SY0-501 : CompTIA Security+ Certification : Part 34
SY0-501 : CompTIA Security+ Certification : Part 34
-
A security administrator is analyzing a user report in which the computer exhibits odd network-related outages. The administrator, however, does not see any suspicious processes running. A prior technician’s notes indicate the machine has been remediated twice, but the system still exhibits odd behavior. Files were deleted from the system recently.
Which of the following is the MOST likely cause of this behavior?
- Crypto-malware
- Rootkit
- Logic bomb
- Session hijacking
-
Joe, a member of the sales team, recently logged into the company servers after midnight local time to download the daily lead form before his coworkers did. Management has asked the security team to provide a method for detecting this type of behavior without impeding the access for sales employee as they travel overseas.
Which of the following would be the BEST method to achieve this objective?
- Configure time-of-day restrictions for the sales staff.
- Install DLP software on the devices used by sales employees.
- Implement a filter on the mail gateway that prevents the lead form from being emailed.
- Create an automated alert on the SIEM for anomalous sales team activity.
-
A security administrator wants to implement least privilege access for a network share that stores sensitive company data. The organization is particularly concerned with the integrity of data and implementing discretionary access control. The following controls are available:
– Read = A user can read the content of an existing file.
– Write = A user can modify the content of an existing file and delete an existing file.
– Create = A user can create a new file and place data within the file.A missing control means the user does not have that access. Which of the following configurations provides the appropriate control to support the organization/s requirements?
- Owners: Read, Write, Create
Group Members: Read, Write
Others: Read, Create - Owners: Write, Create
Group Members: Read, Write, Create
Others: Read - Owners: Read, Write
Group Members: Read, Create
Others: Read, Create - Owners: Write, Create
Group Members: Read, Create
Others: Read, Write, Create
- Owners: Read, Write, Create
-
After reports of slow internet connectivity, a technician reviews the following logs from a server’s host-based firewall:
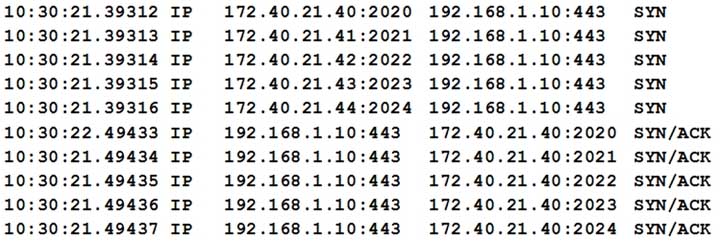
SY0-501 Part 34 Q04 095 Which of the following can the technician conclude after reviewing the above logs?
- The server is under a DDoS attack from multiple geographic locations.
- The server is compromised, and is attacking multiple hosts on the Internet.
- The server is under an IP spoofing resource exhaustion attack.
- The server is unable to complete the TCP three-way handshake and send the last ACK.
-
A company utilizes 802.11 for all client connectivity within a facility. Users in one part of the building are reporting they are unable to access company resources when connected to the company SSID.
Which of the following should the security administrator use to assess connectivity?
- Sniffer
- Honeypot
- Routing tables
- Wireless scanner
-
Which of the following strategies helps reduce risk if a rollback is needed when upgrading a critical system platform?
- Non-persistent configuration
- Continuous monitoring
- Firmware updates
- Fault tolerance
-
A security administrator is creating a risk assessment with regard to how to harden internal communications in transit between servers.
Which of the following should the administrator recommend in the report?
- Configure IPSec in transport mode.
- Configure server-based PKI certificates.
- Configure the GRE tunnel.
- Configure a site-to-site tunnel.
-
A company is executing a strategy to encrypt and sign all proprietary data in transit. The company recently deployed PKI services to support this strategy.
Which of the following protocols supports the strategy and employs certificates generated by the PKI? (Choose three.)
- S/MIME
- TLS
- HTTP-Digest
- SAML
- SIP
- IPSec
- Kerberos
-
A security specialist is notified about a certificate warning that users receive when using a new internal website. After being given the URL from one of the users and seeing the warning, the security specialist inspects the certificate and realizes it has been issued to the IP address, which is how the developers reach the site.
Which of the following would BEST resolve the issue?
- OSCP
- OID
- PEM
- SAN
-
Joe, an employee, asks a coworker how long ago Ann started working at the help desk. The coworker expresses surprise since nobody named Ann works at the help desk. Joe mentions that Ann called several people in the customer service department to help reset their passwords over the phone due to unspecified “server issues”.
Which of the following has occurred?
- Social engineering
- Whaling
- Watering hole attack
- Password cracking
-
Hacktivists are most commonly motivated by:
- curiosity
- notoriety
- financial gain
- political cause
-
A systems administrator is configuring a new network switch for TACACS+ management and authentication.
Which of the following must be configured to provide authentication between the switch and the TACACS+ server?
- 802.1X
- SSH
- Shared secret
- SNMPv3
- CHAP
-
A security analyst monitors the syslog server and notices the following:
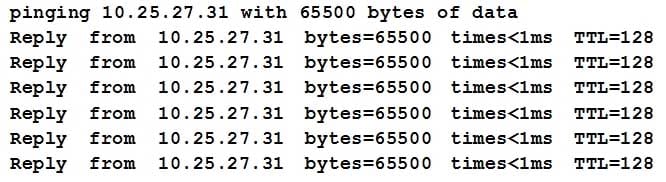
SY0-501 Part 34 Q13 096 - Memory leak
- Buffer overflow
- Null pointer deference
- Integer overflow
-
A security, who is analyzing the security of the company’s web server, receives the following output:
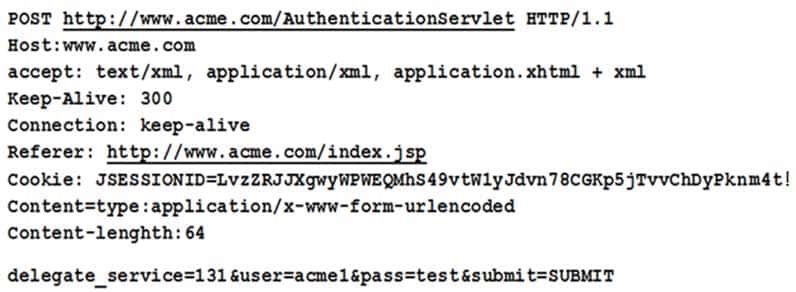
SY0-501 Part 34 Q14 097 Which of the following is the issue?
- Code signing
- Stored procedures
- Access violations
- Unencrypted credentials
-
Which of the following is an example of resource exhaustion?
- A penetration tester requests every available IP address from a DHCP server.
- An SQL injection attack returns confidential data back to the browser.
- Server CPU utilization peaks at 100% during the reboot process.
- System requirements for a new software package recommend having 12GB of RAM, but only 8GB are available.
-
A security consultant is setting up a new electronic messaging platform and wants to ensure the platform supports message integrity validation.
Which of the following protocols should the consultant recommend?
- S/MIME
- DNSSEC
- RADIUS
- 802.11x
-
Datacenter employees have been battling alarms in a datacenter that has been experiencing hotter than normal temperatures. The server racks are designed so all 48 rack units are in use, and servers are installed in any manner in which the technician can get them installed.
Which of the following practices would BEST alleviate the heat issues and keep costs low?
- Utilize exhaust fans.
- Use hot and cold aisles.
- Airgap the racks.
- Use a secondary AC unit.
-
When accessing a popular website, a user receives a warming that the certificate for the website is not valid. Upon investigation, it was noted that the certificate is not revoked and the website is working fine for other users.
Which of the following is the MOST likely cause for this?
- The certificate is corrupted on the server.
- The certificate was deleted from the local cache.
- The user needs to restart the machine.
- The system date on the user’s device is out of sync.
-
A company wishes to move all of its services and applications to a cloud provider but wants to maintain full control of the deployment, access, and provisions of its services to its users.
Which of the following BEST represents the required cloud deployment model?
- SaaS
- IaaS
- MaaS
- Hybrid
- Private
-
A systems administrator has created network file shares for each department with associated security groups for each role within the organization.
Which of the following security concepts is the systems administrator implementing?
- Separation of duties
- Permission auditing
- Least privilege
- Standard naming conversation