SY0-501 : CompTIA Security+ Certification : Part 08
-
Which of the following types of attacks precedes the installation of a rootkit on a server?
- Pharming
- DDoS
- Privilege escalation
- DoS
-
Which of the following cryptographic algorithms is irreversible?
- RC4
- SHA-256
- DES
- AES
-
A security analyst receives an alert from a WAF with the following payload:
var data= “<test test test>” ++ <../../../../../../etc/passwd>”Which of the following types of attacks is this?
- Cross-site request forgery
- Buffer overflow
- SQL injection
- JavaScript data insertion
- Firewall evasion script
-
A workstation puts out a network request to locate another system. Joe, a hacker on the network, responds before the real system does, and he tricks the workstation into communicating with him. Which of the following BEST describes what occurred?
- The hacker used a race condition.
- The hacker used a pass-the-hash attack.
- The hacker-exploited improper key management.
- The hacker exploited weak switch configuration.
-
Audit logs from a small company’s vulnerability scanning software show the following findings:
Destinations scanned:
-Server001- Internal human resources payroll server
-Server101-Internet-facing web server
-Server201- SQL server for Server101
-Server301-Jumpbox used by systems administrators accessible from the internal networkValidated vulnerabilities found:
-Server001- Vulnerable to buffer overflow exploit that may allow attackers to install software
-Server101- Vulnerable to buffer overflow exploit that may allow attackers to install software
-Server201-OS updates not fully current
-Server301- Accessible from internal network without the use of jumpbox
-Server301-Vulnerable to highly publicized exploit that can elevate user privilegesAssuming external attackers who are gaining unauthorized information are of the highest concern, which of the following servers should be addressed FIRST?
- Server001
- Server101
- Server201
- Server301
-
A security analyst wants to harden the company’s VoIP PBX. The analyst is worried that credentials may be intercepted and compromised when IP phones authenticate with the BPX. Which of the following would best prevent this from occurring?
- Implement SRTP between the phones and the PBX.
- Place the phones and PBX in their own VLAN.
- Restrict the phone connections to the PBX.
- Require SIPS on connections to the PBX.
-
An organization is comparing and contrasting migration from its standard desktop configuration to the newest version of the platform. Before this can happen, the Chief Information Security Officer (CISO) voices the need to evaluate the functionality of the newer desktop platform to ensure interoperability with existing software in use by the organization. In which of the following principles of architecture and design is the CISO engaging?
- Dynamic analysis
- Change management
- Baselining
- Waterfalling
-
A security administrator suspects a MITM attack aimed at impersonating the default gateway is underway. Which of the following tools should the administrator use to detect this attack? (Choose two.)
- Ping
- Ipconfig
- Tracert
- Netstat
- Dig
- Nslookup
-
A user is presented with the following items during the new-hire onboarding process:
-Laptop
-Secure USB drive
-Hardware OTP token
-External high-capacity HDD
-Password complexity policy
-Acceptable use policy
-HASP key
-Cable lockWhich of the following is one component of multifactor authentication?
- Secure USB drive
- Cable lock
- Hardware OTP token
- HASP key
-
An organization requires users to provide their fingerprints to access an application. To improve security, the application developers intend to implement multifactor authentication. Which of the following should be implemented?
- Use a camera for facial recognition
- Have users sign their name naturally
- Require a palm geometry scan
- Implement iris recognition
-
A network technician is setting up a segmented network that will utilize a separate ISP to provide wireless access to the public area for a company. Which of the following wireless security methods should the technician implement to provide basic accountability for access to the public network?
- Pre-shared key
- Enterprise
- Wi-Fi Protected setup
- Captive portal
-
After a routine audit, a company discovers that engineering documents have been leaving the network on a particular port. The company must allow outbound traffic on this port, as it has a legitimate business use. Blocking the port would cause an outage. Which of the following technology controls should the company implement?
- NAC
- Web proxy
- DLP
- ACL
-
A security analyst has received the following alert snippet from the HIDS appliance:

SY0-501 Part 08 Q13 025 Given the above logs, which of the following is the cause of the attack?
- The TCP ports on destination are all open
- FIN, URG, and PSH flags are set in the packet header
- TCP MSS is configured improperly
- There is improper Layer 2 segmentation
-
A security analyst reviews the following output:
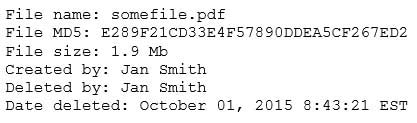
SY0-501 Part 08 Q14 026 The analyst loads the hash into the SIEM to discover if this hash is seen in other parts of the network. After inspecting a large number of files, the security analyst reports the following:

SY0-501 Part 08 Q14 027 Which of the following is the MOST likely cause of the hash being found in other areas?
- Jan Smith is an insider threat
- There are MD5 hash collisions
- The file is encrypted
- Shadow copies are present
-
A company’s AUP requires:
– Passwords must meet complexity requirements.
– Passwords are changed at least once every six months.
– Passwords must be at least eight characters long.An auditor is reviewing the following report:
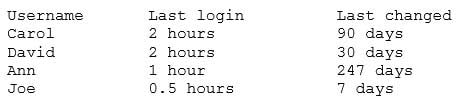
SY0-501 Part 08 Q15 028 Which of the following controls should the auditor recommend to enforce the AUP?
- Account lockout thresholds
- Account recovery
- Password expiration
- Prohibit password reuse
-
An organization’s primary datacenter is experiencing a two-day outage due to an HVAC malfunction. The node located in the datacenter has lost power and is no longer operational, impacting the ability of all users to connect to the alternate datacenter. Which of the following BIA concepts BEST represents the risk described in this scenario?
- SPoF
- RTO
- MTBF
- MTTR
-
A security analyst notices anomalous activity coming from several workstations in the organizations. Upon identifying and containing the issue, which of the following should the security analyst do NEXT?
- Document and lock the workstations in a secure area to establish chain of custody
- Notify the IT department that the workstations are to be reimaged and the data restored for reuse
- Notify the IT department that the workstations may be reconnected to the network for the users to continue working
- Document findings and processes in the after-action and lessons learned report
-
An employee receives an email, which appears to be from the Chief Executive Officer (CEO), asking for a report of security credentials for all users.
Which of the following types of attack is MOST likely occurring?
- Policy violation
- Social engineering
- Whaling
- Spear phishing
-
An information security analyst needs to work with an employee who can answer questions about how data for a specific system is used in the business. The analyst should seek out an employee who has the role of:
- steward
- owner
- privacy officer
- systems administrator
-
A group of non-profit agencies wants to implement a cloud service to share resources with each other and minimize costs. Which of the following cloud deployment models BEST describes this type of effort?
- Public
- Hybrid
- Community
- Private
Subscribe
0 Comments
Newest