312-49 : Computer Hacking Forensic Investigator : Part 27
-
What does the command “C:\>wevtutil gl <log name>” display?
- Configuration information of a specific Event Log
- Event logs are saved in .xml format
- Event log record structure
- List of available Event Logs
-
An investigator is analyzing a checkpoint firewall log and comes across symbols. What type of log is he looking at?

312-49 Part 27 Q02 014 - Security event was monitored but not stopped
- Malicious URL detected
- An email marked as potential spam
- Connection rejected
-
For what purpose do the investigators use tools like iPhoneBrowser, iFunBox, OpenSSHSSH, and iMazing?
- Bypassing iPhone passcode
- Debugging iPhone
- Rooting iPhone
- Copying contents of iPhone
-
Which of the following does Microsoft Exchange E-mail Server use for collaboration of various e-mail applications?
- Simple Mail Transfer Protocol (SMTP)
- Messaging Application Programming Interface (MAPI)
- Internet Message Access Protocol (IMAP)
- Post Office Protocol version 3 (POP3)
-
Which of the following is a precomputed table containing word lists like dictionary files and brute force lists and their hash values?
- Directory Table
- Rainbow Table
- Master file Table (MFT)
- Partition Table
-
What is the capacity of Recycle bin in a system running on Windows Vista?
- 2.99GB
- 3.99GB
- Unlimited
- 10% of the partition space
-
Brian needs to acquire data from RAID storage. Which of the following acquisition methods is recommended to retrieve only the data relevant to the investigation?
- Static Acquisition
- Sparse or Logical Acquisition
- Bit-stream disk-to-disk Acquisition
- Bit-by-bit Acquisition
-
Analyze the hex representation of mysql-bin.000013 file in the screenshot below. Which of the following will be an inference from this analysis?
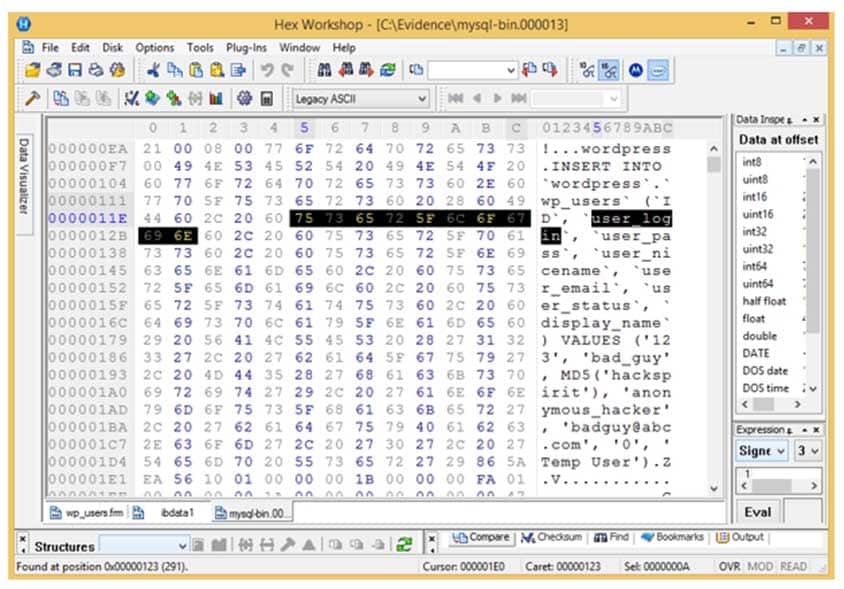
312-49 Part 27 Q08 015 - A user with username bad_guy has logged into the WordPress web application
- A WordPress user has been created with the username anonymous_hacker
- An attacker with name anonymous_hacker has replaced a user bad_guy in the WordPress database
- A WordPress user has been created with the username bad_guy
-
What technique is used by JPEGs for compression?
- TIFF-8
- ZIP
- DCT
- TCD
-
Which of the following is found within the unique instance ID key and helps investigators to map the entry from USBSTOR key to the MountedDevices key?
- ParentIDPrefix
- LastWrite
- UserAssist key
- MRUListEx key
-
What is the investigator trying to analyze if the system gives the following image as output?
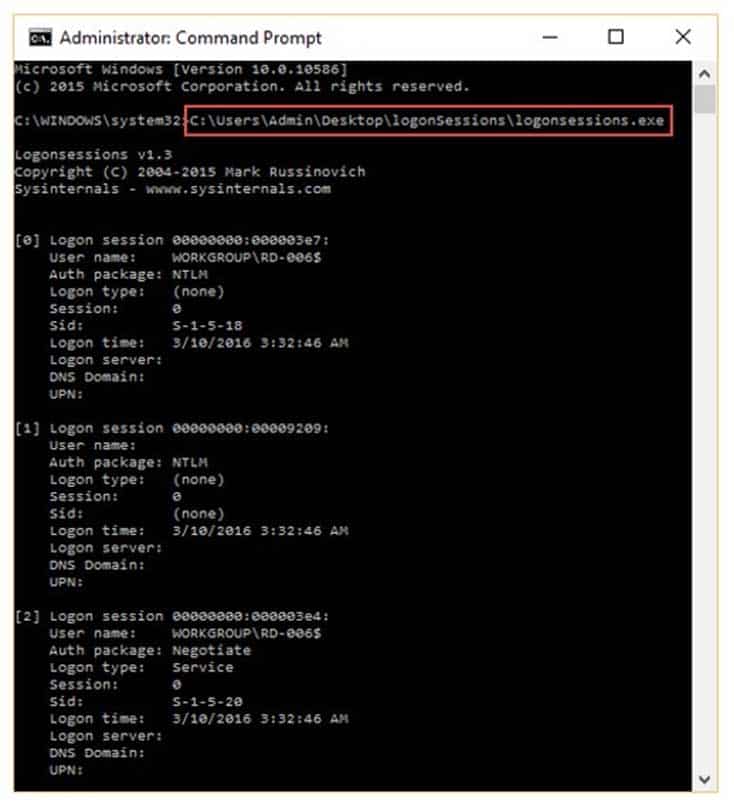
312-49 Part 27 Q11 016 - All the logon sessions
- Currently active logon sessions
- Inactive logon sessions
- Details of users who can logon
Subscribe
0 Comments
Newest