H12-224 : HCNP-R&S Fast Track (Huawei Certified Network Professional – Routing & Switching Fast Track) : Part 02
-
Which of the following standards defines STP?
- 802.1J
- 802.1X
- 802.1D
- 802.1P
-
Which statements about the PVID on the access interface are true?
- When receiving a packet without the VLAN tag, the interface adds the VLAN tag to the packet and sets the VID in the tag to the default VLAN ID.
- When receiving a packet with a VLAN tag, the interface compares the VLAN ID in the tag with the default VLAN ID. If they are the same, the interface forwards the packets; otherwise, the interface discards the packets.
- When the interface sends a packet with a VLAN tag that contains the default VLAN ID, the system removes the VLAN tag of the packet, and then forwards the packet.
- None of the above.
-
Which statement about ARP proxy is false?
- The ARP proxy, namely, the gateway, sends ARP request for the host. The MAC address in the ARP request packet is the MAC address of the host.
- The ARP proxy, namely, the gateway, sends ARP request for the host. The MAC address in the ARP request packet is the MAC address of its own interface.
- ARP proxy is also called promiscuous ARP or ARP hack.
- The ARP proxy allows the hosts on the networks with the same network ID to communicate with each other.
-
In RSTP network environment, a port can be set as edge port when it is directly connected with terminal.
- True
- False
-
Which of the following statements about STP Designated Port is true?
- Each of the bridge can have one Designated Port only.
- Designated Port is responsible for forwarding packets to its connected network segments.
- The only path leading to the Root Bridge is through Designated Port.
- Designated Port forwards the data packet from its corresponding switch to the Root Switch.
-
The following is the command output on a root switch of an MSTP region. How many switches are located in the MSTP region?
- Less than 10
- Less than 20
- Less than 30
- Less than 40
-
If an MSTP switch detects that the neighboring switch works in RSTP mode, which mode does the MSTP switch work?
- STP mode
- RSTP mode
- MSTP mode
- All of the above
-
When the GVRP registration mode is FIXED, which statement is true?
- VLANs can be manually created and registered on the interface, and can also be dynamically registered and deregistered on the interface.
- VLANs cannot be manually created and registered on the interface, but can be dynamically registered and deregistered on the interface.
- VLANs can be manually created and registered on the interface, but cannot be dynamically registered or deregistered on the interface.
- VLANs cannot be manually created and registered on the interface, and cannot be dynamically registered or deregistered on the interface.
-
In a switching network that has been enabled with STP protocol, the priorities of all the switches are the same. The MAC address of switch1 is 00-e0-fc-00-00-40, MAC address of switch2 is 00-e0-fc-00-00-10, MAC address of switch3 is 00-e0-fc-00-00-20, and MAC address of switch4 is 00-e0-fc-00-00-80. Which of the switches will be elected as the Root Bridge?
- Switch1
- Switch2
- Switch3
- Switch4
-
Which statements are false?
- The VLAN mapping function is usually configured on the edge node of a public network.
- The VLAN mapping function can save VLAN resources on a public network.
- VLAN mapping allows private networks on different VLANs to communicate with each other over the ISP network.
- VLAN mapping allows only the private networks on the same VLAN to communicate with each other.
-
After detecting a user with a new MAC address, the switch initiates an EAP authentication request. If the client does not respond and the MAC address bypass authentication is not configured, which statement is false?
- If the client does not respond after the number of authentication requests reaches a specified value, the switch considers that the client software is not installed.
- All permissions of the user are prohibited.
- The user is allowed to access only the isolated zone.
- Detection is initiated again after a period of time.
-
As shown in the figure, which switch is the root switch according to the configuration?
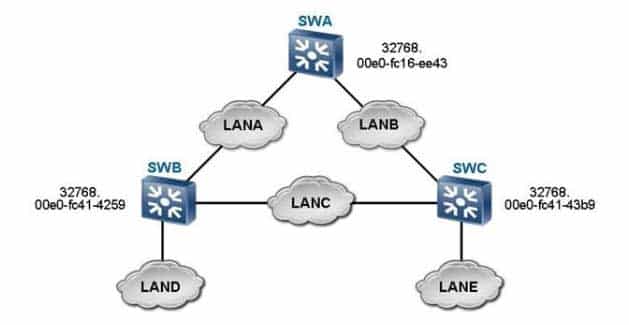
H12-224 HCNP-R&S Fast Track (Huawei Certified Network Professional – Routing & Switching Fast Track) Part 02 Q12 003 - SWA
- SWB
- SWC
- None of the above
-
The STP protocol can prevent broadcast storms caused by loops on the Layer 2 network.
- True
- False
-
According to the figure, what is the status of Ethernet1/0/13 in MSTI 1?
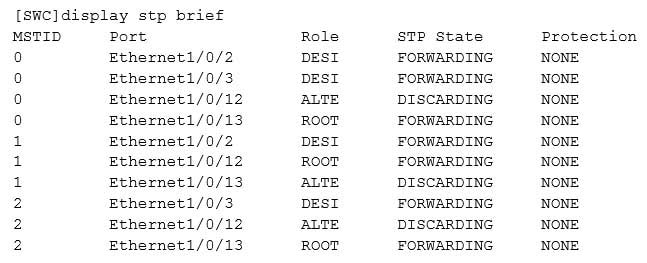
H12-224 HCNP-R&S Fast Track (Huawei Certified Network Professional – Routing & Switching Fast Track) Part 02 Q14 004 - Forwarding
- Discarding
- Learning
- None of the above
-
Which types of interfaces can be configured with selective QinQ? (Choose two.)
- Access interface
- Trunk interface
- Hybrid interface
- dot1q-tunnel interface
-
Which of the following statements about the link failure detection in STP protocol is not true?
- When network topology is stable, the Designated Port sends BPDU packet at every Hello Time interval.
- When network topology is stable, BPDU packets will be transmitted periodically.
- When the port does not receive new BPDU within a certain interval, the old configuration BPDU will time out and the link failure can be detected.
- The port sends Configuration BPDU at every Hello Time interval. When the link fails, Configuration BPDU cannot be sent out. As a result, this port can detect the link failure.
-
Which statement about the hybrid interface is true?
- A hybrid interface can only be connected to network device.
- A hybrid interface can only be connected to host.
- A hybrid interface can be connected to host or network device.
- A hybrid interface cannot be configured with VLAN ID.
-
Which statements are true? (Choose three.)
- Port isolation is a mechanism that controls the access between switch interfaces.
- Port isolation is an isolation mechanism at the physical layer.
- Port isolation prevents the computers connected to different ports from accessing each other.
- Port isolation can be configured based on VLANs.
-
On the RSTP network as shown in the figure, what RSTP operations will occur after the E1 port of SWB fails? (Choose three.)
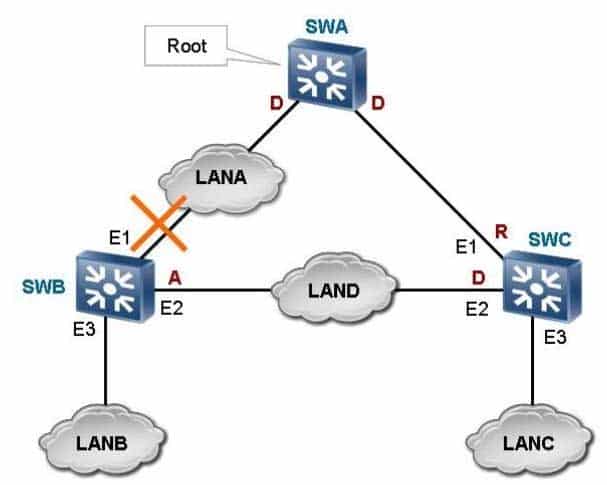
H12-224 HCNP-R&S Fast Track (Huawei Certified Network Professional – Routing & Switching Fast Track) Part 02 Q19 005 - SWB deletes the MAC address entries with the E1 port as the destination interface.
- The spanning tree is recalculated and the E2 port is elected as the new root port.
- All the interfaces in forwarding state send topology change notifications (TCNs) to notify other switches of the topology change.
- All the non-edge ports in forwarding state send TCNs to notify other switches of the topology change.
-
According to the MSTP protocol, each MST instance calculates an independent spanning tree by using the RSTP algorithm.
- True
- False
Subscribe
0 Comments
Newest