SY0-501 : CompTIA Security+ Certification : Part 37
SY0-501 : CompTIA Security+ Certification : Part 37
-
An organization has air gapped a critical system.
Which of the following BEST describes the type of attacks that are prevented by this security measure?
- Attacks from another local network segment
- Attacks exploiting USB drives and removable media
- Attacks that spy on leaked emanations or signals
- Attacks that involve physical intrusion or theft
-
An organization wants to ensure network access is granted only after a user or device has been authenticated.
Which of the following should be used to achieve this objective for both wired and wireless networks?
- CCMP
- PKCS#12
- IEEE 802.1X
- OCSP
-
A security administrator is choosing an algorithm to generate password hashes.
Which of the following would offer the BEST protection against offline brute force attacks?
- MD5
- 3DES
- AES
- SHA-1
-
A security administrator is investigating many recent incidents of credential theft for users accessing the company’s website, despite the hosting web server requiring HTTPS for access. The server’s logs show the website leverages the HTTP POST method for carrying user authentication details.
Which of the following is the MOST likely reason for compromise?
- The HTTP POST method is not protected by HTTPS.
- The web server is running a vulnerable SSL configuration.
- The HTTP response is susceptible to sniffing.
- The company doesn’t support DNSSEC.
-
A user from the financial aid office is having trouble interacting with the finaid directory on the university’s ERP system. The systems administrator who took the call ran a command and received the following output:
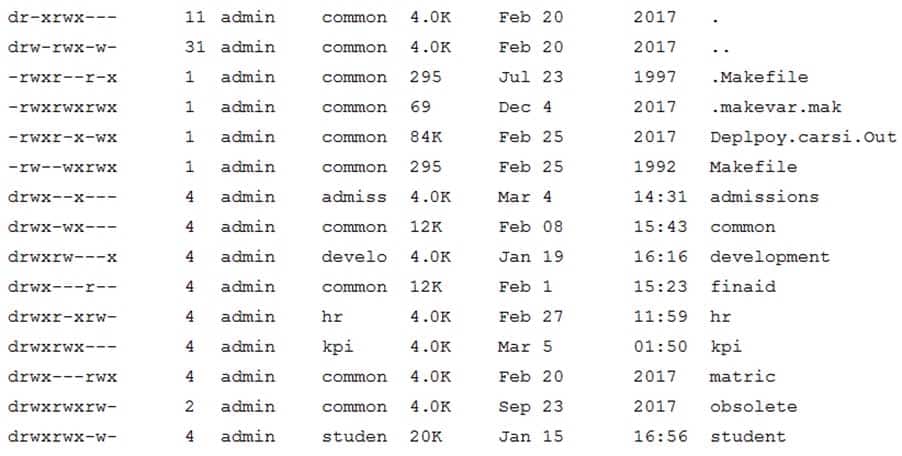
SY0-501 Part 37 Q05 102 Subsequently, the systems administrator has also confirmed the user is a member of the finaid group on the ERP system.
Which of the following is the MOST likely reason for the issue?
- The permissions on the finaid directory should be drwxrwxrwx.
- The problem is local to the user, and the user should reboot the machine.
- The permissions on the finaid directory should be d—rwx—.
- The finaid directory has an improper group assignment.
-
An organization wants to deliver streaming audio and video from its home office to remote locations all over the world. It wants the stream to be delivered securely and protected from intercept and replay attacks.
Which of the following protocols is BEST suited for this purpose?
- SSH
- SIP
- S/MIME
- SRTP
-
A manager makes an unannounced visit to the marketing department and performs a walk-through of the office. The manager observes unclaimed documents on printers. A closer look at these documents reveals employee names, addresses, ages, birth dates, marital/dependent statuses, and favorite ice cream flavors. The manager brings this to the attention of the marketing department head. The manager believes this information to be PII, but the marketing head does not agree. Having reached a stalemate, which of the following is the MOST appropriate action to take NEXT?
- Elevate to the Chief Executive Officer (CEO) for redress; change from the top down usually succeeds.
- Find the privacy officer in the organization and let the officer act as the arbiter.
- Notify employees whose names are on these files that their personal information is being compromised.
- To maintain a working relationship with marketing, quietly record the incident in the risk register.
-
A security administrator is implementing a secure method that allows developers to place files or objects onto a Linux server. Developers are required to log in using a username, password, and asymmetric key.
Which of the following protocols should be implemented?
- SSL/TLS
- SFTP
- SRTP
- IPSec
-
Which of the following BEST describes the purpose of authorization?
- Authorization provides logging to a resource and comes after authentication.
- Authorization provides authentication to a resource and comes after identification.
- Authorization provides identification to a resource and comes after authentication.
- Authorization provides permissions to a resource and comes after authentication.
-
A security analyst is emailing PII in a spreadsheet file to an audit validator for after-actions related to a security assessment. The analyst must make sure the PII data is protected with the following minimum requirements:
– Ensure confidentiality at rest.
– Ensure the integrity of the original email message.Which of the following controls would ensure these data security requirements are carried out?
- Encrypt and sign the email using S/MIME.
- Encrypt the email and send it using TLS.
- Hash the email using SHA-1.
- Sign the email using MD5.
-
The network information for a workstation is as follows:
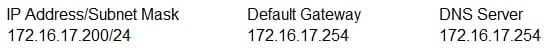
SY0-501 Part 37 Q11 103 When the workstation’s user attempts to access www.example.com, the URL that actually opens is www.notexample.com. The user successfully connects to several other legitimate URLs. Which of the following have MOST likely occurred? (Choose two.)
- ARP poisoning
- Buffer overflow
- DNS poisoning
- Domain hijacking
- IP spoofing
-
Which of the following implements a stream cipher?
- File-level encryption
- IKEv2 exchange
- SFTP data transfer
- S/MIME encryption
-
A security technician has been assigned data destruction duties. The hard drives that are being disposed of contain highly sensitive information. Which of the following data destruction techniques is MOST appropriate?
- Degaussing
- Purging
- Wiping
- Shredding
-
Which of the following BEST explains how the use of configuration templates reduces organization risk?
- It ensures consistency of configuration for initial system implementation.
- It enables system rollback to a last known-good state if patches break functionality.
- It facilitates fault tolerance since applications can be migrated across templates.
- It improves vulnerability scanning efficiency across multiple systems.
-
A Chief Information Security Officer (CISO) is performing a BIA for the organization in case of a natural disaster. Which of the following should be at the top of the CISO’s list?
- Identify redundant and high-availability systems.
- Identity mission-critical applications and systems.
- Identify the single point of failure in the system.
- Identity the impact on safety of the property.
-
Which of the following should a technician use to protect a cellular phone that is needed for an investigation, to ensure the data will not be removed remotely?
- Air gap
- Secure cabinet
- Faraday cage
- Safe
-
Which of the following is the MOST significant difference between intrusive and non-intrusive vulnerability scanning?
- One uses credentials, but the other does not.
- One has a higher potential for disrupting system operations.
- One allows systems to activate firewall countermeasures.
- One returns service banners, including running versions.
-
While reviewing system logs, a security analyst notices that a large number of end users are changing their passwords four times on the day the passwords are set to expire. The analyst suspects they are cycling their passwords to circumvent current password controls. Which of the following would provide a technical control to prevent this activity from occurring?
- Set password aging requirements.
- Increase the password history from three to five.
- Create an AUP that prohibits password reuse.
- Implement password complexity requirements.
-
A security analyst is running a credential-based vulnerability scanner on a Windows host. The vulnerability scanner is using the protocol NetBIOS over TCP/IP to connect to various systems, However, the scan does not return any results. To address the issue, the analyst should ensure that which of the following default ports is open on systems?
- 135
- 137
- 3389
- 5060
-
An organization’s research department uses workstations in an air-gapped network. A competitor released products based on files that originated in the research department. Which of the following should management do to improve the security and confidentiality of the research files?
- Implement multifactor authentication on the workstations.
- Configure removable media controls on the workstations.
- Install a web application firewall in the research department.
- Install HIDS on each of the research workstations.