312-49 : Computer Hacking Forensic Investigator : Part 17
-
An executive has leaked the company trade secrets through an external drive. What process should the investigation team take if they could retrieve his system?
- Postmortem Analysis
- Real-Time Analysis
- Packet Analysis
- Malware Analysis
-
Company ABC has employed a firewall, IDS, Antivirus, Domain Controller, and SIEM. The company’s domain controller goes down. From which system would you begin your investigation?
- Domain Controller
- Firewall
- SIEM
- IDS
-
Which code does the FAT file system use to mark the file as deleted?
- ESH
- 5EH
- H5E
- E5H
-
What does the 63.78.199.4(161) denotes in a Cisco router log?
Mar 14 22:57:53.425 EST: %SEC-6-IPACCESSLOGP: list internet-inbound denied udp 66.56.16.77(1029) -> 63.78.199.4(161), 1 packet
- Destination IP address
- Source IP address
- Login IP address
- None of the above
-
Microsoft Security IDs are available in Windows Registry Editor. The path to locate IDs in Windows 7 is:
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\ProfileList
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\RegList
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Regedit
-
Which of the following commands shows you all of the network services running on Windows-based servers?
- Netstart
- Net Session
- Net use
- Net config
-
Which of the following are small pieces of data sent from a website and stored on the user’s computer by the user’s web browser to track, validate, and maintain specific user information?
- Temporary Files
- Open files
- Cookies
- Web Browser Cache
-
Pagefile.sys is a virtual memory file used to expand the physical memory of a computer. Select the registry path for the page file:
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\System Management
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Device Management
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management\PrefetchParameters
-
Which of the following commands shows you the names of all open shared files on a server and the number of file locks on each file?
- Net config
- Net file
- Net share
- Net sessions
-
The surface of a hard disk consists of several concentric rings known as tracks; each of these tracks has smaller partitions called disk blocks. What is the size of each block?
- 512 bits
- 512 bytes
- 256 bits
- 256 bytes
-
In Windows Security Event Log, what does an event id of 530 imply?
- Logon Failure – Unknown user name or bad password
- Logon Failure – User not allowed to logon at this computer
- Logon Failure – Account logon time restriction violation
- Logon Failure – Account currently disabled
-
Which of the following technique creates a replica of an evidence media?
- Data Extraction
- Backup
- Bit Stream Imaging
- Data Deduplication
-
Which among the following search warrants allows the first responder to get the victim’s computer information such as service records, billing records, and subscriber information from the service provider?
- Citizen Informant Search Warrant
- Electronic Storage Device Search Warrant
- John Doe Search Warrant
- Service Provider Search Warrant
-
Madison is on trial for allegedly breaking into her university’s internal network. The police raided her dorm room and seized all of her computer equipment. Madison’s lawyer is trying to convince the judge that the seizure was unfounded and baseless. Under which US Amendment is Madison’s lawyer trying to prove the police violated?
- The 4th Amendment
- The 1st Amendment
- The 10th Amendment
- The 5th Amendment
-
Casey has acquired data from a hard disk in an open source acquisition format that allows her to generate compressed or uncompressed image files. What format did she use?
- Portable Document Format
- Advanced Forensics Format (AFF)
- Proprietary Format
- Raw Format
-
Depending upon the jurisdictional areas, different laws apply to different incidents. Which of the following law is related to fraud and related activity in connection with computers?
- 18 USC §1029
- 18 USC §1030
- 18 USC §1361
- 18 USC §1371
-
Linux operating system has two types of typical bootloaders namely LILO (Linux Loader) and GRUB (Grand Unified Bootloader). In which stage of the booting process do the bootloaders become active?
- Bootloader Stage
- Kernel Stage
- BootROM Stage
- BIOS Stage
-
Which of the following Event Correlation Approach checks and compares all the fields systematically and intentionally for positive and negative correlation with each other to determine the correlation across one or multiple fields?
- Rule-Based Approach
- Automated Field Correlation
- Field-Based Approach
- Graph-Based Approach
-
Which of the following tool creates a bit-by-bit image of an evidence media?
- Recuva
- FileMerlin
- AccessData FTK Imager
- Xplico
-
Data is striped at a byte level across multiple drives, and parity information is distributed among all member drives.
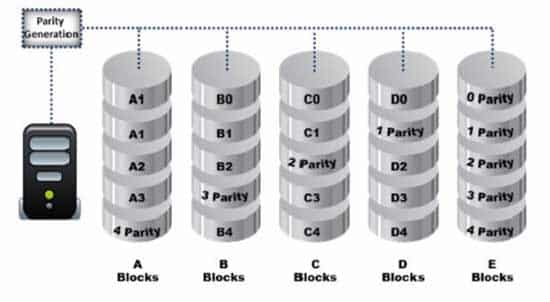
312-49 Part 17 Q20 010 What RAID level is represented here?
- RAID Level 0
- RAID Level 5
- RAID Level 3
- RAID Level 1
Subscribe
0 Comments
Newest