SY0-501 : CompTIA Security+ Certification : Part 33
SY0-501 : CompTIA Security+ Certification : Part 33
-
An organization employee resigns without giving adequate notice. The following day, it is determined that the employee is still in possession of several company-owned mobile devices.
Which of the following could have reduced the risk of this occurring? (Choose two.)
- Proper offboarding procedures
- Acceptable use policies
- Non-disclosure agreements
- Exit interviews
- Background checks
- Separation of duties
-
Which of the following differentiates ARP poisoning from a MAC spoofing attack?
- ARP poisoning uses unsolicited ARP replies.
- ARP poisoning overflows a switch’s CAM table.
- MAC spoofing uses DHCPOFFER/DHCPACK packets.
- MAC spoofing can be performed across multiple routers.
-
A security administrator has completed a monthly review of DNS server query logs. The administrator notices continuous name resolution attempts from a large number of internal hosts to a single Internet addressable domain name. The security administrator then correlated those logs with the establishment of persistent TCP connections out to this domain. The connections seem to be carrying on the order of kilobytes of data per week.
Which of the following is the MOST likely explanation for this anomaly?
- An attacker is exfiltrating large amounts of proprietary company data.
- Employees are playing multiplayer computer games.
- A worm is attempting to spread to other hosts via SMB exploits.
- Internal hosts have become members of a botnet.
-
An audit found that an organization needs to implement job rotation to be compliant with regulatory requirements. To prevent unauthorized access to systems after an individual changes roles or departments, which of the following should the organization implement?
- Permission auditing and review
- Exit interviews
- Offboarding
- Multifactor authentication
-
A company has just completed a vulnerability scan of its servers. A legacy application that monitors the HVAC system in the datacenter presents several challenges, as the application vendor is no longer in business.
Which of the following secure network architecture concepts would BEST protect the other company servers if the legacy server were to be exploited?
- Virtualization
- Air gap
- VLAN
- Extranet
-
Which of the following methods is used by internal security teams to assess the security of internally developed applications?
- Active reconnaissance
- Pivoting
- White box testing
- Persistence
-
A company wants to implement a wireless network with the following requirements:
– All wireless users will have a unique credential.
– User certificates will not be required for authentication.
– The company’s AAA infrastructure must be utilized.
– Local hosts should not store authentication tokens.Which of the following should be used in the design to meet the requirements?
- EAP-TLS
- WPS
- PSK
- PEAP
-
A technician has discovered a crypto-virus infection on a workstation that has access to sensitive remote resources.
Which of the following is the immediate NEXT step the technician should take?
- Determine the source of the virus that has infected the workstation.
- Sanitize the workstation’s internal drive.
- Reimage the workstation for normal operation.
- Disable the network connections on the workstation.
-
A user is unable to open a file that has a grayed-out icon with a lock. The user receives a pop-up message indicating that payment must be sent in Bitcoin to unlock the file. Later in the day, other users in the organization lose the ability to open files on the server.
Which of the following has MOST likely occurred? (Choose three.)
- Crypto-malware
- Adware
- Botnet attack
- Virus
- Ransomware
- Backdoor
- DDoS attack
-
A security administrator is configuring a RADIUS server for wireless authentication. The configuration must ensure client credentials are encrypted end-to-end between the client and the authenticator.
Which of the following protocols should be configured on the RADIUS server? (Choose two.)
- PAP
- MSCHAP
- PEAP
- NTLM
- SAML
-
A security engineer implements multiple technical measures to secure an enterprise network. The engineer also works with the Chief Information Officer (CIO) to implement policies to govern user behavior.
Which of the following strategies is the security engineer executing?
- Baselining
- Mandatory access control
- Control diversity
- System hardening
-
A security analyst identified an SQL injection attack.
Which of the following is the FIRST step in remediating the vulnerability?
- Implement stored procedures.
- Implement proper error handling.
- Implement input validations.
- Implement a WAF.
-
Joe, a contractor, is hired by a firm to perform a penetration test against the firm’s infrastructure. When conducting the scan, he receives only the network diagram and the network list to scan against the network.
Which of the following scan types is Joe performing?
- Authenticated
- White box
- Automated
- Gray box
-
Which of the following types of security testing is the MOST cost-effective approach used to analyze existing code and identity areas that require patching?
- Black box
- Gray box
- White box
- Red box
- Blue box
-
Which of the following needs to be performed during a forensics investigation to ensure the data contained in a drive image has not been compromised?
- Follow the proper chain of custody procedures.
- Compare the image hash to the original hash.
- Ensure a legal hold has been placed on the image.
- Verify the time offset on the image file.
-
A company is performing an analysis of the corporate enterprise network with the intent of identifying any one system, person, function, or service that, when neutralized, will cause or cascade disproportionate damage to the company’s revenue, referrals, and reputation.
Which of the following an element of the BIA that this action is addressing?
- Identification of critical systems
- Single point of failure
- Value assessment
- Risk register
-
An analyst generates the following color-coded table shown in the exhibit to help explain the risk of potential incidents in the company. The vertical axis indicates the likelihood of an incident, while the horizontal axis indicates the impact.
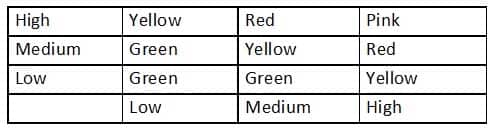
SY0-501 Part 33 Q17 093 Which of the following is this table an example of?
- Internal threat assessment
- Privacy impact assessment
- Qualitative risk assessment
- Supply chain assessment
-
An office recently completed digitizing all its paper records. Joe, the data custodian, has been tasked with the disposal of the paper files, which include:
– Intellectual property
– Payroll records
– Financial information
– Drug screening resultsWhich of the following is the BEST way to dispose of these items?
- Schredding
- Pulping
- Deidentifying
- Recycling
-
Upon learning about a user who has reused the same password for the past several years, a security specialist reviews the logs. The following is an extraction of the report after the most recent password change requirement:

SY0-501 Part 33 Q19 094 Which of the following security controls is the user’s behavior targeting?
- Password expiration
- Password history
- Password complexity
- Password reuse
-
In a lessons learned report, it is suspected that a well-organized, well-funded, and extremely sophisticated group of attackers may have been responsible for a breach at a nuclear facility.
Which of the following describes the type of actors that may have been implicated?
- Nation state
- Hacktivist
- Insider
- Competitor