ITE 8 Module 11 Quiz – 11.8.2 Windows Configuration Quiz Answers 2025 Full 100%
ITE 8 Module 11 Quiz – 11.8.2 Windows Configuration Quiz Answers 2025 Full 100%
This is the ITE 8 Module 11 Quiz – 11.8.2 Windows Configuration Quiz Answers 2025 Full 100% collection for IT Essentials 8.0 Chapter 11 Quiz. It includes the latest 2025 updates, carefully compiled by experts with detailed explanations to enhance understanding.
| IT Essentials 8 | |
| Final Exam Answers Ch 1 - 9 | |
| Final Exam Answers Ch 10 - 14 | |
| Final Exam Composite Answers Ch 1 - 14 | |
| IT Essentials 8 Chapter 11 | |
| Chapter 11 Exam Answers | Online Test |
| Chapter 11 Quiz Answers | Online Test |
| IT Essentials 8 Chapter 12 | |
| Chapter 12 Exam Answers | Online Test |
| Chapter 12 Quiz Answers | Online Test |
| Checkpoint Exam #4 (Chapters 10 – 11) Answers | Online Test |
IT Essentials v8 Module 11 Quiz – 11.8.2 Windows Configuration Quiz Answers 2025 Full 100%
-
Why would an administrator use Windows Remote Desktop and Windows Remote Assistant?
- to provide secure remote access to resources on another network
- to connect to a remote computer over the network to control its applications and data
- to enable sharing of files and presentations with a group of users over the Internet
- to connect to an enterprise network across an unsecured connection and act as a local client of that network
Answers Explanation & Hints: Windows Remote Desktop and Remote Assistant allow an administrator to connect a local computer with a remote computer across the network and to interact with it as though it were the local computer. The administrator sees and can interact with the desktop of the remote computer. With Remote Desktop, the administrator logs onto the remote computer using an existing user account and starts a new user session. No user is required at the remoter computer to allow this access. With Remote Assistant, the purpose is for a technician to interact with a remote computer with the assistance of a remote user. The remote user must allow the remote access to the current user session and is able to observe what the technician is doing.
-
How many Libraries are created for each user by default on a new Windows 10 installation?
- 6
- 4
- 5
- 2
Answers Explanation & Hints: When Windows 10 is installed, it creates six default libraries for each user.
-
What are two file attributes in the Windows environment? (Choose two.)
- read-only
- archive
- security
- general
- details
Answers Explanation & Hints: The file attributes are read-only, archive, hidden, and system. Details, security, and general are tabs on the file Properties applet.
-
A help desk technician is talking to a user to clarify a technical problem that the user is having. What are two examples of open-ended questions that the technician might use to help determine the issue? (Choose two.)
- What updates have you performed lately?
- Can you boot the operating system?
- Has anyone else used the computer recently?
- Can you boot up in safe mode?
- What happens when you try to access your files?
Answers Explanation & Hints: Close-ended questions generally have a fixed or limited set of possible responses, such as “yes” or “no”. Open-ended questions imply no limited or fixed set of replies but rather generally prompt the responder to provide more meaningful feedback.
-
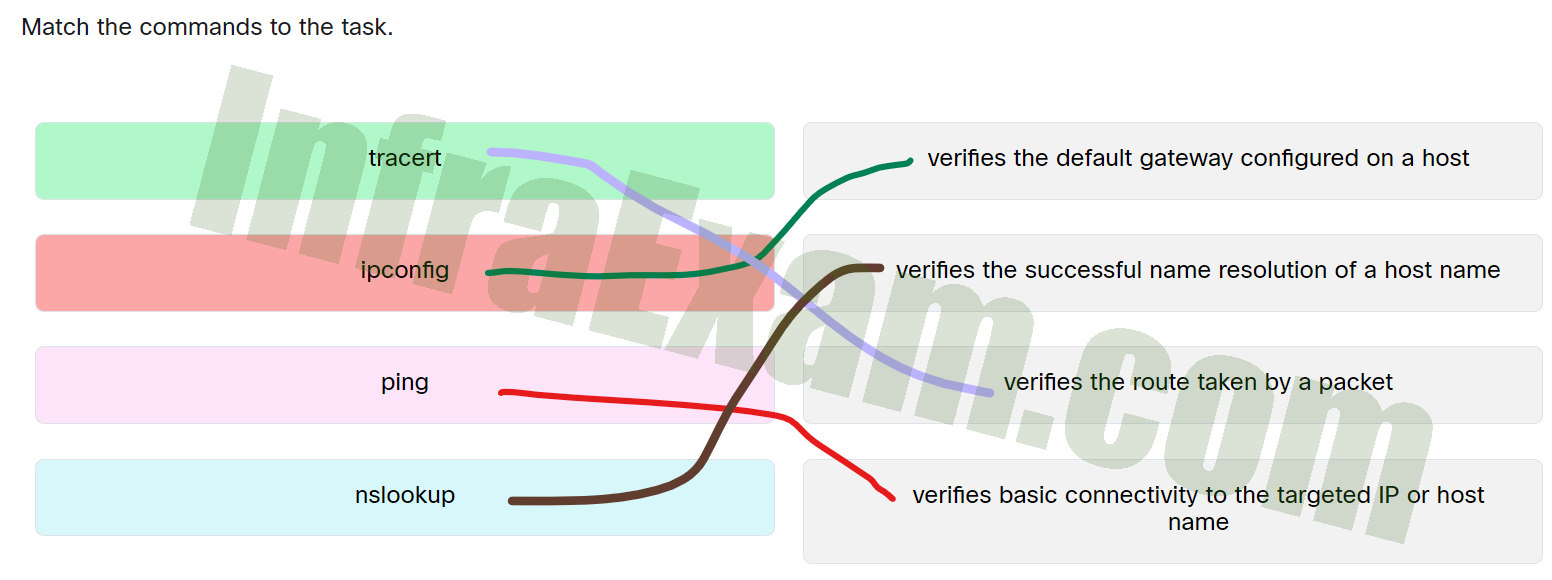
Match the commands to the task.
ITE 8 + ITE 7.0 Chapter 11 Quiz Answers 11.8.1.2 Windows Configuration Quiz Answers 01 - ping —> verifies basic connectivity to the targeted IP or host name
- nslookup —> verifies the successful name resolution of a host name
- tracert —> verifies the route taken by a packet
- ipconfig —> verifies the default gateway configured on a host
Answers Explanation & Hints: Place the options in the following order:
Ipconfig Verifies the default gateway configured on a host Nslookup Verifies the successful name resolution of a host name Tracert Verifies the route taken by a packet Ping Verifies basic connectivity to the targeted IP or host name
-
In which folder are application files for 32-bit programs typically located on a computer that is running a 64-bit edition of Windows 7?
- C:\Application Data
- C:\Program Files
- C:\Users
- C:\Program Files (x86)
Answers Explanation & Hints: The C:\users folder contains all the user profiles. The C:\Application Data folder contains application data related to all users. The 32 bit program files are located in the C:\Program Files(x86) folder while 64 bit program files are located in the C:\Program Files folder.
-
A user notices that some of the programs that are installed before upgrading to Windows 7 no longer function properly. What can the user do to fix this problem?
- Change the file system to FAT16.
- Lower the UAC setting in the Change User Account Control settings dialog box of the User Accounts control.
- Reinstall the programs in Compatibility Mode.
- Update the driver for the graphics card.
Answers Explanation & Hints: UAC is used to change user account settings while converting the file system to FAT16 and updating the driver for the graphics card will not resolve the issue. Compatibility mode in Windows 7 allows for the running of a program created for previous versions of the Windows environment.
-
A corporation has expanded to include multiple remote offices around the globe. Which technology should be used to allow the remote offices to communicate and share network resources privately?
- Remote Desktop
- Remote Assistance
- administrative share
- VPN
Answers Explanation & Hints: A Virtual Private Network (VPN) is used to connect remote sites together securely over a public network.
-
A user logs into Active Directory on a workstation and the user home directory does not redirect to a network share on a file server. A technician suspects that the group policy setting is incorrect. Which command can the technician use to verify the group policy settings?
- rstrui
- tasklist
- runas
- gpupdate
- gpresult
Answers Explanation & Hints: The functions of the listed commands are as follows:
- runas – runs a program or tool with different permissions
- rstrui – starts the System Restore utility
- gpresult – displays group policy settings
- gpupdate – refreshes group policy settings
- tasklist – displays currently running applications
-
Which Windows utility can be used to schedule a regular backup for preventive maintenance?
- Windows Task Manager
- Disk Cleanup
- System Restore
- Windows Task Scheduler
Answers Explanation & Hints: Windows Task Scheduler is a tool that helps scheduling repetitive tasks, such as backups, antivirus scans, and more.
-
Which two issues are likely to cause BSOD errors? (Choose two.)
- power supply failure
- lack of antivirus software
- device driver errors
- RAM failing
- out-of-date browser
Answers Explanation & Hints: Device driver errors are the most likely cause of BSOD errors. Failing RAM can also create BSOD errors. Software issues such as browsers and antivirus do not produce BSOD errors. A power supply failure would prevent the machine from starting.
-
A user wants to configure a password on a Windows 10 PC when the PC is woken from hibernation. Where can the user configure this?
- Control Panel, Power Options
- Settings, Privacy
- Settings, Accounts
- Control Panel, User Accounts
Answers Explanation & Hints: In Windows 10, the configuration of a password for a PC woken from hibernation or sleep can be set in Settings->Accounts.
-
Which TCP port number would be used for remotely connecting to a network switch and configuring it via an unencrypted connection?
- 20
- 22
- 3389
- 443
Answers Explanation & Hints: The server listens on TCP port 3389 and UDP port 3389 for remote connections.
-
A technician notices that an application is not responding to commands and that the computer seems to respond slowly when applications are opened. What is the best administrative tool to force the release of system resources from the unresponsive application?
- Event Viewer
- Add or Remove Programs
- System Restore
- Task Manager
Answers Explanation & Hints: Use the Task Manager Performance tab to see a visual representation of CPU and RAM utilization. This is helpful in determining if more memory is needed. Use the Applications tab to halt an application that is not responding.
-
What are three common causes of operating systems problems? (Choose three.)
- a corrupted registry
- loose cable connections
- virus infection
- CMOS battery problem
- incorrect IP addressing information
- failed service pack installation
Answers Explanation & Hints: Typical causes of operating system problems are as follows:
- corrupted or missing system files
- incorrect device driver
- failed update or service pack installation
- corrupted registry
- failing of faulty hard drive
- incorrect password
- virus infection
- spyware
-
What is true about restore points?
- Restore points should always be created before making changes to a system.
- Restore points back up personal data files.
- Once System Restore is used to restore a system, the change is irreversible.
- Restore points recover corrupted or deleted data files.
Answers Explanation & Hints: Any change from a system restore is reversible. A restore point only contains information about the system and registry settings and therefore cannot be used to backup or recover data files.
-
After solving a problem on a computer, a technician checks the event log to ensure that there are no new error messages. At which step of the troubleshooting process is this action taking place?
- Determine an exact cause.
- Establish a theory of probable cause.
- Verify the solution and full system functionality.
- Document the findings.
Answers Explanation & Hints: In this situation, the probable cause has been identified and the exact cause has been acted upon. Documenting the findings is the last action in the process and happens after checking that the problem has been solved by the solution implemented.
-
A technician is designing a hardware preventive maintenance plan for a company. Which strategy should be included in the plan?
- Only clean equipment that is requested by the customer.
- Avoid performing maintenance operations on plug and play devices that are controlled by the operating system.
- Schedule and document routine maintenance tasks.
- Omit performing maintenance operations on components until the equipment malfunctions.
Answers Explanation & Hints: The type of tasks that need to be scheduled include operating system and antivirus updates as well as hard drive routines.
-
In which folder are application files for 32-bit programs typically located on a computer that is running a 64-bit edition of Windows 10?
- C:\Users
- C:\Program Files
- C:\Application Data
- C:\Program Files (x86)
Answers Explanation & Hints: The C:\users folder contains all the user profiles. The C:\Application Data folder contains application data related to all users. The 32-bit program files are located in the C:\Program Files(x86) folder while 64-bit program files are located in the C:\Program Files folder.
| IT Essentials 8 | |
| Final Exam Answers Ch 1 - 9 | |
| Final Exam Answers Ch 10 - 14 | |
| Final Exam Composite Answers Ch 1 - 14 | |
| IT Essentials 8 Chapter 11 | |
| Chapter 11 Exam Answers | Online Test |
| Chapter 11 Quiz Answers | Online Test |
| IT Essentials 8 Chapter 12 | |
| Chapter 12 Exam Answers | Online Test |
| Chapter 12 Quiz Answers | Online Test |
| Checkpoint Exam #4 (Chapters 10 – 11) Answers | Online Test |