SY0-501 : CompTIA Security+ Certification : Part 13
SY0-501 : CompTIA Security+ Certification : Part 13
-
A company wants to ensure that the validity of publicly trusted certificates used by its web server can be determined even during an extended internet outage.
Which of the following should be implemented?
- Recovery agent
- Ocsp
- Crl
- Key escrow
-
An administrator intends to configure an IPSec solution that provides ESP with integrity protection, but not confidentiality protection.
Which of the following AES modes of operation would meet this integrity-only requirement?
- HMAC
- PCBC
- CBC
- GCM
- CFB
-
The chief security officer (CS0) has issued a new policy that requires that all internal websites be configured for HTTPS traffic only. The network administrator has been tasked to update all internal sites without incurring additional costs.
Which of the following is the best solution for the network administrator to secure each internal website?
- Use certificates signed by the company CA
- Use a signing certificate as a wild card certificate
- Use certificates signed by a public ca
- Use a self-signed certificate on each internal server
Explanation:This is a way to update all internal sites without incurring additional costs?
To be a CA (Certificate Authority), you need an infrastructure that consists of considerable operational elements, hardware, software, policy frameworks and practice statements, auditing, security infrastructure and personnel. -
A security program manager wants to actively test the security posture of a system. The system is not yet in production and has no uptime requirement or active user base.
Which of the following methods will produce a report which shows vulnerabilities that were actually exploited?
- Peer review
- Component testing
- Penetration testing
- Vulnerability testing
Explanation:A penetration test, or pen test, is an attempt to evaluate the security of an IT infrastructure by safely trying to exploit vulnerabilities.
-
A new intern in the purchasing department requires read access to shared documents. Permissions are normally controlled through a group called “Purchasing”, however, the purchasing group permissions allow write access.
Which of the following would be the BEST course of action?
- Modify all the shared files with read only permissions for the intern.
- Create a new group that has only read permissions for the files.
- Remove all permissions for the shared files.
- Add the intern to the “Purchasing” group.
-
A business has recently deployed laptops to all sales employees. The laptops will be used primarily from home offices and while traveling, and a high amount of wireless mobile use is expected.
To protect the laptops while connected to untrusted wireless networks, which of the following would be the BEST method for reducing the risk of having the laptops compromised?
- MAC filtering
- Virtualization
- OS hardening
- Application white-listing
-
DRAG DROP
Task: Determine the types of attacks below by selecting an option from the dropdown list.

SY0-501 Part 13 Q07 034 Question 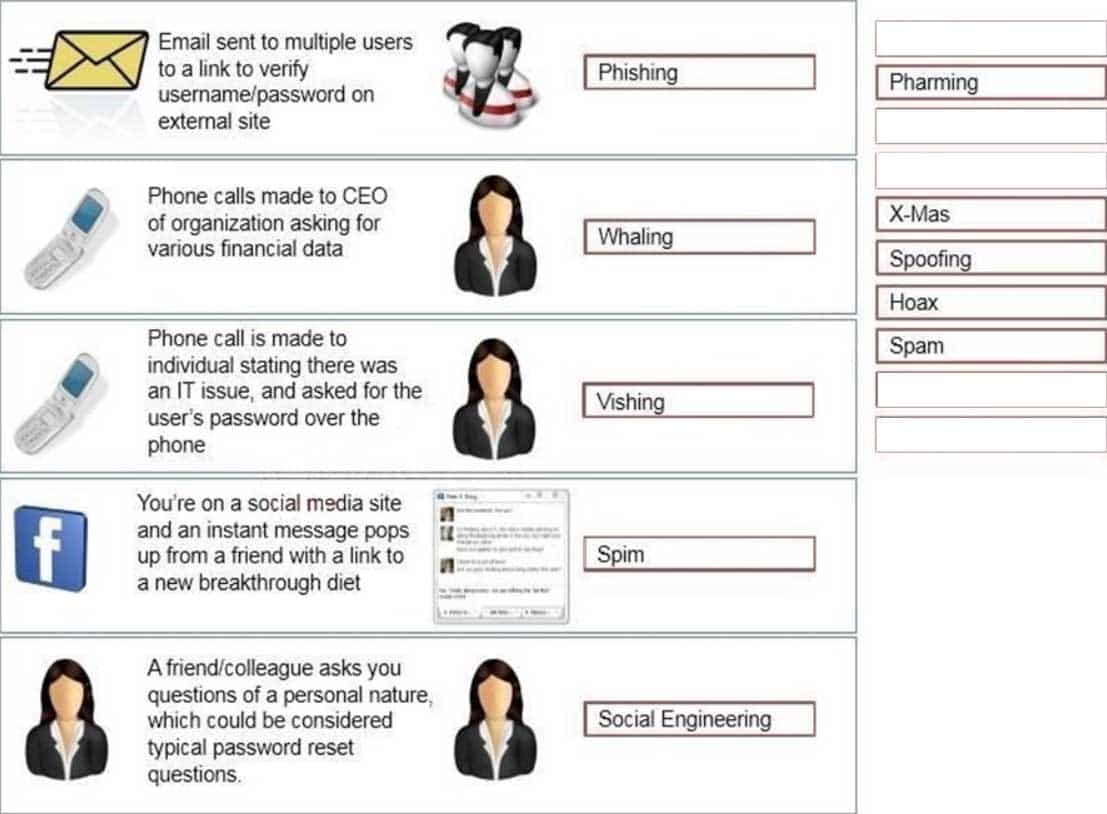
SY0-501 Part 13 Q07 034 Answer Explanation:
A: Phishing is the act of sending an email to a user falsely claiming to be an established legitimate enterprise in an attempt to scam the user into surrendering private information that will be used for identity theft.
Phishing email will direct the user to visit a website where they are asked to update personal information, such as a password, credit card, social security, or bank account numbers, that the legitimate organization already has. The website, however, is bogus and set up only to steal the information the user enters on the page.B: Whaling is a specific kind of malicious hacking within the more general category of phishing, which involves hunting for data that can be used by the hacker. In general, phishing efforts are focused on collecting personal data about users. In whaling, the targets are high-ranking bankers, executives or others in powerful positions or job titles. Hackers who engage in whaling often describe these efforts as “reeling in a big fish,” applying a familiar metaphor to the process of scouring technologies for loopholes and opportunities for data theft. Those who are engaged in whaling may, for example, hack into specific networks where these powerful individuals work or store sensitive data. They may also set up keylogging or other malware on a work station associated with one of these executives. There are many ways that hackers can pursue whaling, leading C-level or top-level executives in business and government to stay vigilant about the possibility of cyber threats.
C: Vishing is the act of using the telephone in an attempt to scam the user into surrendering private information that will be used for identity theft. The scammer usually pretends to be a legitimate business, and fools the victim into thinking he or she will profit.
D: SPIM is a term sometimes used to refer to spam over IM (Instant Messaging). It’s also called just spam, instant spam, or IM marketing. No matter what the name, it consists of unwanted messages transmitted through some form of instant messaging service, which can include Short Message Service (SMS)
E: Social engineering is a non-technical method of intrusion hackers use that relies heavily on human interaction and often involves tricking people into breaking normal security procedures. It is one of the greatest threats that organizations today encounter. A social engineer runs what used to be called a “con game.” For example, a person using social engineering to break into a computer network might try to gain the confidence of an authorized user and get them to reveal information that compromises the network’s security. Social engineers often rely on the natural helpfulness of people as well as on their weaknesses. They might, for example, call the authorized employee with some kind of urgent problem that requires immediate network access. Appealing to vanity, appealing to authority, appealing to greed, and old-fashioned eavesdropping are other typical social engineering techniques.http://www.webopedia.com/TERM/P/phishing.html
http://www.techopedia.com/definition/28643/whaling
http://www.webopedia.com/TERM/V/vishing.html
http://searchsecurity.techtarget.com/definition/social-engineering -
SIMULATION
You have just received some room and WiFi access control recommendations from a security consulting company. Click on each building to bring up available security controls. Please implement the following requirements:
The Chief Executive Officer’s (CEO) office had multiple redundant security measures installed on the door to the office. Remove unnecessary redundancies to deploy three-factor authentication, while retaining the expensive iris render.
The Public Cafe has wireless available to customers. You need to secure the WAP with WPA and place a passphrase on the customer receipts.
In the Data Center you need to include authentication from the “something you know” category and take advantage of the existing smartcard reader on the door.
In the Help Desk Office, you need to require single factor authentication through the use of physical tokens given to guests by the receptionist.
The PII Office has redundant security measures in place. You need to eliminate the redundancy while maintaining three-factor authentication and retaining the more expensive controls.

SY0-501 Part 13 Q08 035 Instructions: The original security controls for each office can be reset at any time by selecting the Reset button. Once you have met the above requirements for each office, select the Save button. When you have completed the entire simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.

SY0-501 Part 13 Q08 036 
SY0-501 Part 13 Q08 037 
SY0-501 Part 13 Q08 038 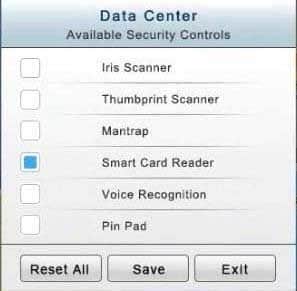
SY0-501 Part 13 Q08 039 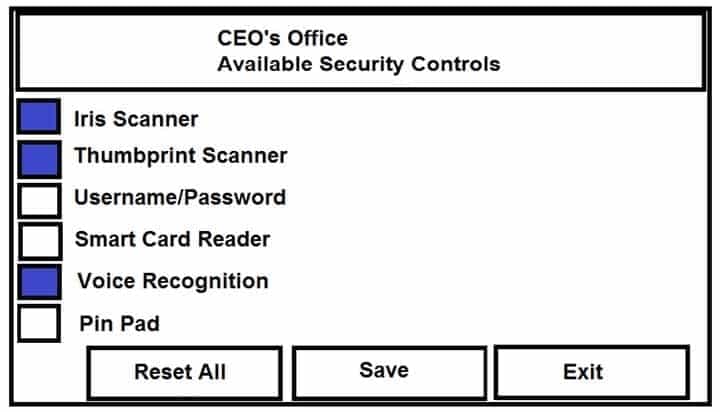
SY0-501 Part 13 Q08 040 - For correct answers: see the explanation below
-
SIMULATION
Task: Configure the firewall (fill out the table) to allow these four rules:
- Only allow the Accounting computer to have HTTPS access to the Administrative server. - Only allow the HR computer to be able to communicate with the Server 2 System over SCP. - Allow the IT computer to have access to both the Administrative Server 1 and Administrative Server 2
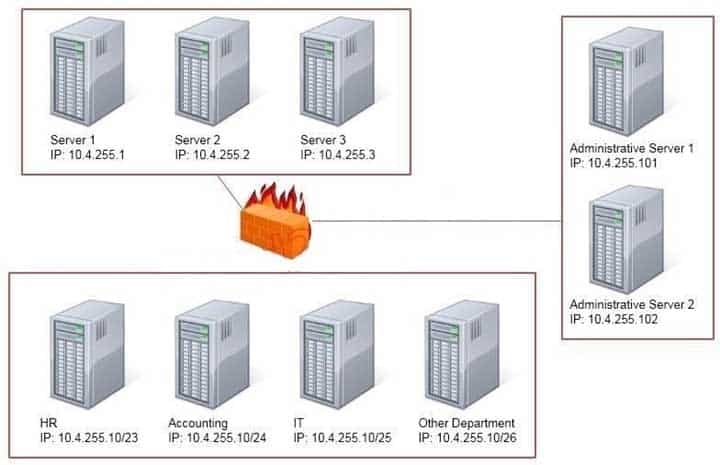
SY0-501 Part 13 Q09 046 
SY0-501 Part 13 Q09 047 - For correct answers: see the explanation below
Explanation:
Use the following answer for this simulation task.
Below table has all the answers required for this question.
SY0-501 Part 13 Q09 048 Firewall rules act like ACLs, and they are used to dictate what traffic can pass between the firewall and the internal network. Three possible actions can be taken based on the rule’s criteria:
Block the connection Allow the connection
Allow the connection only if it is securedTCP is responsible for providing a reliable, one-to-one, connection-oriented session. TCP establishes a connection and ensures that the other end receives any packets sent.
Two hosts communicate packet results with each other. TCP also ensures that packets are decoded and sequenced properly. This connection is persistent during the session.
When the session ends, the connection is torn down.
UDP provides an unreliable connectionless communication method between hosts. UDP is considered a best-effort protocol, but it’s considerably faster than TCP.
The sessions don’t establish a synchronized session like the kind used in TCP, and UDP doesn’t guarantee error-free communications.
The primary purpose of UDP is to send small packets of information.
The application is responsible for acknowledging the correct reception of the data. Port 22 is used by both SSH and SCP with UDP.
Port 443 is used for secure web connections? HTTPS and is a TCP port.
Thus to make sure only the Accounting computer has HTTPS access to the Administrative server you should use TCP port 443 and set the rule to allow communication between 10.4.255.10/24 (Accounting) and 10.4.255.101 (Administrative server1) Thus to make sure that only the HR computer has access to Server2 over SCP you need use of TCP port 22 and set the rule to allow communication between 10.4.255.10/23 (HR) and 10.4.255.2 (server2)
Thus to make sure that the IT computer can access both the Administrative servers you need to use a port and accompanying port number and set the rule to allow communication between: 10.4.255.10.25 (IT computer) and 10.4.255.101 (Administrative server1)
10.4.255.10.25 (IT computer) and 10.4.255.102 (Administrative server2) -
HOTSPOT
For each of the given items, select the appropriate authentication category from the dropdown choices.
Instructions: When you have completed the simulation, please select the Done button to submit.
SY0-501 Part 13 Q10 049 Question 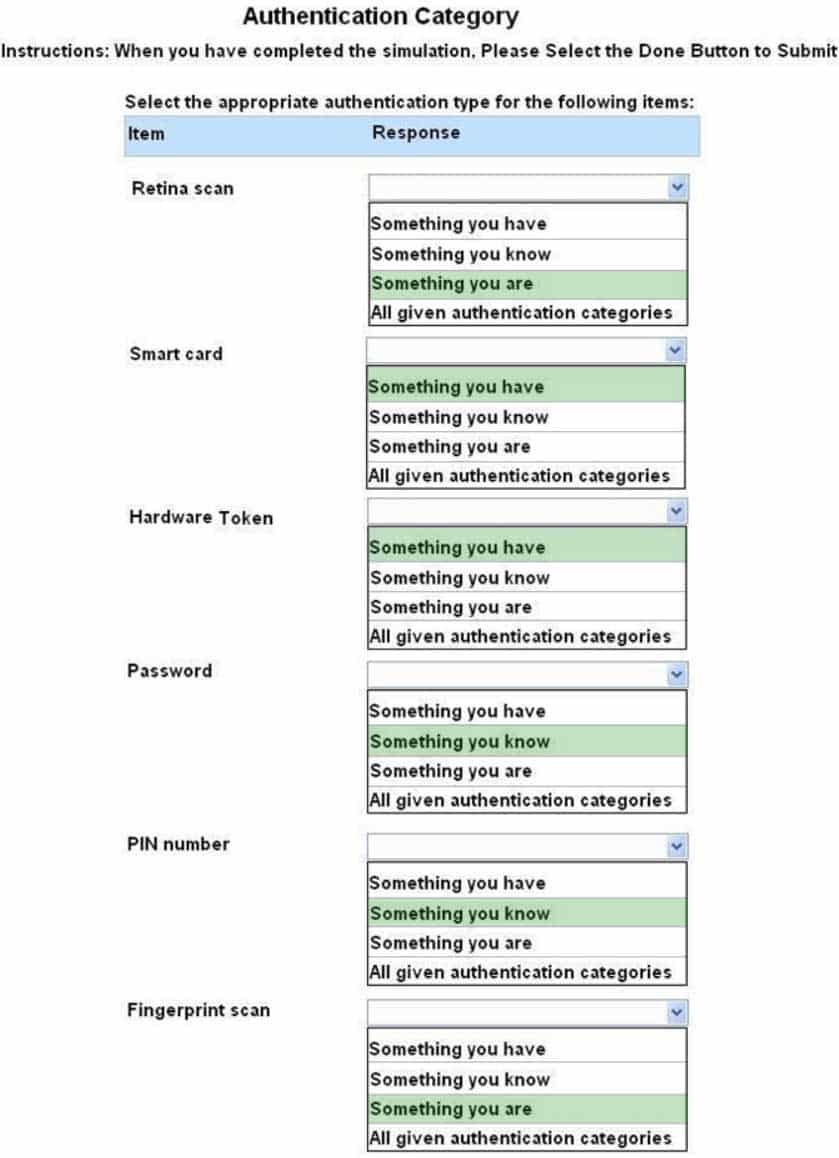
SY0-501 Part 13 Q10 049 Answer Answer:
Something you are includes fingerprints, retina scans, or voice recognition.
Something you have includes smart cards, token devices, or keys.
Something you know includes a password, codes, PINs, combinations, or secret phrases. Somewhere you are including a physical location s or logical addresses, such as domain name, an IP address, or a MAC address.
Something you do includes your typing rhythm, a secret handshake, or a private knock http://en.wikipedia.org/wiki/Password_authentication_protocol#Working_cycle http://en.wikipedia.org/wiki/Smart_card#Security -
During a data breach cleanup, it is discovered that not all of the sites involved have the necessary data wiping tools. The necessary tools are quickly distributed to the required technicians, but when should this problem BEST be revisited?
- Reporting
- Preparation
- Mitigation
- Lessons Learned
-
HOTSPOT
For each of the given items, select the appropriate authentication category from the drop down choices.
Select the appropriate authentication type for the following items: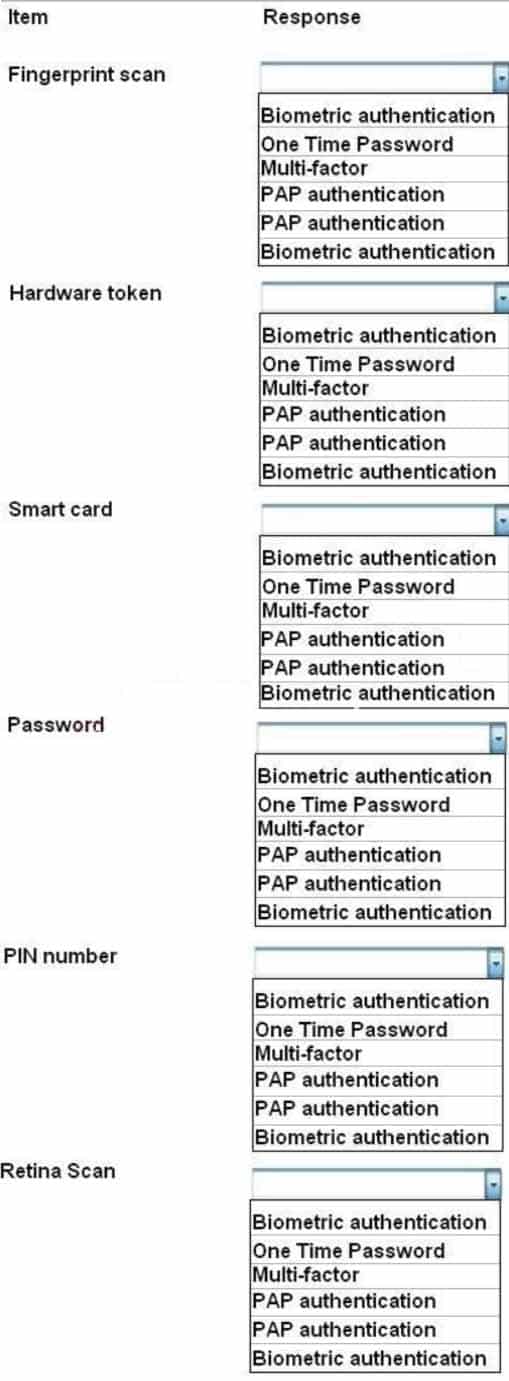
SY0-501 Part 13 Q12 050 Question 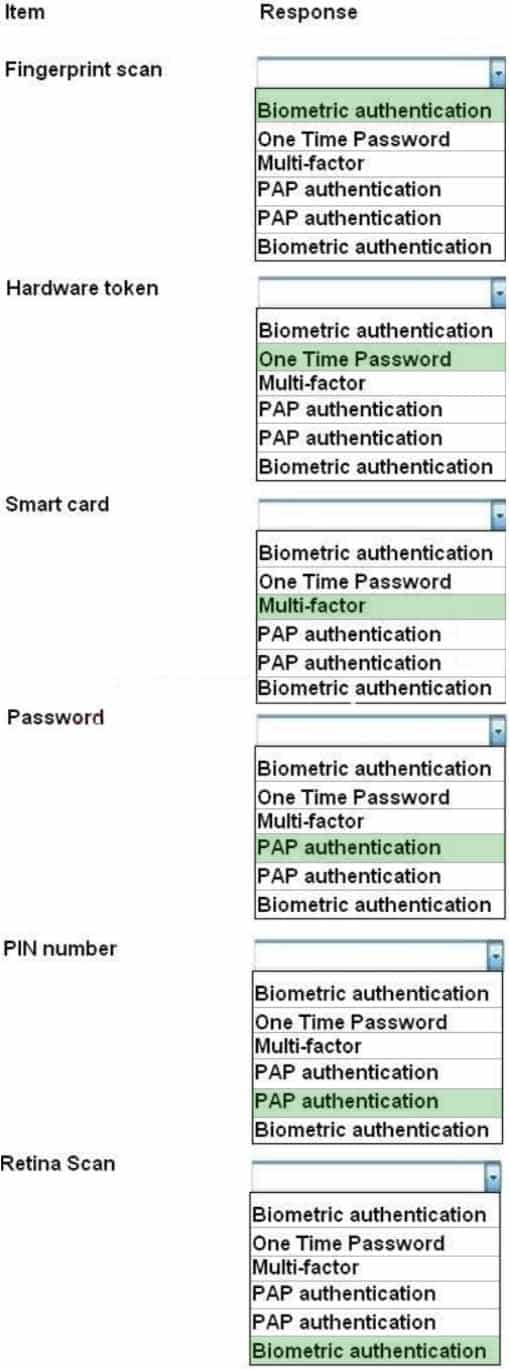
SY0-501 Part 13 Q12 050 Answer -
SIMULATION
A security administrator discovers that an attack has been completed against a node on the corporate network. All available logs were collected and stored.
You must review all network logs to discover the scope of the attack, check the box of the node(s) that have been compromised and drag and drop the appropriate actions to complete the incident response on the network. The environment is a critical production environment; perform the LEAST disruptive actions on the network, while still performing the appropriate incid3nt responses.
Instructions: The web server, database server, IDS, and User PC are clickable. Check the box of the node(s) that have been compromised and drag and drop the appropriate actions to complete the incident response on the network. Not all actions may be used, and order is not important. If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.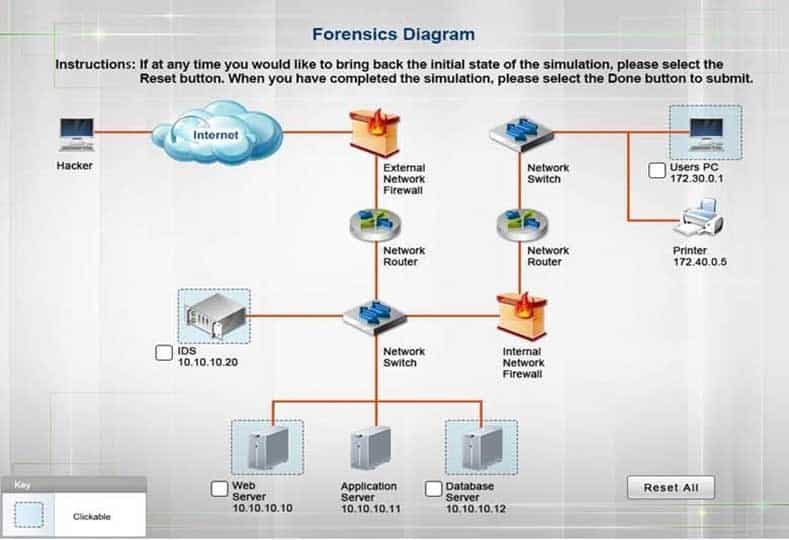
SY0-501 Part 13 Q13 051 - For correct answers: see the explanation below
Explanation:
Database server was attacked, actions should be to capture network traffic and Chain of Custody.
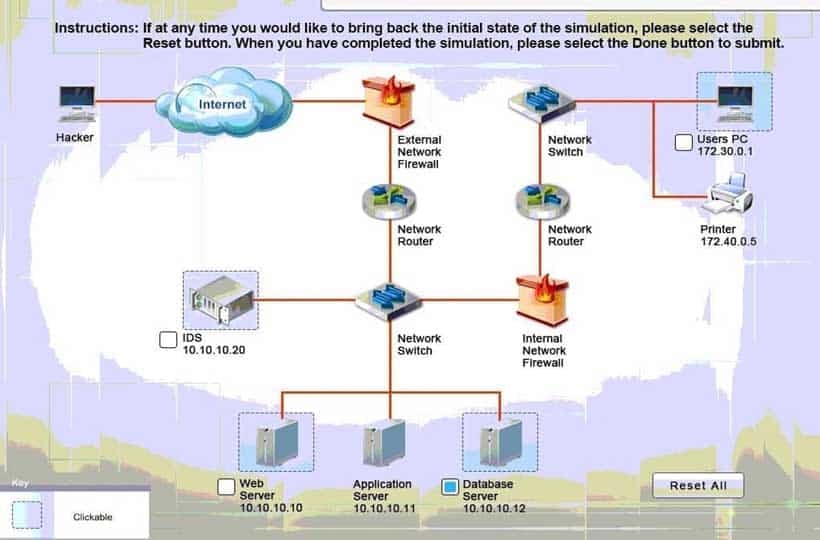
SY0-501 Part 13 Q13 052 
SY0-501 Part 13 Q13 053 IDS Server Log:
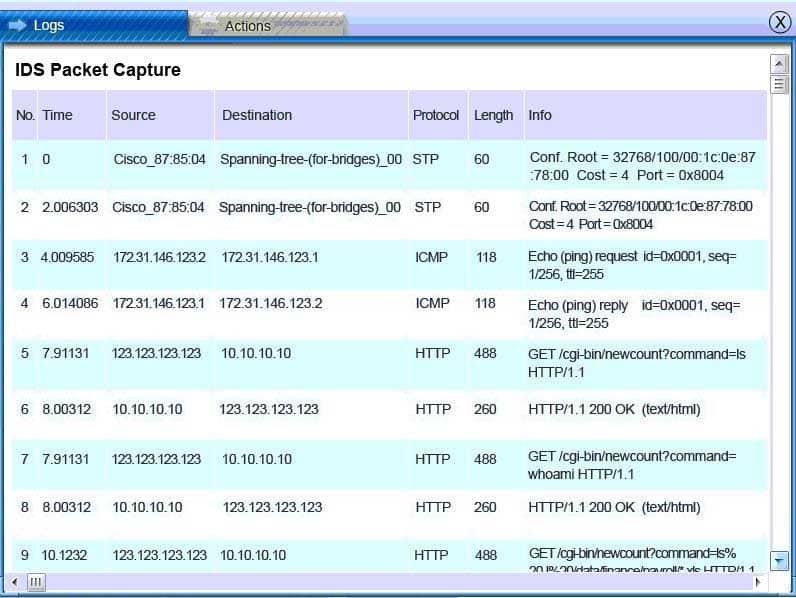
SY0-501 Part 13 Q13 054 Web Server Log:
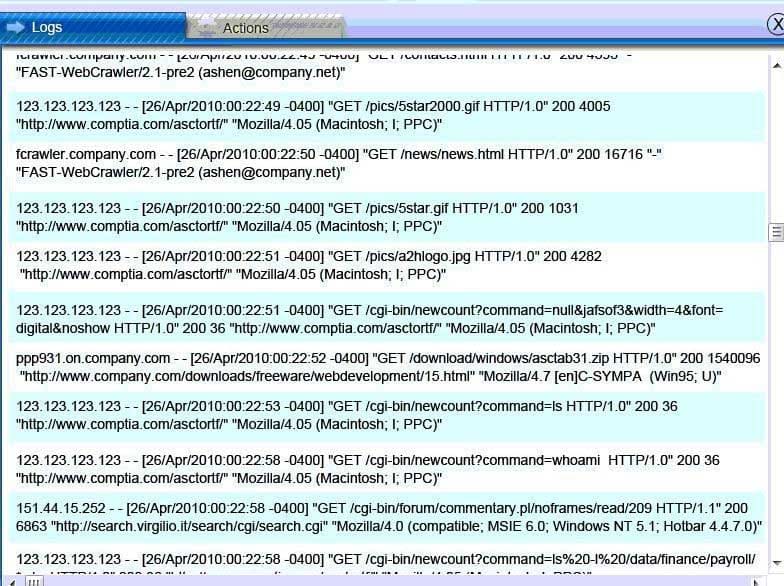
SY0-501 Part 13 Q13 055 
SY0-501 Part 13 Q13 056 Database Server Log:
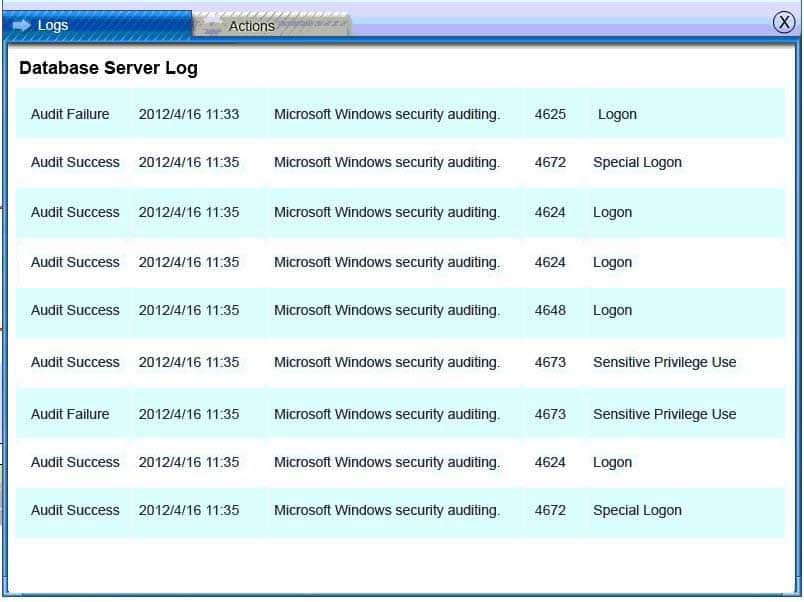
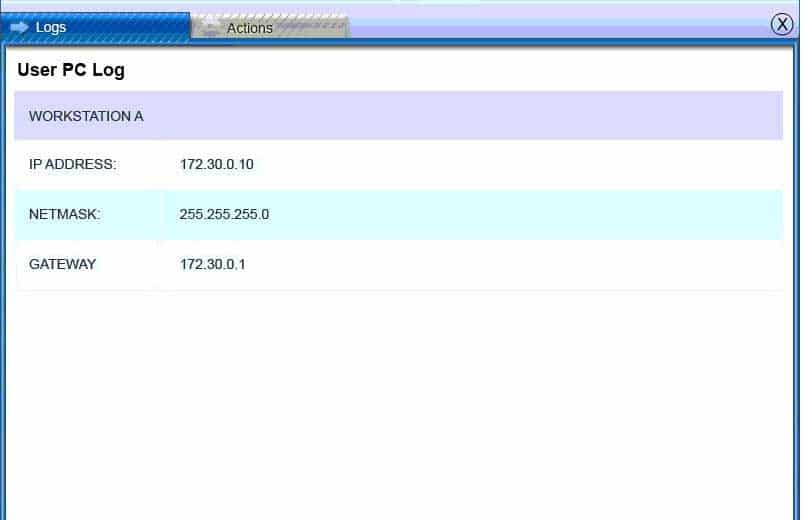
SY0-501 Part 13 Q13 057 Users PC Log:
-
Joe, a technician, is working remotely with his company provided laptop at the coffee shop near his home. Joe is concerned that another patron of the coffee shop may be trying to access his laptop.
Which of the following is an appropriate control to use to prevent the other patron from accessing Joe’s laptop directly?
- full-disk encryption
- Host-based firewall
- Current antivirus definitions
- Latest OS updates
-
An attacker uses a network sniffer to capture the packets of a transaction that adds $20 to a gift card. The attacker then user a function of the sniffer to push those packets back onto the network again, adding another $20 to the gift card. This can be done many times.
Which of the following describes this type of attack?
- Integer overflow attack
- Smurf attack
- Replay attack
- Buffer overflow attack
- Cross-site scripting attack
-
An organization is moving its human resources system to a cloud services provider.
The company plans to continue using internal usernames and passwords with the service provider, but the security manager does not want the service provider to have a company of the passwords.Which of the following options meets all of these requirements?
- Two-factor authentication
- Account and password synchronization
- Smartcards with PINS
- Federated authentication
-
The data backup window has expanded into the morning hours and has begun to affect production users. The main bottleneck in the process is the time it takes to replicate the backups to separate severs at the offsite data center.
Which of the following uses of deduplication could be implemented to reduce the backup window?
- Implement deduplication at the network level between the two locations
- Implement deduplication on the storage array to reduce the amount of drive space needed
- Implement deduplication on the server storage to reduce the data backed up
- Implement deduplication on both the local and remote servers
-
A penetration testing is preparing for a client engagement in which the tester must provide data that proves and validates the scanning tools’ results.
Which of the following is the best method for collecting this information?
- Set up the scanning system’s firewall to permit and log all outbound connections
- Use a protocol analyzer to log all pertinent network traffic
- Configure network flow data logging on all scanning system
- Enable debug level logging on the scanning system and all scanning tools used.
-
Which of the following best describes the initial processing phase used in mobile device forensics?
- The phone should be powered down and the battery removed to preserve the state of data on any internal or removable storage utilized by the mobile device
- The removable data storage cards should be processed first to prevent data alteration when examining the mobile device
- The mobile device should be examined first, then removable storage and lastly the phone without removable storage should be examined again
- The phone and storage cards should be examined as a complete unit after examining the removable storage cards separately.
-
Ann a security analyst is monitoring the IDS console and noticed multiple connections from an internal host to a suspicious call back domain.
Which of the following tools would aid her to decipher the network traffic?
- Vulnerability Scanner
- NMAP
- NETSTAT
- Packet Analyzer