SY0-501 : CompTIA Security+ Certification : Part 35
SY0-501 : CompTIA Security+ Certification : Part 35
-
A technician has installed a new AAA server, which will be used by the network team to control access to a company’s routers and switches. The technician completes the configuration by adding the network team members to the NETWORK_TEAM group, and then adding the NETWORK_TEAM group to the appropriate ALLOW_ACCESS access list. Only members of the network team should have access to the company’s routers and switches.
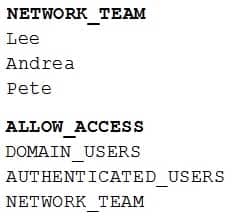
SY0-501 Part 35 Q01 098 Members of the network team successfully test their ability to log on to various network devices configured to use the AAA server. Weeks later, an auditor asks to review the following access log sample:

SY0-501 Part 35 Q01 099 Which of the following should the auditor recommend based on the above information?
- Configure the ALLOW_ACCESS group logic to use AND rather than OR.
- Move the NETWORK_TEAM group to the top of the ALLOW_ACCESS access list.
- Disable groups nesting for the ALLOW_ACCESS group in the AAA server.
- Remove the DOMAIN_USERS group from ALLOW_ACCESS group.
-
A security technician has been given the task of preserving emails that are potentially involved in a dispute between a company and a contractor.
Which of the following BEST describes this forensic concept?
- Legal hold
- Chain of custody
- Order of volatility
- Data acquisition
-
Which of the following outcomes is a result of proper error-handling procedures in secure code?
- Execution continues with no notice or logging of the error condition.
- Minor fault conditions result in the system stopping to preserve state.
- The program runs through to completion with no detectable impact or output.
- All fault conditions are logged and do not result in a program crash.
-
Which of the following enables sniffing attacks against a switched network?
- ARP poisoning
- IGMP snooping
- IP spoofing
- SYN flooding
-
A company wants to ensure users are only logging into the system from their laptops when they are on site. Which of the following would assist with this?
- Geofencing
- Smart cards
- Biometrics
- Tokens
-
During a penetration test, the tester performs a preliminary scan for any responsive hosts. Which of the following BEST explains why the tester is doing this?
- To determine if the network routes are improperly forwarding request packets
- To identify the total number of hosts and determine if the network can be victimized by a DoS attack
- To identify servers for subsequent scans and further investigation
- To identify the unresponsive hosts and determine if those could be used as zombies in a follow-up scan.
-
Which of the following is being used when a malicious actor searches various social media websites to find information about a company’s system administrators and help desk staff?
- Passive reconnaissance
- Initial exploitation
- Vulnerability scanning
- Social engineering
-
Given the following requirements:
– Help to ensure non-repudiation
– Capture motion in various formatsWhich of the following physical controls BEST matches the above descriptions?
- Camera
- Mantrap
- Security guard
- Motion sensor
-
Which of the following is a random value appended to a credential that makes the credential less susceptible to compromise when hashed?
- Nonce
- Salt
- OTP
- Block cipher
- IV
-
An organization has hired a new remote workforce. Many new employees are reporting that they are unable to access the shared network resources while traveling. They need to be able to travel to and from different locations on a weekly basis. Shared offices are retained at the headquarters location. The remote workforce will have identical file and system access requirements, and must also be able to log in to the headquarters location remotely. Which of the following BEST represent how the remote employees should have been set up initially? (Choose two.)
- User-based access control
- Shared accounts
- Group-based access control
- Mapped drives
- Individual accounts
- Location-based policies
-
A salesperson often uses a USB drive to save and move files from a corporate laptop. The coprorate laptop was recently updated, and now the files on the USB are read-only. Which of the following was recently added to the laptop?
- Antivirus software
- File integrity check
- HIPS
- DLP
-
A network technician is setting up a new branch for a company. The users at the new branch will need to access resources securely as if they were at the main location. Which of the following networking concepts would BEST accomplish this?
- Virtual network segmentation
- Physical network segmentation
- Site-to-site VPN
- Out-of-band access
- Logical VLANs
-
A water utility company has seen a dramatic increase in the number of water pumps burning out. A malicious actor was attacking the company and is responsible for the increase. Which of the following systems has the attacker compromised?
- DMZ
- RTOS
- SCADA
- IoT
-
An organization’s Chief Executive Officer (CEO) directs a newly hired computer technician to install an OS on the CEO’s personal laptop. The technician performs the installation, and a software audit later in the month indicates a violation of the EULA occurred as a result. Which of the following would address this violation going forward?
- Security configuration baseline
- Separation of duties
- AUP
- NDA
-
Which of the following attackers generally possesses minimal technical knowledge to perform advanced attacks and uses widely available tools as well as publicly available information?
- Hacktivist
- White hat hacker
- Script kiddle
- Penetration tester
-
A company is performing an analysis of which corporate units are most likely to cause revenue loss in the event the unit is unable to operate. Which of the following is an element of the BIA that this action is addressing?
- Critical system inventory
- Single point of failure
- Continuity of operations
- Mission-essential functions
-
A company has critical systems that are hosted on an end-of-life OS. To maintain operations and mitigate potential vulnerabilities, which of the following BEST accomplishes this objective?
- Use application whitelisting.
- Employ patch management.
- Disable the default administrator account.
- Implement full-disk encryption.
-
Which of the following terms BEST describes an exploitable vulnerability that exists but has not been publicly disclosed yet?
- Design weakness
- Zero-day
- Logic bomb
- Trojan
-
A company’s IT staff is given the task of securely disposing of 100 server HDDs. The security team informs the IT staff that the data must not be accessible by a third party after disposal. Which of the following is the MOST time-efficient method to achieve this goal?
- Use a degausser to sanitize the drives.
- Remove the platters from the HDDs and shred them.
- Perform a quick format of the HDD drives.
- Use software to zero fill all of the hard drives.
-
A company has migrated to two-factor authentication for accessing the corporate network, VPN, and SSO. Several legacy applications cannot support multifactor authentication and must continue to use usernames and passwords. Which of the following should be implemented to ensure the legacy applications are as secure as possible while ensuring functionality? (Choose two.)
- Privileged accounts
- Password reuse restrictions
- Password complexity requirements
- Password recovery
- Account disablement