Network Security (Version 1) – Network Security 1.0 Modules 15-17: Cryptography Group Exam Answers 2025
Network Security (Version 1) – Network Security 1.0 Modules 15-17: Cryptography Group Exam Answers 2025
| Network Security 1.0 | |
| Final Exam Answers | |
| This Chapters 15 - 17 | |
| Chapters 15 - 17 Exam Answers | Online Test |
| Next Chapters 18 - 19 | |
| Chapters 18 - 19 Exam Answers | Online Test |
-
Which requirement of secure communications is ensured by the implementation of MD5 or SHA hash generating algorithms?
- confidentiality
- authentication
- integrity
- nonrepudiation
Answers Explanation & Hints: Integrity is ensured by implementing either MD5 or SHA hash generating algorithms. Many modern networks ensure authentication with protocols, such as HMAC. Data confidentiality is ensured through symmetric encryption algorithms, including DES, 3DES, and AES. Data confidentiality can also be ensured using asymmetric algorithms, including RSA and PKI.
-
What is another name for confidentiality of information?
- privacy
- accuracy
- consistency
- trustworthiness
Answers Explanation & Hints: Privacy is another name for confidentiality. Accuracy, consistency, and trustworthiness describe integrity of data.
-
As data is being stored on a local hard disk, which method would secure the data from unauthorized access?
- data encryption
- a duplicate hard drive copy
- deletion of sensitive files
- two factor authentication
Answers Explanation & Hints: Data encryption is the process of converting data into a form where only a trusted, authorized person with a secret key or password can decrypt the data and access the original form.
-
What popular encryption algorithm requires that both the sender and receiver know a pre-shared key?
- PKI
- MD5
- HMAC
- AES
Answers Explanation & Hints: MD5 is a hashing algorithm that guarantees that no one intercepted the message and altered it. Advanced Encryption Standard (AES) is a popular symmetric encryption algorithm where each communicating party needs to know the pre-shared key. Public key infrastructure (PKI) is an asymmetric encryption algorithm based on the assumption that the two communicating parties have not previously shared a secret key. HMAC is a hash message authentication code that guarantees that the message is not a forgery and actually comes from the authentic source.
-
The following message was encrypted using a Caesar cipher with a key of 2:
fghgpf vjg ecuvng
What is the plaintext message?
- defend the region
- invade the castle
- defend the castle
- invade the region
Answers Explanation & Hints: The Caesar cipher was a simple substitution cipher. In this example, if the key is 2, the letter d was moved two spaces to the right, resulting in an encoded message that used the letter f in place of the letter d . The letter g would be the substitute for the letter e , and so on. So, the resulting plaintext is f= d , g= e , h= f , g= e , p= n , f= d , v= t , j= h , g= e , e= c , c= a , u= s , v= t , n= l , g= e .
-
What is an example of the one-time pad cipher?
- RC4
- rail fence
- Caesar
- Vigenère
Answers Explanation & Hints: RC4 is an example of the one-time pad cipher, and it is widely used on the Internet. The Caesar cipher is a simple substitution cipher, and the Vigenère cipher is based on the Caesar cipher. An example of a transposition cipher is the rail fence cipher.
-
In which method used in cryptanalysis does the attacker know a portion of the plaintext and the corresponding ciphertext?
- brute-force
- ciphertext
- chosen-plaintext
- meet-in-the-middle
Answers Explanation & Hints: There are several methods used in cryptanalysis:Brute-force – The attacker tries every possible key knowing that eventually one of them will work.
Ciphertext – The attacker has the ciphertext of several messages encrypted but no knowledge of the underlying plaintext.
Known-Plaintext – The attacker has access to the ciphertext of several messages and knows something about the plaintext underlying that ciphertext.
Chosen-Plaintext – The attacker chooses which data the encryption device encrypts and observes the ciphertext output.
Chosen-Ciphertext – The attacker can choose different ciphertext to be decrypted and has access to the decrypted plaintext.
Meet-in-the-Middle – The attacker knows a portion of the plaintext and the corresponding ciphertext.
-
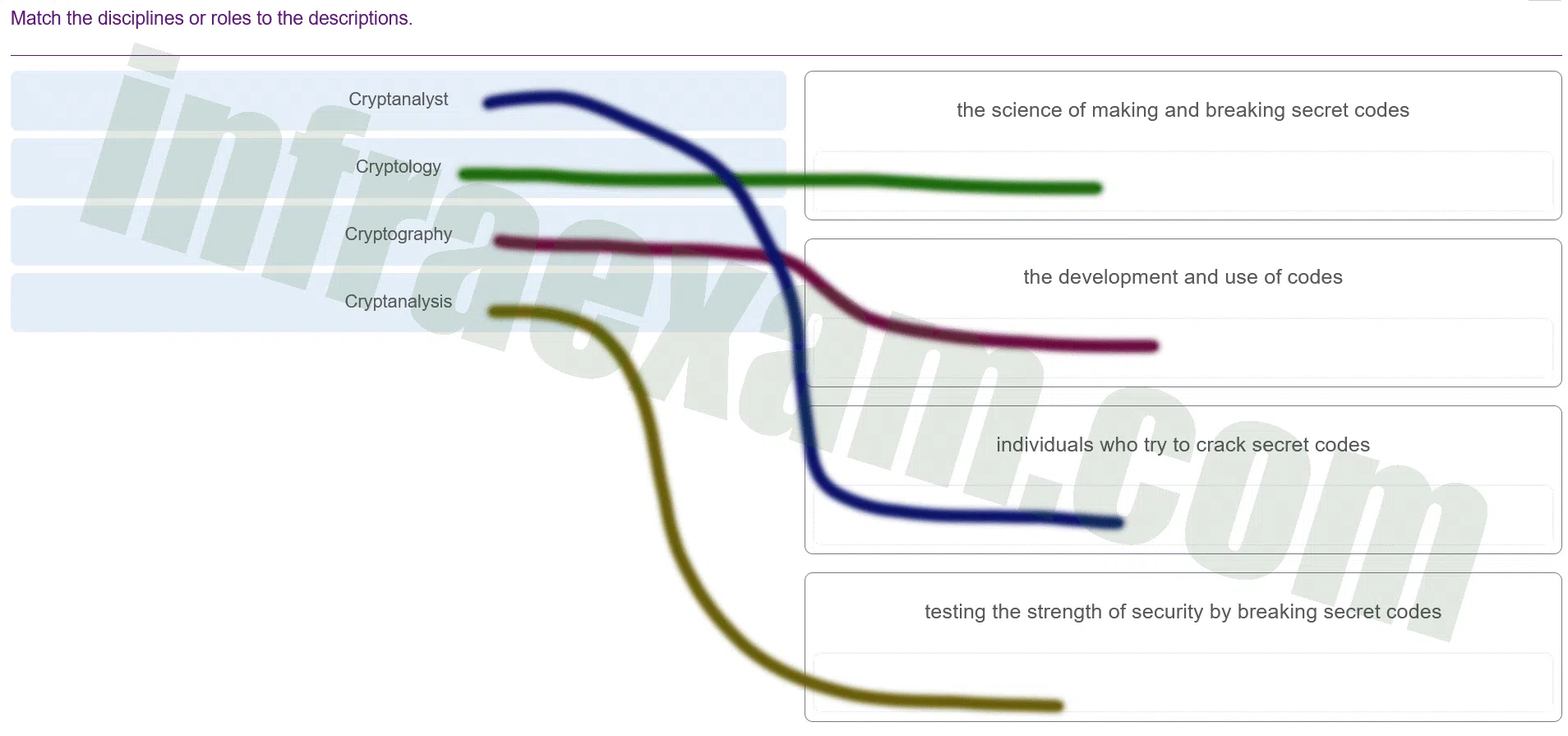
Match the disciplines or roles to the descriptions.
Network Security (Version 1) – Network Security 1.0 Modules 15-17 Cryptography Group Exam Answers 001 -
What are two properties of a cryptographic hash function? (Choose two.)
- Complex inputs will produce complex hashes.
- Hash functions can be duplicated for authentication purposes.
- The output is a fixed length.
- The input for a particular hash algorithm has to have a fixed size.
- The hash function is one way and irreversible.
Answers Explanation & Hints: A cryptographic hash function should have the following properties:The input can be any length.
The output has a fixed length.
The hash value is relatively easy to compute for any given input.
The hash is one way and not reversible.
The hash is collision free, meaning that two different input values will result in different hash values
-
A company is developing a security policy for secure communication. In the exchange of critical messages between a headquarters office and a branch office, a hash value should only be recalculated with a predetermined code, thus ensuring the validity of data source. Which aspect of secure communications is addressed?
- data integrity
- non-repudiation
- data confidentiality
- origin authentication
Answers Explanation & Hints: Secure communications consists of four elements: Data confidentiality – guarantees that only authorized users can read the message
Data integrity – guarantees that the message was not altered
Origin authentication – guarantees that the message is not a forgery and does actually come from whom it states
Data nonrepudiation – guarantees that the sender cannot repudiate, or refute, the validity of a message sent
-
Which algorithm can ensure data integrity?
- MD5
- AES
- RSA
- PKI
Answers Explanation & Hints: Data integrity guarantees that the message was not altered in transit. Integrity is ensured by implementing either of the Secure Hash Algorithms (SHA-2 or SHA-3). The MD5 message digest algorithm is still widely in use.
-
What is the keyspace of an encryption algorithm?
- the mathematical equation that is used to create a key
- the set of all possible values used to generate a key
- the set of procedures used to calculate asymmetric keys
- the set of hash functions used to generate a key
Answers Explanation & Hints: The keyspace of an encryption algorithm is the set of all possible key values. Keys with n bits produce a keyspace with 2^ n possible key values.
-
Which two items are used in asymmetric encryption? (Choose two.)
- a token
- a DES key
- a private key
- a public key
- a TPM
Answers Explanation & Hints: A token is something that is used to provide two-factor authentication. DES is using an identical key to encrypt and decrypt. Asymmetric encryption uses a private key associated with a public key.
-
What are two symmetric encryption algorithms? (Choose two.)
- 3DES
- MD5
- AES
- HMAC
- SHA
Answers Explanation & Hints: MD5, HMAC, and SHA are hashing algorithms.
-
Which statement describes asymmetric encryption algorithms?
- They include DES, 3DES, and AES.
- They have key lengths ranging from 80 to 256 bits.
- They are also called shared-secret key algorithms.
- They are relatively slow because they are based on difficult computational algorithms.
Answers Explanation & Hints: DES, 3DES, and AES are examples of symmetric encryption algorithms (also known as shared secret key algorithms). The usual key length for symmetric algorithms is 80-256 bits. Asymmetric algorithms are relatively slow because they are based on difficult computational algorithms.
-
What technology supports asymmetric key encryption used in IPsec VPNs?
- 3DES
- IKE
- SEAL
- AES
Answers Explanation & Hints: IKE, or Internet Key Exchange, is a protocol to support asymmetric encryption algorithms. It is used to securely exchange encryption keys in the setup of IPsec VPNs.
-
What is the purpose of a digital certificate?
- It guarantees that a website has not been hacked.
- It provides proof that data has a traditional signature attached.
- It ensures that the person who is gaining access to a network device is authorized.
- It authenticates a website and establishes a secure connection to exchange confidential data.
Answers Explanation & Hints: Digital signatures commonly use digital certificates that are used to verify the identity of the originator in order to authenticate a vendor website and establish an encrypted connection to exchange confidential data. One such example is when a person logs into a financial institution from a web browser.
-
Alice and Bob are using a digital signature to sign a document. What key should Alice use to sign the document so that Bob can make sure that the document came from Alice?
- username and password from Alice
- private key from Alice
- public key from Bob
- private key from Bob
Answers Explanation & Hints: Alice and Bob are used to explain asymmetric cryptography used in digital signatures. Alice uses a private key to encrypt the message digest. The message, encrypted message digest, and the public key are used to create the signed document and prepare it for transmission.
-
Which three security services are provided by digital signatures? (Choose three.)
- authenticates the source
- authenticates the destination
- guarantees data has not changed in transit
- provides data encryption
- provides nonrepudiation using HMAC functions
- provides confidentiality of digitally signed data
Answers Explanation & Hints: Digital signatures are a mathematical technique used to provide three basic security services. Digital signatures have specific properties that enable entity authentication and data integrity. In addition, digital signatures provide nonrepudiation of the transaction. In other words, the digital signature serves as legal proof that the data exchange did take place.
-
What is the purpose for using digital signatures for code signing?
- to generate a virtual ID
- to establish an encrypted connection to exchange confidential data with a vendor website
- to authenticate the identity of the system with a vendor website
- to verify the integrity of executable files downloaded from a vendor website
Answers Explanation & Hints: Code signing is used to verify the integrity of executable files downloaded from a vendor website. Code signing uses digital certificates to authenticate and verify the identity of a website.
-
In a hierarchical CA topology, where can a subordinate CA obtain a certificate for itself?
- from the root CA only
- from the root CA or from self-generation
- from the root CA or another subordinate CA at the same level
- from the root CA or another subordinate CA at a higher level
- from the root CA or another subordinate CA anywhere in the tree
Answers Explanation & Hints: In a hierarchical CA topology, CAs can issue certificates to end users and to subordinate CAs, which in turn issue their certificates to end users, other lower level CAs, or both. In this way, a tree of CAs and end users is built in which every CA can issue certificates to lower level CAs and end users. Only the root CA can issue a self-signing certificate in a hierarchical CA topology.
-
What technology has a function of using trusted third-party protocols to issue credentials that are accepted as an authoritative identity?
- PKI certificates
- symmetric keys
- hashing algorithms
- digital signatures
Answers Explanation & Hints: Digital certificates are used to prove the authenticity and integrity of PKI certificates, but a PKI Certificate Authority is a trusted third-party entity that issues PKI certificates. PKI certificates are public information and are used to provide authenticity, confidentiality, integrity, and nonrepudiation services that can scale to large requirements.
-
Two users must authenticate each other using digital certificates and a CA. Which option describes the CA authentication procedure?
- The CA is always required, even after user verification is complete.
- The users must obtain the certificate of the CA and then their own certificate.
- After user verification is complete, the CA is no longer required, even if one of the involved certificates expires.
- CA certificates are retrieved out-of-band using the PSTN, and the authentication is done in-band over a network.
Answers Explanation & Hints: When two users must authenticate each other using digital certificates and CA, both users must obtain their own digital certificate from a CA. They submit a certificate request to a CA, and the CA will perform a technical verification by calling the end user (out-of-band). Once the request is approved, the end user retrieves the certificate over the network (in-band) and installs the certificate on the system. After both users have installed their certificate, they can perform authentication by sending their certificate to each other. Each site will use the public key of the CA to verify the validity of the certificate; no CA is involved at this point. If both certificates are verified, both users can now authenticate each other.
-
An IT enterprise is recommending the use of PKI applications to securely exchange information between the employees. In which two cases might an organization use PKI applications to securely exchange information between users? (Choose two.)
- 802.1x authentication
- FTP transfers
- HTTPS web service
- local NTP server
- file and directory access permission
Answers Explanation & Hints: The Public Key Infrastructure (PKI) is a third party-system referred to as a certificate authority or CA. The PKI is the framework used to securely exchange information between parties. Common PKI applications are as follows:
SSL/TLS certificate-based peer authentication
Secure network traffic using IPsec VPNs
HTTPS Web traffic
Control access to the network using 802.1x authentication
Secure email using the S/MIME protocol
Secure instant messaging
Approve and authorize applications with Code Signing
Protect user data with the Encryption File System (EFS)
Implement two-factor authentication with smart cards
Securing USB storage devices
| Network Security 1.0 | |
| Final Exam Answers | |
| This Chapters 15 - 17 | |
| Chapters 15 - 17 Exam Answers | Online Test |
| Next Chapters 18 - 19 | |
| Chapters 18 - 19 Exam Answers | Online Test |