SY0-501 : CompTIA Security+ Certification : Part 09
SY0-501 : CompTIA Security+ Certification : Part 09
-
An administrator is configuring access to information located on a network file server named “Bowman”. The files are located in a folder named “BalkFiles”. The files are only for use by the “Matthews” division and should be read-only. The security policy requires permissions for shares to be managed at the file system layer and also requires those permissions to be set according to a least privilege model. Security policy for this data type also dictates that administrator-level accounts on the system have full access to the files.
The administrator configures the file share according to the following table:

SY0-501 Part 09 Q01 029 Which of the following rows has been misconfigured?
- Row 1
- Row 2
- Row 3
- Row 4
- Row 5
-
A copy of a highly confidential salary report was recently found on a printer in the IT department. The human resources department does not have this specific printer mapped to its devices, and it is suspected that an employee in the IT department browsed to the share where the report was located and printed it without authorization. Which of the following technical controls would be the BEST choice to immediately prevent this from happening again?
- Implement a DLP solution and classify the report as confidential, restricting access only to human resources staff
- Restrict access to the share where the report resides to only human resources employees and enable auditing
- Have all members of the IT department review and sign the AUP and disciplinary policies
- Place the human resources computers on a restricted VLAN and configure the ACL to prevent access from the IT department
-
A company is developing a new system that will unlock a computer automatically when an authorized user sits in front of it, and then lock the computer when the user leaves. The user does not have to perform any action for this process to occur. Which of the following technologies provides this capability?
- Facial recognition
- Fingerprint scanner
- Motion detector
- Smart cards
-
A security analyst accesses corporate web pages and inputs random data in the forms. The response received includes the type of database used and SQL commands that the database accepts. Which of the following should the security analyst use to prevent this vulnerability?
- Application fuzzing
- Error handling
- Input validation
- Pointer dereference
-
Which of the following differentiates a collision attack from a rainbow table at
- A rainbow table attack performs a hash lookup
- A rainbow table attack uses the hash as a password
- In a collision attack, the hash and the input data are equivalent
- In a collision attack, the same input results in different hashes
-
A help desk is troubleshooting user reports that the corporate website is presenting untrusted certificate errors to employees and customers when they visit the website. Which of the following is the MOST likely cause of this error, provided the certificate has not expired?
- The certificate was self signed, and the CA was not imported by employees or customers
- The root CA has revoked the certificate of the intermediate CA
- The valid period for the certificate has passed, and a new certificate has not been issued
- The key escrow server has blocked the certificate from being validated
-
A security analyst is investigating a suspected security breach and discovers the following in the logs of the potentially compromised server:
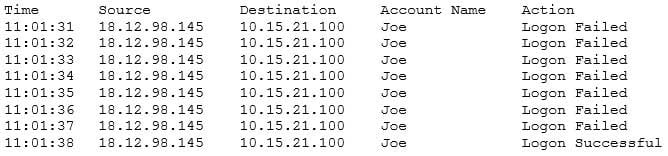
SY0-501 Part 09 Q07 030 Which of the following would be the BEST method for preventing this type of suspected attack in the future?
- Implement password expirations
- Implement restrictions on shared credentials
- Implement account lockout settings
- Implement time-of-day restrictions on this server
-
DRAG DROP
A security administrator is given the security and availability profiles for servers that are being deployed.
1. Match each RAID type with the correct configuration and MINIMUM number of drives.
2. Review the server profiles and match them with the appropriate RAID type based on integrity, availability, I/O, storage requirements. Instructions:- All drive definitions can be dragged as many times as necessary - Not all placeholders may be filled in the RAID configuration boxes - If parity is required, please select the appropriate number of parity checkboxes - Server profiles may be dragged only once
If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
SY0-501 Part 09 Q08 031 Question 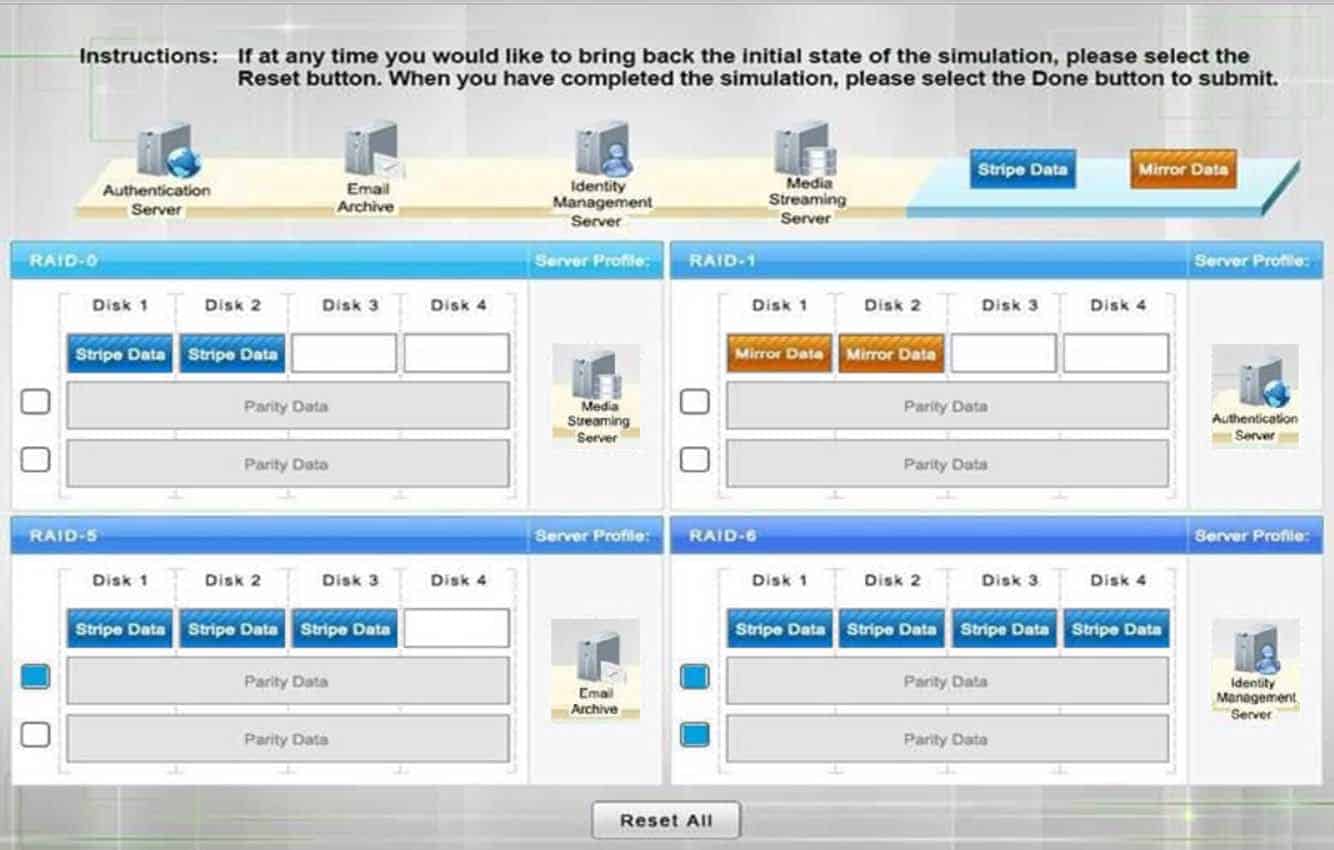
SY0-501 Part 09 Q08 031 Answer Explanation:
RAID-0 is known as striping. It is not a fault tolerant solution but does improve disk performance for read/write operations. Striping requires a minimum of two disks and does not use parity.
RAID-0 can be used where performance is required over fault tolerance, such as a media streaming server.
RAID-1 is known as mirroring because the same data is written to two disks so that the two disks have identical data. This is a fault tolerant solution that halves the storage space. A minimum of two disks are used in mirroring and does not use parity. RAID-1 can be used where fault tolerance is required over performance, such as on an authentication server. RAID-5 is a fault tolerant solution that uses parity and striping. A minimum of three disks are required for RAID-5 with one disk’s worth of space being used for parity information. However, the parity information is distributed across all the disks. RAID-5 can recover from a sing disk failure.
RAID-6 is a fault tolerant solution that uses dual parity and striping. A minimum of four disks are required for RAID-6. Dual parity allows RAID-6 to recover from the simultaneous failure of up to two disks. Critical data should be stored on a RAID-6 system. -
A security administrator is trying to encrypt communication. For which of the following reasons should administrator take advantage of the Subject Alternative Name (SAM) attribute of a certificate?
- It can protect multiple domains
- It provides extended site validation
- It does not require a trusted certificate authority
- It protects unlimited subdomains
-
After a merger between two companies a security analyst has been asked to ensure that the organization’s systems are secured against infiltration by any former employees that were terminated during the transition.
Which of the following actions are MOST appropriate to harden applications against infiltration by former employees? (Choose two.)
- Monitor VPN client access
- Reduce failed login out settings
- Develop and implement updated access control policies
- Review and address invalid login attempts
- Increase password complexity requirements
- Assess and eliminate inactive accounts
-
A new mobile application is being developed in-house. Security reviews did not pick up any major flaws, however vulnerability scanning results show fundamental issues at the very end of the project cycle.
Which of the following security activities should also have been performed to discover vulnerabilities earlier in the lifecycle?
- Architecture review
- Risk assessment
- Protocol analysis
- Code review
-
A security administrator is creating a subnet on one of the corporate firewall interfaces to use as a DMZ which is expected to accommodate at most 14 physical hosts.
Which of the following subnets would BEST meet the requirements?
- 192.168.0.16 255.25.255.248
- 192.168.0.16/28
- 192.168.1.50 255.255.25.240
- 192.168.2.32/27
-
A company has a security policy that specifies all endpoint computing devices should be assigned a unique identifier that can be tracked via an inventory management system. Recent changes to airline security regulations have cause many executives in the company to travel with mini tablet devices instead of laptops. These tablet devices are difficult to tag and track. An RDP application is used from the tablet to connect into the company network.
Which of the following should be implemented in order to meet the security policy requirements?
- Virtual desktop infrastructure (IDI)
- WS-security and geo-fencing
- A hardware security module (HSM)
- RFID tagging system
- MDM software
- Security Requirements Traceability Matrix (SRTM)
-
The security administrator receives an email on a non-company account from a coworker stating that some reports are not exporting correctly. Attached to the email was an example report file with several customers’ names and credit card numbers with the PIN.
Which of the following is the BEST technical controls that will help mitigate this risk of disclosing sensitive data?
- Configure the mail server to require TLS connections for every email to ensure all transport data is encrypted
- Create a user training program to identify the correct use of email and perform regular audits to ensure compliance
- Implement a DLP solution on the email gateway to scan email and remove sensitive data or files
- Classify all data according to its sensitivity and inform the users of data that is prohibited to share
-
A technician is configuring a wireless guest network. After applying the most recent changes the technician finds the new devices can no longer find the wireless network by name but existing devices are still able to use the wireless network.
Which of the following security measures did the technician MOST likely implement to cause this Scenario?
- Deactivation of SSID broadcast
- Reduction of WAP signal output power
- Activation of 802.1X with RADIUS
- Implementation of MAC filtering
- Beacon interval was decreased
-
A security administrator has been assigned to review the security posture of the standard corporate system image for virtual machines. The security administrator conducts a thorough review of the system logs, installation procedures, and network configuration of the VM image. Upon reviewing the access logs and user accounts, the security administrator determines that several accounts will not be used in production.
Which of the following would correct the deficiencies?
- Mandatory access controls
- Disable remote login
- Host hardening
- Disabling services
-
Although a web enabled application appears to only allow letters in the comment field of a web form, malicious user was able to carry a SQL injection attack by sending special characters through the web comment field.
Which of the following has the application programmer failed to implement?
- Revision control system
- Client side exception handling
- Server side validation
- Server hardening
-
An attacker discovers a new vulnerability in an enterprise application. The attacker takes advantage of the vulnerability by developing new malware. After installing the malware, the attacker is provided with access to the infected machine.
Which of the following is being described?
- Zero-day exploit
- Remote code execution
- Session hijacking
- Command injection
-
A security administrator returning from a short vacation receives an account lock-out message when attempting to log into the computer. After getting the account unlocked the security administrator immediately notices a large amount of emails alerts pertaining to several different user accounts being locked out during the past three days. The security administrator uses system logs to determine that the lock-outs were due to a brute force attack on all accounts that has been previously logged into that machine.
Which of the following can be implemented to reduce the likelihood of this attack going undetected?
- Password complexity rules
- Continuous monitoring
- User access reviews
- Account lockout policies
-
A bank requires tellers to get manager approval when a customer wants to open a new account. A recent audit shows that there have been four cases in the previous year where tellers opened accounts without management approval. The bank president thought separation of duties would prevent this from happening.
In order to implement a true separation of duties approach the bank could:
- Require the use of two different passwords held by two different individuals to open an account
- Administer account creation on a role based access control approach
- Require all new accounts to be handled by someone else other than a teller since they have different duties
- Administer account creation on a rule based access control approach