Refer to the exhibit. What HMAC algorithm is being used to provide data integrity?
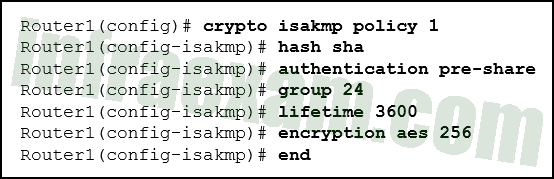
- SHA
- MD5
- DH
- AES
Answers Explanation & Hints: Two popular algorithms that are used to ensure that data is not intercepted and modified (data integrity) are MD5 and SHA. The command Router1(config-isakmp)# hash sha indicates that SHA is being used. AES is an encryption protocol and provides data confidentiality. DH (Diffie-Hellman) is an algorithm that is used for key exchange. RSA is an algorithm used for authentication.