network interface with traffic.
- At the Command Prompt, enter ipconfig /flushdns clear the DNS cache.
C:\Users\Student> ipconfig /flushdns
Windows IP Configuration
Successfully flushed the DNS Resolver Cache.
- Enter nslookup at the prompt to enter the nslookup interactive mode.
- Enter the domain name of a website. The domain name www.cisco.com is used in this example. Enter www.cisco.com at the > prompt.
C:\Users\Student> nslookup
Default Server: UnKnown
Address: 68.105.28.16
> www.cisco.com
Server: UnKnown
Address: 68.105.28.16
Non-authoritative answer:
Name: e2867.dsca.akamaiedge.net
Addresses: 2001:578:28:68d::b33
2001:578:28:685::b33
96.7.79.147
Aliases: www.cisco.com
www.cisco.com.akadns.net
wwwds.cisco.com.edgekey.net
wwwds.cisco.com.edgekey.net.globalredir.akadns.net
- Enter exit when finished to exit the nslookup interactive mode. Close the command prompt.
- Click Stop capturing packets to stop the Wireshark capture.
Step 2: Explore DNS Query Traffic
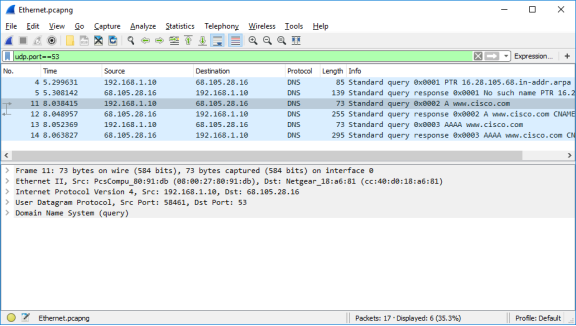
- Observe the traffic captured in the Wireshark Packet List pane. Enter udp.port == 53 in the filter box and click the arrow (or press enter) to display only DNS packets.
- Select the DNS packet labeled Standard query 0x0002 A www.cisco.com.
In the Packet Details pane, notice this packet has Ethernet II, Internet Protocol Version 4, User Datagram Protocol and Domain Name System (query).
- Expand Ethernet II to view the details. Observe the source and destination fields.
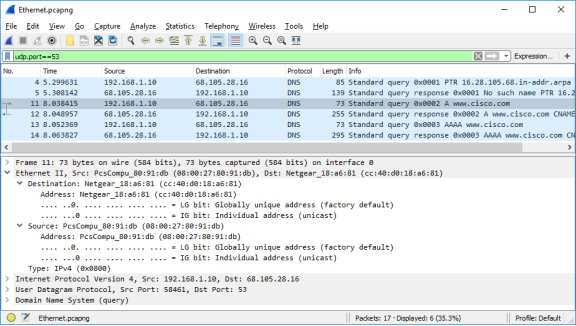
Question:
What are the source and destination MAC addresses? Which network interfaces are these MAC addresses associated with?
Type your answers here.
In this example, the source MAC address is associated with the NIC on the PC and the destination MAC address is associated with the default gateway. If there is a local DNS server, the destination MAC address would be the MAC address of the local DNS server.
- Expand Internet Protocol Version 4. Observe the source and destination IPv4 addresses.
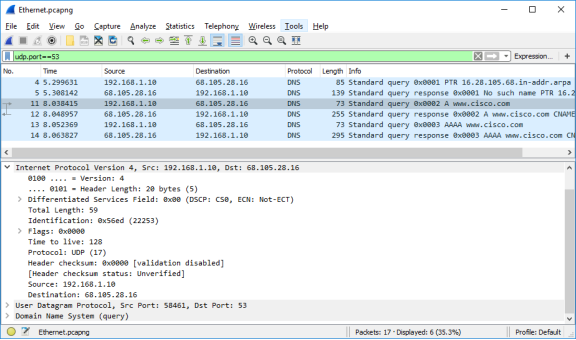
Question:
What are the source and destination IP addresses? Which network interfaces are these IP addresses associated with?
Type your answers here.
In this example, the source IP address is associated with the NIC on the PC and the destination IP address is associated with the DNS server.
- Expand the User Datagram Protocol. Observe the source and destination ports.
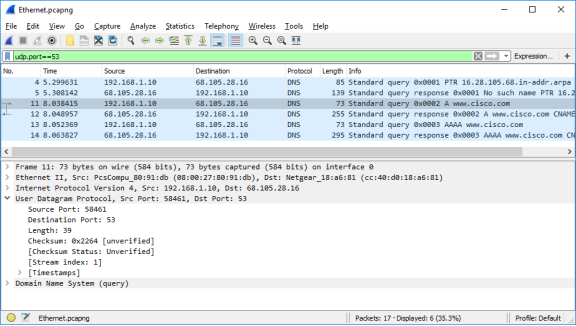
Question:
What are the source and destination ports? What is the default DNS port number?
Type your answers here.
The source port number is 58461 and the destination port is 53, which is the default DNS port number.
- Open a Command Prompt and enter arp –a and ipconfig /all to record the MAC and IP addresses of the PC.
C:\Users\Student> arp -a
Interface: 192.168.1.10 — 0x4
Internet Address Physical Address Type
192.168.1.1 cc-40-d0-18-a6-81 dynamic
192.168.1.122 b0-a7-37-46-70-bb dynamic
192.168.1.255 ff-ff-ff-ff-ff-ff static
224.0.0.22 01-00-5e-00-00-16 static
224.0.0.252 01-00-5e-00-00-fc static
239.255.255.250 01-00-5e-7f-ff-fa static
255.255.255.255 ff-ff-ff-ff-ff-ff static
C:\Users\Studuent> ipconfig /all
Windows IP Configuration
Host Name . . . . . . . . . . . . : DESKTOP
Primary Dns Suffix . . . . . . . :
Node Type . . . . . . . . . . . . : Hybrid
IP Routing Enabled. . . . . . . . : No
WINS Proxy Enabled. . . . . . . . : No
Ethernet adapter Ethernet:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Intel(R) PRO/1000 MT Desktop Adapter
Physical Address. . . . . . . . . : 08-00-27-80-91-DB
DHCP Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
Link-local IPv6 Address . . . . . : fe80::d829:6d18:e229:a705%4(Preferred)
IPv4 Address. . . . . . . . . . . : 192.168.1.10(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Lease Obtained. . . . . . . . . . : Tuesday, August 20, 2019 5:39:51 PM
Lease Expires . . . . . . . . . . : Wednesday, August 21, 2019 5:39:50 PM
Default Gateway . . . . . . . . . : 192.168.1.1
DHCP Server . . . . . . . . . . . : 192.168.1.1
DHCPv6 IAID . . . . . . . . . . . : 50855975
DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-24-21-BA-64-08-00-27-80-91-DB
DNS Servers . . . . . . . . . . . : 68.105.28.16
68.105.29.16
NetBIOS over Tcpip. . . . . . . . : Enabled
Question:
Compare the MAC and IP addresses in the Wireshark results to the results from the ipconfig /all results. What is your observation?
Type your answers here.
The IP and MAC addresses captured in the Wireshark results are the same as the addresses listed in arp – a and ipconfig /all command.
- Expand Domain Name System (query) in the Packet Details pane. Then expand the Flags and Queries.
Observe the results. The flag is set to do the query recursively to query for the IP address to www.cisco.com.
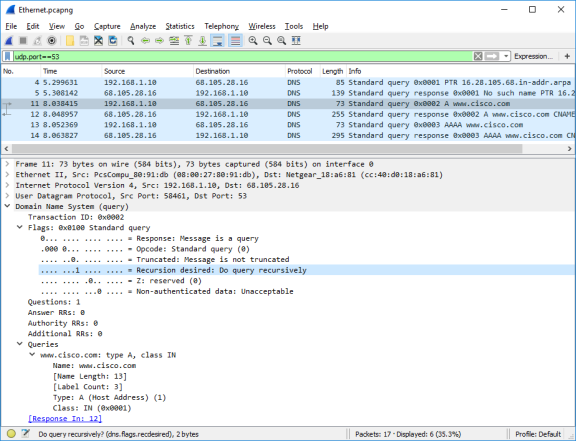
Step 3: Explore DNS Response Traffic
- Select the corresponding response DNS packet labeled Standard query response 0x0002 A www.cisco.com.
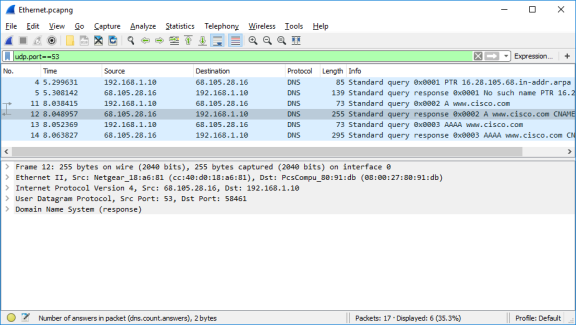
Questions:
What are the source and destination MAC and IP addresses and port numbers? How do they compare to the addresses in the DNS query packets?
Type your answers here.
The source IP, MAC address, and port number in the query packet are now destination addresses. The destination IP, MAC address, and port number in the query packet are now source addresses.
- Expand Domain Name System (response). Then expand the Flags, Queries, and Answers. Observe the results.
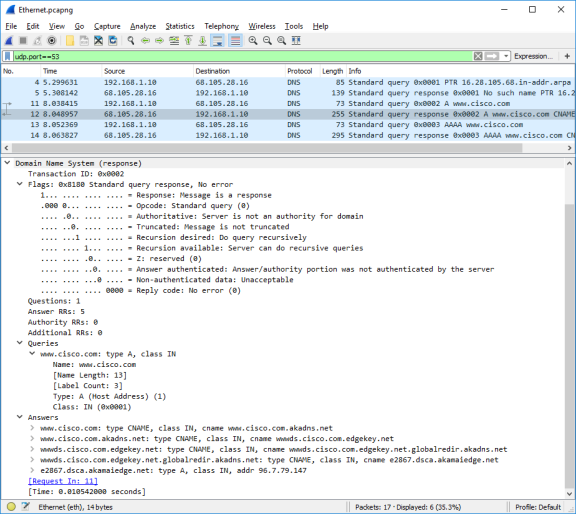
Question:
Can the DNS server do recursive queries?
Type your answers here.
Yes, the DNS can handle recursive queries.
- Observe the CNAME and A records in the answers details.
Question:
How do the results compare to nslookup results?
Type your answers here.
The results in the Wireshark should be the same as the results from nslookup in the Command Prompt.
Reflection Question
- From the Wireshark results, what else can you learn about the network when you remove the filter?
Type your answers here.
Without the filters, the results display other packets, such as DHCP and ARP. From these packets and the information contained within these packets, you can learn about other devices and their functions within the LAN.
- How can an attacker use Wireshark to compromise your network security?
Type your answers here.
An attacker on the LAN can use Wireshark to observe the network traffic and can get sensitive information in the packet details if the traffic is not encrypted.