SY0-501 : CompTIA Security+ Certification : Part 41
SY0-501 : CompTIA Security+ Certification : Part 41
-
A first responder needs to collect digital evidence from a compromised headless virtual host. Which of the following should the first responder collect FIRST?
- Virtual memory
- BIOS configuration
- Snapshot
- RAM
-
Which of the following BEST explains the difference between a credentialed scan and a non-credentialed scan?
- A credentialed scan sees devices in the network, including those behind NAT, while a non-credentialed scan sees outward-facing applications.
- A credentialed scan will not show up in system logs because the scan is running with the necessary authorization, while non-credentialed scan activity will appear in the logs.
- A credentialed scan generates significantly more false positives, while a non-credentialed scan generates fewer false positives.
- A credentialed scan sees the system the way an authorized user sees the system, while a non-credentialed scan sees the system as a guest.
-
Using a one-time code that has been texted to a smartphone is an example of:
- something you have.
- something you know.
- something you do.
- something you are.
-
The exploitation of a buffer-overrun vulnerability in an application will MOST likely lead to:
- arbitrary code execution.
- resource exhaustion.
- exposure of authentication credentials.
- dereferencing of memory pointers.
-
A security professional wants to test a piece of malware that was isolated on a user’s computer to document its effect on a system. Which of the following is the FIRST step the security professional should take?
- Create a sandbox on the machine.
- Open the file and run it.
- Create a secure baseline of the system state.
- Harden the machine.
-
In highly secure environments where the risk of malicious actors attempting to steal data is high, which of the following is the BEST reason to deploy Faraday cages?
- To provide emanation control to prevent credential harvesting
- To minimize signal attenuation over distances to maximize signal strength
- To minimize external RF interference with embedded processors
- To protect the integrity of audit logs from malicious alteration
-
Which of the following is the proper use of a Faraday cage?
- To block electronic signals sent to erase a cell phone
- To capture packets sent to a honeypot during an attack
- To protect hard disks from access during a forensics investigation
- To restrict access to a building allowing only one person to enter at a time
-
A security administrator found the following piece of code referenced on a domain controller’s task scheduler:
$var = GetDomainAdmins If $var != ‘fabio’ SetDomainAdmins = NULL
With which of the following types of malware is the code associated?
- RAT
- Backdoor
- Logic bomb
- Crypto-malware
-
An email recipient is unable to open a message encrypted through PKI that was sent from another organization. Which of the following does the recipient need to decrypt the message?
- The sender’s private key
- The recipient’s private key
- The recipient’s public key
- The CA’s root certificate
- The sender’s public key
- An updated CRL
-
An employee opens a web browser and types a URL into the address bar. Instead of reaching the requested site, the browser opens a completely different site. Which of the following types of attacks have MOST likely occurred? (Choose two.)
- DNS hijacking
- Cross-site scripting
- Domain hijacking
- Man-in-the-browser
- Session hijacking
-
DRAG DROP
An attack has occurred against a company.
INSTRUCTIONS
You have been tasked to do the following:
Identify the type of attack that is occurring on the network by clicking on the attacker’s tablet and reviewing the output. (Answer Area 1)
Identify which compensating controls should be implemented on the assets, in order to reduce the effectiveness of future attacks by dragging them to the correct server. (Answer area 2)
All objects will be used, but not all placeholders may be filled. Objects may only be used once.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

SY0-501 Part 41 Q11 105 
SY0-501 Part 41 Q11 106 
SY0-501 Part 41 Q11 107 Question 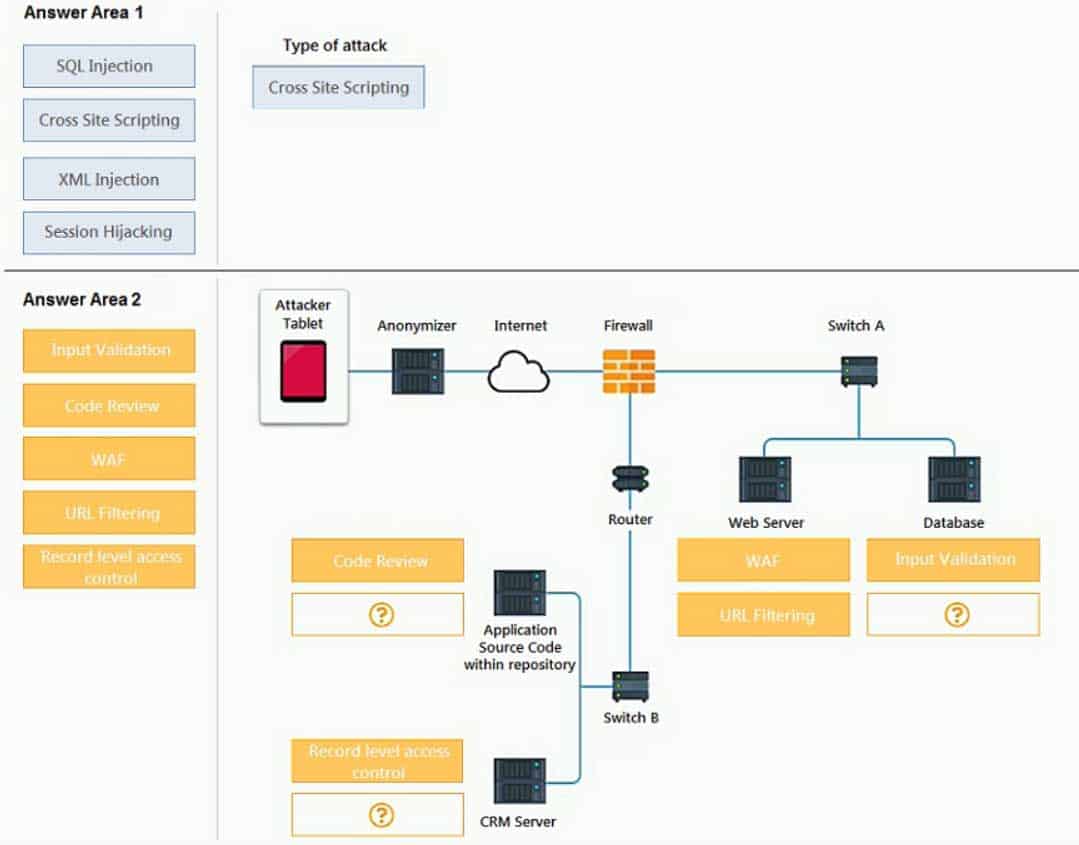
SY0-501 Part 41 Q11 107 Answer -
A security administrator has received multiple calls from the help desk about customers who are unable to access the organization’s web server. Upon reviewing the log files, the security administrator determines multiple open requests have been made from multiple IP addresses, which is consuming system resources. Which of the following attack types does this BEST describe?
- DDoS
- DoS
- Zero day
- Logic bomb
-
A coding error has been discovered on a customer-facing website. The error causes each request to return confidential PHI data for the incorrect organization. The IT department is unable to identify the specific customers who are affected. As a result, all customers must be notified of the potential breach. Which of the following would allow the team to determine the scope of future incidents?
- Intrusion detection system
- Database access monitoring
- Application fuzzing
- Monthly vulnerability scans
-
A systems engineer wants to leverage a cloud-based architecture with low latency between network-connected devices that also reduces the bandwidth that is required by performing analytics directly on the endpoints. Which of the following would BEST meet the requirements? (Choose two.)
- Private cloud
- SaaS
- Hybrid cloud
- IaaS
- DRaaS
- Fog computing
-
A systems engineer is setting up a RADIUS server to support a wireless network that uses certificate authentication. Which of the following protocols must be supported by both the RADIUS server and the WAPs?
- CCMP
- TKIP
- WPS
- EAP
-
A small retail business has a local store and a newly established and growing online storefront. A recent storm caused a power outage to the business and the local ISP, resulting in several hours of lost sales and delayed order processing. The business owner now needs to ensure two things:
– Protection from power outages
– Always-available connectivity in case of an outageThe owner has decided to implement battery backups for the computer equipment. Which of the following would BEST fulfill the owner’s second need?
- Lease a telecommunications line to provide POTS for dial-up access.
- Connect the business router to its own dedicated UPS.
- Purchase services from a cloud provider for high availability.
- Replace the business’s wired network with a wireless network.
-
A systems engineer is configuring a wireless network. The network must not require installation of third-party software. Mutual authentication of the client and the server must be used. The company has an internal PKI. Which of the following configurations should the engineer choose?
- EAP-TLS
- EAP-TTLS
- EAP-FAST
- EAP-MD5
- PEAP
-
A security operations team recently detected a breach of credentials. The team mitigated the risk and followed proper processes to reduce risk. Which of the following processes would BEST help prevent this issue from happening again?
- Risk assessment
- Chain of custody
- Lessons learned
- Penetration test
-
An organization plans to transition the intrusion detection and prevention techniques on a critical subnet to an anomaly-based system. Which of the following does the organization need to determine for this to be successful?
- The baseline
- The endpoint configurations
- The adversary behavior profiles
- The IPS signatures
-
Joe, an employee, knows he is going to be fired in three days. Which of the following is Joe?
- An insider threat
- A competitor
- A hacktivist
- A state actor