SY0-501 : CompTIA Security+ Certification : Part 16
SY0-501 : CompTIA Security+ Certification : Part 16
-
A malicious attacker has intercepted HTTP traffic and inserted an ASCII line that sets the referrer URL.
Which of the following is the attacker most likely utilizing?
- Header manipulation
- Cookie hijacking
- Cross-site scripting
- Xml injection
-
A company would like to prevent the use of a known set of applications from being used on company computers.
Which of the following should the security administrator implement?
- Whitelisting
- Anti-malware
- Application hardening
- Blacklisting
- Disable removable media
-
A new hire wants to use a personally owned phone to access company resources. The new hire expresses concern about what happens to the data on the phone when they leave the company.
Which of the following portions of the company’s mobile device management configuration would allow the company data to be removed from the device without touching the new hire’s data?
- Asset control
- Device access control
- Storage lock out
- Storage segmentation
-
A consultant has been tasked to assess a client’s network. The client reports frequent network outages. Upon viewing the spanning tree configuration, the consultant notices that an old and law performing edge switch on the network has been elected to be the root bridge.
Which of the following explains this scenario?
- The switch also serves as the DHCP server
- The switch has the lowest MAC address
- The switch has spanning tree loop protection enabled
- The switch has the fastest uplink port
-
An organization is trying to decide which type of access control is most appropriate for the network. The current access control approach is too complex and requires significant overhead.
Management would like to simplify the access control and provide user with the ability to determine what permissions should be applied to files, document, and directories. The access control method that BEST satisfies these objectives is:
- Rule-based access control
- Role-based access control
- Mandatory access control
- Discretionary access control
-
While reviewing the security controls in place for a web-based application, a security controls assessor notices that there are no password strength requirements in place. Because of this vulnerability, passwords might be easily discovered using a brute force attack.
Which of the following password requirements will MOST effectively improve the security posture of the application against these attacks? (Choose two.)
- Minimum complexity
- Maximum age limit
- Maximum length
- Minimum length
- Minimum age limit
- Minimum re-use limit
-
A security administrator determined that users within the company are installing unapproved software. Company policy dictates that only certain applications may be installed or ran on the user’s computers without exception.
Which of the following should the administrator do to prevent all unapproved software from running on the user’s computer?
- Deploy antivirus software and configure it to detect and remove pirated software
- Configure the firewall to prevent the downloading of executable files
- Create an application whitelist and use OS controls to enforce it
- Prevent users from running as administrator so they cannot install software.
-
A security administrator is tasked with implementing centralized management of all network devices. Network administrators will be required to logon to network devices using their LDAP credentials. All command executed by network administrators on network devices must fall within a preset list of authorized commands and must be logged to a central facility.
Which of the following configuration commands should be implemented to enforce this requirement?
- LDAP server 10.55.199.3
- CN=company, CN=com, OU=netadmin, DC=192.32.10.233
- SYSLOG SERVER 172.16.23.50
- TACAS server 192.168.1.100
-
A website administrator has received an alert from an application designed to check the integrity of the company’s website. The alert indicated that the hash value for a particular MPEG file has changed. Upon further investigation, the media appears to be the same as it was before the alert.
Which of the following methods has MOST likely been used?
- Cryptography
- Time of check/time of use
- Man in the middle
- Covert timing
- Steganography
-
An attacker captures the encrypted communication between two parties for a week, but is unable to decrypt the messages. The attacker then compromises the session key during one exchange and successfully compromises a single message. The attacker plans to use this key to decrypt previously captured and future communications, but is unable to.
This is because the encryption scheme in use adheres to:
- Asymmetric encryption
- Out-of-band key exchange
- Perfect forward secrecy
- Secure key escrow
-
Many employees are receiving email messages similar to the one shown below:
From IT department To employee Subject email quota exceeded
Pease click on the following link http:www.website.info/email.php?quota=1Gb and provide your username and password to increase your email quota. Upon reviewing other similar emails, the security administrator realized that all the phishing URLs have the following common elements; they all use HTTP, they all come from .info domains, and they all contain the same URI.
Which of the following should the security administrator configure on the corporate content filter to prevent users from accessing the phishing URL, while at the same time minimizing false positives?
- BLOCK http://www.*.info/”
- DROP http://”website.info/email.php?*
- Redirect http://www,*. Info/email.php?quota=*TOhttp://company.com/corporate_polict.html
- DENY http://*.info/email.php?quota=1Gb
-
A security analyst is reviewing the following packet capture of an attack directed at a company’s server located in the DMZ:
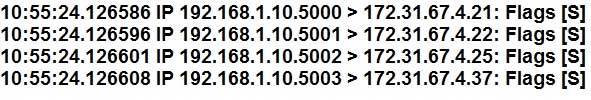
SY0-501 Part 16 Q12 059 Which of the following ACLs provides the BEST protection against the above attack and any further attacks from the same IP, while minimizing service interruption?
- DENY TCO From ANY to 172.31.64.4
- Deny UDP from 192.168.1.0/24 to 172.31.67.0/24
- Deny IP from 192.168.1.10/32 to 0.0.0.0/0
- Deny TCP from 192.168.1.10 to 172.31.67.4
-
The IT department needs to prevent users from installing untested applications.
Which of the following would provide the BEST solution?
- Job rotation
- Least privilege
- Account lockout
- Antivirus
-
An attack that is using interference as its main attack to impede network traffic is which of the following?
- Introducing too much data to a targets memory allocation
- Utilizing a previously unknown security flaw against the target
- Utilizing a previously unknown security flaw against the target
- Inundating a target system with SYN requests
-
An organization wants to conduct secure transactions of large data files. Before encrypting and exchanging the data files, the organization wants to ensure a secure exchange of keys.
Which of the following algorithms is appropriate for securing the key exchange?
- DES
- Blowfish
- DSA
- Diffie-Hellman
- 3DES
-
Ann, a college professor, was recently reprimanded for posting disparaging remarks re-grading her coworkers on a web site. Ann stated that she was not aware that the public was able to view her remakes.
Which of the following security-related trainings could have made Ann aware of the repercussions of her actions?
- Data Labeling and disposal
- Use of social networking
- Use of P2P networking
- Role-based training
-
During a recent audit, it was discovered that many services and desktops were missing security patches.
Which of the following BEST describes the assessment that was performed to discover this issue?
- Network mapping
- Vulnerability scan
- Port Scan
- Protocol analysis
-
When generating a request for a new x.509 certificate for securing a website, which of the following is the MOST appropriate hashing algorithm?
- RC4
- MD5
- HMAC
- SHA
-
The administrator installs database software to encrypt each field as it is written to disk.
Which of the following describes the encrypted data?
- In-transit
- In-use
- Embedded
- At-rest
-
Which of the following allows an application to securely authenticate a user by receiving credentials from a web domain?
- TACACS+
- RADIUS
- Kerberos
- SAML