SY0-501 : CompTIA Security+ Certification : Part 36
SY0-501 : CompTIA Security+ Certification : Part 36
-
Two companies are enabling TLS on their respective email gateways to secure communications over the Internet. Which of the following cryptography concepts is being implemented?
- Perfect forward secrecy
- Ephemeral keys
- Domain validation
- Data in transit
-
The Chief Executive Officer (CEO) received an email from the Chief Financial Officer (CFO), asking the CEO to send financial details. The CEO thought it was strange that the CFO would ask for the financial details via email. The email address was correct in the “From” section of the email. The CEO clicked the form and sent the financial information as requested. Which of the following caused the incident?
- Domain hijacking
- SPF not enabled
- MX records rerouted
- Malicious insider
-
Which of the following control types would a backup of server data provide in case of a system issue?
- Corrective
- Deterrent
- Preventive
- Detective
-
A recent penetration test revealed several issues with a public-facing website used by customers. The testers were able to:
– Enter long lines of code and special characters
– Crash the system
– Gain unauthorized access to the internal application server
– Map the internal networkThe development team has stated they will need to rewrite a significant portion of the code used, and it will take more than a year to deliver the finished product. Which of the following would be the BEST solution to introduce in the interim?
- Content fileting
- WAF
- TLS
- IPS/IDS
- UTM
-
Which of the following can occur when a scanning tool cannot authenticate to a server and has to rely on limited information obtained from service banners?
- False positive
- Passive reconnaissance
- Access violation
- Privilege escalation
-
A systems administrator needs to integrate multiple IoT and small embedded devices into the company’s wireless network securely. Which of the following should the administrator implement to ensure low-power and legacy devices can connect to the wireless network?
- WPS
- WPA
- EAP-FAST
- 802.1X
-
When backing up a database server to LTO tape drives, the following backup schedule is used. Backups take one hour to complete:
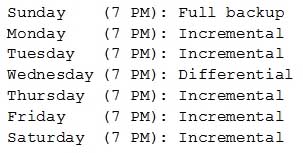
SY0-501 Part 36 Q07 100 On Friday at 9:00 p.m., there is a RAID failure on the database server. The data must be restored from backup. Which of the following is the number of backup tapes that will be needed to complete this operation?
- 1
- 2
- 3
- 4
- 6
-
Management wants to ensure any sensitive data on company-provided cell phones is isolated in a single location that can be remotely wiped if the phone is lost. Which of the following technologies BEST meets this need?
- Geofencing
- Containerization
- Device encryption
- Sandboxing
-
A company is planning to utilize its legacy desktop systems by converting them into dummy terminals and moving all heavy applications and storage to a centralized server that hosts all of the company’s required desktop applications. Which of the following describes the BEST deployment method to meet these requirements?
- IaaS
- VM sprawl
- VDI
- PaaS
-
Joe, a user, reports to the help desk that he can no longer access any documents on his PC. He states that he saw a window appear on the screen earlier, but he closed it without reading it. Upon investigation, the technician sees high disk activity on Joe’s PC. Which of the following types of malware is MOST likely indicated by these findings?
- Keylogger
- Trojan
- Rootkit
- Crypto-malware
-
An administrator is implementing a secure web server and wants to ensure that if the web server application is compromised, the application does not have access to other parts of the server or network. Which of the following should the administrator implement? (Choose two.)
- Mandatory access control
- Discretionary access control
- Rule-based access control
- Role-based access control
- Attribute-based access control
-
A developer has incorporated routines into the source code for controlling the length of the input passed to the program. Which of the following types of vulnerabilities is the developer protecting the code against?
- DLL injection
- Memory leak
- Buffer overflow
- Pointer dereference
-
An application developer has neglected to include input validation checks in the design of the company’s new web application. An employee discovers that repeatedly submitting large amounts of data, including custom code, to an application will allow the execution of the custom code at the administrator level. Which of the following BEST identifies this application attack?
- Cross-site scripting
- Clickjacking
- Buffer overflow
- Replay
-
Which of the following identity access methods creates a cookie on the first login to a central authority to allow logins to subsequent applications without re-entering credentials?
- Multifactor authentication
- Transitive trust
- Federated access
- Single sign-on
-
A network technician is designing a network for a small company. The network technician needs to implement an email server and web server that will be accessed by both internal employees and external customers. Which of the following would BEST secure the internal network and allow access to the needed servers?
- Implementing a site-to-site VPN for server access.
- Implementing a DMZ segment for the server.
- Implementing NAT addressing for the servers.
- Implementing a sandbox to contain the servers.
-
When used together, which of the following qualify as two-factor authentication?
- Password and PIN
- Smart card and PIN
- Proximity card and smart card
- Fingerprint scanner and iris scanner
-
Ann, a new employee, received an email from an unknown source indicating she needed to click on the provided link to update her company’s profile. Once Ann clicked the link, a command prompt appeared with the following output:
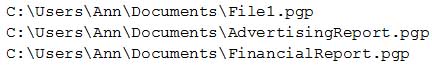
SY0-501 Part 36 Q17 101 Which of the following types of malware was executed?
- Ransomware
- Adware
- Spyware
- Virus
-
A company has a team of penetration testers. This team has located a file on the company file server that they believe contains cleartext usernames followed by a hash. Which of the following tools should the penetration testers use to learn more about the content of this file?
- Exploitation framework
- Vulnerability scanner
- Netcat
- Password cracker
-
The Chief Information Security Officer (CISO) in a company is working to maximize protection efforts of sensitive corporate data. The CISO implements a “100% shred” policy within the organization, with the intent to destroy any documentation that is not actively in use in a way that it cannot be recovered or reassembled. Which of the following attacks is this deterrent MOST likely to mitigate?
- Dumpster diving
- Whaling
- Shoulder surfing
- Vishing
-
A Chief Information Security Officer (CISO) has instructed the information assurance staff to act upon a fast-spreading virus.
Which of the following steps in the incident response process should be taken NEXT?
- Identification
- Eradication
- Escalation
- Containment