SY0-501 : CompTIA Security+ Certification : Part 45
SY0-501 : CompTIA Security+ Certification : Part 45
-
During an incident, a company’s CIRT determines it is necessary to observe the continued network-based transactions between a callback domain and the malware running on an enterprise PC. Which of the following techniques would be BEST to enable this activity while reducing the risk of lateral spread and the risk that the adversary would notice any changes?
- Physically move the PC to a separate Internet point of presence.
- Create and apply microsegmentation rules.
- Emulate the malware in a heavily monitored DMZ segment.
- Apply network blacklisting rules for the adversary domain.
-
An organization has a policy in place that states the person who approves firewall controls/changes cannot be the one implementing the changes. Which of the following is this an example of?
- Change management
- Job rotation
- Separation of duties
- Least privilege
-
An organization just experienced a major cyberattack incident. The attack was well coordinated, sophisticated, and highly skilled. Which of the following targeted the organization?
- Shadow IT
- An insider threat
- A hacktivist
- An advanced persistent threat
-
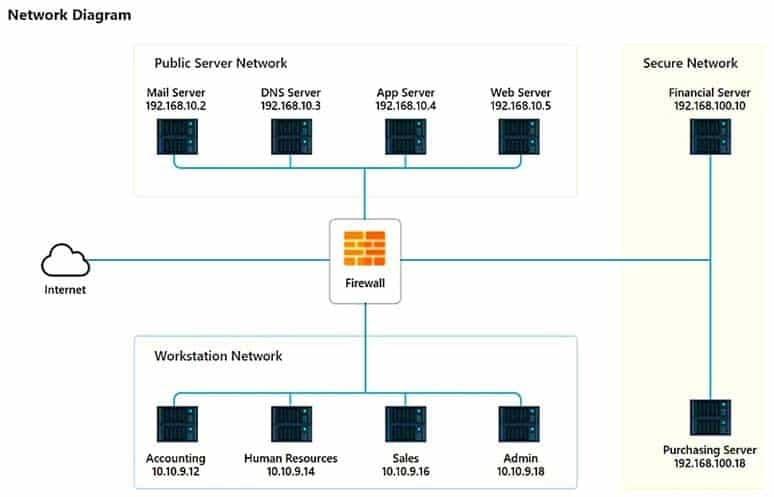
HOTSPOT
The security administration has installed a new firewall which implements an implicit DENY policy by default.
INSTRUCTIONS
Click on the firewall and configure it to allow ONLY the following communication:
– The Accounting workstation can ONLY access the web server on the public network over the default HTTPS port. The accounting workstation should not access other networks.
– The HR workstation should be restricted to communicate with the Financial server ONLY, over the default SCP port.
– The Admin workstation should ONLY be able to access the server on the secure network over the default TFTP port.The firewall will process the rules in a top-down manner in order as a first match. The port number must be typed in and only one port number can be entered per rule. Type ANY for all ports.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
SY0-501 Part 45 Q04 110 
SY0-501 Part 45 Q04 111 Question 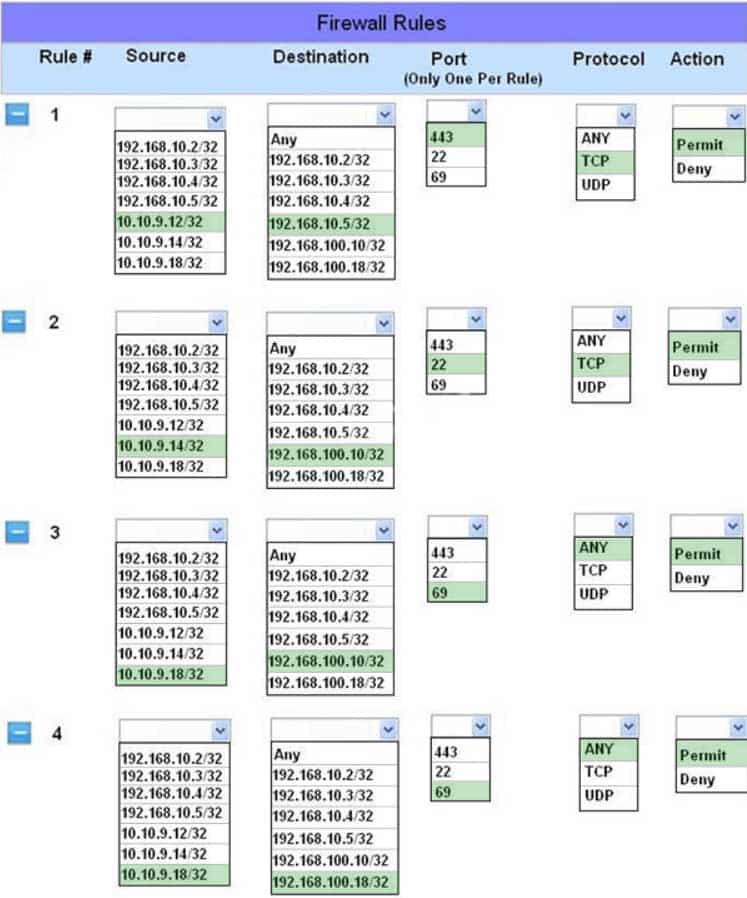
SY0-501 Part 45 Q04 111 Answer -
An organization has decided to host its web application and database in the cloud. Which of the following BEST describes the security concerns for this decision?
- Access to the organization’s servers could be exposed to other cloud-provider clients.
- The cloud vendor is a new attack vector within the supply chain.
- Outsourcing the code development adds risk to the cloud provider.
- Vendor support will cease when the hosting platforms reach EOL.
-
Which of the following describes the ability of code to target a hypervisor from inside a guest OS?
- Fog computing
- VM escape
- Software-defined networking
- Image forgery
- Container breakout
-
An auditor is performing an assessment of a security appliance with an embedded OS that was vulnerable during the last two assessments. Which of the following BEST explains the appliance’s vulnerable state?
- The system was configured with weak default security settings.
- The device uses weak encryption ciphers.
- The vendor has not supplied a patch for the appliance.
- The appliance requires administrative credentials for the assessment.
-
Which of the following BEST describes a security exploit for which a vendor patch is not readily available?
- Integer overflow
- Zero-day
- End of life
- Race condition
-
A systems administrator needs to install the same X.509 certificate on multiple servers. Which of the following should the administrator use?
- Key escrow
- A self-signed certificate
- Certificate chaining
- An extended validation certificate
-
A network administrator has been alerted that web pages are experiencing long load times. After determining it is not a routing or DNS issue, the administrator logs in to the router, runs a command, and receives the following output:

SY0-501 Part 45 Q10 112 Which of the following is the router experiencing?
- DDoS attack
- Memory leak
- Buffer overflow
- Resource exhaustion
-
The Chief Executive Officer (CEO) of an organization would like staff members to have the flexibility to work from home anytime during business hours, including during a pandemic or crisis. However, the CEO is concerned that some staff members may take advantage of the flexibility and work from high-risk countries while on holiday or outsource work to a third-party organization in another country. The Chief Information Officer (CIO) believes the company can implement some basic controls to mitigate the majority of the risk. Which of the following would be BEST to mitigate the CEO’s concerns? (Choose two.)
- Geolocation
- Time-of-day restrictions
- Certificates
- Tokens
- Geotagging
- Role-based access controls
-
Which of the following scenarios would make a DNS sinkhole effective in thwarting an attack?
- An attacker is sniffing traffic to port 53, and the server is managed using unencrypted usernames and passwords.
- An organization is experiencing excessive traffic on port 53 and suspects an attacker is trying to DoS the domain name server.
- Malware is trying to resolve an unregistered domain name to determine if it is running in an isolated sandbox.
- DNS routing tables have been compromised, and an attacker is rerouting traffic to malicious websites.
-
While reviewing the wireless router, the systems administrator of a small business determines someone is spoofing the MAC address of an authorized device. Given the table below:

SY0-501 Part 45 Q13 113 Which of the following should be the administrator’s NEXT step to detect if there is a rogue system without impacting availability?
- Conduct a ping sweep.
- Physically check each system.
- Deny Internet access to the “UNKNOWN” hostname.
- Apply MAC filtering.
-
A university is opening a facility in a location where there is an elevated risk of theft. The university wants to protect the desktops in its classrooms and labs. Which of the following should the university use to BEST protect these assets deployed in the facility?
- Visitor logs
- Cable locks
- Guards
- Disk encryption
- Motion detection
-
Which of the following is the primary reason for implementing layered security measures in a cybersecurity architecture?
- It increases the number of controls required to subvert a system
- It decreases the time a CERT has to respond to a security incident.
- It alleviates problems associated with EOL equipment replacement.
- It allows for bandwidth upgrades to be made without user disruption.
-
Which of the following attacks can be used to exploit a vulnerability that was created by untrained users?
- A spear-phishing email with a file attachment.
- A DoS using IoT devices
- An evil twin wireless access point
- A domain hijacking of a bank website
-
A company uses an enterprise desktop imaging solution to manage deployment of its desktop computers. Desktop computer users are only permitted to use software that is part of the baseline image. Which of the following technical solutions was MOST likely deployed by the company to ensure only known-good software can be installed on corporate desktops?
- Network access control
- Configuration manager
- Application whitelisting
- File integrity checks
-
A company recently experienced a security incident in which its domain controllers were the target of a DoS attack. In which of the following steps should technicians connect domain controllers to the network and begin authenticating users again?
- Preparation
- Identification
- Containment
- Eradication
- Recovery
- Lessons learned
-
Which of the following explains why a vulnerability scan might return a false positive?
- The scan is performed at a time of day when the vulnerability does not exist.
- The test is performed against the wrong host.
- The signature matches the product but not the version information.
- The hosts are evaluated based on an OS-specific profile.
-
An organization has implemented a two-step verification process to protect user access to data that is stored in the cloud. Each employee now uses an email address or mobile number to receive a code to access the data. Which of the following authentication methods did the organization implement?
- Token key
- Static code
- Push notification
- HOTP