312-49 : Computer Hacking Forensic Investigator : Part 12
-
In the following directory listing,
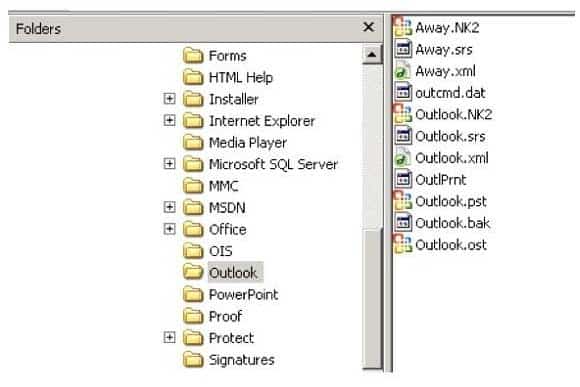
312-49 Part 12 Q01 002 Which file should be used to restore archived email messages for someone using Microsoft Outlook?
- Outlook bak
- Outlook ost
- Outlook NK2
- Outlook NK2
-
Daryl, a computer forensics investigator, has just arrived at the house of an alleged computer hacker. Daryl takes pictures and tags all computer and peripheral equipment found in the house. Daryl packs all the items found in his van and takes them back to his lab for further examination. At his lab, Michael his assistant helps him with the investigation. Since Michael is still in training, Daryl supervises all of his work very carefully. Michael is not quite sure about the procedures to copy all the data off the computer and peripheral devices. How many data acquisition tools should Michael use when creating copies of the evidence for the investigation?
- Two
- One
- Three
- Four
-
What feature of Decryption Collection allows an investigator to crack a password as quickly as possible?
- Cracks every password in 10 minutes
- Distribute processing over 16 or fewer computers
- Support for Encrypted File System
- Support for MD5 hash verification
-
Heather, a computer forensics investigator, is assisting a group of investigators working on a large computer fraud case involving over 20 people. These 20 people, working in different offices, allegedly siphoned off money from many different client accounts. Heather responsibility is to find out how the accused people communicated between each other. She has searched their email and their computers and has not found any useful evidence. Heather then finds some possibly useful evidence under the desk of one of the accused.
In an envelope she finds a piece of plastic with numerous holes cut out of it. Heather then finds the same exact piece of plastic with holes at many of the other accused peoples desks. Heather believes that the 20 people involved in the case were using a cipher to send secret messages in between each other. What type of cipher was used by the accused in this case?
- Grill cipher
- Null cipher
- Text semagram
- Visual semagram
-
What is the smallest physical storage unit on a hard drive?
- Track
- Cluster
- Sector
- Platter
-
When needing to search for a website that is no longer present on the Internet today but was online few years back, what site can be used to view the website collection of pages?
- Proxify.net
- Dnsstuff.com
- Samspade.org
- Archive.org
-
Under confession, an accused criminal admitted to encrypting child pornography pictures and then hiding them within other pictures. What technique did the accused criminal employ?
- Typography
- Steganalysis
- Picture encoding
- Steganography
-
Where does Encase search to recover NTFS files and folders?
- MBR
- MFT
- Slack space
- HAL
-
Given the drive dimensions as follows and assuming a sector has 512 bytes, what is the capacity of the described hard drive?
22,164 cylinders/disk
80 heads/cylinder
63 sectors/track- 53.26 GB
- 57.19 GB
- 11.17 GB
- 10 GB
-
Travis, a computer forensics investigator, is finishing up a case he has been working on for over a month involving copyright infringement and embezzlement. His last task is to prepare an investigative report for the president of the company he has been working for. Travis must submit a hard copy and an electronic copy to this president. In what electronic format should Travis send this report?
- TIFF-8
- DOC
- WPD
-
A forensics investigator is searching the hard drive of a computer for files that were recently moved to the Recycle Bin. He searches for files in C:\RECYCLED using a command line tool but does not find anything. What is the reason for this?
- He should search in C:\Windows\System32\RECYCLED folder
- The Recycle Bin does not exist on the hard drive
- The files are hidden and he must use switch to view them
- Only FAT system contains RECYCLED folder and not NTFS
-
Why should you never power on a computer that you need to acquire digital evidence from?
- When the computer boots up, files are written to the computer rendering the data nclean
- When the computer boots up, the system cache is cleared which could destroy evidence
- When the computer boots up, data in the memory buffer is cleared which could destroy evidence
- Powering on a computer has no affect when needing to acquire digital evidence from it
-
What is the slave device connected to the secondary IDE controller on a Linux OS referred to?
- hda
- hdd
- hdb
- hdc
-
What will the following command accomplish?
dd if=/dev/xxx of=mbr.backup bs=512 count=1
- Back up the master boot record
- Restore the master boot record
- Mount the master boot record on the first partition of the hard drive
- Restore the first 512 bytes of the first partition of the hard drive
-
Preparing an image drive to copy files to is the first step in Linux forensics. For this purpose, what would the following command accomplish?
dcfldd if=/dev/zero of=/dev/hda bs=4096 conv=noerror, sync
- Fill the disk with zeros
- Low-level format
- Fill the disk with 4096 zeros
- Copy files from the master disk to the slave disk on the secondary IDE controller
-
A picture file is recovered from a computer under investigation. During the investigation process, the file is enlarged 500% to get a better view of its contents. The picture quality is not degraded at all from this process. What kind of picture is this file. What kind of picture is this file?
- Raster image
- Vector image
- Metafile image
- Catalog image
-
What advantage does the tool Evidor have over the built-in Windows search?
- It can find deleted files even after they have been physically removed
- It can find bad sectors on the hard drive
- It can search slack space
- It can find files hidden within ADS
-
An on-site incident response team is called to investigate an alleged case of computer tampering within their company. Before proceeding with the investigation, the CEO informs them that the incident will be classified as low level. How long will the team have to respond to the incident?
- One working day
- Two working days
- Immediately
- Four hours
-
What type of attack sends SYN requests to a target system with spoofed IP addresses?
- SYN flood
- Ping of death
- Cross site scripting
- Land
-
Harold is a computer forensics investigator working for a consulting firm out of Atlanta Georgia. Harold is called upon to help with a corporate espionage case in Miami Florida. Harold assists in the investigation by pulling all the data from the computers allegedly used in the illegal activities. He finds that two suspects in the company where stealing sensitive corporate information and selling it to competing companies. From the email and instant messenger logs recovered, Harold has discovered that the two employees notified the buyers by writing symbols on the back of specific stop signs. This way, the buyers knew when and where to meet with the alleged suspects to buy the stolen material. What type of steganography did these two suspects use?
- Text semagram
- Visual semagram
- Grill cipher
- Visual cipher
Subscribe
0 Comments
Newest