DevNet Associate (Version 1.0) – DevNet Associate 1.01 Practice Final Exam Answers 2025 Full 100%
DevNet Associate (Version 1.0) – DevNet Associate 1.01 Practice Final Exam Answers 2025 Full 100% 2025
This is a collection of Cisco NetAcad DevNet Associate (Version 1.0), DevNet Associate 1.01, and DEVASC 1.01 for Practice Final Exam Answers Full 100% in 2025. Our team expert has made this series for putting all on one page to be easy to navigate and learn. This DevNet Associate Practice Final exam answer is for the Cisco Netacad learning platform. Review all questions and answers before you take the exam to get a full mark of 100%.
| DevNet - DEVASC 1.0 | |
| Final Exam | |
| Practice Final Exam Answers | Online Test |
| Final Exam Answers | Online Test |
| 200-901 Certification Practice Exam | Online Test |
DevNet Associate (Version 1.0) – DevNet Associate 1.01 Practice Final Exam Answers Full 100% 2025
-
When working with both a live production environment and testing code in a shared developer sandbox, what are two important rules to follow? (Choose two.)
- Never use any personal tokens in the sandbox, but instead use a customized token for development.
- Never use a customized token in the sandbox, but instead use personal tokens that currently exist.
- Never use publicly posted tokens or credentials in a production environment.
- Never provide any identifying information in community or public environments.
- Never request assistance or share information in community or public environments.
Explanation & Hint: When working in a learning environment or community-based environment, remember never to use any personal tokens or credentials in the sandbox. Also, do not use tokens or credentials provided in a course or online community in a production environment. It is important to be protective of tokens, passwords, and other identifying information in development environments.
-
What are the two types of DevNet Sandboxes? (Choose two.)
- always-on
- reserved
- assigned
- exclusive
- internal-use only
Explanation & Hint: The two types of DevNet Sandboxes include always-on and reserved. An “always-on” sandbox is available to anyone and typically provides read-only access. A reserved Cisco DevNet Sandbox has shared resources with a quota setting and uses a VPN connection so that traffic to and from the sandbox and development environment is protected.
-
Which fee-based Cisco DevNet developer support option provides a response time of 1 business day?
- chat with DevNet
- case-based ticket
- knowledge base
- community forum
Explanation & Hint: Case-based tickets provide 1-on-1 support for certain Cisco APIs. The response time is commonly 1 business day and the cost varies based on the amount of case-based tickets purchased.
-
Which DevNet resource would a student use to learn how to make REST API requests?
- DevNet Sandbox
- Code Exchange
- DevNet Support
- DevNet Learning Labs
Explanation & Hint: DevNet provides a catalog of free, self-paced online tutorials called Learning Labs.
-
Which two forums are available on the Cisco Developer Community? (Choose two.)
- Developer Networking
- Developer Coding
- Developer Automation
- Developer Security
- Developer Support
Explanation & Hint: There are a total of ten developer forums on the Cisco Developer Community:
Developer Networking
Developer Collaboration
Developer Security
Developer Data Center
Developer Internet of Things
Developer Cloud
Developer Services
Developer Mobility
Developer Analytics and Automation Software
Developer DevNet Site
-
In which phase of the SDLC process does the product development team gather feedback from the potential customer on the desired features for the new software?
- requirements and analysis
- design
- implementation
- deployment
Explanation & Hint: The first phase of the SDLC is the requirements and analysis phase. In this phase the product owner and qualified team members, using feedback from potential customers, gather the requirements for the software to be built.
-
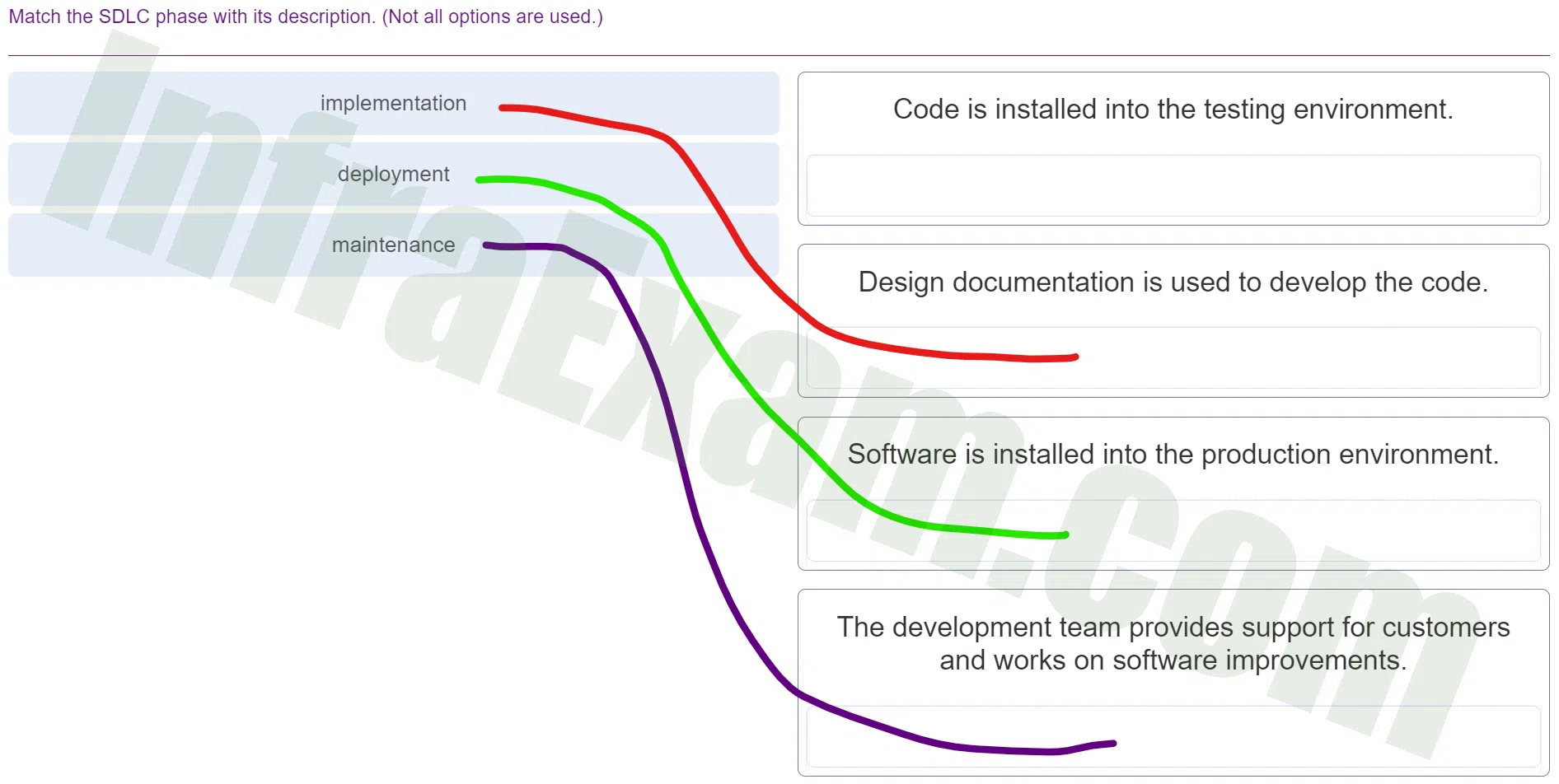
Match the SDLC phase with its description. (Not all options are used.)
DevNet Associate (Version 1.0) – DevNet Associate 1.01 Practice Final Exam Answers 001 - implementation ==> Design documentation is used to develop the code.
- deployment ==> Software is installed into the production environment.
- maintenance ==> The development team provides support for customers and works on software improvements.
Explanation & Hint: Implementation:
- Description: Design documentation is used to develop the code.
- Explanation: During the Implementation phase of the SDLC, the design specifications and plans developed in the previous phases (such as requirements analysis and design) are put into action. In this phase, programmers or developers write the actual code based on the design documentation. The implementation phase focuses on translating the design into executable code while adhering to coding standards, best practices, and the software architecture.
Deployment:
- Description: Software is installed into the production environment.
- Explanation: The Deployment phase marks the transition of the software from the development environment to the production environment, making it available for end-users. This involves tasks such as installing the software, configuring servers, setting up databases, and ensuring that the application runs smoothly in the live environment. It’s a critical phase where careful planning and testing are essential to minimize disruptions and ensure a successful launch.
Maintenance:
- Description: The development team provides support for customers and works on software improvements.
- Explanation: The Maintenance phase of the SDLC involves ongoing activities after the software has been deployed. This phase includes providing support to customers, addressing issues, fixing bugs, and making improvements to the software based on user feedback and changing requirements. Maintenance can be divided into corrective (fixing defects), adaptive (adapting to changes in the environment), perfective (enhancing features), and preventive (proactively preventing issues) activities.
These SDLC phases collectively guide the development process from initial concept to deployment and beyond. They ensure a structured approach to software development, helping teams produce high-quality software that meets user needs and expectations.
-
An organization is using the Waterfall methodology for a software development project. In what order are the SDLC phases completed when using this method?
- requirements and analysis, design, implementation, testing, deployment, maintenance
- requirements and analysis, design, implementation, deployment, testing, maintenance
- requirements and analysis, design, testing, implementation, deployment, maintenance
- requirements and analysis, design, deployment, testing, implementation, maintenance
Explanation & Hint: The Software Development Life Cycle (SDLC) is the process of developing software from concept to final product. The process consists of six phases, with each phase using the results of the previous phase as input. The phases are ordered as follows: (1) requirements & analysis, (2) design, (3) implementation, (4) testing, (5) deployment, and (6) maintenance.
-
Which SDLC phase concludes with a high quality, bug-free, working piece of software that is ready for production?
- testing
- design
- implementation
- deployment
Explanation & Hint: There are six phases in the SDLC process:
- Requirements & analysis : The product owner and qualified team members gather the requirements for the software to be built.
- Design : Software architects and developers design the software based on the provided software requirement specification document.
- Implementation : Developers take the design documentation and develop the code according to that design.
- Testing : Test engineers take the code and install it into the testing environment so that they can follow the test plan.
- Deployment : The software is installed into the production environment.
- Maintenance : The development team provides support for customers and works on software improvements.
-
Which terminal command can be used to print the Python version number installed on a system?
- python -V
- python -i
- python -h
- which python
Explanation & Hint: The command python -V can be used from a command or terminal window to view the Python version installed on the system.
-
What is an operational characteristic of the local version control system?
- It stores a delta of two versions of a file as opposed to the file itself.
- It locks a file once it is checked out by a user to prevent modification by others.
- It allows multiple individuals to edit a working copy of a file at the same time.
- It pushes a working copy of a file to a main repository after individuals have made changes.
Explanation & Hint: There are three types of version control systems:
• Local version control system
• Centralized version control system
• Distributed version control system
The local version control system stores the delta between the two versions of the file, as opposed to the file itself. When the user wants to revert to the previous version of the file, the delta is reversed to get to the requested version.
-
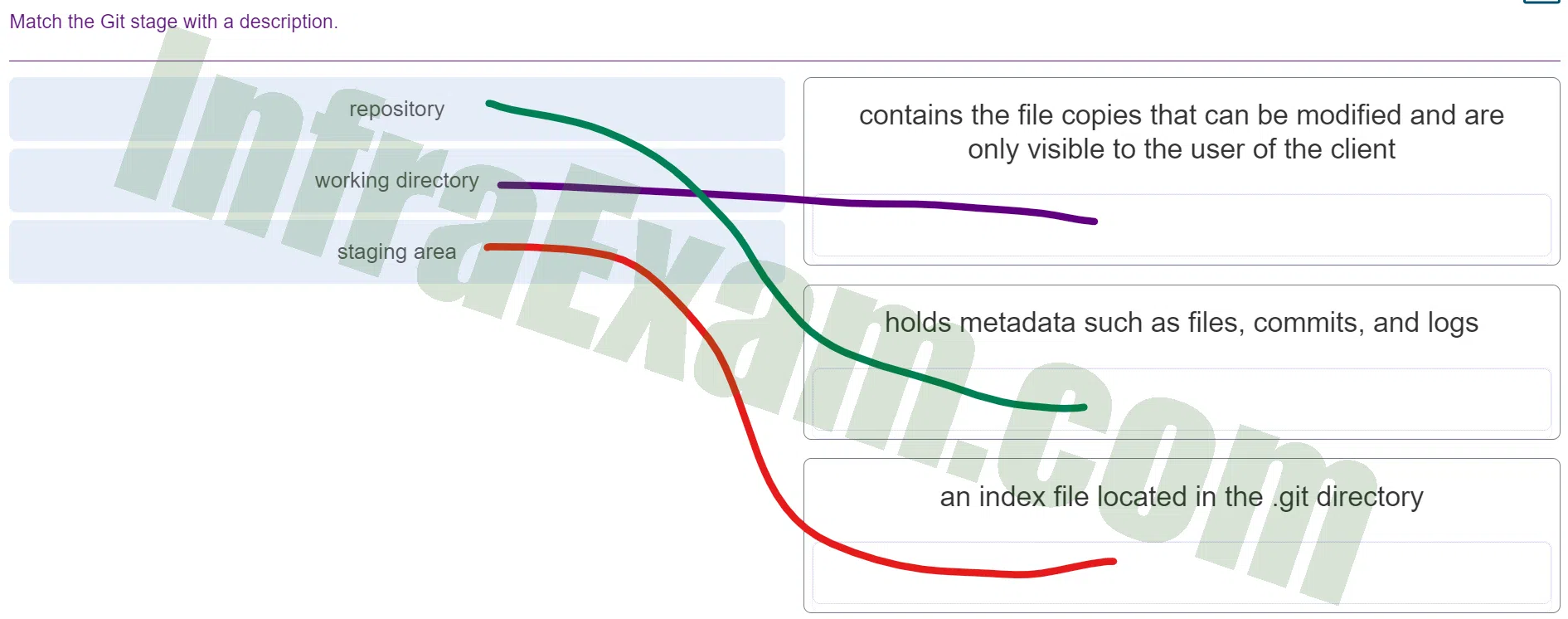
Match the Git stage with a description.
DevNet Associate (Version 1.0) – DevNet Associate 1.01 Practice Final Exam Answers 002 - repository ==> holds metadata such as files, commits, and logs
- working directory ==> contains the file copies that can be modified and are only visible to the user of the client
- staging area ==> an index file located in the .git directory
Explanation & Hint: Repository:
- Description: Holds metadata such as files, commits, and logs.
- Explanation: The repository is the core of Git, where all the project’s files, version history (commits), and related metadata are stored. It represents the complete history and state of the project.
Working Directory:
- Description: Contains the file copies that can be modified and are only visible to the user of the client.
- Explanation: The working directory is where you interact with the actual files in your project. It contains copies of the files from the repository, and you can modify them freely. These changes are only visible to you locally and do not affect the shared project until they’re committed.
Staging Area:
- Description: An index file located in the .git directory.
- Explanation: The staging area (also known as the “index”) is an intermediate step between the working directory and the repository. It’s a place where you can prepare and organize changes before committing them. When you stage changes, you’re selecting which modifications should be included in the next commit. The staging area helps you control what gets saved in the repository.
These Git stages work together to manage and track changes to your project, ensuring a systematic and controlled approach to version control and collaboration.
-
Which Git command is used to get an initial copy on an existing Git repository for the first time?
- git clone
- git repo
- git add
- git copy
Explanation & Hint: The command that you would use for the first copy of an existing Git repository is git clone .
-
A student is learning Python using the interactive interpreter mode. The student issues these commands:
>>> class Url(): ... def __init__(self, host, prot): ... self.host = host ... self.prot = prot ... self.url = self.prot + "://" + self.host ... >>>
Which type of Python structure is created?
- a class
- a module
- a method
- a function
Explanation & Hint: In Python, classes are a means of bundling data storage and functionality in a single structure. Each class declaration defines a new object type. A class is defined with the class Class_Name() command.
-
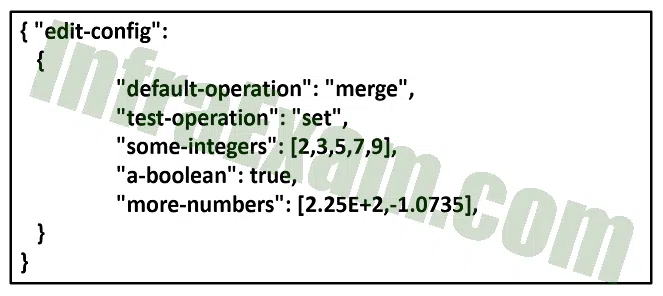
Refer to the exhibit. Which message format is being used?
DevNet Associate (Version 1.0) – DevNet Associate 1.01 Practice Final Exam Answers 01 - JSON
- XML
- HTML
- YAML
Explanation & Hint: JSON objects are unordered sets of name/value pairs that begin and end with curly braces { }.
-
How does YAML maintain data-structure hierarchy?
- indentation
- brackets
- braces
- parenthesis
Explanation & Hint: In YAML the data-structure hierarchy is maintained by outline indentation.
-
Which three characteristics are associated with the SOAP architecture? (Choose three.)
- neutral
- stateless
- extensible
- independent
- layered system
- uniform interface
Explanation & Hint: SOAP architecture has three characteristics:
Independent – different applications can communicate with one another
Extensible – extensions can be added to SOAP because it is an application of XML
Neutral – SOAP can use a variety of protocols including HTTP, SMTP, TCP, UDP, or JMS
-
A network operator is testing a network management application that uses REST API to communicate with network devices. The operator received an HTTP response code 403 in a test step. What does this response code indicate?
- Request failed due to a client-side issue.
- Access is not granted based on supplied credentials.
- Client has not authenticated to access the site or API call.
- The page at HTTP URL location does not exist or is hidden.
Explanation & Hint: Most common HTTP status codes include:
- 200 – OK (using GET or POST to exchange data with an API successfully)
- 201 – Created (creating resources by using a REST API call successfully)
- 400 – Bad Request (The request from the client is failed due to client-side issue.)
- 401 – Unauthorized (The client is not authenticated to access site or API call.)
- 403 – Forbidden (The access request is not granted based on the supplied credentials.)
- 404 – Not Found (The page requested at HTTP URL location does not exist or is hidden.)
-
What are two features of REST APIs? (Choose two.)
- Requests always contain data.
- They communicate over HTTP.
- Responses are always in JSON format.
- They maintain session states in communications.
- They follow the Representational State Transfer principles.
Explanation & Hint: REST APIs are the short name for Representational State Transfer Webservice APIs. They follow the REST architectural style and communicate over HTTP. REST API requests and responses can use many different data formats; it is not mandatory to use JSON. It is also not mandatory for requests or responses to contain data. Data is provided when applicable. Communication using REST APIs is stateless.
-
Which three authentication mechanisms are used in REST APIs? (Choose three.)
- SSO
- OAuth
- API Key
- open authentication
- basic authentication
- bearer authentication
Explanation & Hint: For security reasons, most REST APIs require authentication to prevent random users from being able to create, update, or delete information incorrectly or maliciously. Basic Authentication, Bearer Authentication, and API Key are authentication mechanisms used by REST APIs. OAuth is an authorization mechanism.
-
A client is using an API key to authenticate and access resources on a website through a REST API. The string in the API request is GET http://example.com:8080/v1/books?API_KEY= < key >. Which component in the API request is used to provide this string?
- cookie
- header
- body data
- query string
Explanation & Hint: A REST API request can provide an API key in a few different ways including query string, header, body data, and cookie. In this case, the API key is provided through the query string that is preceded with a symbol ? .
-
What are two advantages of using an API rate limit? (Choose two.)
- It protects against a DoS attack.
- It reduces the amount of overhead within the API request.
- It provides better quality of service and response time.
- It supports token passing so that each client gets a turn.
- It allows requests to be processed in a prioritized manner.
Explanation & Hint: An API rate limit allows a web service to control the number of requests made in a defined amount of time and is a best practice to use for public and unrestricted APIs. Benefits of using rate limits include the following:
Avoids a server overload from too many requests at once
Provides better service and response time to all users
Protects against a denial of service (DoS) attack
-
Refer to the exhibit. A student is learning network automation with Python and REST API. The student constructs a small Python script to get information from a local network device. The device is a sandbox located inside the college lab and it is using a self-signed SSL certificate. Which parameter is needed in the Python code (in place of the question mark) to skip the SSL verification?
DevNet Associate (Version 1.0) – DevNet Associate 1.01 Practice Final Exam Answers 02 - verify = NO
- verify = YES
- verify = True
- verify = False
Explanation & Hint: When the protocol used within the URI is HTTPS, the connection will perform an SSL handshake between the client and the server for secure authentication. This handshake needs to be successful before the REST API request is even sent to the API server. However, because the SSL is self-signed, it would not pass the SSL verification with a CA. In the case of learning and practicing on a local resource, the SSL verification can be turned off by the “verify = False” parameter.
-
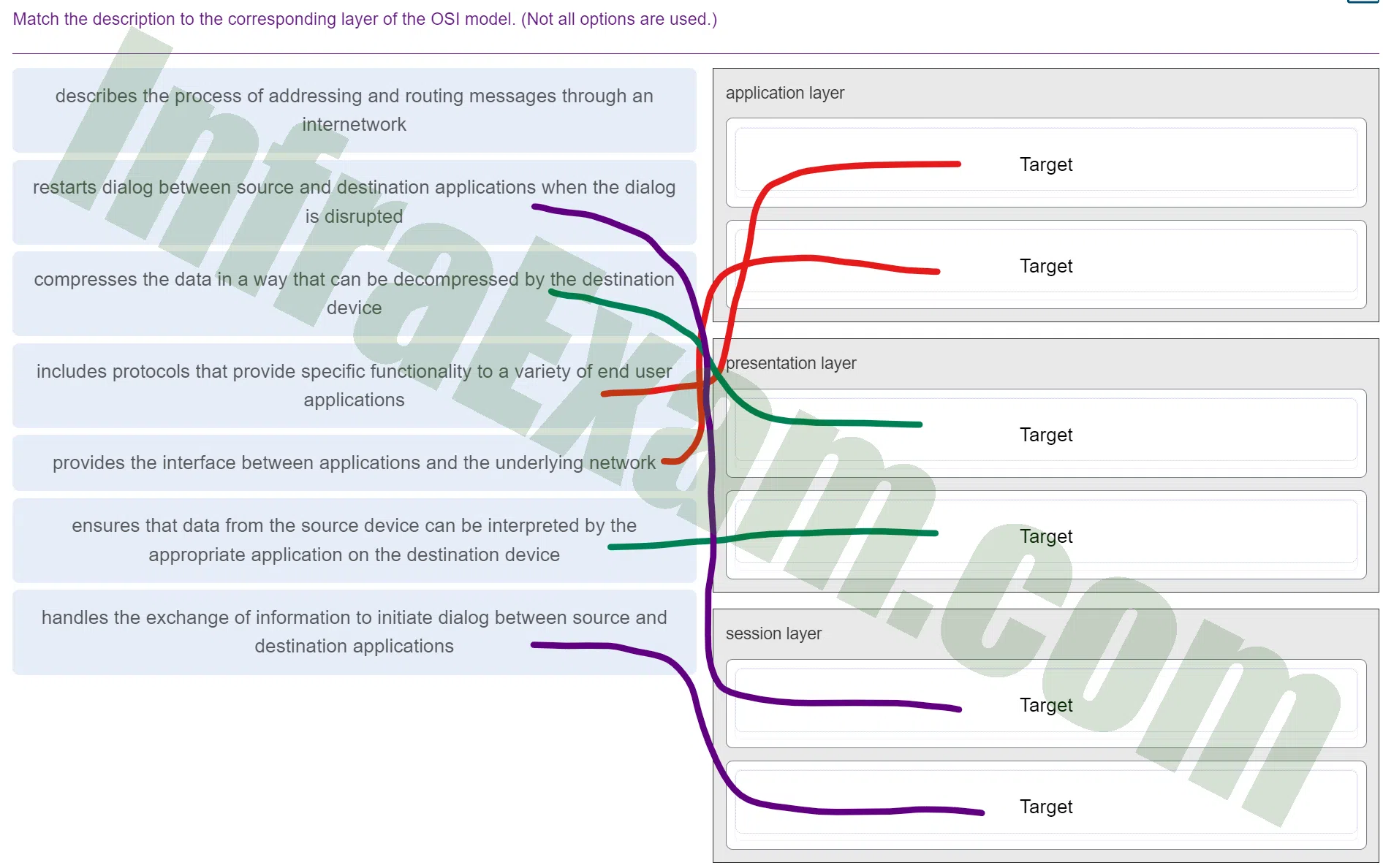
Match the description to the corresponding layer of the OSI model. (Not all options are used.)
DevNet Associate (Version 1.0) – DevNet Associate 1.01 Practice Final Exam Answers 003 - application layer
includes protocols that provide specific functionality to a variety of end user applications
provides the interface between applications and the underlying network - presentation layer
compresses the data in a way that can be decompressed by the destination device
ensures that data from the source device can be interpreted by the appropriate application on the destination device - session layer
restarts dialog between source and destination applications when the dialog is disrupted
handles the exchange of information to initiate dialog between source and destination applicationsExplanation & Hint: Application Layer:
- Includes protocols that provide specific functionality to a variety of end-user applications: The Application Layer is the top layer of the OSI model. It is responsible for providing services and network support to end-user applications. This layer contains protocols that enable communication between different types of software applications, such as web browsers, email clients, and file transfer programs.
- Provides the interface between applications and the underlying network: The Application Layer acts as an interface between the software applications running on different devices and the underlying network infrastructure. It allows applications to access network services and resources without needing to understand the complexities of network protocols.
Presentation Layer:
- Compresses the data in a way that can be decompressed by the destination device: The Presentation Layer handles data translation, encryption, and compression. It ensures that data is formatted and encoded properly for transmission across the network. Compression here refers to the process of reducing the size of data for efficient transmission and storage.
- Ensures that data from the source device can be interpreted by the appropriate application on the destination device: The Presentation Layer ensures that data from the source device is translated into a format that the destination application can understand. It deals with data syntax and semantics to ensure proper communication between different systems with potentially different data formats.
Session Layer:
- Restarts dialogs between source and destination applications when they are disrupted: The Session Layer is responsible for establishing, maintaining, and terminating communication sessions between two devices. If a communication session is interrupted or disrupted, the Session Layer can help reestablish and manage the ongoing dialog between the source and destination applications.
- Handles the exchange of information to initiate dialogs between source and destination applications: The Session Layer facilitates the setup, coordination, and termination of communication between two devices. It manages the dialog control, ensuring that data exchange is organized and that both the source and destination applications are in sync.
These layers collectively form the upper layers (Layer 5, 6, and 7) of the OSI model, which focus on providing services directly to end-users and applications while abstracting the complexities of the lower layers of the network.
- application layer
-
What attribute of a NIC would place it at the data link layer of the OSI model?
- attached Ethernet cable
- IP address
- MAC address
- RJ-45 port
- TCP/IP protocol stack
Explanation & Hint: The data link layer describes media access and physical addressing. The encoding of a MAC address on a NIC places it at that layer. Ports and cables are placed at the physical layer of the OSI model. IP addresses are placed at the network layer. The TCP/IP protocol stack describes a different model.
-
Which field in an 802.1Q Ethernet frame is used by switches to identify VLAN membership of the frame?
- Preamble
- Data
- FCS
- Tag
Explanation & Hint: The 12-bit VLAN identifier is part of the 4-byte Tag field of an 802.1Q Ethernet frame.
-
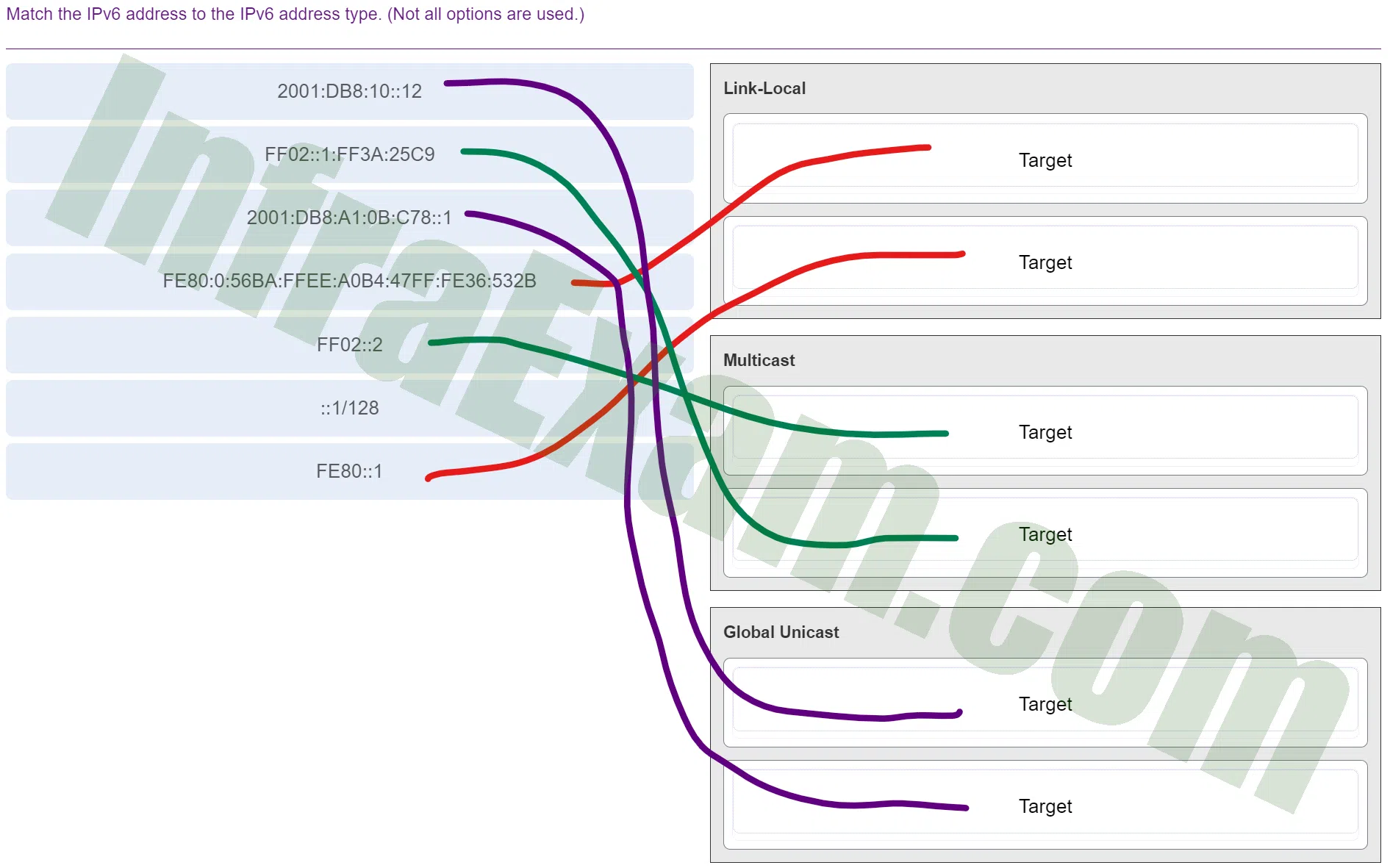
Match the IPv6 address to the IPv6 address type. (Not all options are used.)
DevNet Associate (Version 1.0) – DevNet Associate 1.01 Practice Final Exam Answers 004 - Link-Local
FE80:0:56BA:FFEE:A0B4:47FF:FE36:532B
FE80::1 - Multicast
FF02::2
FF02::1:FF3A:25C9 - Global Unicast
2001:DB8:10::12
2001:DB8:A1:0B:C78::1Explanation & Hint: Link-Local:
- FE80:0:56BA:FFEE:A0B4:47FF:FE36:532B: This is an example of a Link-Local IPv6 address. Link-Local addresses are used for communication within the same network segment (link). They are automatically configured and are only valid within a specific network segment. They are often used for neighbor discovery and initial communication setup.
- FE80::1: Another example of a Link-Local IPv6 address. The “FE80” prefix indicates a Link-Local address, and “::1” signifies the interface with the lowest numerical value on the local link, which is typically used for loopback.
Multicast:
- FF02::2: This is an example of an IPv6 Multicast address. Multicast addresses are used for one-to-many or many-to-many communication. They allow a single packet to be sent to multiple recipients simultaneously. In this case, the address “FF02::2” is a well-known multicast address used for all routers on the local network segment.
- FF02::1:FF3A:25C9: Another example of an IPv6 Multicast address. This type of multicast address is used for solicited-node multicast addresses. They are associated with IPv6 neighbor discovery and are used to resolve IPv6 addresses to MAC addresses.
Global Unicast:
- 2001:DB8:10::12: This is an example of a Global Unicast IPv6 address. Global Unicast addresses are used for unique global communication on the Internet. The “2001:DB8” prefix is reserved for documentation and example purposes.
- 2001:DB8:A1:0B:C78::1: Another example of a Global Unicast IPv6 address. It demonstrates the structure of a globally unique address, which is used for communicating across the broader Internet.
In summary, IPv6 addresses are classified into different types based on their purpose and scope. Link-Local addresses are limited to the local network segment, Multicast addresses allow communication to multiple recipients, and Global Unicast addresses are used for global Internet communication.
- Link-Local
-
What are three parts of an IPv6 global unicast address? (Choose three.)
- an interface ID that is used to identify the local network for a particular host
- a global routing prefix that is used to identify the network portion of the address that has been provided by an ISP
- a subnet ID that is used to identify networks inside of the local enterprise site
- a global routing prefix that is used to identify the portion of the network address provided by a local administrator
- an interface ID that is used to identify the local host on the network
Explanation & Hint: There are three elements that make up an IPv6 global unicast address. A global routing prefix which is provided by an ISP, a subnet ID which is determined by the organization, and an interface ID which uniquely identifies the interface interface of a host.
-
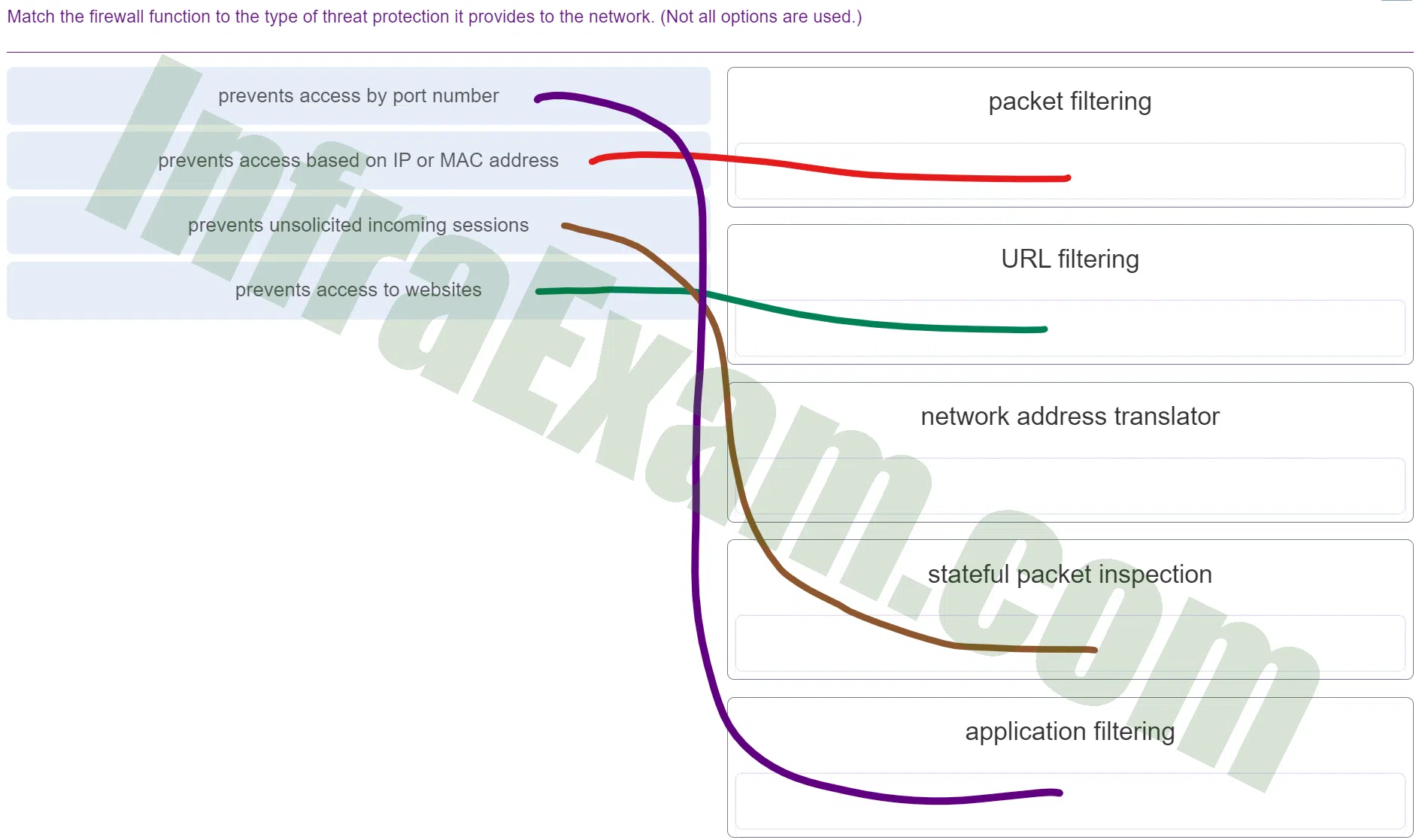
Match the firewall function to the type of threat protection it provides to the network. (Not all options are used.)
DevNet Associate (Version 1.0) – DevNet Associate 1.01 Practice Final Exam Answers 005 - prevents access by port number ==> packet filtering
- prevents access based on IP or MAC address ==> URL filtering
- prevents unsolicited incoming sessions ==> stateful packet inspection
- prevents access to websites ==> application filtering
-
Explanation & Hint: Packet Filtering (Prevents access by port number):
- Explanation: Packet filtering is a basic form of firewall protection that filters incoming and outgoing network traffic based on specific criteria, such as source and destination IP addresses, port numbers, and protocols. By preventing access based on port numbers, packet filtering helps control the types of services and applications that can communicate through specific ports. This can help block unauthorized access to certain network services or applications that might be running on specific ports.
URL Filtering (Prevents access based on IP or MAC address):
- Explanation: URL filtering is a firewall function that controls access to websites based on their URLs or IP addresses. It helps prevent users from accessing specific websites or online resources by blocking requests to certain URLs or IP addresses. While the description doesn’t align perfectly with the function, URL filtering is typically associated with blocking or allowing access to websites based on defined rules.
Stateful Packet Inspection (Prevents unsolicited incoming sessions):
- Explanation: Stateful packet inspection (SPI) is an advanced firewall technique that monitors the state of active connections and inspects packets to determine whether they’re part of an established and legitimate session. By preventing unsolicited incoming sessions, SPI ensures that only packets associated with established connections or responses to outgoing requests are allowed through the firewall. This helps block unauthorized attempts to establish new connections from external sources.
Application Filtering (Prevents access to websites):
- Explanation: While the description doesn’t directly match the function, application filtering is a firewall feature that allows or blocks specific applications or services from accessing the network. This can include blocking certain websites, but it’s broader in scope. Application filtering is used to control access to various types of network applications and services based on predefined policies.
These firewall functions provide different layers of protection to a network by controlling and filtering traffic based on specific attributes, helping to enhance security and manage network resources effectively.
Network address translators translate internal IP addresses to to outside IP addresses and do not prevent network attacks.
-
Which protocol automates assignment of IP addresses on a network, and which port number does it use? (Choose two.)
- DHCP
- DNS
- SMB
- 53
- 67
- 80
Explanation & Hint: DNS uses port 53 and translates URLs to IP addresses. SMB provides shared access to files and printers and uses port 445. Port 80 is used by HTTP. HTTP is a protocol used to communicate between a web browser and a server.
-
Which two statements are correct if a configured NTP master on a network cannot reach any clock with a lower stratum number? (Choose two.)
- The NTP master will claim to be synchronized at the configured stratum number.
- The NTP master will be the clock with 1 as its stratum number.
- An NTP server with a higher stratum number will become the master.
- Other systems will be willing to synchronize to that master using NTP.
- The NTP master will lower its stratum number.
Explanation & Hint: If the network NTP master cannot reach any clock with a lower stratum number, the system will claim to be synchronized at the configured stratum number, and other systems will be willing to synchronize to it using NTP.
-
An international manufacturing company is implementing an industrial internet of things plant infrastructure. The design requires that computing resources are located as close to the user as possible. Which cloud model is suitable for this situation?
- public
- hybrid
- private
- edge
Explanation & Hint: Edge clouds are located as close to the user as possible. Having computing power at the network edge is a benefit for internet of things devices such as cameras, industrial automation equipment, and autonomous vehicles.
-
A network engineer is working on a bash script in order to automate some mundane tasks needed by the department. Why would the engineer add a she-bang (#!) to the top of the script as shown:
#!/bin/bash
- The script file has commands that need to be run in the bash shell.
- The commands within the script file are to have the output stored in the /bin/bash directory.
- The script file has specific commands that are preceded by the exclamation mark (!) and should not be executed.
- The script file has specific commands that are preceded by the pound sign (#) and should not be executed.
Explanation & Hint: A she-bang is the pound sign (#) followed by an exclamation mark (!) and designates the path to the command interpreter. In this case, the interpreter is bash and bash will be used to interpret the script that follows.
-
Match the CI/CD software development philosophy with a description.
DevNet Associate (Version 1.0) – DevNet Associate 1.01 Practice Final Exam Answers 006 - continuous delivery ==> The application development process is performed in short sprints so that enough code is always in a deployable state.
- continuous integration ==> The changes from all developers are continually merged with the main branch of the existing application.
- continuous deployment ==> Once changes are tested and integrated with the main branch they are tested again and then deployed to production.
Explanation & Hint: Continuous Delivery:
- Description: The application development process is performed in short sprints so that enough code is always in a deployable state.
- Explanation: Continuous Delivery is a software development approach where code changes are automatically built, tested, and prepared for deployment throughout the development lifecycle. It emphasizes maintaining a codebase that is consistently in a state where it could be deployed to production at any time. This is achieved by breaking down development into smaller iterations (sprints), ensuring that the codebase is well-tested and functional after each sprint. Continuous Delivery stops short of actually deploying the code to production automatically, giving teams the flexibility to choose when to release.
Continuous Integration:
- Description: The changes from all developers are continually merged with the main branch of the existing application.
- Explanation: Continuous Integration is a practice where developers frequently integrate their code changes into a shared version control repository. This integration is done multiple times throughout the day, with each integration triggering an automated build and test process. The primary goal of Continuous Integration is to identify and address integration issues, conflicts, and bugs early in the development process. By frequently merging code changes into a common codebase, developers can ensure that the software remains functional and that any conflicts are resolved quickly.
Continuous Deployment:
- Description: Once changes are tested and integrated with the main branch, they are tested again and then deployed to production.
- Explanation: Continuous Deployment is an extension of Continuous Delivery, where changes that pass automated testing are automatically deployed to production. In this approach, every successful code change goes through the entire pipeline and is released to production without manual intervention. This promotes frequent releases and ensures that the latest features and fixes are always available to end-users. Automated testing and rigorous quality control are crucial in Continuous Deployment to ensure that only stable and thoroughly tested changes make it into production.
These CI/CD software development philosophies aim to improve the efficiency, quality, and speed of software development and deployment by automating processes, maintaining codebase stability, and promoting collaboration among development teams.
-
A network engineer is configuring a Jenkins job and finishing with the following script in order to trigger the build:
node { stage('Preparation') { catchError(buildResult: 'SUCCESS') { sh 'docker stop samplerunning' sh 'docker rm samplerunning' } } stage('Build') { build 'BuildAppJob' } stage('Results') { build 'TestAppJob' } }- After saving the job, what should the engineer do next?
- Run the job.
- Test the script in Docker.
- Manually run the samplerunning container.
- Open the Recent Changes option to verify the results of the job.
Explanation & Hint: Once a script is created, use the Build Now Jenkins menu option to run the job. If the script is done correctly, then the Stage View should show three green boxes. If errors are found, check the script for errors.
-
What are three tools used by developers for scanning code to check for well-known security issues? (Choose three.)
- Bandit
- Brakeman
- VisualCodeGrepper
- VIRL
- Docker
- Viptela
Explanation & Hint: Because most code developers are not security experts, it is not uncommon to have security vulnerabilities inadvertently written into applications. To help mitigate this threat, there are code scanning tools that a developer can use to look for any well-know security issues embedded into the code. Examples of such tools are Bandit, Brakeman, and VisualCodeGrepper.
-
What are three ways to mitigate SQL injection threats? (Choose three.)
- stateless packet-filtering firewalls
- stored procedures configured with the “db_owner” rights set as default
- dynamic queries
- database firewalls
- parameterized database queries
- whitelist input validation
Explanation & Hint: SQL injection is a basic web application attack technique which, if successful, can delete or change sensitive data or reveal it to the attacker. There are several methods to mitigate the threat of SQL injection such as the use of parameterized database queries, database firewalls, and whitelist input validation.
-
What is the purpose of adding salt to the password hashing process?
- to create a unique hash for every password
- to make hashed passwords deterministic
- to increase the length of a password
- to decrease password complexity
Explanation & Hint: Because of the deterministic nature of the hash function, hashed passwords are not unique. The same password always produces the same hash even if the password is created by different users. The salting process adds random data to the input of the hash function to guarantee a unique, nondeterministic output.
-
What are two benefits of using automation for IT infrastructure? (Choose two.)
- increased speed in the deployment of technologies and products
- reduced need for IT personnel and operations staff
- reduced risk while working at scale
- increased implementation of specific opinionated companion components
- reduced user requisition requests for on-demand infrastructure
Explanation & Hint: There are commonly three benefits of infrastructure automation:
Speed
Repeatability
The ability to work at scale, with reduced risk
-
Which component of a software-defined infrastructure provides available cloud resources within hours or minutes of needing them?
- platform abstraction
- self-service
- observability
- repeatability
Explanation & Hint: Self-service or “platforms on demand” speeds up all phases of development by using cloud resources that can be available within hours or minutes of needing them.
-
What is an example of an SLI?
- 100% availability will be maintained for any services provided.
- All services provided include data integrity and security and comply with local regulations about where and how data is stored.
- All applications being provided will offer a good-enough experience to the user base.
- 95% of requests will be served within 75 milliseconds.
Explanation & Hint: A Service Level Indicator or SLI is a real-world benchmark metric used to determine Service-Level Objectives (SLOs).
-
What are two processes that can be used to execute remote scripts securely? (Choose two.)
- access the built-in rexec command within Bash, target the IP address of the remote machine, and execute the Bash command
- store scripts in a Git repository, install git on the remote machine, clone the repo, check out a branch, and execute the scripts
- store scripts locally, transmit them to a target machine with scp , log into the remote machine via ssh, and execute the scripts
- store scripts on a webserver, log into the remote machine, and retrieve the scripts using wget via HTTP
- pipe scripts to a remote machine using cat | telnet and execute them in sequence with other commands, capturing and returning results to a local terminal
Explanation & Hint: There are many ways to configure remote systems using scripts. However, scripts should be delivered to a remote system through the use of secured protocols or services or both.
-
Which component is required by both Puppet and Chef to be run on hosts?
- cron jobs that access a server to randomize access times to prevent server overload
- IPtables that enable masquerade tunneling
- agents that query a server to determine their desired state, then converge upon it
- certificates for authentication and encryption
Explanation & Hint: Puppet and Chef both require the use of an agent, which is used to reterieve information and make desired changes.
-
A user is working on Ansible on the local NMS to manage remote network devices. The user issues the ansible webservers -m ping command to test the communication. What is the parameter ping in the command?
- a class
- a module
- a method
- a function
Explanation & Hint: In the ansible webservers -m ping command, the parameter ping is an Ansible module invoked by the switch -m .
-
A student in the DevNet class is learning SDKs and APIs. What is the difference between an API and an SDK?
- An API is a software development tool for developing applications, whereas an SDK is a set of protocols for building application software.
- An API is a tool box that contains multiple SDKs, whereas each SDK allows the creation of software for a specific hardware platform.
- An API contains the components that have been created for a specific purpose, whereas an SDK is commonly an interface for a service.
- An API is essentially a documented set of URIs, whereas an SDK is a package integrated with code examples and libraries.
Explanation & Hint: Most SDKs are packages that require installation and are integrated with libraries, documents, and code examples. APIs are essentially a documented set of URIs that act as an interface for a service.
-
Which modeling language is most commonly used for data modeling?
- SQL
- YAML
- YANG
- Python
Explanation & Hint: YANG, an acronym for Yet Another Next Generation, is a data modeling language used to model configuration and state data manipulated by the Network Configuration Protocol (NETCONF), NETCONF remote procedure calls, and NETCONF notifications.
-
An engineer is learning how to enable RESTful API access for the Cisco Meraki Dashboard. What is the first step that must be taken in order to use API calls with the Meraki enterprise cloud-managed networking infrastructure service?
- The engineer must first generate an API key by going to the My Profile page within the GUI.
- Each cloud-managed organization must specify API access and allow the Meraki Dashboard administrator to employ site-specific APIs.
- The Meraki Dashboard API must first be enabled under Organizations > Settings within the GUI.
- A GET request must be created and include header parameters including authentication credentials and the Meraki API URL.
Explanation & Hint: In order to provide API access for an organization, API access must first be enabled within the GUI, under Organization > Settings .
After the API is enabled, an API key must be generated within the My Profile page.
-
What does the Intersight REST API enable an application developer to access?
- IETF Interface
- JavaScript Object Notation
- Universal Resource Locator
- Management Information Model
Explanation & Hint: The Intersight REST API enables a user to access the Management Information Model. The Intersight API accepts and returns messages that are encapsulated through JavaScript Object Notation (JSON) documents and uses HTTP over TLS as the transport protocol.
-
Which two types of APIs are supported by Cisco Finesse? (Choose two.)
- AXL
- REST
- SOAP
- JavaScript
- Python SDK
Explanation & Hint: Cisco Finesse has REST APIs and JavaScript APIs that can be used to build fully customized agent desktops, integrate contact center functionality into applications, and integrate applications into the Finesse agent and supervisor desktop.
-
What are three platforms that the Firepower Management Center can run on in the overall architecture of a large enterprise? (Choose three.)
- on every router
- on VMWare VSphere
- in an availability zone
- on Amazon Web Services (AWS)
- on a wide range of Cisco devices
- in the Secure Operations Center (SOC)
Explanation & Hint: Firepower Management Center can run on VMware vSphere or Amazon Web Services (AWS). It can also run on a range of physical devices including the Cisco FMC series.
| DevNet - DEVASC 1.0 | |
| Final Exam | |
| Practice Final Exam Answers | Online Test |
| Final Exam Answers | Online Test |
| 200-901 Certification Practice Exam | Online Test |