SY0-501 : CompTIA Security+ Certification : Part 31
SY0-501 : CompTIA Security+ Certification : Part 31
-
A law office has been leasing dark fiber from a local telecommunications company to connect a remote office to company headquarters. The telecommunications company has decided to discontinue its dark fiber product and is offering an MPLS connection, which the law office feels is too expensive. Which of the following is the BEST solution for the law office?
- Remote access VPN
- VLAN
- VPN concentrator
- Site-to-site VPN
-
An analyst is part of a team that is investigating a potential breach of sensitive data at a large financial services organization. The organization suspects a breach occurred when proprietary data was disclosed to the public. The team finds servers were accessed using shared credentials that have been in place for some time. In addition, the team discovers undocumented firewall rules, which provided unauthorized external access to a server. Suspecting the activities of a malicious insider threat, which of the following was MOST likely to have been utilized to exfiltrate the proprietary data?
- Keylogger
- Botnet
- Crypto-malware
- Backdoor
- Ransomware
- DLP
-
An organization is providing employees on the shop floor with computers that will log their time based on when they sign on and off the network.
Which of the following account types should the employees receive?
- Shared account
- Privileged account
- User account
- Service account
-
A member of the human resources department is searching for candidate resumes and encounters the following error message when attempting to access popular job search websites:
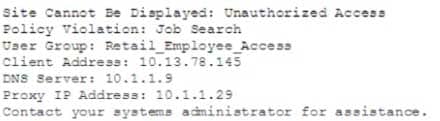
SY0-501 Part 31 Q04 086 Which of the following would resolve this issue without compromising the company’s security policies?
- Renew the DNS settings and IP address on the employee’s computer
- Add the employee to a less restrictive group on the content filter
- Remove the proxy settings from the employee’s web browser
- Create an exception for the job search sites in the host-based firewall on the employee’s computer
-
A security analyst is reviewing the password policy for a service account that is used for a critical network service. The password policy for this account is as follows:

SY0-501 Part 31 Q05 087 Which of the following adjustments would be the MOST appropriate for the service account?
- Disable account lockouts
- Set the maximum password age to 15 days
- Set the minimum password age to seven days
- Increase password length to 18 characters
-
An employee in the finance department receives an email, which appears to come from the Chief Financial Officer (CFO), instructing the employee to immediately wire a large sum of money to a vendor. Which of the following BEST describes the principles of social engineering used? (Choose two.)
- Familiarity
- Scarcity
- Urgency
- Authority
- Consensus
-
A security administrator has replaced the firewall and notices a number of dropped connections. After looking at the data the security administrator sees the following information that was flagged as a possible issue:

SY0-501 Part 31 Q07 088 Which of the following can the security administrator determine from this?
- An SQL injection attack is being attempted
- Legitimate connections are being dropped
- A network scan is being done on the system
- An XSS attack is being attempted
-
A penetration testing team deploys a specifically crafted payload to a web server, which results in opening a new session as the web server daemon. This session has full read/write access to the file system and the admin console. Which of the following BEST describes the attack?
- Domain hijacking
- Injection
- Buffer overflow
- Privilege escalation
-
A corporation is concerned that, if a mobile device is lost, any sensitive information on the device could be accessed by third parties. Which of the following would BEST prevent this from happening?
- Initiate remote wiping on lost mobile devices
- Use FDE and require PINs on all mobile devices
- Use geolocation to track lost devices
- Require biometric logins on all mobile devices
-
Ann, a security analyst, wants to implement a secure exchange of email. Which of the following is the BEST option for Ann to implement?
- PGP
- HTTPS
- WPA
- TLS
-
After a security assessment was performed on the enterprise network, it was discovered that:
1. Configuration changes have been made by users without the consent of IT.
2. Network congestion has increased due to the use of social media.
3. Users are accessing file folders and network shares that are beyond the scope of their need to know.Which of the following BEST describe the vulnerabilities that exist in this environment? (Choose two.)
- Poorly trained users
- Misconfigured WAP settings
- Undocumented assets
- Improperly configured accounts
- Vulnerable business processes
-
A security administrator wants to determine if a company’s web servers have the latest operating system and application patches installed. Which of the following types of vulnerability scans should be conducted?
- Non-credentialed
- Passive
- Port
- Credentialed
- Red team
- Active
-
During a recent audit, several undocumented and unpatched devices were discovered on the internal network. Which of the following can be done to prevent similar occurrences?
- Run weekly vulnerability scans and remediate any missing patches on all company devices
- Implement rogue system detection and configure automated alerts for new devices
- Install DLP controls and prevent the use of USB drives on devices
- Configure the WAPs to use NAC and refuse connections that do not pass the health check
-
A company needs to implement a system that only lets a visitor use the company’s network infrastructure if the visitor accepts the AUP. Which of the following should the company use?
- WiFi-protected setup
- Password authentication protocol
- Captive portal
- RADIUS
-
An analyst is currently looking at the following output:

SY0-501 Part 31 Q15 089 Which of the following security issues has been discovered based on the output?
- Insider threat
- License compliance violation
- Unauthorized software
- Misconfigured admin permissions
-
A company has purchased a new SaaS application and is in the process of configuring it to meet the company’s needs. The director of security has requested that the SaaS application be integrated into the company’s IAM processes. Which of the following configurations should the security administrator set up in order to complete this request?
- LDAP
- RADIUS
- SAML
- NTLM
-
An organization wants to implement a method to correct risks at the system/application layer. Which of the following is the BEST method to accomplish this goal?
- IDS/IPS
- IP tunneling
- Web application firewall
- Patch management
-
A company recently updated its website to increase sales. The new website uses PHP forms for leads and provides a directory with sales staff and their phone numbers. A systems administrator is concerned with the new website and provides the following log to support the concern:
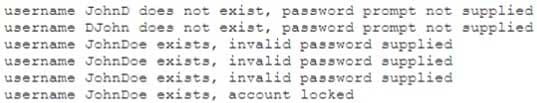
SY0-501 Part 31 Q18 090 Which of the following is the systems administrator MOST likely to suggest to the Chief Information Security Officer (CISO) based on the above?
- Changing the account standard naming convention
- Implementing account lockouts
- Discontinuing the use of privileged accounts
- Increasing the minimum password length from eight to ten characters
-
A company hired a firm to test the security posture of its database servers and determine if any vulnerabilities can be exploited. The company provided limited imformation pertaining to the infrastructure and database server. Which of the following forms of testing does this BEST describe?
- Black box
- Gray box
- White box
- Vulnerability scanning
-
When considering IoT systems, which of the following represents the GREATEST ongoing risk after a vulnerability has been discovered?
- Difficult-to-update firmware
- Tight integration to existing systems
- IP address exhaustion
- Not using industry standards