SY0-501 : CompTIA Security+ Certification : Part 02
SY0-501 : CompTIA Security+ Certification : Part 02
-
Which of the following types of keys is found in a key escrow?
- Public
- Private
- Shared
- Session
-
A security analyst is reviewing the following output from an IPS:
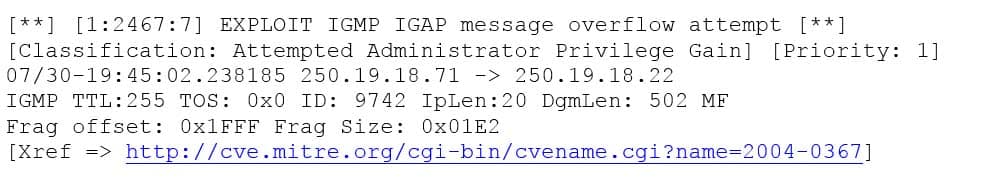
SY0-501 Part 02 Q02 005 Given this output, which of the following can be concluded? (Choose two.)
- The source IP of the attack is coming from 250.19.18.22.
- The source IP of the attack is coming from 250.19.18.71.
- The attacker sent a malformed IGAP packet, triggering the alert.
- The attacker sent a malformed TCP packet, triggering the alert.
- The TTL value is outside of the expected range, triggering the alert.
-
Despite having implemented password policies, users continue to set the same weak passwords and reuse old passwords. Which of the following technical controls would help prevent these policy violations? (Choose two.)
- Password expiration
- Password length
- Password complexity
- Password history
- Password lockout
-
Which of the following types of cloud infrastructures would allow several organizations with similar structures and interests to realize the benefits of shared storage and resources?
- Private
- Hybrid
- Public
- Community
-
A company is currently using the following configuration:
– IAS server with certificate-based EAP-PEAP and MSCHAP
– Unencrypted authentication via PAPA security administrator needs to configure a new wireless setup with the following configurations:
– PAP authentication method
– PEAP and EAP provide two-factor authenticationWhich of the following forms of authentication are being used? (Choose two.)
- PAP
- PEAP
- MSCHAP
- PEAP- MSCHAP
- EAP
- EAP-PEAP
-
An auditor wants to test the security posture of an organization by running a tool that will display the following:

SY0-501 Part 02 Q06 006 Which of the following commands should be used?
-
nbtstat -
nc
-
arp
-
ipconfig
-
-
A company determines that it is prohibitively expensive to become compliant with new credit card regulations. Instead, the company decides to purchase insurance to cover the cost of any potential loss. Which of the following is the company doing?
- Transferring the risk
- Accepting the risk
- Avoiding the risk
- Migrating the risk
-
A company is using a mobile device deployment model in which employees use their personal devices for work at their own discretion. Some of the problems the company is encountering include the following:
– There is no standardization.
– Employees ask for reimbursement for their devices.
– Employees do not replace their devices often enough to keep them running efficiently.
– The company does not have enough control over the devices.Which of the following is a deployment model that would help the company overcome these problems?
- BYOD
- VDI
- COPE
- CYOD
-
A botnet has hit a popular website with a massive number of GRE-encapsulated packets to perform a DDoS attack. News outlets discover a certain type of refrigerator was exploited and used to send outbound packets to the website that crashed. To which of the following categories does the refrigerator belong?
- SoC
- ICS
- IoT
- MFD
-
Users report the following message appears when browsing to the company’s secure site: This website cannot be trusted. Which of the following actions should a security analyst take to resolve these messages? (Choose two.)
- Verify the certificate has not expired on the server.
- Ensure the certificate has a .pfx extension on the server.
- Update the root certificate into the client computer certificate store.
- Install the updated private key on the web server.
- Have users clear their browsing history and relaunch the session.
-
When trying to log onto a company’s new ticketing system, some employees receive the following message: Access denied: too many concurrent sessions. The ticketing system was recently installed on a small VM with only the recommended hardware specifications. Which of the following is the MOST likely cause for this error message?
- Network resources have been exceeded.
- The software is out of licenses.
- The VM does not have enough processing power.
- The firewall is misconfigured.
-
Joe, an employee, wants to show his colleagues how much he knows about smartphones. Joe demonstrates a free movie application that he installed from a third party on his corporate smartphone. Joe’s colleagues were unable to find the application in the app stores. Which of the following allowed Joe to install the application? (Choose two.)
- Near-field communication.
- Rooting/jailbreaking
- Ad-hoc connections
- Tethering
- Sideloading
-
Which of the following can be provided to an AAA system for the identification phase?
- Username
- Permissions
- One-time token
- Private certificate
-
Which of the following implements two-factor authentication?
- A phone system requiring a PIN to make a call
- At ATM requiring a credit card and PIN
- A computer requiring username and password
- A datacenter mantrap requiring fingerprint and iris scan
-
Malicious traffic from an internal network has been detected on an unauthorized port on an application server.
Which of the following network-based security controls should the engineer consider implementing?
- ACLs
- HIPS
- NAT
- MAC filtering
-
A network administrator wants to implement a method of securing internal routing. Which of the following should the administrator implement?
- DMZ
- NAT
- VPN
- PAT
-
A security administrator is developing controls for creating audit trails and tracking if a PHI data breach is to occur. The administrator has been given the following requirements:
– All access must be correlated to a user account.
– All user accounts must be assigned to a single individual.
– User access to the PHI data must be recorded.
– Anomalies in PHI data access must be reported.
– Logs and records cannot be deleted or modified.Which of the following should the administrator implement to meet the above requirements? (Choose three.)
- Eliminate shared accounts.
- Create a standard naming convention for accounts.
- Implement usage auditing and review.
- Enable account lockout thresholds.
- Copy logs in real time to a secured WORM drive.
- Implement time-of-day restrictions.
- Perform regular permission audits and reviews.
-
Which of the following encryption methods does PKI typically use to securely protect keys?
- Elliptic curve
- Digital signatures
- Asymmetric
- Obfuscation
-
An organization is using a tool to perform a source code review. Which of the following describes the case in which the tool incorrectly identifies the vulnerability?
- False negative
- True negative
- False positive
- True positive
-
An organization’s internal auditor discovers that large sums of money have recently been paid to a vendor that management does not recognize. The IT security department is asked to investigate the organizations the organization’s ERP system to determine how the accounts payable module has been used to make these vendor payments.
The IT security department finds the following security configuration for the accounts payable module:New Vendor Entry – Required Role: Accounts Payable Clerk New Vendor Approval – Required Role: Accounts Payable Clerk Vendor Payment Entry – Required Role: Accounts Payable Clerk Vendor Payment Approval – Required Role: Accounts Payable Manager
Which of the following changes to the security configuration of the accounts payable module would BEST mitigate the risk?



