SY0-501 : CompTIA Security+ Certification : Part 18
SY0-501 : CompTIA Security+ Certification : Part 18
-
An administrator thinks the UNIX systems may be compromised, but a review of system log files provides no useful information. After discussing the situation with the security team, the administrator suspects that the attacker may be altering the log files and removing evidence of intrusion activity.
Which of the following actions will help detect attacker attempts to further alter log files?
- Enable verbose system logging
- Change the permissions on the user’s home directory
- Implement remote syslog
- Set the bash_history log file to “read only”
-
A global gaming console manufacturer is launching a new gaming platform to its customers.
Which of the following controls reduces the risk created by malicious gaming customers attempting to circumvent control by way of modifying consoles?
- Firmware version control
- Manual software upgrades
- Vulnerability scanning
- Automatic updates
- Network segmentation
- Application firewalls
-
An audit has revealed that database administrators are also responsible for auditing database changes and backup logs.
Which of the following access control methodologies would BEST mitigate this concern?
- Time of day restrictions
- Principle of least privilege
- Role-based access control
- Separation of duties
-
An external contractor, who has not been given information about the software or network architecture, is conducting a penetration test. Which of the following BEST describes the test being performed?
- Black box
- White box
- Passive reconnaissance
- Vulnerability scan
-
A security administrator receives an alert from a third-party vendor that indicates a certificate that was installed in the browser has been hijacked at the root of a small public CA. The security administrator knows there are at least four different browsers in use on more than a thousand computers in the domain worldwide.
Which of the following solutions would be BEST for the security administrator to implement to most efficiently assist with this issue?
- SSL
- CRL
- PKI
- ACL
-
A security analyst has set up a network tap to monitor network traffic for vulnerabilities. Which of the following techniques would BEST describe the approach the analyst has taken?
- Compliance scanning
- Credentialed scanning
- Passive vulnerability scanning
- Port scanning
-
Due to regulatory requirements, a security analyst must implement full drive encryption on a Windows file server.
Which of the following should the analyst implement on the system to BEST meet this requirement? (Choose two.)
- Enable and configure EFS on the file system.
- Ensure the hardware supports TPM, and enable it in the BIOS.
- Ensure the hardware supports VT-X, and enable it in the BIOS.
- Enable and configure BitLocker on the drives.
- Enable and configure DFS across the file system.
-
A company’s loss control department identifies theft as a recurring loss type over the past year. Based on the department’s report, the Chief Information Officer (CIO) wants to detect theft of datacenter equipment.
Which of the following controls should be implemented?
- Biometrics
- Cameras
- Motion detectors
- Mantraps
-
Which of the following penetration testing concepts is being used when an attacker uses public Internet databases to enumerate and learn more about a target?
- Reconnaissance
- Initial exploitation
- Pivoting
- Vulnerability scanning
- White box testing
-
While performing a penetration test, the technicians want their efforts to go unnoticed for as long as possible while they gather useful data about the network they are assessing.
Which of the following would be the BEST choice for the technicians?
- Vulnerability scanner
- Offline password cracker
- Packet sniffer
- Banner grabbing
-
A security analyst captures forensic evidence from a potentially compromised system for further investigation. The evidence is documented and securely stored to FIRST:
- maintain the chain of custody.
- preserve the data.
- obtain a legal hold.
- recover data at a later time.
-
A security analyst is investigating a security breach. Upon inspection of the audit an access logs, the analyst notices the host was accessed and the /etc/passwd file was modified with a new entry for username “gotcha” and user ID of 0. Which of the following are the MOST likely attack vector and tool the analyst should use to determine if the attack is still ongoing? (Select TWO)
- Logic bomb
- Backdoor
- Keylogger
- Netstat
- Tracert
- Ping
-
A company recently replaced its unsecure email server with a cloud-based email and collaboration solution that is managed and insured by a third party. Which of the following actions did the company take regarding risks related to its email and collaboration services?
- Transference
- Acceptance
- Mitigation
- Deterrence
-
A security administrator is reviewing the following network capture:
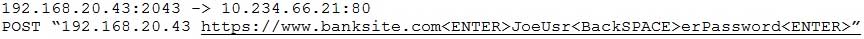
SY0-501 Part 18 Q14 061 Which of the following malware is MOST likely to generate the above information?
- Keylogger
- Ransomware
- Logic bomb
- Adware
-
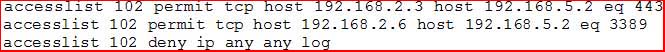
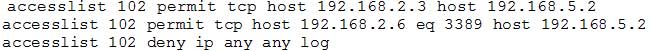
A network administrator adds an ACL to allow only HTTPS connections form host 192.168.2.3 to web server 192.168.5.2. After applying the rule, the host is unable to access the server. The network administrator runs the output and notices the configuration below:

SY0-501 Part 18 Q15 062 Which of the following rules would be BEST to resolve the issue?
-
A datacenter recently experienced a breach. When access was gained, an RF device was used to access an air-gapped and locked server rack. Which of the following would BEST prevent this type of attack?
- Faraday cage
- Smart cards
- Infrared detection
- Alarms
-
A security analyst is working on a project that requires the implementation of a stream cipher. Which of the following should the analyst use?
- Hash function
- Elliptic curve
- Symmetric algorithm
- Public key cryptography
-
Which of the following would allow for the QUICKEST restoration of a server into a warm recovery site in a case in which server data mirroring is not enabled?
- Full backup
- Incremental backup
- Differential backup
- Snapshot
-
In determining when it may be necessary to perform a credentialed scan against a system instead of a non-credentialed scan, which of the following requirements is MOST likely to influence this decision?
- The scanner must be able to enumerate the host OS of devices scanned.
- The scanner must be able to footprint the network.
- The scanner must be able to check for open ports with listening services.
- The scanner must be able to audit file system permissions
-
The computer resource center issued smartphones to all first-level and above managers. The managers have the ability to install mobile tools. Which of the following tools should be implemented to control the types of tools the managers install?
- Download manager
- Content manager
- Segmentation manager
- Application manager