SY0-501 : CompTIA Security+ Certification : Part 19
SY0-501 : CompTIA Security+ Certification : Part 19
-
Which of the following BEST describes a network-based attack that can allow an attacker to take full control of a vulnerable host?
- Remote exploit
- Amplification
- Sniffing
- Man-in-the-middle
-
A security auditor is putting together a report for the Chief Executive Officer (CEO) on personnel security and its impact on the security posture of the whole organization. Which of the following would be the MOST important factor to consider when it comes to personnel security?
- Insider threats
- Privilege escalation
- Hacktivist
- Phishing through social media
- Corporate espionage
-
A security administrator wants to configure a company’s wireless network in a way that will prevent wireless clients from broadcasting the company’s SSID. Which of the following should be configured on the company’s access points?
- Enable ESSID broadcast
- Enable protected management frames
- Enable wireless encryption
- Disable MAC authentication
- Disable WPS
- Disable SSID broadcast
-
A wireless network has the following design requirements:
– Authentication must not be dependent on enterprise directory service
– It must allow background reconnection for mobile users
– It must not depend on user certificatesWhich of the following should be used in the design to meet the requirements? (Choose two.)
- PEAP
- PSK
- Open systems authentication
- EAP-TLS
- Captive portals
-
Which of the following strategies should a systems architect use to minimize availability risks due to insufficient storage capacity?
- High availability
- Scalability
- Distributive allocation
- Load balancing
-
A security engineer wants to implement a site-to-site VPN that will require SSL certificates for mutual authentication. Which of the following should the engineer implement if the design requires client MAC address to be visible across the tunnel?
- Tunnel mode IPSec
- Transport mode VPN IPSec
- L2TP
- SSL VPN
-
After surfing the Internet, Joe, a user, woke up to find all his files were corrupted. His wallpaper was replaced by a message stating the files were encrypted and he needed to transfer money to a foreign country to recover them. Joe is a victim of:
- a keylogger
- spyware
- ransomware
- a logic bomb
-
Security administrators attempted corrective action after a phishing attack. Users are still experiencing trouble logging in, as well as an increase in account lockouts. Users’ email contacts are complaining of an increase in spam and social networking requests. Due to the large number of affected accounts, remediation must be accomplished quickly.
Which of the following actions should be taken FIRST? (Choose two.)
- Disable the compromised accounts
- Update WAF rules to block social networks
- Remove the compromised accounts with all AD groups
- Change the compromised accounts’ passwords
- Disable the open relay on the email server
- Enable sender policy framework
-
Which of the following allows an auditor to test proprietary-software compiled code for security flaws?
- Fuzzing
- Static review
- Code signing
- Regression testing
-
Ann, a user, states that her machine has been behaving erratically over the past week. She has experienced slowness and input lag and found text files that appear to contain pieces of her emails or online conversations with coworkers. The technician runs a standard virus scan but detects nothing.
Which of the following types of malware has infected the machine?
- Ransomware
- Rootkit
- Backdoor
- Keylogger
-
A security administrator wants to implement a logon script that will prevent MITM attacks on the local LAN.
Which of the following commands should the security administrator implement within the script to accomplish this task?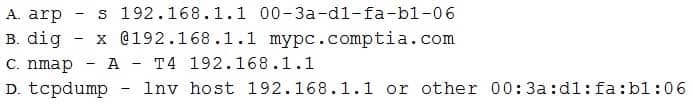
SY0-501 Part 19 Q11 067 - Option A
- Option B
- Option C
- Option D
-
Which of the following is the BEST reason for salting a password hash before it is stored in a database?
- To prevent duplicate values from being stored
- To make the password retrieval process very slow
- To protect passwords from being saved in readable format
- To prevent users from using simple passwords for their access credentials
-
An actor downloads and runs a program against a corporate login page. The program imports a list of usernames and passwords, looking for a successful attempt.
Which of the following terms BEST describes the actor in this situation?
- Script kiddie
- Hacktivist
- Cryptologist
- Security auditor
-
An organization wants to utilize a common, Internet-based third-party provider for authorization and authentication. The provider uses a technology based on OAuth 2.0 to provide required services. To which of the following technologies is the provider referring?
- Open ID Connect
- SAML
- XACML
- LDAP
-
A penetration tester harvests potential usernames from a social networking site. The penetration tester then uses social engineering to attempt to obtain associated passwords to gain unauthorized access to shares on a network server.
Which of the following methods is the penetration tester MOST likely using?
- Escalation of privilege
- SQL injection
- Active reconnaissance
- Proxy server
-
Which of the following could occur when both strong and weak ciphers are configured on a VPN concentrator? (Choose two.)
- An attacker could potentially perform a downgrade attack.
- The connection is vulnerable to resource exhaustion.
- The integrity of the data could be at risk.
- The VPN concentrator could revert to L2TP.
- The IPSec payload is reverted to 16-bit sequence numbers.
-
Which of the following is the BEST choice for a security control that represents a preventive and corrective logical control at the same time?
- Security awareness training
- Antivirus
- Firewalls
- Intrusion detection system
-
A web developer improves client access to the company’s REST API. Authentication needs to be tokenized but not expose the client’s password.
Which of the following methods would BEST meet the developer’s requirements?
- SAML
- LDAP
- OAuth
- Shibboleth
-
A vulnerability scan is being conducted against a desktop system. The scan is looking for files, versions, and registry values known to be associated with system vulnerabilities. Which of the following BEST describes the type of scan being performed?
- Non-intrusive
- Authenticated
- Credentialed
- Active
-
A security analyst is updating a BIA document. The security analyst notices the support vendor’s time to replace a server hard drive went from eight hours to two hours.
Given these new metrics, which of the following can be concluded? (Choose two.)
- The MTTR is faster.
- The MTTR is slower.
- The RTO has increased.
- The RTO has decreased.
- The MTTF has increased.
- The MTTF has decreased.