312-49 : Computer Hacking Forensic Investigator : Part 14
-
What type of flash memory card comes in either Type I or Type II and consumes only five percent of the power required by small hard drives?
- SD memory
- CF memory
- MMC memory
- SM memory
-
Julie is a college student majoring in Information Systems and Computer Science. She is currently writing an essay for her computer crimes class. Julie paper focuses on white-collar crimes in America and how forensics investigators investigate the cases. Julie would like to focus the subject. Julie would like to focus the subject of the essay on the most common type of crime found in corporate America. What crime should Julie focus on?
- Physical theft
- Copyright infringement
- Industrial espionage
- Denial of Service attacks
-
A forensics investigator needs to copy data from a computer to some type of removable media so he can examine the information at another location. The problem is that the data is around 42GB in size. What type of removable media could the investigator use?
- Blu-Ray single-layer
- HD-DVD
- Blu-Ray dual-layer
- DVD-18
-
Steven has been given the task of designing a computer forensics lab for the company he works for. He has found documentation on all aspects of how to design a lab except the number of exits needed. How many exits should Steven include in his design for the computer forensics lab?
- Three
- One
- Two
- Four
-
You have been called in to help with an investigation of an alleged network intrusion. After questioning the members of the company IT department, you search through the server log files to find any trace of the intrusion. After that you decide to telnet into one of the company routers to see if there is any evidence to be found. While connected to the router, you see some unusual activity and believe that the attackers are currently connected to that router. You start up an ethereal session to begin capturing traffic on the router that could be used in the investigation. At what layer of the OSI model are you monitoring while watching traffic to and from the router?
- Network
- Transport
- Data Link
- Session
-
Which forensic investigating concept trails the whole incident from how the attack began to how the victim was affected?
- Point-to-point
- End-to-end
- Thorough
- Complete event analysis
-
Sniffers that place NICs in promiscuous mode work at what layer of the OSI model?
- Network
- Transport
- Physical
- Data Link
-
Where are files temporarily written in Unix when printing?
- /usr/spool
- /var/print
- /spool
- /var/spool
-
All Blackberry email is eventually sent and received through what proprietary RIM-operated mechanism?
- Blackberry Message Center
- Microsoft Exchange
- Blackberry WAP gateway
- Blackberry WEP gateway
-
Which program is the bootloader when Windows XP starts up?
- KERNEL.EXE
- NTLDR
- LOADER
- LILO
-
What encryption technology is used on Blackberry devices Password Keeper?
- 3DES
- AES
- Blowfish
- RC5
-
What is the first step taken in an investigation for laboratory forensic staff members?
- Packaging the electronic evidence
- Securing and evaluating the electronic crime scene
- Conducting preliminary interviews
- Transporting the electronic evidence
-
What type of analysis helps to identify the time and sequence of events in an investigation?
- Time-based
- Functional
- Relational
- Temporal
-
Cylie is investigating a network breach at a state organization in Florida. She discovers that the intruders were able to gain access into the company firewalls by overloading them with IP packets. Cylie then discovers through her investigation that the intruders hacked into the company phone system and used the hard drives on their PBX system to store shared music files. What would this attack on the company PBX system be called?
- Phreaking
- Squatting
- Crunching
- Pretexting
-
What will the following command accomplish in Linux?
fdisk /dev/hda
- Partition the hard drive
- Format the hard drive
- Delete all files under the /dev/hda folder
- Fill the disk with zeros
-
In the following email header, where did the email first originate from?
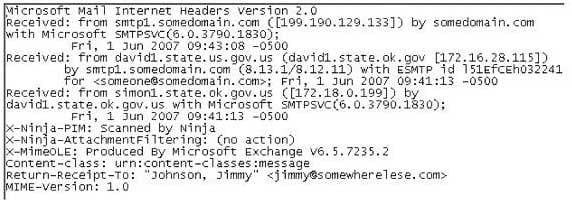
312-49 Part 14 Q16 005 - Somedomain.com
- Smtp1.somedomain.com
- Simon1.state.ok.gov.us
- David1.state.ok.gov.us
-
A computer forensics investigator is inspecting the firewall logs for a large financial institution that has employees working 24 hours a day, 7 days a week.
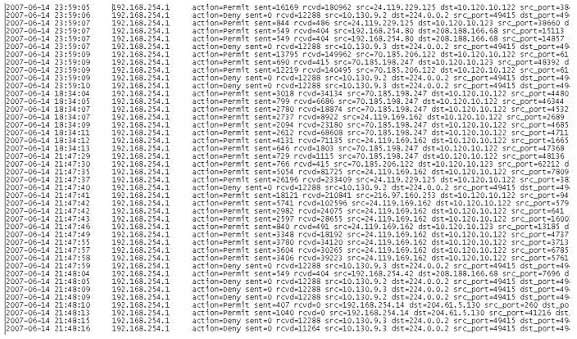
312-49 Part 14 Q17 006 What can the investigator infer from the screenshot seen below?
- A smurf attack has been attempted
- A denial of service has been attempted
- Network intrusion has occurred
- Buffer overflow attempt on the firewall.
-
When investigating a wireless attack, what information can be obtained from the DHCP logs?
- The operating system of the attacker and victim computers
- IP traffic between the attacker and the victim
- MAC address of the attacker
- If any computers on the network are running in promiscuous mode
-
This type of testimony is presented by someone who does the actual fieldwork and does not offer a view in court.
- Civil litigation testimony
- Expert testimony
- Victim advocate testimony
- Technical testimony
-
On an Active Directory network using NTLM authentication, where on the domain controllers are the passwords stored?
- SAM
- AMS
- Shadow file
- Password.conf
Subscribe
0 Comments
Newest