SY0-501 : CompTIA Security+ Certification : Part 28
SY0-501 : CompTIA Security+ Certification : Part 28
-
A security administrator suspects that a DDoS attack is affecting the DNS server. The administrator accesses a workstation with the hostname of workstation01 on the network and obtains the following output from the ipconfig command:
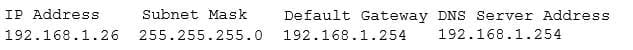
SY0-501 Part 28 Q01 073 The administrator successfully pings the DNS server from the workstation. Which of the following commands should be issued from the workstation to verify the DDoS attack is no longer occuring?
- dig www.google.com
- dig 192.168.1.254
- dig workstation01.com
- dig 192.168.1.26
-
A security administrator has configured a RADIUS and a TACACS+ server on the company’s network. Network devices will be required to connect to the TACACS+ server for authentication and send accounting information to the RADIUS server. Given the following information:
RADIUS IP: 192.168.20.45 TACACS+ IP: 10.23.65.7
Which of the following should be configured on the network clients? (Choose two.)
- Accounting port: TCP 389
- Accounting port: UDP 1812
- Accounting port: UDP 1813
- Authentication port: TCP 49
- Authentication port: TCP 88
- Authentication port: UDP 636
-
A number of employees report that parts of an ERP application are not working. The systems administrator reviews the following information from one of the employee workstations:
Execute permission denied: financemodule.dll Execute permission denied: generalledger.dll
Which of the following should the administrator implement to BEST resolve this issue while minimizing risk and attack exposure?
- Update the application blacklist
- Verify the DLL’s file integrity
- Whitelist the affected libraries
- Place the affected employees in the local administrator’s group
-
A security analyst receives a notification from the IDS after working hours, indicating a spike in network traffic. Which of the following BEST describes this type of IDS?
- Anomaly-based
- Stateful
- Host-based
- Signature-based
-
An instructor is teaching a hands-on wireless security class and needs to configure a test access point to show students an attack on a weak protocol. Which of the following configurations should the instructor implement?
- WPA2
- WPA
- EAP
- WEP
-
A security analyst is hardening a large-scale wireless network. The primary requirements are the following:
– Must use authentication through EAP-TLS certificates
– Must use an AAA server
– Must use the most secure encryption protocolGiven these requirements, which of the following should the analyst implement and recommend? (Choose two.)
- 802.1X
- 802.3
- LDAP
- TKIP
- CCMP
- WPA2-PSK
-
A company recently experienced data exfiltration via the corporate network. In response to the breach, a security analyst recommends deploying an out-of-band IDS solution. The analyst says the solution can be implemented without purchasing any additional network hardware. Which of the following solutions will be used to deploy the IDS?
- Network tap
- Network proxy
- Honeypot
- Port mirroring
-
An organization wants to implement a solution that allows for automated logical controls for network defense. An engineer plans to select an appropriate network security component, which automates response actions based on security threats to the network. Which of the following would be MOST appropriate based on the engineer’s requirements?
- NIPS
- HIDS
- Web proxy
- Elastic load balancer
- NAC
-
A highly complex password policy has made it nearly impossible to crack account passwords. Which of the following might a hacker still be able to perform?
- Pass-the-hash attack
- ARP poisoning attack
- Birthday attack
- Brute force attack
-
Which of the following is the main difference between an XSS vulnerability and a CSRF vulnerability?
- XSS needs the attacker to be authenticated to the trusted server.
- XSS does not need the victim to be authenticated to the trusted server.
- CSRF needs the victim to be authenticated to the trusted server.
- CSRF does not need the victim to be authenticated to the trusted server.
- CSRF does not need the attacker to be authenticated to the trusted server.
-
A group of developers is collaborating to write software for a company. The developers need to work in subgroups and control who has access to their modules. Which of the following access control methods is considered user-centric?
- Time-based
- Mandatory
- Rule-based
- Discretionary
-
Which of the following methods minimizes the system interaction when gathering information to conduct a vulnerability assessment of a router?
- Download the configuration
- Run a credentialed scan.
- Conduct the assessment during downtime
- Change the routing to bypass the router.
-
Which of the following BEST explains why sandboxing is a best practice for testing software from an untrusted vendor prior to an enterprise deployment?
- It allows the software to run in an unconstrained environment with full network access.
- It eliminates the possibility of privilege escalation attacks against the local VM host.
- It facilitates the analysis of possible malware by allowing it to run until resources are exhausted.
- It restricts the access of the software to a contained logical space and limits possible damage.
-
A small- to medium-sized company wants to block the use of USB devices on its network. Which of the following is the MOST cost-effective way for the security analyst to prevent this?
- Implement a DLP system
- Apply a GPO
- Conduct user awareness training
- Enforce the AUP.
-
Which of the following is the BEST way for home users to mitigate vulnerabilities associated with IoT devices on their home networks?
- Power off the devices when they are not in use.
- Prevent IoT devices from contacting the Internet directly.
- Apply firmware and software updates upon availability.
- Deploy a bastion host on the home network.
-
Corporations choose to exceed regulatory framework standards because of which of the following incentives?
- It improves the legal defensibility of the company.
- It gives a social defense that the company is not violating customer privacy laws.
- It proves to investors that the company takes APT cyber actors seriously
- It results in overall industrial security standards being raised voluntarily.
-
A security administrator is implementing a new WAF solution and has placed some of the web servers behind the WAF, with the WAF set to audit mode. When reviewing the audit logs of external requests and posts to the web servers, the administrator finds the following entry:
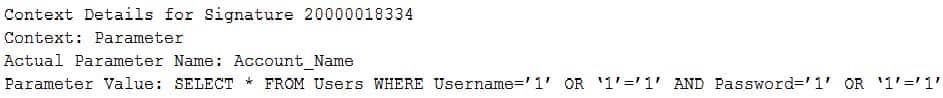
SY0-501 Part 28 Q17 074 Based on this data, which of the following actions should the administrator take?
- Alert the web server administrators to a misconfiguration.
- Create a blocking policy based on the parameter values.
- Change the parameter name ‘Account_Name’ identified in the log.
- Create an alert to generate emails for abnormally high activity.
-
A call center company wants to implement a domain policy primarily for its shift workers. The call center has large groups with different user roles. Management wants to monitor group performance. Which of the following is the BEST solution for the company to implement?
- Reduced failed logon attempts
- Mandatory password changes
- Increased account lockout time.
- Time-of-day restrictions
-
A buffer overflow can result in:
- loss of data caused by unauthorized command execution.
- privilege escalation caused by TPM override.
- reduced key strength due to salt manipulation.
- repeated use of one-time keys.
-
Users are attempting to access a company’s website but are transparently redirected to another websites. The users confirm the URL is correct. Which of the following would BEST prevent this issue in the future?
- DNSSEC
- HTTPS
- IPSec
- TLS/SSL