312-76 : EC-Council Disaster Recovery Professional : Part 05
-
Organizations must assess the safety of their workplaces and consider the ability of a business to continue despite risk impact. When assessing business continuity risks, the HR Professional must consider several different types of disasters, their probability, and impact on an organization. What category of disaster is best described as acts of terrorism, major thefts, sabotage, or labor disputes?
- Organized or deliberate disruptions
- System failures
- Environmental disasters
- Serious information security incidents
-
Which of the following command line tools are available in Helix Live acquisition tool on Windows?
Each correct answer represents a complete solution. Choose all that apply.
- netstat
- whois
- cab extractors
- ipconfig
-
Which of the following authorizes and documents all the changes in the IT Infrastructure and its components (Configuration Items) in order to maintain a minimum amount of interruptive effects upon the running operation?
- The IT Security Manager
- The Configuration Manager
- The Change Manager
- The Service Level Manager
-
You work as a Network administrator for Infonet Inc. The company has 135 Windows XP Professional computers and twenty Windows 2003 Server computers. You want to specify the number of invalid logon attempts allowed before a user account is locked out. What will you do to accomplish the task?
- Reset Account Lockout Counter After policy.
- Set Account Lockout Threshold policy.
- Set Account Lockout Duration policy.
- Enforce Password Must Meet Complexity Requirements policy.
-
Which of the following techniques is an encryption method that uses public-key encryption to encrypt and digitally sign e-mail messages during communication between e-mail clients?
- DES
- IDEA
- PGP
- AES
-
DRAG DROP
Drag and drop the appropriate team names in front of their respective responsibilities.
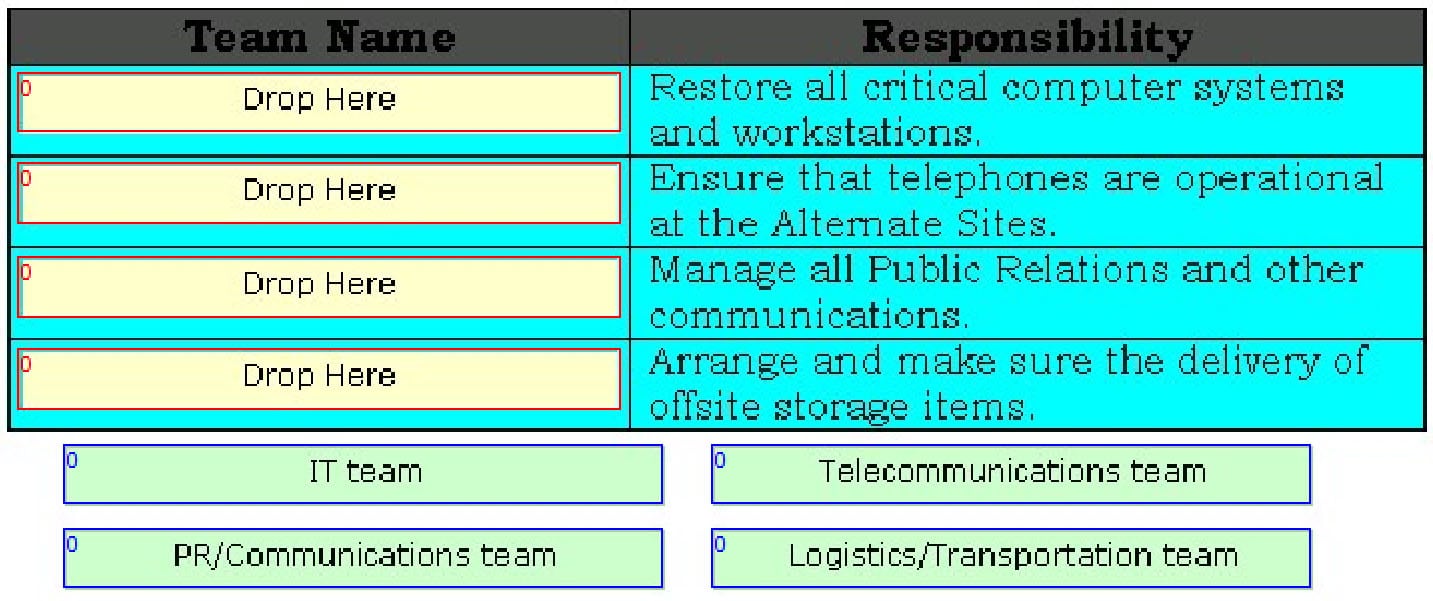
312-76 Part 05 Q06 003 
312-76 Part 05 Q06 004 -
Joseph is a merchant. He lives in an area that is prone to natural disasters. What will he do to save his data from a disaster?
- Restore the data.
- E-mail the data.
- Print the data.
- Backup the data.
-
Which of the following BCP teams deals with the key decision making and guides recovery teams and business personnel?
- Off-site storage team
- Emergency management team
- Damage assessment team
- Emergency action team
-
Which of the following procedures is designed to contain data, hardware, and software that can be critical for a business?
- Disaster Recovery Plan
- Crisis Communication Plan
- Cyber Incident Response Plan
- Occupant Emergency Plan
-
You work as a security manager for SoftTech Inc. You along with your team are doing the disaster recovery for your project. Which of the following steps are performed by you for secure recovery based on the extent of the disaster and the organization’s recovery ability?
Each correct answer represents a part of the solution. Choose three.
- Recover at the primary operating site
- Recover to an alternate site for critical functions
- Restore full system after a catastrophic loss
- Restore full system at an alternate operating site
-
You work as a CSO (Chief Security Officer) for Tech Perfect Inc. You have a disaster scenario and you want to discuss it with your team members for getting appropriate responses of the disaster. In which of the following disaster recovery tests can this task be performed?
- Parallel test
- Full-interruption test
- Structured walk-through test
- Simulation test
-
Which of the following plans is designed to protect critical business processes from natural or man-made failures or disasters and the resultant loss of capital due to the unavailability of normal business processes?
- Contingency plan
- Disaster recovery plan
- Crisis communication plan
- Business continuity plan
-
Which of the following refers to the ability to ensure that the data is not modified or tampered with?
- Integrity
- Confidentiality
- Availability
- Non-repudiation
-
Which of the following BCP teams handles financial arrangement, public relations, and media inquiries at the time of disaster recovery?
- Applications team
- Software team
- Emergency management team
- Off-site storage team
-
SIMULATION
Fill in the blank with an appropriate phrase.
The ___________ is concerned with rebuilding production processing and determining the criticality of data.- recovery team
-
Which of the following policies is related to the backup of data?
- Backup policy
- Network security policy
- User password policy
- Privacy policy
-
DRAG DROP
Disaster recovery plan consists of various tiers for identifying the methods of recovering mission-critical computer systems that are necessary to support business continuity. All these tiers provide a simple method to define current service levels and associated risks. Choose and re-order the tiers of disaster recovery plan.
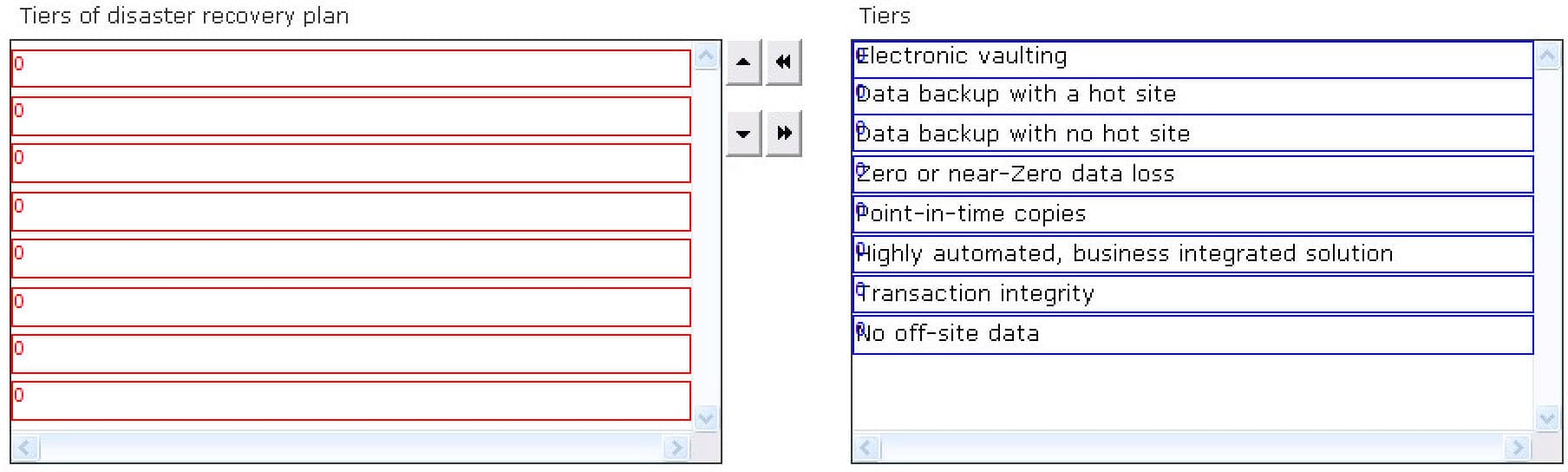
312-76 Part 05 Q17 005 
312-76 Part 05 Q17 006 -
ISO 17799 has two parts. The first part is an implementation guide with guidelines on how to build a comprehensive information security infrastructure and the second part is an auditing guide based on requirements that must be met for an organization to be deemed compliant with ISO 17799. What are the ISO 17799 domains?
Each correct answer represents a complete solution. Choose all that apply.
- Business continuity management
- Information security policy for the organization
- Personnel security
- System architecture management
- System development and maintenance
-
You are an Incident manager in Orangesect.Inc. You have been tasked to set up a new extension of your enterprise. The networking, to be done in the new extension, requires different types of cables and an appropriate policy that will be decided by you. Which of the following stages in the Incident handling process involves your decision making?
- Containment
- Preparation
- Identification
- Eradication
-
A Web-based credit card company had collected financial and personal details of Mark before issuing him a credit card. The company has now provided Mark’s financial and personal details to another company. Which of the following Internet laws has the credit card issuing company violated?
- Security law
- Privacy law
- Trademark law
- Copyright law
Subscribe
0 Comments
Newest