312-49 : Computer Hacking Forensic Investigator : Part 13
-
What is the CIDR from the following screenshot?
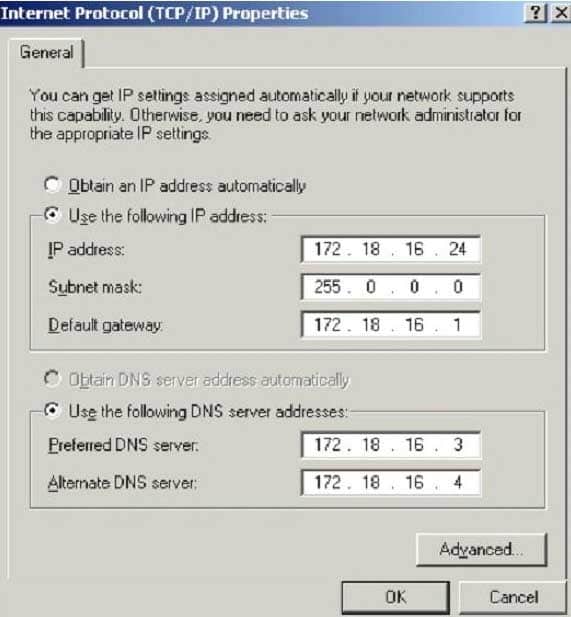
312-49 Part 13 Q01 003 - /24A./24A./24
- /32 B./32 B./32
- /16 C./16 C./16
- /8D./8D./8
-
How many times can data be written to a DVD+R disk?
- Twice
- Once
- Zero
- Infinite
-
What must be obtained before an investigation is carried out at a location?
- Search warrant
- Subpoena
- Habeas corpus
- Modus operandi
-
Paul is a computer forensics investigator working for Tyler & Company Consultants. Paul has been called upon to help investigate a computer hacking ring broken up by the local police. Paul begins to inventory the PCs found in the hackers hideout. Paul then comes across a PDA left by them that is attached to a number of different peripheral devices. What is the first step that Paul must take with the PDA to ensure the integrity of the investigation?
- Place PDA, including all devices, in an antistatic bag
- Unplug all connected devices
- Power off all devices if currently on
- Photograph and document the peripheral devices
-
During an investigation, an employee was found to have deleted harassing emails that were sent to someone else. The company was using Microsoft Exchange and had message tracking enabled. Where could the investigator search to find the message tracking log file on the Exchange server?
- C:\Program Files\Exchsrvr\servername.log
- D:\Exchsrvr\Message Tracking\servername.log
- C:\Exchsrvr\Message Tracking\servername.log
- C:\Program Files\Microsoft Exchange\srvr\servername.log
-
Paraben Lockdown device uses which operating system to write hard drive data?
- Mac OS
- Red Hat
- Unix
- Windows
-
What technique is used by JPEGs for compression?
- ZIP
- TCD
- DCT
- TIFF-8
-
John is working as a computer forensics investigator for a consulting firm in Canada. He is called to seize a computer at a local web caf purportedly used as a botnet server. John thoroughly scans the computer and finds nothing that would lead him to think the computer was a botnet server. John decides to scan the virtual memory of the computer to possibly find something he had missed. What information will the virtual memory scan produce?
- It contains the times and dates of when the system was last patched
- It is not necessary to scan the virtual memory of a computer
- It contains the times and dates of all the system files
- Hidden running processes
-
What method of copying should always be performed first before carrying out an investigation?
- Parity-bit copy
- Bit-stream copy
- MS-DOS disc copy
- System level copy
-
Where is the default location for Apache access logs on a Linux computer?
- usr/local/apache/logs/access_log
- bin/local/home/apache/logs/access_log
- usr/logs/access_log
- logs/usr/apache/access_log
-
Jacob is a computer forensics investigator with over 10 years experience in investigations and has written over 50 articles on computer forensics. He has been called upon as a qualified witness to testify the accuracy and integrity of the technical log files gathered in an investigation into computer fraud. What is the term used for Jacob testimony in this case?
- Justification
- Authentication
- Reiteration
- Certification
-
How often must a company keep log files for them to be admissible in a court of law?
- All log files are admissible in court no matter their frequency
- Weekly
- Monthly
- Continuously
-
What file is processed at the end of a Windows XP boot to initialize the logon dialog box?
- NTOSKRNL.EXE
- NTLDR
- LSASS.EXE
- NTDETECT.COM
-
John is working on his company policies and guidelines. The section he is currently working on covers company documents; how they should be handled, stored, and eventually destroyed. John is concerned about the process whereby outdated documents are destroyed. What type of shredder should John write in the guidelines to be used when destroying documents?
- Strip-cut shredder
- Cross-cut shredder
- Cross-hatch shredder
- Cris-cross shredder
-
To check for POP3 traffic using Ethereal, what port should an investigator search by?
- 143
- 25
- 110
- 125
-
When should an MD5 hash check be performed when processing evidence?
- After the evidence examination has been completed
- On an hourly basis during the evidence examination
- Before and after evidence examination
- Before the evidence examination has been completed
-
At what layer does a cross site scripting attack occur on?
- Presentation
- Application
- Session
- Data Link
-
Davidson Trucking is a small transportation company that has three local offices in Detroit Michigan. Ten female employees that work for the company have gone to an attorney reporting that male employees repeatedly harassed them and that management did nothing to stop the problem. Davidson has employee policies that outline all company guidelines, including awareness on harassment and how it will not be tolerated. When the case is brought to court, whom should the prosecuting attorney call upon for not upholding company policy?
- IT personnel
- Employees themselves
- Supervisors
- Administrative assistant in charge of writing policies
-
When searching through file headers for picture file formats, what should be searched to find a JPEG file in hexadecimal format?
- FF D8 FF E0 00 10
- FF FF FF FF FF FF
- FF 00 FF 00 FF 00
- EF 00 EF 00 EF 00
-
Jack Smith is a forensics investigator who works for Mason Computer Investigation Services. He is investigating a computer that was infected by Ramen Virus.
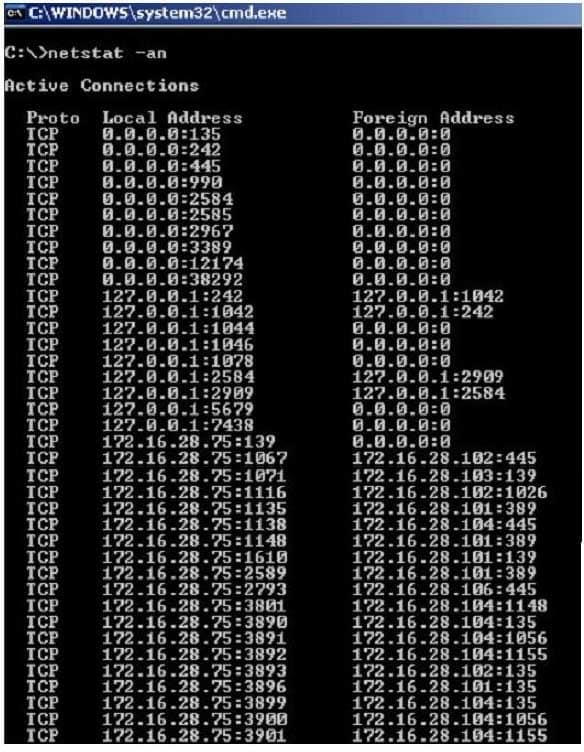
312-49 Part 13 Q20 004 He runs the netstat command on the machine to see its current connections. In the following screenshot, what do the 0.0.0.0 IP addresses signify?
- Those connections are established
- Those connections are in listening mode
- Those connections are in closed/waiting mode
- Those connections are in timed out/waiting mode
Subscribe
0 Comments
Newest