312-49 : Computer Hacking Forensic Investigator : Part 15
-
Why is it still possible to recover files that have been emptied from the Recycle Bin on a Windows computer?
- The data is still present until the original location of the file is used
- The data is moved to the Restore directory and is kept there indefinitely
- The data will reside in the L2 cache on a Windows computer until it is manually deleted
- It is not possible to recover data that has been emptied from the Recycle Bin
-
When is it appropriate to use computer forensics?
- If copyright and intellectual property theft/misuse has occurred
- If employees do not care for their boss management techniques
- If sales drop off for no apparent reason for an extended period of time
- If a financial institution is burglarized by robbers
-
Madison is on trial for allegedly breaking into her university internal network. The police raided her dorm room and seized all of her computer equipment. Madison lawyer is trying to convince the judge that the seizure was unfounded and baseless. Under which US Amendment is Madison lawyer trying to prove the police violated?
- The 10th Amendment
- The 5th Amendment
- The 1st Amendment
- The 4th Amendment
-
Using Linux to carry out a forensics investigation, what would the following command accomplish?
dd if=/usr/home/partition.image of=/dev/sdb2 bs=4096 conv=notrunc,noerror
- Search for disk errors within an image file
- Backup a disk to an image file
- Copy a partition to an image file
- Restore a disk from an image file
-
In handling computer-related incidents, which IT role should be responsible for recovery, containment, and prevention to constituents?
- Security Administrator
- Network Administrator
- Director of Information Technology
- Director of Administration
-
What will the following Linux command accomplish?
dd if=/dev/mem of=/home/sam/mem.bin bs=1024
- Copy the master boot record to a file
- Copy the contents of the system folder to a file
- Copy the running memory to a file
- Copy the memory dump file to an image file
-
Before performing a logical or physical search of a drive in Encase, what must be added to the program?
- File signatures
- Keywords
- Hash sets
- Bookmarks
-
When a router receives an update for its routing table, what is the metric value change to that path?
- Increased by 2
- Decreased by 1
- Increased by 1
- Decreased by 2
-
When operating systems mark a cluster as used but not allocated, the cluster is considered as _________
- Corrupt
- Bad
- Lost
- Unallocated
-
While looking through the IIS log file of a web server, you find the following entries:
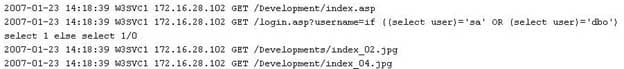
312-49 Part 15 Q10 007 What is evident from this log file?
- Web bugs
- Cross site scripting
- Hidden fields
- SQL injection is possible
-
Why would you need to find out the gateway of a device when investigating a wireless attack?
- The gateway will be the IP of the proxy server used by the attacker to launch the attack
- The gateway will be the IP of the attacker computer
- The gateway will be the IP used to manage the RADIUS server
- The gateway will be the IP used to manage the access point
-
Using Internet logging software to investigate a case of malicious use of computers, the investigator comes across some entries that appear odd.
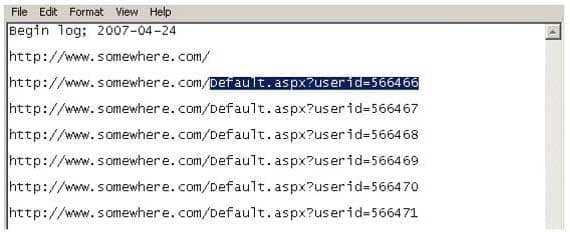
312-49 Part 15 Q12 008 From the log, the investigator can see where the person in question went on the Internet. From the log, it appears that the user was manually typing in different user ID numbers. What technique this user was trying?
- Parameter tampering
- Cross site scripting
- SQL injection
- Cookie Poisoning
-
Why would a company issue a dongle with the software they sell?
- To provide source code protection
- To provide wireless functionality with the software
- To provide copyright protection
- To ensure that keyloggers cannot be used
-
What feature of Windows is the following command trying to utilize?
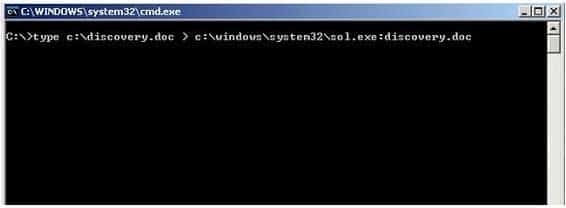
312-49 Part 15 Q14 009 - White space
- AFS
- ADS
- Slack file
-
Harold is finishing up a report on a case of network intrusion, corporate spying, and embezzlement that he has been working on for over six months. He is trying to find the right term to use in his report to describe network-enabled spying. What term should Harold use?
- Spycrack
- Spynet
- Netspionage
- Hackspionage
-
What is considered a grant of a property right given to an individual who discovers or invents a new machine, process, useful composition of matter or manufacture?
- Copyright
- Design patent
- Trademark
- Utility patent
-
Where is the startup configuration located on a router?
- Static RAM
- BootROM
- NVRAM
- Dynamic RAM
-
While searching through a computer under investigation, you discover numerous files that appear to have had the first letter of the file name replaced by the hex code byte 5h. What does this indicate on the computer?
- The files have been marked as hidden
- The files have been marked for deletion
- The files are corrupt and cannot be recovered
- The files have been marked as read-only
-
While presenting his case to the court, Simon calls many witnesses to the stand to testify. Simon decides to call Hillary Taft, a lay witness, to the stand. Since Hillary is a lay witness, what field would she be considered an expert in?
- Technical material related to forensics
- No particular field
- Judging the character of defendants/victims
- Legal issues
-
When reviewing web logs, you see an entry for resource not found in the HTTP status code field.
What is the actual error code that you would see in the log for resource not found?
- 202
- 404
- 606
- 999
Subscribe
0 Comments
Newest