IT Essentials 8 Chapter 12 Exam Answers | IT Essentials 7 Chapter 12 Exam Answers Full 100% 2023 2024
This is serial collection of Cisco NetAcad ITE 8, ITE 8.0, ITE 8.01, ITE 7, ITE 7.0, ITE 7.02, ITE v8, ITE v8.0, ITE v8.01, ITE v7, ITE v7.0, ITE v7.02, ITE Version 8, ITE Version 8.0, ITE Version 8.01, ITE Version 7, ITE Version 7.0, ITE Version 7.02, IT Essentials 8, IT Essentials 7.02, IT Essentials 8.01, IT Essentials 7, IT Essentials 7.0, and IT Essentials 8.0 Chapter 12 Exam Answers in 2023 2024. We also combine two more versions of IT Essentials (Version 8.0) – IT Essentials 8.0 Chapter 12 exam answers and IT Essentials (Version 7.00) – IT Essentials 7.0 Chapter 12 exam answers in the page too. All questions and answers were verified by experts to get the full 100%.
| IT Essentials 8 & ITE 7.02 | |
| Final Exam Answers Ch 1 - 9 | |
| Final Exam Answers Ch 10 - 14 | |
| Final Exam Composite Answers Ch 1 - 14 | |
| IT Essentials 8 & ITE 7.02 - Chapter 12 | |
| Chapter 12 Exam Answers | Online Test |
| Chapter 12 Exam Answers | Online Test |
| Checkpoint Exam #4 (Chapters 10 – 11) Answers | |
| IT Essentials 8 & ITE 7.02 - Chapter 13 | |
| Chapter 13 Exam Answers | Online Test |
| Chapter 13 Quiz Answers | Online Test |
| IT Essentials 8 & ITE 7.02 - Lab Answers | |
| 12.1.2.2 Lab – Working with Android Answers | |
| 12.1.3.2 Lab – Working with iOS Answers | |
| 12.1.4.4 Lab – Mobile Device Features Answers | |
| 12.2.1.2 Lab – Passcode Locks Answers | |
| 12.4.2.4 Lab – Troubleshoot Mobile Devices Answers | |
| 13.2.3.7 Lab – Bitlocker and Bitlocker To Go Answers | |
ITE 8 Chapter 12 Exam Answers | ITE 7 Chapter 12 Exam Answers Full 100% 2023 2024
-
Which two location data sources can locator apps use to determine the position of a mobile device? (Choose two.)
- cellular towers
- WiFi hotspots
- the sandbox
- remote lock
- an app source
Answers Explanation & Hints:
In addition to GPS, mobile device locator apps can use cellular towers and WiFi hotspots to determine the position of a mobile device. The device sandbox, remote lock, or an app source (Play Store or iTunes) are other features and functions related to security and app downloading.
-
What are two ways that iOS differs from Android? (Choose two.)
- iOS uses an All Apps button whereas Android uses a Home button.
- iOS has a physical Home button, but Android uses navigation icons.
- In iOS, the icon for an app represents the app itself. Deleting the icon in iOS deletes the app. In Android, the icon on the Home screen is a shortcut to the app.
- In iOS, apps can only appear on screens, whereas in Android, apps can appear on screens and in folders.
- In iOS, folders are created by dragging one app on top of another app, but in Android folders must be created from the home screen menu.
Answers Explanation & Hints:
Apple iOS devices have a physical Home button that has many uses. One of the uses of the Home button is navigation between screens. Android uses navigation icons instead of a physical Home button. In addition, much like a Windows OS, apps in Android are represented by icons that are shortcuts to the actual app. In iOS, the icons are the apps. Deleting an icon in Android deletes only the shortcut. However, the entire app is deleted from an iOS device when its icon is deleted.
-
What are two purposes of the passcode lock feature on mobile devices? (Choose two.)
- to help prevent theft of private information
- to prevent unauthorized use of the device
- to erase all personal data from the device
- to return the device to the default factory state
- to restore and re-synchronize the device
- to remotely lock the device if it is stolen
Answers Explanation & Hints:
The passcode lock feature on mobile devices helps prevent theft of private information and places the device into a power saving state. Personal data will not usually be erased from some mobile devices unless the number of failed passcode login attempts exceeds a threshold. Remote lock allows the device to be locked from a remote location. A factory reset returns the device to the original operation state when the device was first purchased. Various applications such as email or cloud storage can provide synchronization capabilities to be able to restore and re-synchronize information such as user data, contacts, and email on a mobile device.y other device features and actions.
-
Refer to the exhibit. What two statements are true about the mobile operating system screen shown? (Choose two.)
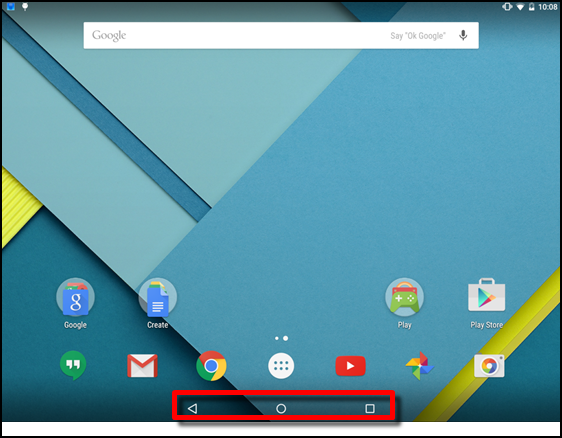
ITE v8.0 – IT Essentials ( Version 8.0) – IT Essentials 8 Chapter 12 Exam Answers 01 - The area enclosed by the red rectangle contains navigation icons.
- The area that is highlighted displays background processes and indicators.
- This is a Windows Phone screen.
- This is an Android screen.
- This is an iOS screen.
Answers Explanation & Hints:
The highlighted area shows the Android operating system navigation icons. From left to right they are Back, Home, and Recent Apps.
-
Which two methods are commonly used to remove the default restrictions and protections added to mobile operating systems? (Choose two.)
- rooting
- jailbreaking
- rootkit execution
- device update
- system backup
Answers Explanation & Hints:
Mobile operating systems are usually protected by a number of software restrictions. Rooting and jailbreaking are two methods for removing restrictions and protections added to mobile operating systems. They are a means of circumventing the usual operation of the device operating system to gain superuser or root administrator permissions.
-
A Linux administrator wants to backup current files in a data directory and store them in a new directory on another disk. Which two commands would be needed? (Choose two.)
- cd
- cp
- rm
- mv
- mkdir
Answers Explanation & Hints:
The mkdir command is used to create the new directory and the cp command is used to copy files from one directory to another.
-
A file called new_resume has the following file permissions: rw-r-x–x . What two facts can be determined from these permissions? (Choose two.)
- The user has full access to the file.
- Members of the group have read and execute access to the file.
- Other people have read and execute access to the file.
- Group members are able to modify the file.
- The user is able to read and modify the file.
- Other people have no access to the file.
Answers Explanation & Hints:
Read, write, and execute permissions are assigned to each file. The permissions are listed in groups of three. The first group of three permissions references users, the second references group members, and the third references others. The first position of each of the three permissions is the R or read permission, the second is the W or write permission, and the third is the X or execute permission. If any position has a dash, the associated group does not have permission for that category. In this case, the user hasread and write access ( rw- ). Group members haveread and execute access ( r-x ). Other people haveexecute only access ( –x) .
-
What is a good source for safely downloading Android apps?
- iTunes
- Google Play
- freeware sites
- the Apple App Store
Answers Explanation & Hints:
Google Play ensures that the app is compatible with the mobile device and is a trusted source for apps.
-
What represents apps in the Windows Phone interface?
- buttons
- icons
- tiles
- widgets
Answers Explanation & Hints:
The Windows Phone OS uses tiles to represent apps. Tiles are rectangles that can display active content. When tapped, they open the associated app. Tiles can be resized to unclutter screens and to reflect the relative importance of the app.
-
What is the result of doing a factory reset on a mobile device?
- The operating system will be updated with the most recent updates and patches.
- All user data and settings will be deleted.
- The operating system will be deleted and all user data is transferred to the Cloud.
- A complete backup of the device is done and all viruses and malware are removed.
Answers Explanation & Hints:
After a factor reset, a mobile device is left in the same state that it was when it left the factory. The operating system software would not be altered but all user data, settings, and third party applications would be deleted. Backups should be done prior to a factory reset. Updates or patches to the operating system could be done before or after the factory reset.
-
What is Wi-Fi calling?
- a method used to push apps to smartphones
- a convenient way to securely and digitally make payments with mobile devices
- a government emergency alert service for smartphones
- a way to make mobile phone calls over a wireless data network
- a method for sharing data between two mobile devices
Answers Explanation & Hints:
Wi-Fi calling is a way that a mobile phone can use a wireless data network to make phone calls as if it were connected to a cellular network. In cases where cell phone coverage is inadequate, calls can be placed from places that have open Wi-Fi networks.
-
What is the purpose of signature files used to secure mobile devices and operating systems?
- They contain a record of historical and pending firmware and software updates.
- They contain a list of all user passwords.
- They contain a log of digital certificates and encryption keys associated with the user.
- They contain sample code from known viruses and malware that is used by security software to identify malicious software.
Answers Explanation & Hints:
Antivirus and antimalware software compare the contents of a disk with sample virus and malware code included in signature files. If a comparison is found, the user can be notified and the virus can be isolated or removed.
-
What is a purpose of the boot manager program?
- It manages antivirus signature files, encryption keys, and certificates when a device boots.
- It automates the POST and checks the disk for bad sectors during a boot.
- It checks the validity of hardware and software on the device after a factory reset.
- It allows the user to select the OS to use to boot the device.
- It allows the user to determine which apps are automatically opened during the boot process.
Answers Explanation & Hints:
Many devices have multiple operating systems installed in different partitions. When a device boots, the boot manager asks the user to select the OS to use. The boot manager then directs the BIOS to the correct partition so that the device can continue to boot by using the selected OS.
-
An administrator is re-imaging a large number of Mac OS X machines. What built-in tool or command can be used to remotely boot the computers?
- mstsc
- Netboot
- Time Machine
- Finder
Answers Explanation & Hints:
Netboot is a built-in tool on the Mac OS that allows for remotely booting the computers. Finder is similar to the Windows File Explorer tool and is used to navigate the Mac OS file system. MSTSC is used to open the Windows Remote Desktop utility. Time Machine is an automatic backup utility built into the Mac OS.
-
What tool or command is used in the Mac OS X to navigate the file system?
- File Explorer
- Task Manager
- Finder
- mstsc
Answers Explanation & Hints:
Finder is similar to the Windows File Explorer tool and is used to navigate the Mac OS file system. The mstsc command is used to open the Windows Remote Desktop utility. The Task Manager tool on Windows allows a user to view all running applications.
-
Which model does Apple use to provide iOS apps to customers?
- iCloud
- Xcode
- sandbox
- walled garden
Answers Explanation & Hints:
Apple uses a walled garden model for the iOS apps. The apps must be submitted to and approved by Apple before they are released to users.
-
Android apps run primarily based on privileges enabled by the user. Sometimes an Android app requires extra privileges to access system components. How do
- Android apps run to accomplish both situations?
- Android apps run in a sandbox.
- Android apps run in a guest mode.
- Android apps run in a walled garden.
- Android apps run through a proxy service.
Answers Explanation & Hints:
Android apps run in a sandbox and have only the privileges enabled by the user. If an app needs to obtain permissions, a prompt will appear and the user can grant permissions through settings.
-
Which navigation icon on the system bar of an Android device is used to return to the previous screen?
- Back
- Home
- Menu
- Recent Apps
Answers Explanation & Hints:
The Back icon, if pressed, returns to the previous screen.
-
Which statement describes the iOS app icons on a mobile device screen?
- Each icon is a shortcut of the app.
- Each icon represents the actual app.
- Each icon represents an instance of the actual app.
- Each icon links to multiple instances of the actual app.
Answers Explanation & Hints:
On the iOS interface, each app on screen is the actual app, not a shortcut.
-
What is the purpose of using the auto-brightness feature on a mobile device with an LCD screen?
- to conserve battery power
- to reduce the interference from sunlight
- to prevent the burn-in effect on the screen
- to display text messages with better contrast
Answers Explanation & Hints:
The LCD screen for most mobile devices uses the most battery power. Lowering the brightness or using the auto-brightness feature helps conserve battery power.
-
Which statement describes the Touch ID in iOS devices?
- It is used as the passcode.
- It is the encryption key set by the user.
- It is the hash value of the user fingerprint.
- It is used to set the touch screen sensitivity.
Answers Explanation & Hints:
Apple uses a technology known as Touch ID in which the user sets up a template fingerprint scan that is converted into a unique hash and stored within a secure cache on the iOS device. The hash is used to authenticate with the user.
-
Which cloud-based storage service does Microsoft provide for backups?
- iCloud
- Dropbox
- OneDrive
- Google Sync
Answers Explanation & Hints:
Data on mobile devices must be backed up periodically to ensure that it can be recovered if needed. Most mobile operating systems come with a user account linked to the cloud services of the vendor, such as iClould for iOS, Google Sync for Android, and OneDrive for Microsoft.
-
A mobile device user notices that the system update includes an update of the Primary Rate ISDN (PRI). What is the function of the PRI?
- It is the configuration of radio frequencies used on the device.
- It is the data rate setting of the user account with the carrier service.
- It is the configuration of the data rates between the device and the cell tower.
- It is the configuration information that the device needs to communicate on networks other than the carrier network.
Answers Explanation & Hints:
In addition to mobile operating system updates, there are two other types of updates for mobile device radio firmware. They are called baseband updates and consist of the Preferred Roaming List (PRL) and the Primary Rate ISDN (PRI). The PRL is configuration information that a cellular phone needs to communicate on networks other than the carrier network. The PRI configures the data rates between the device and the cell tower. This ensures that the device is able to communicate with the tower at the correct rate.
-
A Linux PC user notices that the PC freezes on startup and exhibits kernel panic where there is a stop screen. What is a possible cause for the issue?
- LILO has been deleted.
- GRUB has been corrupted.
- A driver has become corrupted.
- Deja Dup has been turned off in the system.
Answers Explanation & Hints:
When a driver in a Linux system has been corrupted or a piece of hardware is failing, the system will freeze on startup and exhibits kernel panic where there is a stop screen.
-
What command is used to open a text editor in a Linux system?
- grep
- ifconfig
- ls
- vim
Answers Explanation & Hints:
The vim command is used to open a text editor; ls displays files within a directory; grep searches for strings of characters within a file; and ifconfig displays information about the network interface card.
-
Which Linux file system introduced the journaled file system, which can be used to minimize the risk of file system corruption in the event of a sudden power loss?
- ext2
- ext3
- CDFS
- NFS
Answers Explanation & Hints:
The ext3 file system is considered a journaled file system that was designed to improve the existing ext2 file system. A journal, the main feature added to ext3, is a technique used to minimize the risk of file system corruption in the event of sudden power loss.
-
What is the most commonly used method to close an application that appears to be frozen on an OS X-based computer?
- Use Force Quit .
- Use Task Manager .
- Access the Status menu.
- Access the Notification Center .
Answers Explanation & Hints:
To use Force Quit, right-click on the application icon that is not responding from the Dock and close the application.
-
Which file system is the primary file system used by Apple in current Macintosh computers?
- ext2
- ext3
- CDFS
- HFS+
- APFS
Answers Explanation & Hints:
The primary file system used by Apple in its lates Macintosh computers is APFS.
-
An instructor is discussing facts about different mobile device operating software. The instructor states: “The mobile devices have a feature called Spotlight that is a search tool that provides information from many sources.” To which OS does this relate: iOS, Android, or both?
- iOS
- Android
- both
-
An instructor is discussing facts about different mobile device operating software. The instructor states: “This OS uses the system bar, displayed at the bottom of every screen, to navigate apps and screens.” To which OS does this relate: iOS, Android, or both?
- Android
- iOS
- both
-
An instructor is discussing facts about different mobile device operating software. The instructor states: “This OS can be used by programmers to operate devices like laptops, smart TVs, and e-book readers.” To which OS does this relate: iOS, Android, or both?
- Android
- iOS
- both
-
An instructor is discussing facts about different mobile device operating software. The instructor states: “The icon on the Home screen is a shortcut to the app.” To which OS does this relate: iOS, Android, or both?
- Android
- iOS
- both
-
An instructor is discussing facts about different mobile device operating software. The instructor states: “WIFI hotspots are a location data source that can be used by locator apps to determine the position of a mobile device.” To which OS does this relate: iOS, Android, or both?
- both
- iOS
- Android
-
An instructor is discussing facts about different mobile device operating software. The instructor states: “Remote backups are a cloud-enabled service for mobile devices.” To which OS does this relate: iOS, Android, or both?
- both
- iOS
- Android
-
An instructor is discussing facts about different mobile device operating software. The instructor states: “GPS signals are used to enable geocaching, geotagging and device tracking on these mobile devices.” To which OS does this relate: iOS, Android, or both?
- both
- iOS
- Android
-
An instructor is discussing facts about different mobile device operating software. The instructor states: “The start voice control function can be performed with the home button.” To which OS does this relate: iOS, Android, or both?
- iOS
- Android
- both
-
An instructor is discussing facts about different mobile device operating software. The instructor states: “To synchronize a mobile device to a PC, iTunes must be installed on the PC.” To which OS does this relate: iOS, Android, or both?
- iOS
- Android
- both
-
An instructor is discussing facts about different mobile device operating software. The instructor states: “When the device roams out of the range of any Wi-Fi networks, it can connect to the cellular data network if this feature is enabled.” To which OS does this relate: iOS, Android, or both?
- both
- iOS
- Android
| IT Essentials 8 & ITE 7.02 | |
| Final Exam Answers Ch 1 - 9 | |
| Final Exam Answers Ch 10 - 14 | |
| Final Exam Composite Answers Ch 1 - 14 | |
| IT Essentials 8 & ITE 7.02 - Chapter 12 | |
| Chapter 12 Exam Answers | Online Test |
| Chapter 12 Exam Answers | Online Test |
| Checkpoint Exam #4 (Chapters 10 – 11) Answers | |
| IT Essentials 8 & ITE 7.02 - Chapter 13 | |
| Chapter 13 Exam Answers | Online Test |
| Chapter 13 Quiz Answers | Online Test |
| IT Essentials 8 & ITE 7.02 - Lab Answers | |
| 12.1.2.2 Lab – Working with Android Answers | |
| 12.1.3.2 Lab – Working with iOS Answers | |
| 12.1.4.4 Lab – Mobile Device Features Answers | |
| 12.2.1.2 Lab – Passcode Locks Answers | |
| 12.4.2.4 Lab – Troubleshoot Mobile Devices Answers | |
| 13.2.3.7 Lab – Bitlocker and Bitlocker To Go Answers | |