SY0-501 : CompTIA Security+ Certification : Part 47
SY0-501 : CompTIA Security+ Certification : Part 47
-
A junior systems administrator noticed that one of two hard drives in a server room had a red error notification. The administrator removed the hard drive to replace it but was unaware that the server was configured in an array. Which of the following configurations would ensure no data is lost?
- RAID 0
- RAID 1
- RAID 2
- RAID 3
-
Joe, a user at a company, clicked an email link that led to a website that infected his workstation. Joe was connected to the network, and the virus spread to the network shares. The protective measures failed to stop this virus, and it has continued to evade detection. Which of the following should a security administrator implement to protect the environment from this malware?
- Install a definition-based antivirus.
- Implement an IDS/IPS.
- Implement a heuristic behavior-detection solution.
- Implement CASB to protect the network shares.
-
A systems administrator wants to implement a secure wireless network requiring wireless clients to pre-register with the company and install a PKI client certificate prior to being able to connect to the wireless network. Which of the following should the systems administrator configure?
- EAP-TTLS
- EAP-TLS
- EAP-FAST
- EAP with PEAP
- EAP with MSCHAPv2
-
A systems administrator wants to replace the process of using a CRL to verify certificate validity. Frequent downloads are becoming problematic. Which of the following would BEST suit the administrator’s needs?
- OCSP
- CSR
- Key escrow
- CA
-
Which of the following attacks can be mitigated by proper data retention policies?
- Dumpster diving
- Man-in-the-browser
- Spear phishing
- Watering hole
-
SIMULATION
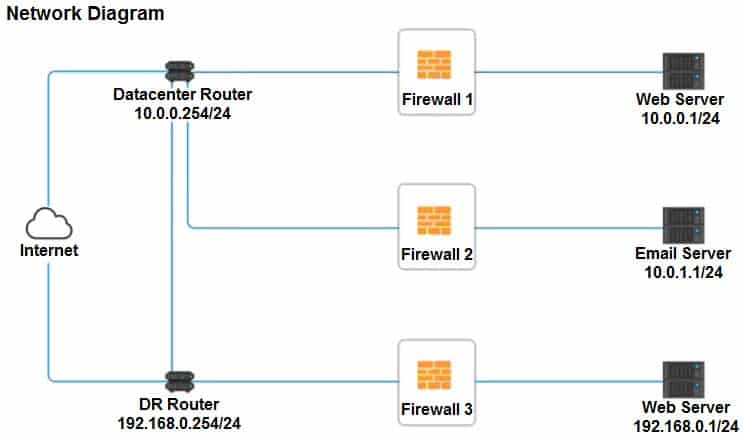
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites.
INSTRUCTIONS
Click on each firewall to do the following:
1. Deny cleartext web traffic.
2. Ensure secure management protocols are used.
3. Resolve issues at the DR site.The ruleset order cannot be modified due to outside constraints.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
SY0-501 Part 47 Q06 117 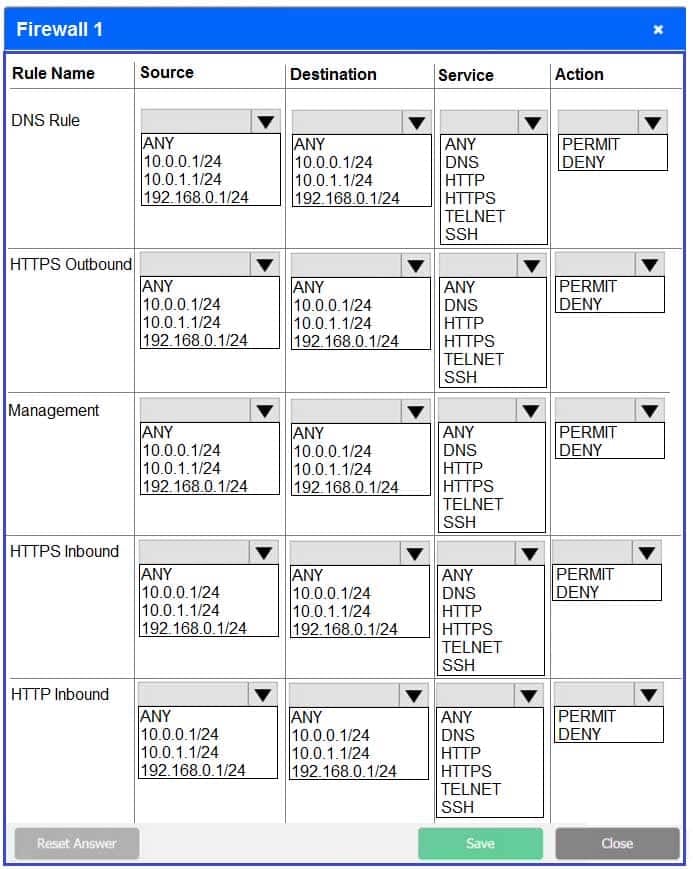
SY0-501 Part 47 Q06 118 
SY0-501 Part 47 Q06 119 
SY0-501 Part 47 Q06 120 - For correct answers: see the explanation below
Explanation:
Firewall 1:
DNS Rule – ANY ANY DNS PERMIT
HTTPS Outbound – 10.0.0.1/24 ANY HTTPS PERMIT
Management – ANY ANY SSH PERMIT
HTTPS Inbound – ANY ANY HTTPS PERMIT
HTTP Inbound – ANY ANY HTTP DENYFirewall 2: No changes should be made to this firewall
Firewall 3:
DNS Rule – ANY ANY DNS PERMIT
HTTPS Outbound – 192.168.0.1/24 ANY HTTPS PERMIT
Management – ANY ANY SSH PERMIT
HTTPS Inbound – ANY ANY HTTPS PERMIT
HTTP Inbound – ANY ANY HTTP DENY -
DRAG DROP
A security engineer is setting up password less authentication for the first time.
INSTRUCTIONS
Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
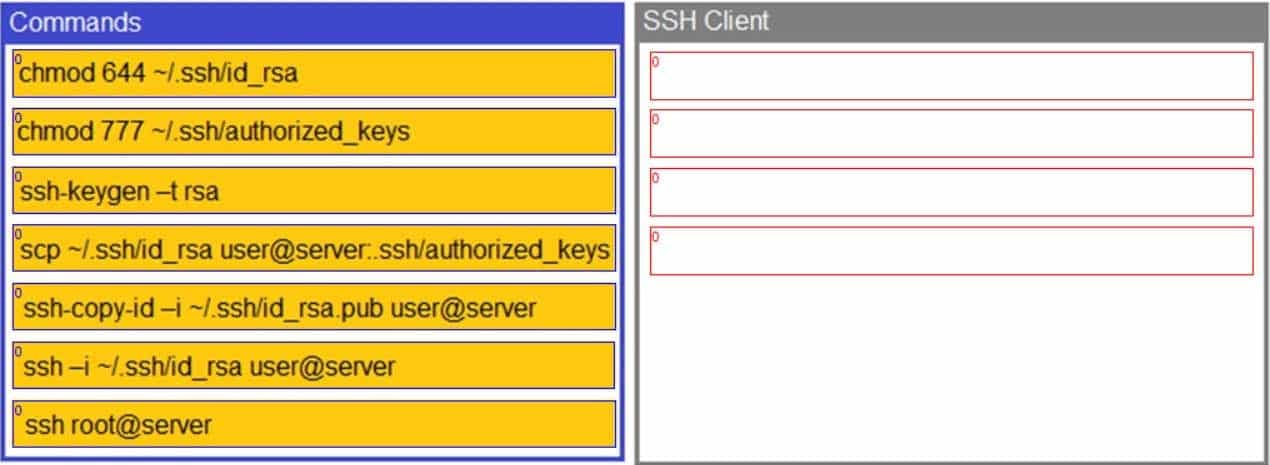
SY0-501 Part 47 Q07 121 Question 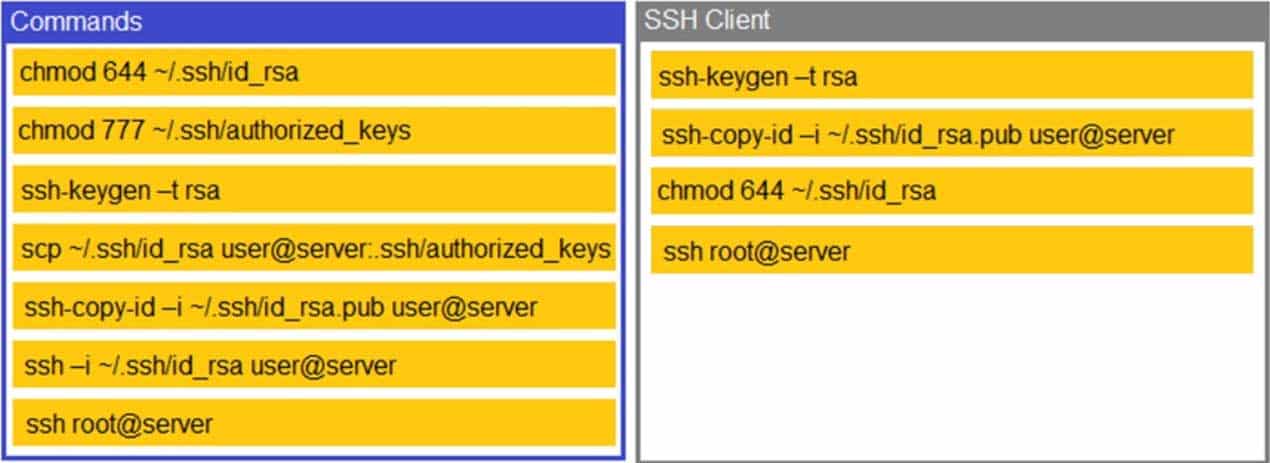
SY0-501 Part 47 Q07 121 Answer -
A security analyst discovers that a company’s username and password database was posted on an Internet forum. The username and passwords are stored in plain text. Which of the following would mitigate the damage done by this type of data exfiltration in the future?
- Create DLP controls that prevent documents from leaving the network
- Implement salting and hashing.
- Configure the web content filter to block access to the forum.
- Increase password complexity requirements.
-
While checking logs, a security engineer notices a number of end users suddenly downloading files with the .tar.gz extension. Closer examination of the files reveals they are PE32 files. The end users state they did not initiate any of the downloads. Further investigation reveals the end users all clicked on an external email containing an infected MHT file with an href link a week prior. Which of the following is MOST likely occurring?
- A RAT was installed and is transferring additional exploit tools.
- The workstations are beaconing to a command-and-control server.
- A logic bomb was executed and is responsible for the data transfers.
- A fireless virus is spreading in the local network environment.
-
A consultant is configuring a vulnerability scanner for a large, global organization in multiple countries. The consultant will be using a service account to scan systems with administrative privileges on a weekly basis, but there is a concern that hackers could gain access to the account and pivot throughout the global network. Which of the following would be BEST to help mitigate this concern?
- Create different accounts for each region, each configured with push MFA notifications.
- Create one global administrator account and enforce Kerberos authentication.
- Create different accounts for each region, limit their logon times, and alert on risky logins.
- Create a guest account for each region, remember the last ten passwords, and block password reuse.
-
The IT department’s on-site developer has been with the team for many years. Each time an application is released, the security team is able to identify multiple vulnerabilities. Which of the following would BEST help the team ensure the application is ready to be released to production?
- Limit the use of third-party libraries.
- Prevent data exposure queries.
- Obfuscate the source code.
- Submit the application to QA before releasing it.
-
In a lessons-learned report, it is suspected that a well-organized, well-funded, and extremely sophisticated group of attackers may have been responsible for a breach at a nuclear facility. Which of the following describes the type of actors that may have been implicated?
- Nation-state
- Hacktivist
- Insider
- Competitor
-
The Chief Security Officer (CSO) at a major hospital wants to implement SSO to help improve security in the environment and protect patient data, particularly at shared terminals. The Chief Risk Officer (CRO) is concerned that training and guidance have not been provided to frontline staff, and a risk analysis has not been performed. Which of the following is the MOST likely cause of the CRO’s concerns?
- SSO would simplify username and password management, making it easier for hackers to guess accounts.
- SSO would reduce password fatigue, but staff would still need to remember more complex passwords.
- SSO would reduce the password complexity for frontline staff.
- SSO would reduce the resilience and availability of systems if the identity provider goes offline.
-
Which of the following control types are alerts sent from a SIEM fulfilling based on vulnerability signatures?
- Preventive
- Corrective
- Compensating
- Detective
-
An attacker is attempting to harvest user credentials on a client’s website. A security analyst notices multiple attempts of random usernames and passwords. When the analyst types in a random username and password, the logon screen displays the following message:
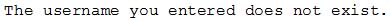
SY0-501 Part 47 Q15 122 Which of the following should the analyst recommend be enabled?
- Input validation
- Obfuscation
- Error handling
- Username lockout
-
A root cause analysis reveals that a web application outage was caused by one of the company’s developers uploading a newer version of the third-party libraries that were shared among several applications. Which of the following implementations would be BEST to prevent this issue from reoccurring?
- CASB
- SWG
- Containerization
- Automated failover
-
A systems administrator is implementing a remote access method for the system that will utilize GUI. Which of the following protocols would be BEST suited for this?
- TLS
- SSH
- SFP
- SRTP
-
A systems administrator wants to configure an enterprise wireless solution that supports authentication over HTTPS and wireless encryption using AES. Which of the following should the administrator configure to support these requirements? (Choose two.)
- 802.1X
- RADIUS federation
- WPS
- Captive portal
- WPA2
- WDS
-
During an audit, the auditor requests to see a copy of the identified mission-critical applications as well as their disaster recovery plans. The company being audited has an SLA around the applications it hosts. With which of the following is the auditor MOST likely concerned?
- ARO/ALE
- MTTR/MTBF
- RTO/RPO
- Risk assessment
-
When a malicious user is able to retrieve sensitive information from RAM, the programmer has failed to implement:
- session keys.
- encryption of data at rest.
- encryption of data in use.
- ephemeral keys.