312-76 : EC-Council Disaster Recovery Professional : Part 03
-
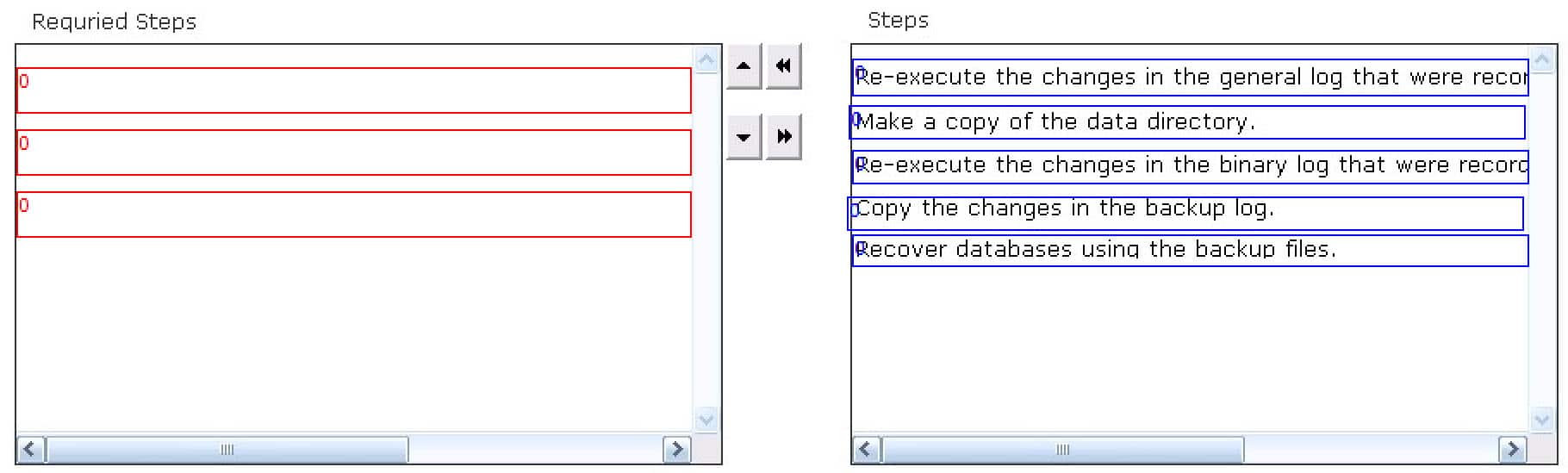
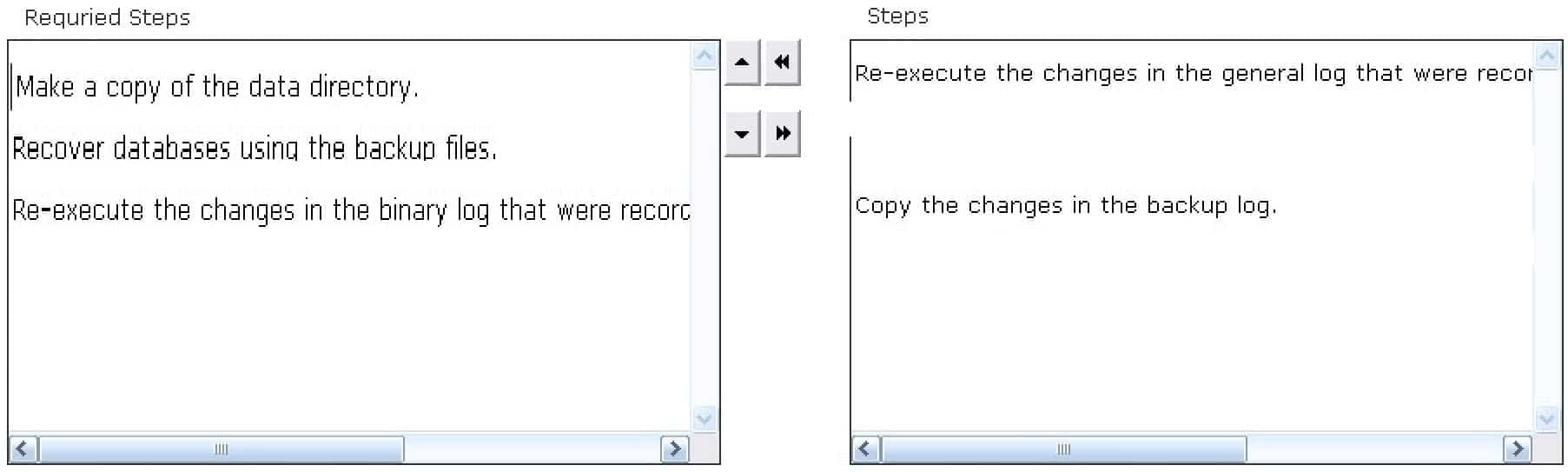
DRAG DROP
Choose the steps involved in the general disaster recovery procedure.
-
Which of the following backup sites is the best way for rapid recovery if you do not need the full recovery temporarily?
- Hot backup site
- Cold backup site
- Mobile backup site
- Warm backup site
-
Which of the following subphases are defined in the maintenance phase of the life cycle models?
Each correct answer represents a part of the solution. Choose all that apply.
- Change control
- Request control
- Release control
- Configuration control
-
SIMULATION
Fill in the blank:
An ___________________ (AS) is a group of networks under a single administration and with single routing policies.
- Autonomous System
-
Which of the following best describes the identification, analysis, and ranking of risks?
- Fixed-price contract
- Design of experiments
- Fast tracking
- Plan Risk management
-
Which of the following procedures is to reduce the risk to personnel, property, and other assets while minimizing work disorders in the event of an emergency?
- Occupant Emergency Plan
- Disaster Recovery Plan
- Cyber Incident Response Plan
- Crisis Communication Plan
-
Which of the following procedures is designed to enable security personnel to identify, mitigate, and recover from malicious computer incidents, such as unauthorized access to a system or data, denial-of-service attacks, or unauthorized changes to system hardware, software, or data?
- Cyber Incident Response Plan
- Crisis Communication Plan
- Occupant Emergency Plan
- Disaster Recovery Plan
-
Which of the following BCP teams assesses the damage of the disaster in order to provide the estimate of the time required to recover?
- Emergency action team
- Off-site storage team
- Emergency management team
- Damage assessment team
-
SIMULATION
Fill the appropriate power supply form factor in the blank space.
_________ form factor is similar to LPX form factor in physical dimensions.- ATX
-
Which of the following are common applications that help in replicating and protecting critical information at the time of disaster?
Each correct answer represents a complete solution. Choose all that apply.
- Asynchronous replication
- Synchronous replication
- Tape backup
- Disk mirroring
-
Configuration Management (CM) is an Information Technology Infrastructure Library (ITIL) IT Service Management (ITSM) process. Configuration Management is used for which of the following?
Each correct answer represents a part of the solution. Choose all that apply.
- To verify configuration records and correct any exceptions
- To account for all IT assets
- To provide precise information support to other ITIL disciplines
- To provide a solid base only for Incident and Problem Management
-
Which of the following plans provides procedures for recovering business operations immediately following a disaster?
- Business recovery plan
- Continuity of operation plan
- Disaster recovery plan
- Business continuity plan
-
You work as a senior project manager in SoftTech Inc. You are working on a software project using configuration management. Through configuration management, you are decomposing the verification system into identifiable, understandable, manageable, traceable units that are known as Configuration Items (CIs). According to you, which of the following processes is known as the decomposition process of a verification system into Configuration Items?
- Configuration auditing
- Configuration identification
- Configuration status accounting
- Configuration control
-
You are working as a project manager in your organization. You are nearing the final stages of project execution and looking towards the final risk monitoring and controlling activities. For your project archives, which one of the following is an output of risk monitoring and control?
- Risk audits
- Qualitative risk analysis
- Quantitative risk analysis
- Requested changes
-
SIMULATION
Fill in the blank with the appropriate phrase.
__________________ is the process of obtaining access using legitimate credentials, and then attempting to leverage that into access to unauthorized system resources.
- Privilege escalation
-
Which of the following procedures can be broadly defined as the plan for the exchange of information before, during, or after a crisis event?
- Occupant Emergency Plan
- Crisis Communication Plan
- Cyber Incident Response Plan
- Disaster Recovery Plan
-
Which of the following processes identifies the threats that can impact the business continuity of operations?
- Business impact analysis
- Function analysis
- Requirement analysis
- Risk analysis
-
Which of the following measurements of a disaster recovery plan are aimed at avoiding an event from occurring?
- Corrective measures
- Detective measures
- Preventive measures
- Supportive measures
-
Which of the following cryptographic system services ensures that the information will not be disclosed to any unauthorized person on a local network?
- Non-repudiation
- Confidentiality
- Authentication
- Integrity
-
Which of the following cryptographic system services proves a user’s identity?
- Confidentiality
- Non-repudiation
- Integrity
- Authentication
Subscribe
0 Comments
Newest