SY0-501 : CompTIA Security+ Certification : Part 07
SY0-501 : CompTIA Security+ Certification : Part 07
-
After an identified security breach, an analyst is tasked to initiate the IR process. Which of the following is the NEXT step the analyst should take?
- Recovery
- Identification
- Preparation
- Documentation
- Escalation
-
A company was recently audited by a third party. The audit revealed the company’s network devices were transferring files in the clear. Which of the following protocols should the company use to transfer files?
- HTTPS
- LDAPS
- SCP
- SNMPv3
-
During a monthly vulnerability scan, a server was flagged for being vulnerable to an Apache Struts exploit. Upon further investigation, the developer responsible for the server informs the security team that Apache Struts is not installed on the server. Which of the following BEST describes how the security team should reach to this incident?
- The finding is a false positive and can be disregarded
- The Struts module needs to be hardened on the server
- The Apache software on the server needs to be patched and updated
- The server has been compromised by malware and needs to be quarantined.
-
A systems administrator wants to protect data stored on mobile devices that are used to scan and record assets in a warehouse. The control must automatically destroy the secure container of mobile devices if they leave the warehouse. Which of the following should the administrator implement? (Choose two.)
- Geofencing
- Remote wipe
- Near-field communication
- Push notification services
- Containerization
-
A security analyst is performing a quantitative risk analysis. The risk analysis should show the potential monetary loss each time a threat or event occurs. Given this requirement, which of the following concepts would assist the analyst in determining this value? (Choose two.)
- ALE
- AV
- ARO
- EF
- ROI
-
Which of the following AES modes of operation provide authentication? (Choose two.)
- CCM
- CBC
- GCM
- DSA
- CFB
-
An audit takes place after company-wide restricting, in which several employees changed roles. The following deficiencies are found during the audit regarding access to confidential data:

SY0-501 Part 07 Q07 022 Which of the following would be the BEST method to prevent similar audit findings in the future?
- Implement separation of duties for the payroll department.
- Implement a DLP solution on the payroll and human resources servers.
- Implement rule-based access controls on the human resources server.
- Implement regular permission auditing and reviews.
-
A security engineer is configuring a wireless network that must support mutual authentication of the wireless client and the authentication server before users provide credentials. The wireless network must also support authentication with usernames and passwords. Which of the following authentication protocols MUST the security engineer select?
- EAP-FAST
- EAP-TLS
- PEAP
- EAP
-
A system’s administrator has finished configuring firewall ACL to allow access to a new web server.

SY0-501 Part 07 Q09 023 The security administrator confirms form the following packet capture that there is network traffic from the internet to the web server:
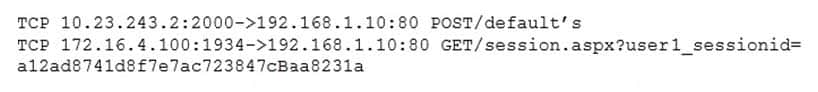
SY0-501 Part 07 Q09 024 The company’s internal auditor issues a security finding and requests that immediate action be taken. With which of the following is the auditor MOST concerned?
- Misconfigured firewall
- Clear text credentials
- Implicit deny
- Default configuration
-
Which of the following vulnerability types would the type of hacker known as a script kiddie be MOST dangerous against?
- Passwords written on the bottom of a keyboard
- Unpatched exploitable Internet-facing services
- Unencrypted backup tapes
- Misplaced hardware token
-
An in-house penetration tester is using a packet capture device to listen in on network communications. This is an example of:
- Passive reconnaissance
- Persistence
- Escalation of privileges
- Exploiting the switch
-
A black hat hacker is enumerating a network and wants to remain covert during the process. The hacker initiates a vulnerability scan. Given the task at hand the requirement of being covert, which of the following statements BEST indicates that the vulnerability scan meets these requirements?
- The vulnerability scanner is performing an authenticated scan.
- The vulnerability scanner is performing local file integrity checks.
- The vulnerability scanner is performing in network sniffer mode.
- The vulnerability scanner is performing banner grabbing.
-
A development team has adopted a new approach to projects in which feedback is iterative and multiple iterations of deployments are provided within an application’s full life cycle. Which of the following software development methodologies is the development team using?
- Waterfall
- Agile
- Rapid
- Extreme
-
A Chief Executive Officer (CEO) suspects someone in the lab testing environment is stealing confidential information after working hours when no one else is around. Which of the following actions can help to prevent this specific threat?
- Implement time-of-day restrictions.
- Audit file access times.
- Secretly install a hidden surveillance camera.
- Require swipe-card access to enter the lab.
-
A company hires a third-party firm to conduct an assessment of vulnerabilities exposed to the Internet. The firm informs the company that an exploit exists for an FTP server that had a version installed from eight years ago. The company has decided to keep the system online anyway, as no upgrade exists form the vendor. Which of the following BEST describes the reason why the vulnerability exists?
- Default configuration
- End-of-life system
- Weak cipher suite
- Zero-day threats
-
An organization uses SSO authentication for employee access to network resources. When an employee resigns, as per the organization’s security policy, the employee’s access to all network resources is terminated immediately. Two weeks later, the former employee sends an email to the help desk for a password reset to access payroll information from the human resources server. Which of the following represents the BEST course of action?
- Approve the former employee’s request, as a password reset would give the former employee access to only the human resources server.
- Deny the former employee’s request, since the password reset request came from an external email address.
- Deny the former employee’s request, as a password reset would give the employee access to all network resources.
- Approve the former employee’s request, as there would not be a security issue with the former employee gaining access to network resources.
-
Joe, a user, wants to send Ann, another user, a confidential document electronically. Which of the following should Joe do to ensure the document is protected from eavesdropping?
- Encrypt it with Joe’s private key
- Encrypt it with Joe’s public key
- Encrypt it with Ann’s private key
- Encrypt it with Ann’s public key
-
A director of IR is reviewing a report regarding several recent breaches. The director compiles the following statistic’s
-Initial IR engagement time frame
-Length of time before an executive management notice went out
-Average IR phase completionThe director wants to use the data to shorten the response time. Which of the following would accomplish this?
- CSIRT
- Containment phase
- Escalation notifications
- Tabletop exercise
-
To reduce disk consumption, an organization’s legal department has recently approved a new policy setting the data retention period for sent email at six months. Which of the following is the BEST way to ensure this goal is met?
- Create a daily encrypted backup of the relevant emails.
- Configure the email server to delete the relevant emails.
- Migrate the relevant emails into an “Archived” folder.
- Implement automatic disk compression on email servers.
-
A security administrator is configuring a new network segment, which contains devices that will be accessed by external users, such as web and FTP server. Which of the following represents the MOST secure way to configure the new network segment?
- The segment should be placed on a separate VLAN, and the firewall rules should be configured to allow external traffic.
- The segment should be placed in the existing internal VLAN to allow internal traffic only.
- The segment should be placed on an intranet, and the firewall rules should be configured to allow external traffic.
- The segment should be placed on an extranet, and the firewall rules should be configured to allow both internal and external traffic.