SY0-501 : CompTIA Security+ Certification : Part 12
SY0-501 : CompTIA Security+ Certification : Part 12
-
DRAG DROP
Drag and drop the correct protocol to its default port.

SY0-501 Part 12 Q01 032 Question 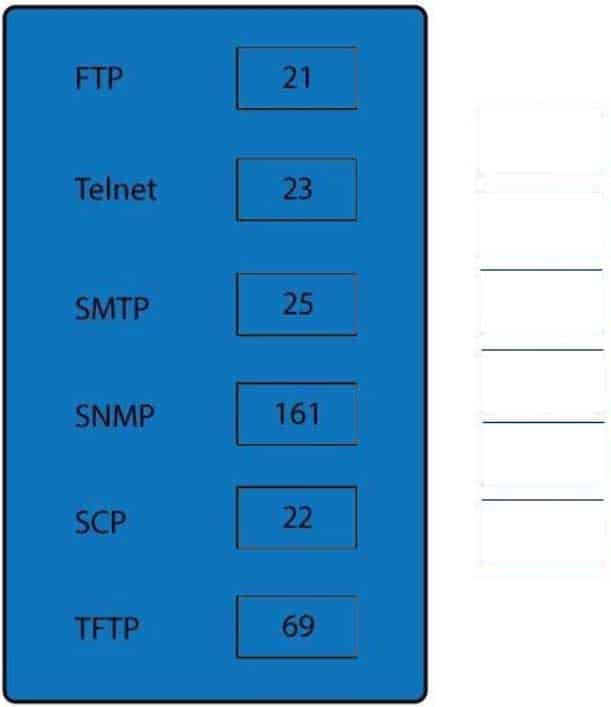
SY0-501 Part 12 Q01 032 Answer Explanation:
FTP uses TCP port 21. Telnet uses port 23.
SSH uses TCP port 22.
All protocols encrypted by SSH, including SFTP, SHTTP, SCP, SExec, and slogin, also use TCP port 22. Secure Copy Protocol (SCP) is a secure file-transfer facility based on SSH and Remote Copy Protocol (RCP).
Secure FTP (SFTP) is a secured alternative to standard File Transfer Protocol (FTP). SMTP uses TCP port 25.
Port 69 is used by TFTP.
SNMP makes use of UDP ports 161 and 162.
List of TCP and UDP port numbers – Wikipedia -
The Chief Technology Officer (CTO) of a company, Ann, is putting together a hardware budget for the next 10 years. She is asking for the average lifespan of each hardware device so that she is able to calculate when she will have to replace each device.
Which of the following categories BEST describes what she is looking for?
- ALE
- MTTR
- MTBF
- MTTF
-
A software developer wants to ensure that the application is verifying that a key is valid before establishing SSL connections with random remote hosts on the Internet.
Which of the following should be used in the code? (Choose two.)
- Escrowed keys
- SSL symmetric encryption key
- Software code private key
- Remote server public key
- OCSP
-
A security guard has informed the Chief Information Security Officer that a person with a tablet has been walking around the building. The guard also noticed strange white markings in different areas of the parking lot.
The person is attempting which of the following types of attacks?
- Jamming
- War chalking
- Packet sniffing
- Near field communication
-
A system administrator is configuring a site-to-site VPN tunnel.
Which of the following should be configured on the VPN concentrator during the IKE phase?
- RIPEMD
- ECDHE
- Diffie-Hellman
- HTTPS
-
A network operations manager has added a second row of server racks in the datacenter. These racks face the opposite direction of the first row of racks.
Which of the following is the reason the manager installed the racks this way?
- To lower energy consumption by sharing power outlets
- To create environmental hot and cold isles
- To eliminate the potential for electromagnetic interference
- To maximize fire suppression capabilities
-
Phishing emails frequently take advantage of high-profile catastrophes reported in the news.
Which of the following principles BEST describes the weakness being exploited?
- Intimidation
- Scarcity
- Authority
- Social proof
-
New magnetic locks were ordered for an entire building. In accordance with company policy, employee safety is the top priority.
In case of a fire where electricity is cut, which of the following should be taken into consideration when installing the new locks?
- Fail safe
- Fault tolerance
- Fail secure
- Redundancy
-
Anne, the Chief Executive Officer (CEO), has reported that she is getting multiple telephone calls from someone claiming to be from the helpdesk. The caller is asking to verify her network authentication credentials because her computer is broadcasting across the network.
This is MOST likely which of the following types of attacks?
- Vishing
- Impersonation
- Spim
- Scareware
-
An administrator discovers the following log entry on a server:
Nov 12 2013 00:23:45 httpd[2342]: GET
/app2/prod/proc/process.php?input=change;cd%20../../../etc;cat%20shadowWhich of the following attacks is being attempted?
- Command injection
- Password attack
- Buffer overflow
- Cross-site scripting
-
A security team wants to establish an Incident Response plan. The team has never experienced an incident.
Which of the following would BEST help them establish plans and procedures?
- Table top exercises
- Lessons learned
- Escalation procedures
- Recovery procedures
-
Which of the following would verify that a threat does exist and security controls can easily be bypassed without actively testing an application?
- Protocol analyzer
- Vulnerability scan
- Penetration test
- Port scanner
Explanation:A vulnerability scan is the automated process of proactively identifying security vulnerabilities of computing systems in a network in order to determine if and where a system can be exploited and/or threatened. While public servers are important for communication and data transfer over the Internet, they open the door to potential security breaches by threat agents, such as malicious hackers.
Vulnerability scanning employs software that seeks out security flaws based on a database of known flaws, testing systems for the occurrence of these flaws and generating a report of the findings that an individual or an enterprise can use to tighten the network’s security.
Vulnerability scanning typically refers to the scanning of systems that are connected to the Internet but can also refer to system audits on internal networks that are not connected to the Internet in order to assess the threat of rogue software or malicious employees in an enterprise. -
Which of the following technologies would be MOST appropriate to utilize when testing a new software patch before a company-wide deployment?
- Cloud computing
- Virtualization
- Redundancy
- Application control
Explanation:Virtualization is used to host one or more operating systems in the memory of a single host computer and allows multiple operating systems to run simultaneously on the same hardware, reducing costs. Virtualization offers the flexibility of quickly and easily making backups of entire virtual systems, and quickly recovering the virtual system when errors occur. Furthermore, malicious code compromises of virtual systems rarely affect the host system, which allows for safer testing and experimentation.
-
A system administrator needs to implement 802.1x whereby when a user logs into the network, the authentication server communicates to the network switch and assigns the user to the proper VLAN.
Which of the following protocols should be used?
- RADIUS
- Kerberos
- LDAP
- MSCHAP
-
A security administrator receives notice that a third-party certificate authority has been compromised, and new certificates will need to be issued.
Which of the following should the administrator submit to receive a new certificate?
- CRL
- OSCP
- PFX
- CSR
- CA
-
DRAG DROP
A forensic analyst is asked to respond to an ongoing network attack on a server. Place the items in the list below in the correct order in which the forensic analyst should preserve them.
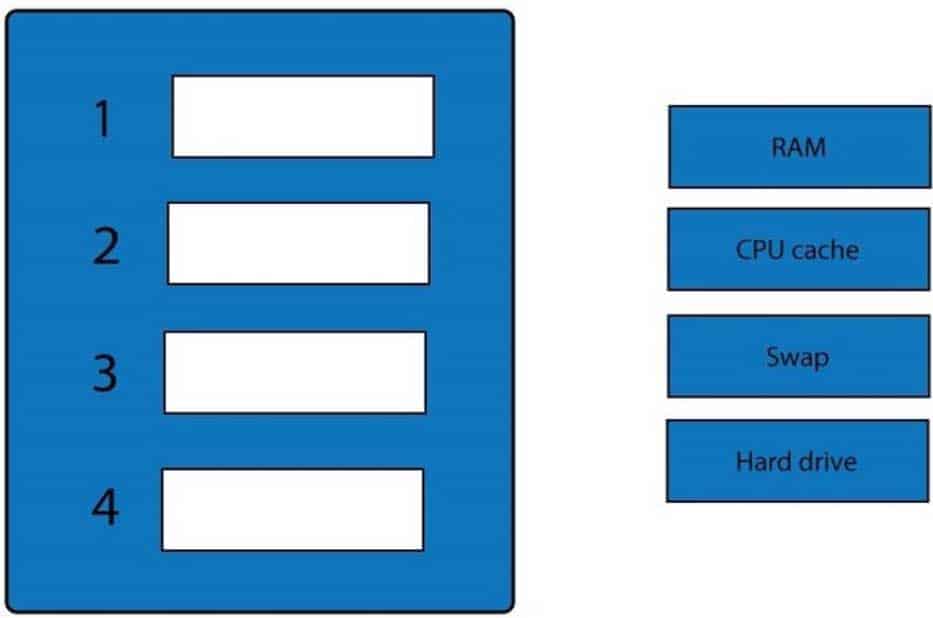
SY0-501 Part 12 Q16 033 Question 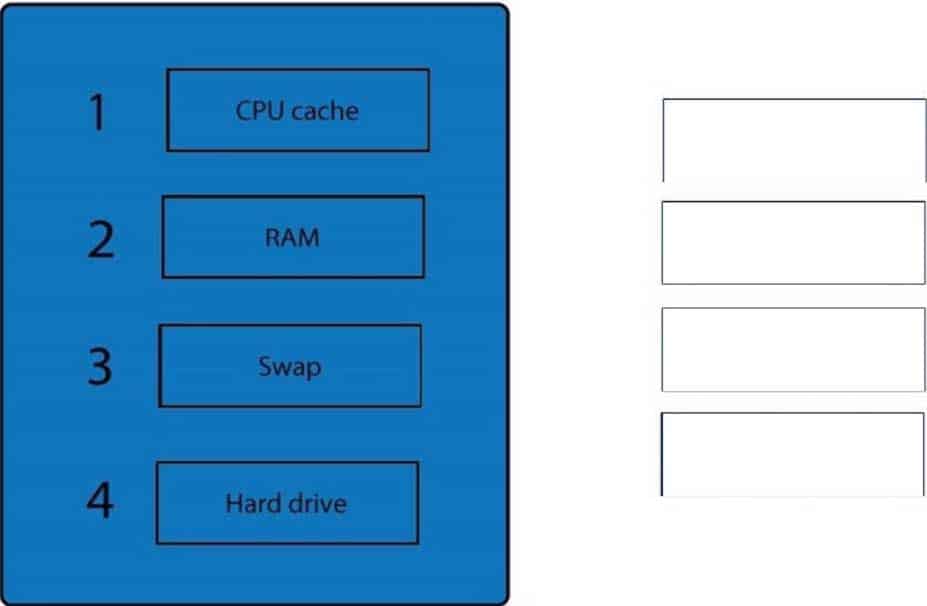
SY0-501 Part 12 Q16 033 Answer Explanation:
When dealing with multiple issues, address them in order of volatility (OOV); always deal with the most volatile first. Volatility can be thought of as the amount of time that you have to collect certain data before a window of opportunity is gone. Naturally, in an investigation you want to collect everything, but some data will exist longer than others, and you cannot possibly collect all of it once. As an example, the OOV in an investigation may be RAM, hard drive data, CDs/DVDs, and printouts.
Order of volatility: Capture system images as a snapshot of what exists, look at network traffic and logs, capture any relevant video/screenshots/hashes, record time offset on the systems, talk to witnesses, and track total man-hours and expenses associated with the investigation. -
A company wants to host a publicly available server that performs the following functions:
- Evaluates MX record lookup - Can perform authenticated requests for A and AAA records - Uses RRSIG
Which of the following should the company use to fulfill the above requirements?
- DNSSEC
- SFTP
- nslookup
- dig
- LDAPS
Explanation:DNS Security Extensions (DNSSEC) provides, among other things, cryptographic authenticity of responses using Resource Record Signatures (RRSIG) and authenticated denial of existence using Next-Secure (NSEC) and Hashed-NSEC records (NSEC3).
-
A security administrator is developing training for corporate users on basic security principles for personal email accounts.
Which of the following should be mentioned as the MOST secure way for password recovery?
- Utilizing a single Qfor password recovery
- Sending a PIN to a smartphone through text message
- Utilizing CAPTCHA to avoid brute force attacks
- Use a different e-mail address to recover password
-
A company researched the root cause of a recent vulnerability in its software. It was determined that the vulnerability was the result of two updates made in the last release. Each update alone would not have resulted in the vulnerability.
In order to prevent similar situations in the future, the company should improve which of the following?
- Change management procedures
- Job rotation policies
- Incident response management
- Least privilege access controls
-
A computer on a company network was infected with a zero-day exploit after an employee accidently opened an email that contained malicious content. The employee recognized the email as malicious and was attempting to delete it, but accidently opened it.
Which of the following should be done to prevent this scenario from occurring again in the future?
- Install host-based firewalls on all computers that have an email client installed
- Set the email program default to open messages in plain text
- Install end-point protection on all computers that access web email
- Create new email spam filters to delete all messages from that sender