ITE v8 – IT Essentials 7 – IT Essentials A+ 220-1102 Certification Practice Exam Answers Full 100% 2023 2024
ITE v8 and IT Essentials 7 – IT Essentials A+ 220-1102 Certification Practice Exam Answers 2023 2024 Full 100%
This is Cisco Netacad ITE v7 and ITE 8 – IT Essentials (Version 7.00) – IT Essentials A+ 220-1102 Certification Practice Exam Exam Answers full 100% for 2023 and 2024 verified by experts with explanations and hints.
| IT Essentials 8 | |
| IT Essentials 8 Final - Mid-term - Cert | |
| Chapter 1 -9 Skills Assessment | NA |
| Chapter 10 - 14 Skills Assessment | NA |
| Practice Final Exam Answers Ch 1 - 9 | Online Test |
| Practice Final Exam Answers Ch 10 - 14 | Online Test |
| Final Exam Answers Ch 1 - 9 | Online Test |
| Final Exam Answers Ch 10 - 14 | Online Test |
| Final Exam Composite Answers Ch 1 - 14 | Online Test |
| A+ 220-1001 | Online Test |
| A+ 220-1002 | Online Test |
IT Essentials (Version 8.0) – IT Essentials A+ 220-1102 Certification Practice Exam Answers Full 100% 2023 2024
-
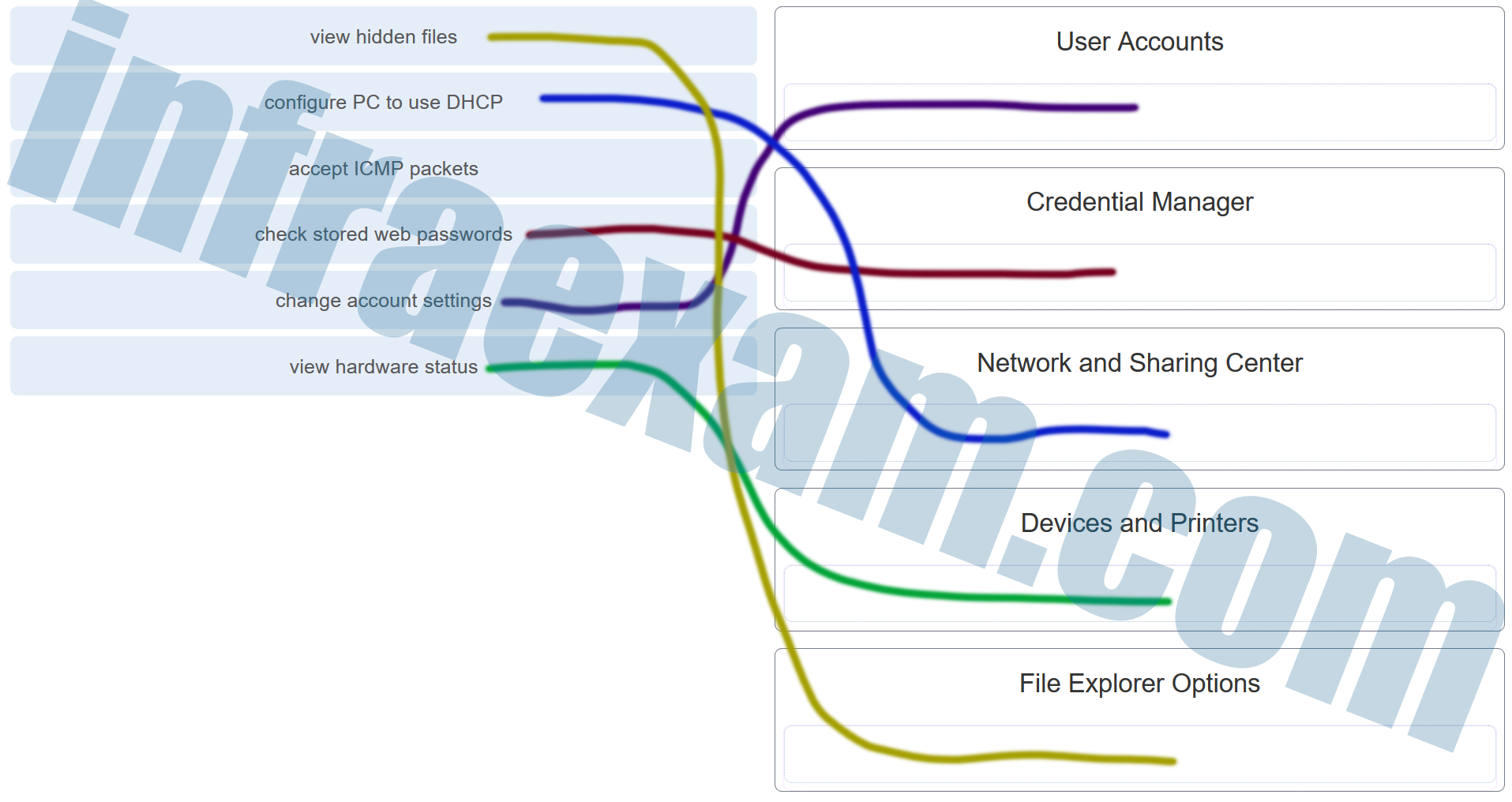
Match the task to the Windows 10 Control Panel utility. (Not all options are used.)
IT Essentials 7 – IT Essentials A+ 220-1002 Certification Practice Exam Answers 02 - view hidden files ==> File Explorer Options
- configure PC to use DHCP ==> Network and Sharing Center
- accept ICMP packets ==> (Not Score)
- check stored web passwords ==> Credential Manager
- change account settings ==> User Accounts
- view hardware status ==> Devices and Printers
Explanation & Hint: - View Hidden Files: This option allows you to modify the folder options to display files and folders that are typically hidden by default in the Windows operating system. Hidden files are often system files that are hidden to prevent accidental modification or deletion.
- Configure PC to use DHCP: DHCP stands for Dynamic Host Configuration Protocol. Configuring a PC to use DHCP means that it will automatically receive an IP address and other network settings (like the gateway, subnet mask, and DNS servers) from a DHCP server, typically a router or a server in a network.
- Accept ICMP Packets: ICMP stands for Internet Control Message Protocol. Allowing ICMP packets often refers to enabling the ability to send and receive network diagnostic packets, such as ping requests and responses. These are used to troubleshoot network connectivity issues.
- Check Stored Web Passwords: In Windows, you can use the Credential Manager to view and manage web credentials, including usernames and passwords that you’ve saved in your web browsers.
- Change Account Settings: This likely refers to the User Accounts settings, where you can change user account names, passwords, account types, and other user-specific settings.
- View Hardware Status: This can be done through the Device Manager, where you can see all the hardware connected to your computer, check for hardware issues, update drivers, and manage device properties.
The other terms in the image relate to various sections within the Windows Control Panel or the Settings app:
- User Accounts: This Control Panel section allows you to change user account settings, manage user accounts, and change account types (administrator or standard user, for instance).
- Credential Manager: This is where Windows stores credentials, such as usernames and passwords, that you use to log in to websites or other computers on a network.
- Network and Sharing Center: This section provides options to view network status, set up a new connection or network, and change advanced sharing settings.
- Devices and Printers: Here you can add and manage devices (like printers, phones, and peripherals) connected to your PC.
- File Explorer Options: This allows you to change how files and folders are displayed on your computer, including viewing hidden files, changing file associations, and other advanced settings.
-
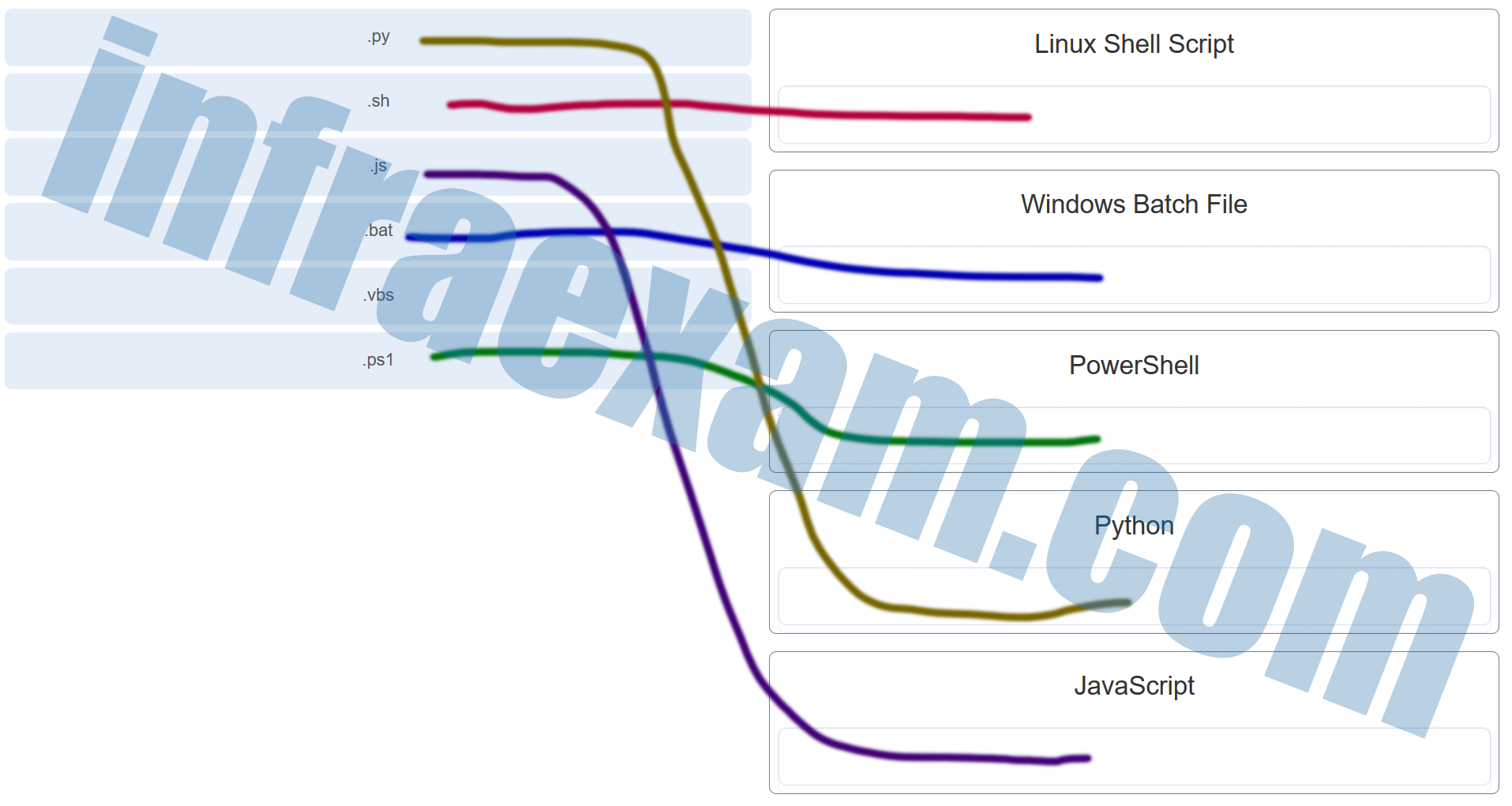
Match the scripting language with the script file name extension. (Not all options are used.)
IT Essentials 7 – IT Essentials A+ 220-1002 Certification Practice Exam Answers 01 - .py ==> Python
- .sh ==> Linux Shell Script
- .js ==> JavaScript
- .bat ==> Windows Batch File
- .vbs ==> (Not Score)
- .ps1 ==> PowerShell
Explanation & Hint: Linux Shell Script is .sh
Linux Shell Script uses a file extension of .sh.
Windows Batch File uses a file extension of .bat.
PowerShell uses a file extension of .ps1.
Python uses a file extension of .py.
JavaScript uses a file extension of .js.
VBScript uses a file extension of .vbs.
-
Which two data storage locations contain persistent data that can be used by computer forensics specialists? (Choose two.)
- hard disk drives
- solid state drives
- RAM
- cache
- CPU registers
Explanation & Hint: Persistent data is data stored on an internal or external hard drive, or an optical drive. Data is preserved when the computer is turned off.
-
On which two occasions is it most likely that a technician will have to perform a clean operating system installation if a backup has not been performed? (Choose two.)
- A user requires access to a new printer.
- The existing operating system is corrupted.
- The existing security software requires upgrading.
- The computer is being moved to a different network.
- A new replacement hard drive is installed in a computer.
-
Explanation & Hint: A clean installation of an operating system is usually required when:
- The existing operating system is corrupted: If the operating system has been damaged to the point where it cannot be repaired through other means (such as system repair, restoration, or in-place upgrades), a clean install is often the best or only option to get the system back to a functioning state.
- A new replacement hard drive is installed in a computer: If the computer’s primary hard drive, which contains the operating system, fails or is replaced, a clean installation of the operating system will be necessary, as the new drive will not have an operating system on it.
The other scenarios listed do not typically require a clean operating system installation:
- A user requires access to a new printer: This situation usually requires the installation of the appropriate printer drivers and software, not a reinstallation of the entire operating system.
- The existing security software requires upgrading: Upgrading security software is a common maintenance task and does not require reinstalling the operating system. It can typically be done within the existing environment.
- The computer is being moved to a different network: Moving a computer to a different network does not affect the installed operating system. Network s
-
Which three items are biometric security devices? (Choose three.)
- fingerprint reader
- retina scanner
- voice recognition
- smart card
- key fob
- password
Explanation & Hint: Fingerprint readers, retina scanners, and voice recognition are all biometric devices, comparing physical characteristics of the user to stored data to authenticate the user. Smart cards, key fobs, and passwords are all security measures, but do not rely on biometrics.
-
Which two precautions can help prevent social engineering? (Choose two.)
- Always ask for the ID of unknown persons.
- Escort all visitors.
- Keep your password securely under your keyboard.
- Do not allow any customers into the workplace.
- Always require a user name and password to be configured.
Explanation & Hint: Asking for IDs and escorting visitors are effective ways to prevent social engineering. Users should never keep their passwords in the work area. Eliminating customers is not always practical for business purposes.
-
Which two guidelines are appropriate for creating strong passwords? (Choose two.)
- Use at least eight characters.
- Include letters, numbers, and symbols.
- Change the password once each year.
- Use only upper case and numeric values in passwords.
- Passwords should contain symbols only.
Explanation & Hint: Strong passwords should be at least eight characters, and should include upper and lower case letters, numbers, and symbols. Although passwords should be changed regularly as specified in the local security policy, the amount of time between changes has no effect on the creation of strong passwords. Limiting a password to only symbols, or to only numbers and upper case letters, does not provide the strongest password possible.
-
A support desk technician is dealing with an angry customer. Which two approaches should the technician take in dealing with the customer? (Choose two.)
- Ask socially related questions to direct the customer away from the problem.
- Work to redirect the conversation to solving the problem.
- Immediately transfer the customer to a higher level technician.
- Reply to the customer with the same level of anger.
- Let the customer explain the problem without interrupting.
Explanation & Hint: Angry customers should be allowed to explain the problem, then be redirected to discussing how the problem can be solved. Transferring the customer, replying in a rude tone, and asking unrelated questions will usually increase, not ease, the anger being expressed by the customer.
-
A technician working on a computer discovers what is suspected to be illegal activity. Which three pieces of information should be immediately documented? (Choose three.)
- duration of the suspected illegal activity
- evidence of the suspected illegal activity
- why the computer was accessed by the technician
- details of all past users of the computer
- technical specifications of the computer
- location of the computer
Explanation & Hint: The initial reason for accessing the computer, the suspected illegal matter or operations, and the location of the computer are immediately apparent to the technician and should be among the first details documented. Details of past computer users and the duration of the illegal activity are matters that the appropriate investigators will determine. The technical specifications of the computer may have little relevance to its illegal use.
-
An administrative assistant tries to link a Bluetooth keyboard and mouse to a computer. The keyboard does not work, but the mouse works fine. What are two issues that could cause this situation? (Choose two.)
- Wi-Fi is turned off.
- The keyboard battery is dead.
- Bluetooth is turned off.
- The Num Lock key has been inadvertently pressed.
- The keyboard is too far from the computer.
-
Explanation & Hint: If a Bluetooth keyboard is not working while the Bluetooth mouse is working fine, two issues that could cause this situation are:
- The keyboard battery is dead: If the keyboard’s battery has no charge, it will not be able to communicate with the computer. Replacing the battery or charging the keyboard, if it uses rechargeable batteries, would be necessary.
- The keyboard is too far from the computer: Bluetooth devices have a range limit, typically up to 10 meters (33 feet) for Class 2 devices. If the keyboard is outside this range, it might not be able to establish or maintain a connection with the computer.
The other options provided are less likely to be the cause:
- Wi-Fi is turned off: Wi-Fi being turned off would not typically affect Bluetooth connectivity, as they are separate communication technologies. However, in some devices, turning off Wi-Fi might also turn off Bluetooth if they share a combined wireless card. But since the mouse is working fine, it indicates that Bluetooth is active.
- Bluetooth is turned off: This is not the issue because the mouse is working fine, which indicates that Bluetooth is enabled on the computer.
- The Num Lock key has been inadvertently pressed: The Num Lock key only affects the number pad on keyboards that have one. It would not prevent the entire keyboard from working. If only the number pad is unresponsive, this could be a possibility, but the scenario implies the entire keyboard is not functioning.
-
What two roles or tasks are associated with level two technicians? (Choose two.)
- remotely updating drivers and software on customer computers
- prioritizing incoming calls according to their severity
- gathering customer information to initiate a work order
- escalating a trouble ticket to a higher level technician
- gathering diagnostic information from a customer computer
Explanation & Hint: Level two technicians are primarily tasked with receiving and working on escalated work orders. Their tasks involve using remote access software to connect to the computer of a customer to perform maintenance and fixes.
-
What are two file attributes in the Windows environment? (Choose two.)
- details
- archive
- read-only
- security
- general
Explanation & Hint: The file attributes are read-only, archive, hidden, and system. Details, security, and general are tabs on the file Properties applet.
-
A user finds that when launching a downloaded Windows update file, Windows Update fails. What are two possible causes for this? (Choose two.)
- The hard disk is failing.
- The Windows Firewall is turned off.
- The downloaded update file is corrupted.
- The virus definitions are out of date.
- A previous update that is required for the current update is not installed.
Explanation & Hint: In the event that the downloaded update file is corrupted or a previously required update was not installed, the Windows Update process will fail.
-
A store in a shopping center uses a wireless network to provide internet access for three tablet computers. The authentication to the wireless router has been configured as 128-bit WEP. Recently the store employees notice that the internet connection is getting slower. The network administrator of the shopping center reviews the logs of the wireless router and notices many non-store devices are associated with the router. Which two actions can the network administrator do to improve the security of the wireless network access? (Choose two.)
- Use a 32-character long SSID.
- Change WEP to WPA2 protocol.
- Change to the 152-bit WEP protocol.
- Use the MAC address filtering feature.
- Ensure that the shared key is randomly generated.
Explanation & Hint: The SSID is used to identify the wireless LAN and should not be considered a method for securing the WLAN. WEP encryption is weak and prone to attacks with wireless hacking tools. WEP should not be used and has been replaced by the much more secure WPA2 protocol. MAC address filtering can ensure that only authorized devices can be associated with the wireless router.
-
A user is hiking in a city park. The user wants to make a call home but cannot get a reliable cellular signal. What are two possible causes for the bad cellular coverage? (Choose two.)
- The location service is turned off.
- The Bluetooth headset is unpaired.
- There are not enough cell towers in the area.
- The distance to the nearest Wi-Fi access point is too far.
- The user is located between coverage areas of the carrier.
Explanation & Hint: A mobile user may experience weak or dropped signal issues if there are not enough cell towers surrounding the area or the location is not covered well by the carrier.
-
A user purchases a new smartphone and is trying to use a high quality Bluetooth headset on the new device. However, the headset is not connected to the smartphone. What are three settings that the user needs to check to troubleshoot the problem? (Choose three.)
- The headset is turned on.
- The pin code is entered correctly.
- The authentication service is turned on.
- The USB port on the headset is working.
- The Bluetooth connection is enabled on the smartphone.
- The battery capacity on the smartphone is above 50%.
Explanation & Hint: Three factors contribute to a successful pairing between a Bluetooth capable host (the smartphone in this case) and a Bluetooth device (the headset):
The Bluetooth device is turned on.
The pin code is entered correctly.
The Bluetooth connection is enabled on the mobile device.
-
An IT technician in a service company has provided extensive remote IT support with product deployment for a customer. After the completion of the contract, a complaint is filed against the IT technician for not following company policy by sending unsolicited emails about services and products that are not related to the contract. What two things should the IT support technician have done differently? (Choose two.)
- The IT technician should have researched the company policy about personal communication with customers on company time.
- The IT technician should have used encryption to hide the purpose of the emails.
- The IT technician should have added the customer to a chain letter with many recipients instead.
- The IT technician should have asked the customer if the customer was interested in receiving information regarding other new services and products.
- The IT technician should have requested permission from a supervisor to send the customer emails.
Explanation & Hint: While working with customers both briefly and over an extended period of time, it is possible to form friendly relationships. It is important to always follow company policy and never send unsolicited messages to a customer. Also do not send unsolicited mass mailings or chain letters to customers from a company email address. Any personal relationships should be kept via personal email accounts and should not reflect the IT organization of the employer.
-
A third-party security firm is performing a security audit of a company and recommends the company utilize the Remote Desktop Protocol. What are two characteristics of the Microsoft Remote Desktop Protocol (RDP)? (Choose two.)
- RDP connects on TCP port 22.
- RDP requires a Windows client.
- RDP uses an encrypted session.
- RDP is a command-line network virtual terminal protocol.
- RDP connects on TCP port 3389.
Explanation & Hint: The Remote Desktop protocol (RDP) is used to remotely access a Windows OS. It is a client/server protocol.The port number for RDP is TCP port 3389 and it uses encryption.
-
A computer can successfully ping outside the local network, but cannot access any World Wide Web services. What is the most probable cause of this problem?
- Windows Firewall is blocking port 80.
- Windows Firewall blocks port 23 by default.
- The computer network interface card is faulty.
- The BIOS or CMOS settings are blocking web access.
Explanation & Hint: The World Wide Web (HTTP) protocol uses port 80; port 23 is used by Telnet. Successful pings to other devices indicate that the network interface card is working correctly. BIOS and CMOS settings control system hardware functions, not network applications such as the World Wide Web.
-
A technician notices that an application is not responding to commands and that the computer seems to respond slowly when applications are opened. What is the best administrative tool to force the release of system resources from the unresponsive application?
- Task Manager
- Add or Remove Programs
- Event Viewer
- System Restore
Explanation & Hint: Use the Task Manager Performance tab to see a visual representation of CPU and RAM utilization. This is helpful in determining if more memory is needed. Use the Applications tab to halt an application that is not responding.
-
Which question would be an example of an open-ended question that a technician might ask when troubleshooting a security issue?
- Is your security software up to date?
- Have you scanned your computer recently for viruses?
- Did you open any attachments from a suspicious email message?
- What symptoms are you experiencing?
Explanation & Hint: Close-ended questions generally have a fixed or limited set of possible responses, such as “yes” or “no”. Open-ended questions imply no limited or fixed set of replies but rather generally prompt the responder to provide more meaningful feedback.
-
A technician is troubleshooting a computer security issue. The computer was compromised by an attacker as a result of the user having a weak password. Which action should the technician take as a preventive measure against this type of attack happening in the future?
- Check the computer for the latest OS patches and updates.
- Verify the physical security of all offices.
- Ensure the security policy is being enforced.
- Scan the computer with protection software.
Explanation & Hint: As part of the fifth step of the troubleshooting process, technicians should apply preventive measures whenever possible. Most company security policies include a section on password complexity and length requirements. Ensuring that this policy is being enforced can help prevent attackers from being able to compromise systems through password cracking.
-
A user wants to extend a primary partition formatted with the NTFS file system with the unallocated space on the hard disk. What must the user do after the primary partition is extended to make it usable?
- Convert the disk type to dynamic.
- Ensure that the disk type is basic.
- Format the disk with the FAT64 file system.
- Partition the new space as a basic disk.
Explanation & Hint: A partition must be formatted with the NTFS file system in order to extend it by using the unallocated space on the disk. Once the partition has been extended, the disk type must be converted to a dynamic disk in order for the new partition to be accessible.
-
A technician has successfully removed malware from a PC and finds that when the system is rebooted error messages are displayed about missing and corrupt system files. What utility can the technician use to replace or fix any corrupted system files?
- ASR
- Fixboot
- Fixmbr
- Regedit
- SFC
Explanation & Hint: ASR is used to recover the operating system when it is totally corrupt and will not boot. Regedit is a registry editor whereas Fixmbr and Fixboot are command line utilities that can be used to repair corrupt boot records. SFC is used to check the integrity of any system files that may have been corrupted and repair them.
-
What is the first step a technician should take when preparing to work on the inside of a computer?
- Remove the power supply.
- Disconnect the computer from power.
- Disconnect the computer from the network.
- Remove external devices such as a mouse.
Explanation & Hint: Before any service inside a computer is performed, the PC should be turned off and disconnected from any source of power to reduce the risk of shock.
-
What is required in order to connect a Wi-Fi enabled laptop to a WPA secured wireless network?
- a security encryption key
- a MAC address
- a username and password
- an updated wireless driver
Explanation & Hint: Regardless of the levels of security configured on a WLAN, a WPA secured WLAN always requires the use of an encryption key. Without the proper key, a device cannot connect to the network.
-
What is a feature that can be used by an administrator to prevent unauthorized users from connecting to a wireless access point?
- MAC filtering
- software firewall
- proxy server
- WPA encryption
Explanation & Hint: Limiting a certain set of MAC addresses to connect to an access point is a way to ensure that only those devices are allowed to use the wireless network. A software firewall is used to prevent other users from gaining access to the protected computer. Configuring WPA encryption does not guarantee that the unauthorized user will not find the way to connect to the network. A proxy server is mostly used to filter traffic based on content.
-
A user is configuring a wireless access point and wants to prevent any neighbors from discovering the network. What action does the user need to take?
- Disable SSID broadcast.
- Enable WPA encryption.
- Configure DMZ settings.
- Configure a DNS server.
Explanation & Hint: Disabling SSID broadcast prevents the access point from announcing the name of the network. Enabling WPA encryption, configuring DMZ settings, and configuring a DNS server will accomplish different tasks, but the name of the network will still be announced.
-
What type of file system allows the use of files larger than 5 GB and is mostly used on internal hard drives?
- FAT32
- FAT64
- NTFS
- CDFS
- exFAT
Explanation & Hint: The file system exFAT, also known as FAT64, is used to address some of the shortcoming of FAT32 and is mainly used for USB flash drives. CDFS is used for optical drives. FAT32 allows the storage of files up to 4 GB in size. NTFS allows the storage of files up to 16 TB in size.
-
Which user account should be used only to perform system management and not as the account for regular use?
- guest
- standard user
- administrator
- power user
Explanation & Hint: The administrator account is used to manage the computer and is very powerful. Best practices recommend that it be used only when it is needed to avoid accidentally performing significant changes to the system.
-
A user has detected that one of the virtual machines in a computer is infected with a virus. Which statement about the situation is likely to be true?
- The host operating system is not necessarily infected with a virus.
- The host machine operating system has a bug.
- All of the virtual machines running on the host are infected with a virus.
- The host machine antivirus program requires an update.
Explanation & Hint: The virtual machines work separately from the host operating systems, even though they use the same system resources. The weaknesses and vulnerabilities from one virtual machine are not spread to other virtual machines or the host operating system.
-
After complaints from users, a technician identifies that the college web server is running very slowly. A check of the server reveals that there are an unusually large number of TCP requests coming from multiple locations on the Internet. What is the source of the problem?
- A DDoS attack is in progress.
- The server is infected with a virus.
- There is insufficient bandwidth to connect to the server.
- There is a replay attack in progress.
Explanation & Hint: The source of the problem cannot be a virus because in this situation the server is passive and at the receiving end of the attack. A replay attack uses intercepted and recorded data in an attempt to gain access to an unauthorized server. This type of attack does not involve multiple computers. The issue is not the bandwidth available, but the number of TCP connections taking place. Receiving a large number of connections from multiple locations is the main symptom of a distributed denial of service attack which use botnets or zombie computers.
-
What is true about restore points?
- Once System Restore is used to restore a system, the change is irreversible.
- Restore points back up personal data files.
- Restore points recover corrupted or deleted data files.
- Restore points should always be created before making changes to a system.
Explanation & Hint: Any change from a system restore is reversible. A restore point only contains information about the system and registry settings and therefore cannot be used to backup or recover data files.
-
A business organization is configuring security on the mobile devices that are used in the organization. The security policy states that business data on mobile devices should only ever be accessed by employees. Which mobile device security feature can be used to best ensure that business data is rendered completely inaccessible if the device is lost or stolen?
- remote lock
- remote wipe
- passcode lock
- sandbox
Explanation & Hint: Remote wipe is a security feature that remotely clears the device of all user data to prevent it from being maliciously compromised. Remote lock and the user passcode lock features on mobile devices can help prevent theft of private information but the data remains on the device and may be accessed if the passcode is ever broken. Sandbox describes the running of mobile apps separate from the operating system.
-
A user is able to only access files required to perform a specific task. What type of security practice is being applied?
- principle of privileges
- principle of necessary privilege
- principle of most privilege
- principle of least privilege
Explanation & Hint: Limiting access to files or folders that are needed to perform a specific job is known as the principle of least privilege. The other options do not exist.
-
Which type of malware is disguised as a legitimate program?
- adware
- worm
- Trojan
- spyware
Explanation & Hint: Trojan horses disguise themselves as legitimate programs. Worms replicate themselves across a network. Adware may attach to a legitimate program, but does not disguise itself. Spyware monitors the activities of a user.
-
Which security threat hides the resources that it uses from antivirus programs?
- worm
- Trojan
- rootkit
- spyware
Explanation & Hint: Rootkits target a known vulnerability to gain administrator-level access. This gives the rootkit the ability to hide itself. Trojans, worms, and spyware do not gain administrator level access.
-
Which statement is correct about installing a 32-bit operating system on a x64 architecture?
- The OS will always make use of all the RAM available.
- The OS will run correctly.
- The OS can address more than 128 GB of memory.
- This combination will provide better security.
Explanation & Hint: A 32-bit operating system can run on a x64 architecture, but it will not be able to use more than 4 GB of the system memory. A 64-bit OS includes features that provide additional security.
-
A technician is troubleshooting a workstation in a domain that has been infected with a virus. What is the first step the technician should take to clean the infected workstation?
- Run the antivirus software.
- Update the antivirus software.
- Turn off system restore.
- Disconnect the workstation from the network.
Explanation & Hint: The first step is to disconnect the infected workstation from the network. This will quarantine the infected workstation and prevent the virus from spreading throughout the network.
-
A technician needs to permanently destroy data on some drives before disposing of them. What is the best way to do this?
- Partition the hard drives.
- Perform a full format.
- Overwrite the drives
- Shatter the drive platters with a hammer.
Explanation & Hint: The best way to permanently destroy data is by shattering the platters of the hard drives with a hammer.
-
A cleaner attempts to enter a computer lab but is denied entry by the receptionist because there is no scheduled cleaning for that day. What type of attack was just prevented?
- Trojan
- shoulder surfing
- war driving
- social engineering
- phishing
Explanation & Hint: Social engineering is when a person attempts to manipulate another individual to gain access to information or resources to which they are not entitled.
-
A company has replaced five desktop computers in the accounting and finance department with new computers. The plan is to donate the recovered computers in a fully functional state to a not-for-profit community organization. How can the company ensure that sensitive financial data cannot be accessed once the computers are donated?
- Data wipe the hard drives by using specialized software.
- Perform a high-level format on the hard drives.
- Drill holes through the hard drive platters.
- Delete all the files and directories on the hard drives.
Explanation & Hint: Data wiping the hard drives with software that will securely erase all data will ensure that company data cannot later be accessed. This may be time consuming but for a small number of computers this is more cost-effective than the expense of degaussing. Deleting all the files and directories on the hard drives or performing a high-level format on each drive will leave the computers vulnerable to having the company data recovered by specific forensic software. Drilling holes in the hard drive platters would mean that the computers are no longer in working condition.
-
A technician is about to install and configure a wireless network at a small branch office. What is the first security measure the technician should apply immediately upon powering up the wireless router?
- Configure encryption on the wireless router and the connected wireless devices.
- Disable the wireless network SSID broadcast.
- Change the default user-name and password of the wireless router.
- Enable MAC address filtering on the wireless router.
Explanation & Hint: The first action a technician should do to secure a new wireless network is to change the default user-name and password of the wireless router. The next action would usually be to configure encryption. Then once the initial group of wireless hosts have connected to the network, MAC address filtering would be enabled and SSID broadcast disabled. This will prevent new unauthorized hosts from finding and connecting to the wireless network.
-
What does virtual memory provide to an operating system?
- an increase in data storage
- an increase in the speed of accessing RAM
- a temporary storage of data until enough RAM is available to process it
- the creation of virtual partitions on the hard drive
Explanation & Hint: The OS uses virtual memory when a computer does not have enough RAM available to run a program. Virtual memory moves data from RAM and places it in a paging file on the hard drive. A paging file is a place where data is stored until enough RAM is available to process the data. This process is much slower than accessing the RAM directly.
-
Which disk management tool scans the critical files of an operating system and replaces the corrupt files?
- Scandisk
- Chkdsk
- Disk Cleanup
- Optimize Drives
- System File Checker
Explanation & Hint: System File Checker will scan critical files of an operating system and replace corrupt files. Scandisk and Chkdsk check the integrity of files and folders on a hard drive. Optimize Drives optimizes space on a hard drive. Disk Cleanup will clear space on a hard drive by looking for files that can be deleted.
-
Why would an administrator use Windows Remote Desktop and Windows Remote Assistant?
- to provide secure remote access to resources on another network
- to connect to an enterprise network across an unsecured connection and act as a local client of that network
- to enable sharing of files and presentations with a group of users over the Internet
- to connect to a remote computer over the network to control its applications and data
Explanation & Hint: Windows Remote Desktop and Remote Assistant allow an administrator to connect a local computer with a remote computer across the network and to interact with it as though it were the local computer. The administrator sees and can interact with the desktop of the remote computer. With Remote Desktop, the administrator logs onto the remote computer using an existing user account and starts a new user session. No user is required at the remoter computer to allow this access. With Remote Assistant, the purpose is for a technician to interact with a remote computer with the assistance of a remote user. The remote user must allow the remote access to the current user session and is able to observe what the technician is doing.
-
A technician needs to check the system settings on a remote computer to make sure it will be compatible with a new software update that will be sent out. The technician will use an administrator account to log in and start a user session on the remote PC. Which Windows tool will the technician use to accomplish this?
- Windows Update Assistant
- Windows VPN remote access client
- Windows Remote Desktop
- Windows file sharing services
Explanation & Hint: Windows Remote Desktop allows a technician to log in to a remote computer through an existing user account. The technician can run programs and view and manipulate files within the system of the remote computer.
-
A business traveler connects to a wireless network with open authentication. What should the traveler do to secure confidential data when connecting to the business services?
- Connect with a VPN.
- Change the network location profile to public.
- Change the Windows firewall settings.
- Manually configure an IP address, subnet mask, and default gateway.
Explanation & Hint: A VPN is used to form a secure tunnel across a public network. This technology allows users to communicate over an insecure network and yet keep data confidential. Changing the network location profile will modify firewall settings on a computer but not increase the confidentiality of data crossing a network. Modifying the IP address, subnet mask, and default gateway will not change the confidentiality of data transmitting on a network.
-
What determines the level of support that a call center technician will provide to an individual customer?
- Support is based on the SLA for that customer.
- All customers receive the same level of support by the call center.
- A level one technician will provide a higher level of support than a level two technician.
- An individual call center technician chooses the level of support based on the time available to assist the customer.
Explanation & Hint: A call center technician must provide the level of support that is outlined in the SLA for that individual customer.
-
A corporation has expanded to include multiple remote offices around the globe. Which technology should be used to allow the remote offices to communicate and share network resources privately?
- VPN
- Remote Desktop
- administrative share
- Remote Assistance
Explanation & Hint: A Virtual Private Network (VPN) is used to connect remote sites together securely over a public network.
-
A user reports that a PC is losing files, not opening some files, and is performing slowly. The technician suspects problems with the hard drive. What should be done to protect the data that is on the PC and to determine the source of the problem, without risking total drive failure?
- Run the format command , then replace the hard drive.
- Run chkdsk , then run format .
- Back up all important files, then replace the hard drive.
- Back up all important files, then run chkdsk .
- Run chkdsk , then back up all important files.
Explanation & Hint: Backing up important files is the first step in protecting existing data. After backing up, running chkdsk will allow the technician to determine if there are bad sectors on the hard drive, without losing any data.
-
A computer technician is notified by a user that there are no automated backups being created on an Apple computer. What is the first thing the technician should check?
- correct date and time configuration
- whether Time Machine is turned on
- if space is available on the local drive
- whether Remote Disc is enabled
Explanation & Hint: Time Machine is the OS X backup tool. To verify whether the tool is turned on, access Settings > Time Machine .
-
A user has been using a smartphone for several hours, but now the applications on the device have become unresponsive. What action should the user take?
- Reconfigure settings.
- Restore the mobile operating system from a backup.
- Restart the device.
- Reset the device to factory defaults.
Explanation & Hint: Restoring a device to factory defaults should only be done if either or both of the following have failed: restarting the device or turning the device off and powering it back on again.
-
When would the PXE option be used when repairing a PC?
- The display cannot be seen clearly.
- There is no response from the mouse or keyboard.
- The computer needs a replacement operating system.
- A newly installed application caused the system to perform erratically.
Explanation & Hint: The Preboot eXecution Environment (PXE, but pronounced pixie) BIOS boot option is used to install an operating system from a remote network location.
-
Which statement describes most enterprise software licenses?
- A user is allowed to install the software on only one computer.
- A company is allowed to use the software campus wide.
- Developers are allowed to modify and share the source code of the software.
- A user is allowed to share the software with friends.
Explanation & Hint: Enterprise software licenses enable many employees of an organization to use a software application, often without the need to register the individual installations. Personal software licenses are intended for personal use of the product. Most personal software licenses allow a user to run the software on only one PC. Open source licenses allow users to modify and share the source code of the software.
-
A company has recently deployed Active Directory and now a workstation cannot connect to a network resource. A technician takes corrective action by modifying group policy settings. Which command should the technician use to make the workstation synchronize with the new settings?
- runas
- rstrui
- tasklist
- gpresult
- gpupdate
Explanation & Hint: The functions of the listed commands are as follows:
runas – runs a program or tool with different permissionsrstrui – starts the System Restore utilitygpresult – displays group policy settingsgpupdate – refreshes group policy settingstasklist – displays currently running applications
-
A user logs into Active Directory on a workstation and the user home directory does not redirect to a network share on a file server. A technician suspects that the group policy setting is incorrect. Which command can the technician use to verify the group policy settings?
- rstrui
- runas
- tasklist
- gpresult
- gpupdate
Explanation & Hint: The functions of the listed commands are as follows:
runas – runs a program or tool with different permissionsrstrui – starts the System Restore utilitygpresult – displays group policy settingsgpupdate – refreshes group policy settingstasklist – displays currently running applications
-
In a Linux operating system, which component interprets user commands and forwards them to the OS?
- CLI
- shell
- kernel
- application program
Explanation & Hint: The functions of different components of a Linux system are as follows:CLI – command-line interface, accepts user commands
shell – a program that interprets the user commands and passes them to the OS
kernel – manages CPU and RAM allocation to processes, system calls, and file systems
application program – program for various applications
-
In Linux and OS X, which CLI command can be used to display the name of the current directory?
- ps
- pwd
- sudo
- chmod
Explanation & Hint: The functions of listed CLI commands of Linux and OS X systems are as follows:ps – lists the process currently running in the system
pwd – displays the name of the current directory
sudo – runs a command as another user
chmod – modifies file permissions
-
A virus has infected several computers in a small office. It is determined that the virus was spread by a USB drive that was shared by users. What can be done to prevent this problem?
- Destroy the USB drive.
- Activate Windows Firewall.
- Change the passwords on the computers.
- Set the antivirus software to scan removable media.
Explanation & Hint: To prevent the problem, the antivirus software should be configured to scan removable media. Destroying the USB drive will prevent that device from spreading the virus to other computers, but will not prevent future transmission of viruses from USB drives. Windows Firewall is a useful tool, but it does not prevent the spread of viruses.
-
Which wireless encryption method is the least secure?
- WEP
- WPA
- AES
- TKIP
Explanation & Hint: WEP is the weakest encryption method. WPA, AES, and TKIP are considered enhancements to the WEP standard and therefore are more secure.
-
A user is reporting that a file has been shared specifically with another user on the network, but the other user opens the file and is unable to save it once edited. What is the probable cause?
- The user shared the document with Read permissions.
- The user forgot to share the parent folder.
- The file has the Archive attribute enabled.
- The file has been deleted.
Explanation & Hint: The permission setting should have been Change or Full Control. The Read permission does not allow edited files to be saved.
-
A customer is explaining a problem with a computer to a technician. The technician recognizes the problem prior to the customer finishing the explanation. What should the technician do?
- Interrupt the customer and let the customer know that the technician knows what the problem is.
- Start working on the PC while listening to the customer at the same time.
- Ask the customer to repeat the problem so that the technician can document it and verify all the facts.
- Wait politely for the customer to finish explaining the problem.
Explanation & Hint: It is always important to allow the customer to finish explaining the problem at hand. You should always be attentive and actively listen to the customer without interrupting and acknowledge the customer occasionally to affirm that you are actively listening to the customer.
-
The Windows PC of a user was shutdown abruptly due to a sudden loss of power. The user then reports that the workstation has lost several files. A help desk technician suspects that part of the hard disk might be damaged. Which Windows utility can the technician use to scan the hard disk and make repairs if necessary?
- Chkdsk
- Disk Cleanup
- Disk Defragmenter
- System File Check
Explanation & Hint: The utility Chkdsk in Windows can be used to check the integrity of files and folders on a hard drive by scanning the file system. It also checks the disk surface for physical errors and tries to fix the errors.
-
A user calls the help desk and reports that the workstation, when powering up, displays error messages about an invalid system disk or invalid boot disk. When a technician comes to the office, the user mentions that the workstation was working well the day before. The technician checks the workstation and makes sure that the cable is firmly connected between the hard drive and the motherboard. What is another likely cause of the problem?
- The MBR/GPT is corrupted.
- The boot service fails to start.
- Some of the operating system files may be corrupted.
- A recently installed device driver is incompatible with the boot.
Explanation & Hint: These error messages indicate that the workstation cannot detect the hard drive as a bootable device. One possible cause is that the MBR/GPT on the hard drive is corrupted so that the workstation cannot locate a valid partition that holds the necessary codes to start booting.
-
A user reports that an application crashed. The technician tries a few other applications on the PC and finds that none of them start normally or that they crash soon after being launched. What is a possible cause of the problem?
- The hard disk is failing.
- The PC is infected by a virus.
- The Windows Firewall is turned off for the Private networks profile.
- The applications need updates from the software vendors.
Explanation & Hint: A virus infection could cause issues such as a file name change, one or more applications crashing, or files disappearing on a PC. The failing hard disk and lack of updates from the vendors should not cause the same issues for multiple applications. The Windows Firewall being off is not a direct cause of such issues.
-
A user calls the help desk and reports that a security alert appears on the screen about a malware attempt to enter the PC. What should the technician instruct the user to do?
- Turn on the Windows Firewall.
- Close the email client software.
- Scan the PC to remove any malware.
- Stop wired or wireless network connection immediately.
Explanation & Hint: The security alert indicates that the antimalware software has detected a potential malware attack. There could be other malware attacks toward the PC. Therefore, the user should be proactive and run a thorough security scan to remove any malware that is found.
-
A student tells a teacher that many junk emails are appearing on a new personal laptop. What is a possible cause of the problem?
- The student has spent too much time surfing the web.
- The school email server is not functioning properly.
- The laptop needs to be updated to the latest OS version.
- The new laptop does not have antivirus or anti-spam software installed.
Explanation & Hint: A new computer should have antivirus, or anti-spam filter for the email client, or anti-spam software installed to protect from spammers.
-
A sales representative is driving to visit several customer sites in the city. The representative notices that the smartphone is draining battery power more quickly than normal. What is a possible cause of the issue?
- The battery charger is malfunctioning.
- The smartphone was not fully charged.
- The smartphone is roaming among cell towers.
- There are not enough Wi-Fi access points in the area.
Explanation & Hint: When a mobile device is roaming among cells, the battery consumption is increased because the device needs to detect and negotiate with cell towers for connections. What the user experienced here is relative to the normal use. Thus, the issues of whether the device is fully charged and the condition of the battery charger are irrelevant.
-
A user is shopping in a mall and gets a notification that a new email is received on the smartphone. The user is wondering how the email message was delivered because the data usage feature is turned off. The user notices that the smartphone is connected to the coffee shop inside the mall using Wi-Fi. What caused this connection?
- The Wi-Fi access point in the coffee shop uses the same channel as the user smartphone uses.
- The Wi-Fi access point in the coffee shop uses WPA2 Personal settings.
- The smartphone is set to automatically connect to available Wi-Fi networks.
- The service carrier of the smartphone provides Wi-Fi connections inside the mall.
Explanation & Hint: When a mobile device is set to automatically connect to unknown Wi-Fi networks, the device will search and connect to any open access Wi-Fi networks.
-
A user attended the wedding of a coworker and took pictures using a smartphone. The user receives phone calls from several coworkers the next day and is shocked to learn that these pictures now appear on multiple web pages. What is a possible cause for the incident?
- The passcode for the smartphone has been hacked.
- The user account for the cloud service has been hacked.
- The smartphone sent the pictures to the websites by mistake.
- The smartphone is set to automatically upload files to the coworker group folder.
Explanation & Hint: Many service carriers offer cloud-based storage for mobile devices to upload contents to the cloud service for backup purposes. However, if the user account to the cloud service is compromised, a hacker can access the contents freely.
-
A student is jogging in a city park. The student has an app on the smartphone that tracks exercise activities. The student receives a notification that a new email has been received and stops to read the email message. However, the email app is slow to respond. What is a reason for the slowness of the app to open?
- The smartphone OS is frozen.
- The email app requires a large amount of RAM.
- The exercise tracking app is using the GPS service.
- The smartphone is unable to decrypt the email message.
Explanation & Hint: The health app uses the GPS receiver to track certain exercise activities, such as jogging and running. GPS service uses a lot of device resources to find and sync with satellites. The GPS receiver locks onto the signals sent from the satellites and constantly calculates its position relative to these satellites. After the position has been determined, the GPS receiver calculates other information, such as speed, time, and distance to a programmed destination. While the GPS receiver is working, a mobile device may appear slow in response to other apps.
-
A user reports that the PC displays a warning message. The warning message indicates that the PC is infected by a virus. A technician comes with a USB drive that contains a malware detection and removal program. What should the technician do before running the program?
- Make a backup of the data.
- Disconnect the hard drive.
- Boot the PC in Safe Mode.
- Change the BIOS setting to make the USB drive bootable.
Explanation & Hint: Booting the PC in Safe Mode will prevent most drivers and applications from loading into the system. These may include drivers and programs related to malware. Safe Mode allows the antivirus software to scan all areas of the disk.
-
A user reports that a Windows 10 PC displays a warning message. The warning message indicates that the PC is infected by malware. A technician comes to the office and makes sure that the PC is disconnected from all wired and wireless networks. What should the technician do next to further investigate the incident?
- Disconnect the hard drive.
- Boot the PC in Safe Mode.
- Save log files to removable media.
- Move the malware to the Quarantined Items folder.
Explanation & Hint: When a malware protection program detects that a computer is infected, it removes or quarantines the threat. However, the computer is most likely still at risk. The first step to remediating an infected computer is to remove the computer from the network to prevent other computers from becoming infected. The next step is to follow any incident response policies that are in place. The log files should be saved to a removable media for further analysis. Restarting an infected PC may destroy the evidence of infection.
-
All Windows 10 computers in a small advertising company are configured with the System Restore service. One of the PCs was infected by malware when an employee was doing research on the internet. The IT administrator scans the system and deletes the malware from the Quarantined Items folder. What should the administrator do next to complete the remediation process?
- Create a restore point.
- Delete all restore points.
- Disable the System Restore service.
- Restore the system from a backup.
Explanation & Hint: Once the System Restore service is turned on, a PC will create regular restore points. When the PC is infected with malware, the system restore points may contain infected files. Deleting all system restore points after the system has been remediated, prevents bringing infected files into the system when the System Restore service is needed.
-
A mobile user downloads and installs an app. Once the app is installed, the Android mobile device is frozen. What is a cause for the issue?
- The app needs an update.
- The mobile OS needs to be replaced.
- The app is not compatible with the device.
- Additional apps are needed for the app to function correctly.
Explanation & Hint: A new app may not have been designed properly and may not be compatible with the OS on an Android device. Because of this, the device may appear frozen.
-
When a user tries to run a program, a missing or corrupt DLL message is displayed. What is a solution to fix the problem?
- Reinstall the correct drivers.
- Use the msconfig command to adjust the startup settings for the program.
- Run Windows Startup Repair.
- Run sfc /scannow in Safe Mode.
Explanation & Hint: A possible solution to a reported missing or corrupt DLL is to restart the computer in Safe Mode and run sfc /scannow . Windows Startup Repair is used to solve Windows startup problems. Adjusting the program startup settings by using msconfig is applicable only to programs that start correctly. Drivers relate to hardware, not to programs.
-
A server administrator needs to remotely configure a legacy network device. The legacy network device only supports a plain-text session connection. Which remote access tool should be used?
- Telnet client
- Windows Remote Desktop client
- SSH client
- Windows Remote Assistance client
Explanation & Hint: Legacy devices may not support remote access sessions that require encryption. These devices may rely on using plain-text sessions provided by the Telnet protocol on TCP port 23.
-
A programmer is building a script that will test a condition of either true or false. Which data type would the programmer use?
- char
- Bool
- int
- float
Explanation & Hint: The basic data types used in a script include:
int represents integerschar represents charactersfloat represents decimal numbersstrings represent alphanumeric charactersBool represents true or false
-
A programmer needs to automate processes and tasks in an operating system. Which tool would the programmer use to build a script file?
- a text editor
- a comparison operator
- an executable automation tool
- a compiler
Explanation & Hint: A script file is a simple text file used to automate processes and tasks on various operating systems. A “script” can be created by any common text editor.
-
A user has a computer that is infected with spyware. What should be performed after the spyware is completely cleaned?
- Delete system restore files.
- Run Windows Update .
- Run a disk defragmentation.
- Create a full backup.
Explanation & Hint: An infected computer that performs a system restore will save the virus or spyware along with the restore point. Therefore, system restore files must be deleted after the removal of malware.
-
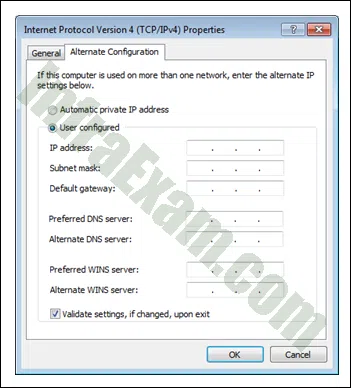
Refer to the exhibit. In what situation would a technician use this tab?
ITE v8 – IT Essentials A+ 220-1102 Certification Practice Exam Answers 01 - when the device will not be using the Internet
- when a laptop is used both at work with DHCP and at home with a static IP address
- when a device is behind a firewall and software is being used that needs access to a remote network
- when the computer will be using a VPN connection and accessing the Internet while connected through the VPN
Explanation & Hint: The Alternate Configuration tab allows a device to have two IP configurations. One configuration allows for setting the network card to DCHP using the General tab and then configuring a static IP address for the home network using the Alternate Configuration tab.
-
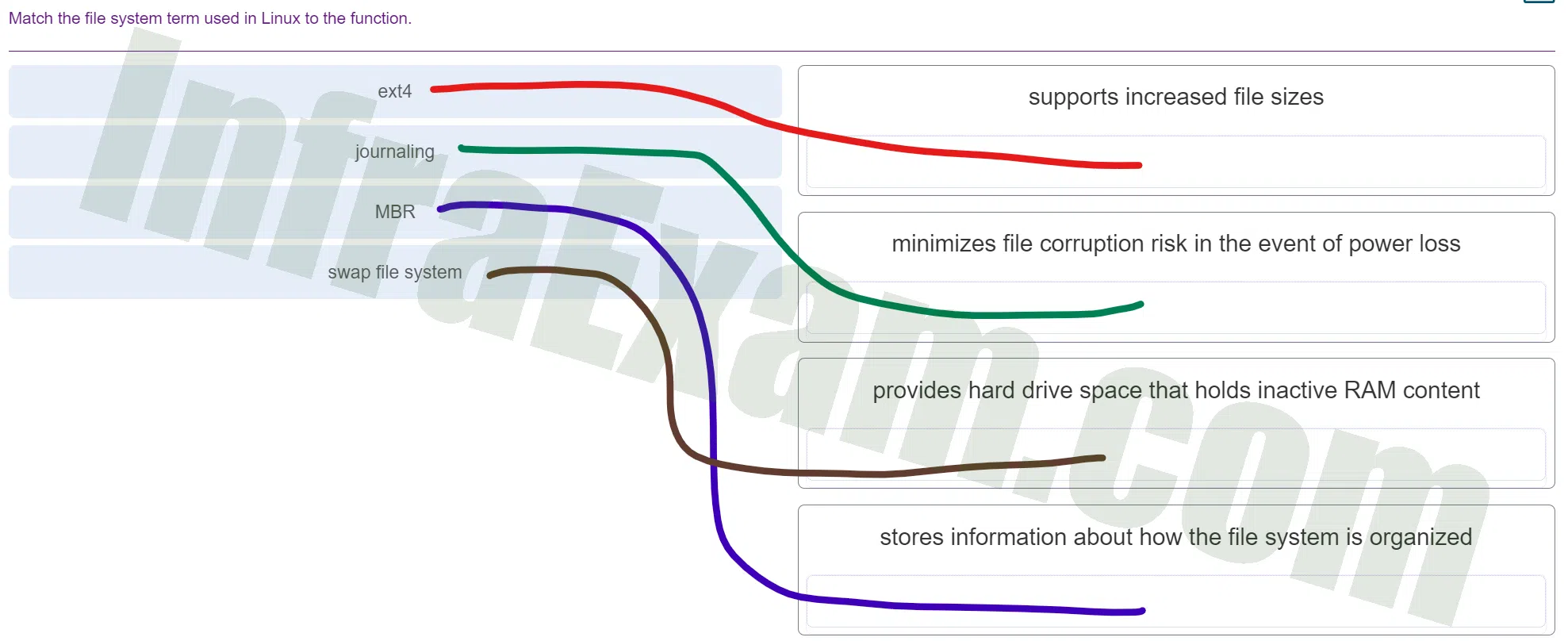
Match the file system term used in Linux to the function.
ITE v8 – IT Essentials A+ 220-1102 Certification Practice Exam Answers 001 - ext4 ==> supports increased file sizes
- journaling ==> minimizes file corruption risk in the event of power loss
- MBR ==> stores information about how the file system is organized
- swap file system ==> provides hard drive space that holds inactive RAM content
Explanation & Hint: The certification objectives list the words "swap file system" as a term to be defined as it relates to the Linux file system. Swap space, swap file, or swap partition are other words for describing hard drive space that is used when the system needs more memory than there is RAM.
-
A company has a guest wireless network available for visitors while on the company premises. A technician has noted that unauthorized users are connecting to this wireless network from outside the premises. Which action can be taken to reduce unauthorized connections to the guest wireless network while enabling visitors to still connect quickly and easily without assistance while on the company premises?
- Disable SSID broadcast.
- Enable MAC address filtering.
- Configure WPA encryption.
- Reduce the radio power level.
Explanation & Hint: Reducing the transmitted radio power to a level that gives network coverage only within the company premises will enable authorized visitors to continue to connect to the guest network connect quickly and easily without assistance, but prevent connection from outside the premises. Enabling MAC address filtering, configuring WPA encryption, and disabling SSID broadcast will prevent unauthorized access to the network. However, these actions will also make it more difficult for visitors to connect when the requirement is for quick and easy access without assistance.
-
What is an example of a web application using multifactor authentication?
- A user logs on to an online shopping website and uses a credit card to make an order.
- A network administrator needs to swipe a card in order to access the corporate server room.
- Teleworkers are required to establish a VPN connection to the company before logging into the company internal web server.
- A user attends a large conference and tries to access Google Gmail at the conference site. The Gmail service sends a verification code to the smartphone of the user.
Explanation & Hint: When multifactor authentication is implemented, two or more different authentication methods are used. Multifactor authentication is often used when accessing online services. For example, when a user wants to access a service, an authenticator application sends a code called a one-time password (OTP) to the registered phone or email address of the user. The user must supply the correct account username and password plus the OTP code to authenticate.
-
Which process in Windows 10 is responsible for assigning system resources and driver installation?
- explorer
- PnP
- winlogon
- services
Explanation & Hint: The PnP (Plug and Play) process is responsible for the assignment of system resources and driver installation in Windows 10.
-
What is the default file system used during a fresh installation of Windows 10?
- NTFS
- HPFS
- FAT16
- FAT32
Explanation & Hint: The default file system for a Windows 10 installation is NTFS.
-
A technician has just purchased a new Windows 10 PC and wants to transfer selected files, folders, profiles, and applications from the old Windows PC. What tool or utility does Microsoft recommend to do this?
- PCmover Express
- Upgrade Assistant
- User State Migration Tool
- Windows Task Manager
Explanation & Hint: PCmover Express is the software tool recommended by Microsoft to automatically moves files, settings, and user profiles from an old PC to a new one. The free version is no longer available, and there is a cost to use it from LapLink.
-
What is the purpose of Windows 10 ReadyBoost?
- It speeds up the Windows 10 start time.
- It enables Windows to treat an external flash device, such as a USB drive, as a hard drive cache.
- It enables the UEFI bios to boot faster.
- It enables the quadruple channels on a 64-bit processor.
Explanation & Hint: Another form of virtual memory is using an external flash device and Windows ReadyBoost to enhance system performance. Windows 10 ReadyBoost enables Windows 10 to treat an external flash device, such as a USB drive, as a hard drive cache.
-
Where are 32-bit program files located in a 64-bit version of Windows 10 Pro?
- c:\Program files
- c:\Program files (x86)
- c:\Windows\system32
- c:\users
Explanation & Hint: In a Windows 10 64-bit operating system, 32-bit program files are located in the c:\programs (x86) folder, while 64-bit programs are located in the c:\Programs folder.
-
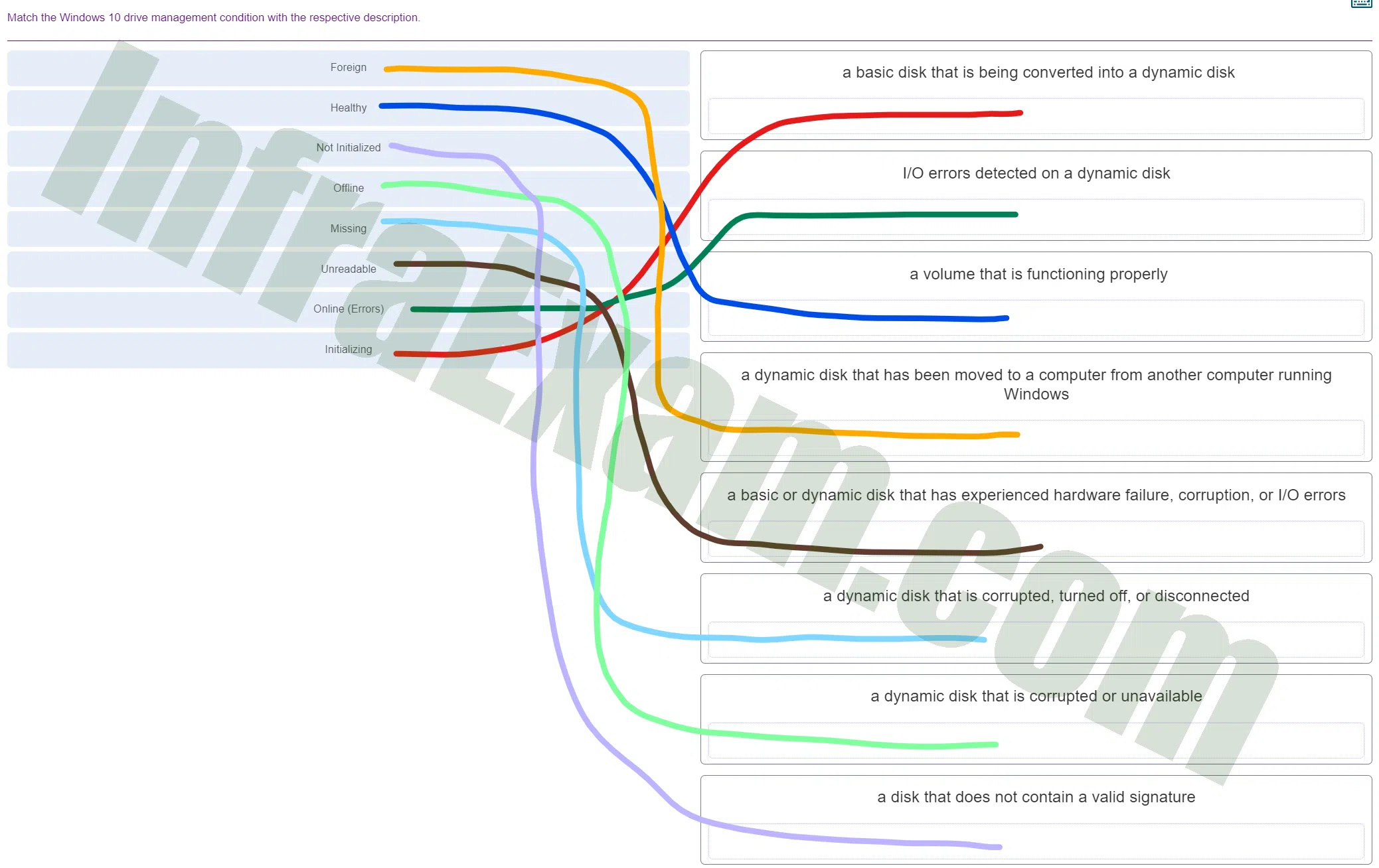
Match the Windows 10 drive management condition with the respective description.
ITE v8 – IT Essentials A+ 220-1102 Certification Practice Exam Answers 002 - Foreign ==> a dynamic disk that has been moved to a computer from another computer running Windows
- Healthy ==> a volume that is functioning properly
- Not Initialized ==> a disk that does not contain a valid signature
- Offline ==> a dynamic disk that is corrupted or unavailable
- Missing ==> a dynamic disk that is corrupted, turned off, or disconnected
- Unreadable ==> a basic or dynamic disk that has experienced hardware failure, corruption, or I/O errors
- Online (Errors) ==> I/O errors detected on a dynamic disk
- Initializing ==> a basic disk that is being converted into a dynamic disk
-
Explanation & Hint: - Foreign: A disk that is marked as ‘Foreign’ usually indicates that it has been moved from another computer running Windows and contains a dynamic volume that is not recognized by the new system. To use the disk, it must be imported or converted.
- Healthy: A ‘Healthy’ disk is one that is functioning properly without any reported errors.
- Not Initialized: A disk that is ‘Not Initialized’ indicates that it does not yet contain a valid signature and cannot be used to store data until it is initialized.
- Offline: An ‘Offline’ disk could be one that is corrupted, turned off, or disconnected. This status indicates that the disk is not accessible by the operating system.
- Missing: A ‘Missing’ disk might be one that is expected to be present (such as in a RAID configuration) but is not detected by the system. This could be due to disconnection or hardware failure.
- Unreadable: An ‘Unreadable’ disk is one where the system cannot read its metadata or data content. This could be due to I/O errors, corruption, or a hardware issue.
- Online (Errors): An ‘Online’ disk with errors indicates that there are I/O errors detected on a dynamic disk. The system can access the disk, but there are issues that need attention.
- Initializing: This status is typically seen when a basic disk is being converted into a dynamic disk or when a new disk is being prepared for use.
- A disk that does not contain a valid signature: This could be due to various issues, including disk corruption or a missing initialization. It might need to be initialized and formatted before use.
-
A user signs up on an application that requires multifactor authentication. The user chooses to register the phone number for the authentication system. Which three items must the user provide in order to authenticate? (Choose three.)
- IP address
- OTP
- password
- email address
- account username
- answer to secret question
Explanation & Hint: Authenticator applications have become a popular method for multifactor authentication. An authenticator application sends a code called a one-time password (OTP) to the registered phone or email address to access the service. To authenticate, the user must supply their account username and password plus the OTP code.
-
A user visits a trusted website. The website sends the user a link via email to the default browser window. When the user clicks on the link, a message appears stating that there is a problem with the website’s security certificate. Why has this occurred?
- the browser has identified it as a malware
- the antivirus has flagged this as a known virus
- the pop-up windows on the browser have been disabled
- the CRLs of the browser have not been updated
Explanation & Hint: Certificate authorities (CAs) issue certificates to domains that contain a public key so that the CA that issued the certificate can validate it because they signed it. The browser can provide the information associated with the certificate when a site is using HTTPS. A certificate error can be addressed by updating the certificate store for the respective browser.
-
Which two statements are true regarding 64-bit processor architecture? (Choose two.)
- It supports a maximum of 4GB RAM memory.
- It supports both 32-bit and 64-bit operating systems.
- It has additional registers for 64-bit address space.
- It has only 64-bit registers.
- It only supports 64-bit operating systems.
Explanation & Hint: The 64-bit processor architecture contains additional 64-bit registers to support 64-bit address space. This allows it to run both 32-bit and 64-bit operating systems and applications.
-
Which two statements are true regarding GPT partitions? (Choose two.)
- They are commonly used in computers with UEFI firmware.
- They are commonly used in computers with BIOS based firmware.
- They store a backup of the partition table.
- They have a maximum partition size of 2TB.
- They store the partition and boot data in one place.
Explanation & Hint: GPT partitions are commonly used in computers with UEFI firmware. They store a backup of the partition table and can support up to 128 partitions. The maximum partition size is 9.4ZB.
-
A technician wishes to use the reset option to repair a Windows 10 installation and chooses the option that will retain the user’s personal files. Which statement is true based on using this option?
- All user files and applications will be restored together with the complete reinstallation of Windows 10.
- Only user files will be restored together with the complete reinstallation of Windows 10.
- All user files and applications will be deleted, and a complete reinstallation of Windows 10 will occur.
- Only corrupt files of the Windows 10 installation will be replaced and repaired.
Explanation & Hint: By using the reset process from within the recovery area, it will remove all apps and programs, change the computer’s settings back to their defaults, and reinstall Windows 10 without removing any user personal data files.
-
A technician wishes to start Windows 10 in safe mode to troubleshoot it. What key or key combination would begin this process?
- recycle power and hold down the F8 key
- recycle power and hold down the del key
- ctrl + F6 and restart
- hold the Shift key and select the Restart option in the Power menu
Explanation & Hint: Hold the Shift key and select the Restart option in the Power menu. This will display the Choose an Option screen. To get the startup settings, select Troubleshoot, then from the next screen, select Advanced options. Inside Advanced options, select Startup settings, then on the next screen, select Restart. The computer will then restart and display the Startup Settings menu from which you can select enable Safe Mode.
-
What does the activation of the Offline Files feature in the Sync Center do in Windows 10?
- It sets up a local file location that will store the files to be synchronized.
- It sets up a sync partnership with the networked file location.
- It sets up manual synchronization.
- It sets up synchronization to occur automatically.
Explanation & Hint: Using Sync Center requires activation of the Offline Files feature. This sets up a local file location that will store the files to be synchronized. It also requires you to set up a sync partnership with the networked file location. Files can be synchronized manually, and synchronization can also be scheduled to occur automatically.
-
What are two advantages of SD-WAN technologies over traditional WAN? (Choose two.)
- network consistency and reliability
- integrated and automated network security features
- independently configured devices instead of centrally
- required to activate platform as a service (PaaS)
- network monitoring and management is not required
Explanation & Hint: SD-WAN technologies offer network consistency and reliability and integrated automated network security features such as built-in firewalls, encryption, sandboxing, and IPS. With SD-WAN, the WAN devices are configured centrally, unlike traditional WAN devices configured independently. PaaS can be implemented on both SD-WANs and traditional WANs. Best practice requires network monitoring and management, which SD-WAN facilitates.
-
A user calls the help desk with the following situation. “My Windows operating system is slowing down more and more each day and it now takes ages to load an application.” What advice should the help desk agent give to the caller?
- Use the Disk Defragmenter to remedy the problem.
- Set the file permissions to read and execute.
- If using Windows, set the idle timeout and screen lock.
- Create a virtual machine with an OS that supports the application.
-
Explanation & Hint: The help desk agent should consider a few factors before providing advice, as the problem of a slowing Windows operating system could be due to various issues. Here’s a breakdown of the suggested solutions and their appropriateness:
- Use the Disk Defragmenter to remedy the problem: This is a viable option, especially if the user has an older system with a mechanical hard drive. Disk fragmentation can lead to slower system performance. Running the Disk Defragmenter can organize the data on the hard drive more efficiently, potentially improving system speed and responsiveness. However, this advice is less relevant for systems with SSDs (Solid State Drives), as defragmentation is not beneficial for SSDs and can actually reduce their lifespan.
- Set the file permissions to read and execute: This advice is unlikely to help with the issue described. File permissions typically impact access to files and security, not system performance. Adjusting permissions would not address the problem of a slowing system or applications taking a long time to load.
- If using Windows, set the idle timeout and screen lock: This suggestion is more related to security and power management rather than system performance. Setting idle timeout and screen lock can help with saving energy and securing the system when it’s not in use, but it won’t address the issue of the system slowing down or applications taking longer to load.
- Create a virtual machine with an OS that supports the application: This is an advanced solution and may not be practical for the average user. It involves setting up a virtual environment with a different operating system, which can be resource-intensive and may not necessarily solve the issue if the underlying problem is related to hardware limitations or system maintenance needs.
Other steps the help desk agent might suggest include:
- Checking for Malware: Run a full system antivirus scan to ensure that the system is not being slowed down by malware.
- Clearing Temporary Files and Cache: Over time, systems can accumulate a lot of temporary files and cache, which can slow down performance. Using a system cleanup tool to remove these files can sometimes improve speed.
- Updating the Operating System and Drivers: Ensure that the latest updates for Windows and device drivers are installed, as these can include performance improvements and bug fixes.
- Checking System Resource Usage: Use the Task Manager to check for any applications or processes that are using excessive system resources (CPU, memory, disk) and address them as necessary.
- Adding More RAM: If the system is consistently running out of memory, adding more RAM can improve performance.
Ultimately, the best advice will depend on the specific details of the user’s situation, such as the age and specifications of their computer, the specific applications they’re using, and other factors.
-
A user calls the help desk with the following situation. “I was updating my operating system software and the power went out before it finished. My PC terminates before the boot process is complete.” What advice should the help desk agent give to the caller?
- Press F8 during the boot process to use the last known good configuration.
- Set the file permissions to read and execute.
- If using Windows, set the idle timeout and screen lock.
- Create a virtual machine with an OS that supports the application.
-
Explanation & Hint: In this scenario, where a power outage interrupted an operating system update and now the PC fails to complete the boot process, the help desk agent should offer specific advice to address potential corruption in the operating system. Here’s an evaluation of the provided suggestions:
- Press F8 during the boot process to use the last known good configuration: This is a relevant and potentially effective suggestion. On many Windows systems, especially older ones, pressing F8 during boot can bring up the Advanced Boot Options menu. From here, selecting “Last Known Good Configuration” might allow the system to boot using the settings and drivers from the last successful startup. This could resolve issues caused by an incomplete update.
- Set the file permissions to read and execute: This advice is not applicable to the problem described. File permissions relate to the security and accessibility of files, not boot process issues or incomplete updates.
- If using Windows, set the idle timeout and screen lock: This suggestion is irrelevant to the problem. Idle timeout and screen lock settings are related to power management and security when the system is running normally, not to issues with booting or incomplete operating system updates.
- Create a virtual machine with an OS that supports the application: This advice does not address the immediate issue of the PC failing to boot due to an interrupted update. Creating a virtual machine is a more advanced step and would require a functioning system.
Additional steps the help desk agent might suggest include:
- Boot into Safe Mode: If the Last Known Good Configuration does not work, booting into Safe Mode is another option. Safe Mode loads Windows with a minimal set of drivers and services. From Safe Mode, the user can attempt repairs or restore the system to a previous point.
- Use Windows Recovery Environment (WinRE): If Safe Mode is not accessible, using the Windows Recovery Environment can be a next step. This can be accessed via a Windows installation media or a recovery drive. From WinRE, the user can access troubleshooting and repair tools like Startup Repair, System Restore, or Command Prompt for more advanced repairs.
- System Restore: If accessible either from Safe Mode or WinRE, performing a System Restore to revert the system back to a previous state before the update can resolve the issue.
- Reinstalling the Operating System: As a last resort, if other repair methods fail, reinstalling Windows might be necessary. This should be done with caution, as it can lead to data loss if not backed up properly.
In all cases, it’s important to guide the user through these steps carefully, especially if they are not familiar with advanced troubleshooting methods.
-
A user calls the help desk with the following situation. “I added a new PC to my LAN. I can ping other devices on my LAN but not any remote devices.” What advice should the help desk agent give to the caller?
- Check the IP address configuration on the new PC, because the default gateway may be incorrect.
- Set the file permissions to read and execute.
- If using Windows, set the idle timeout and screen lock.
- Create a virtual machine with an OS that supports the application.
-
Explanation & Hint: In this case, where a user has added a new PC to their Local Area Network (LAN) and can ping devices within the LAN but not remote devices, the help desk agent should focus on connectivity and network configuration issues. Here’s an evaluation of the provided suggestions:
- Check the IP address configuration on the new PC, because the default gateway may be incorrect: This is a relevant and likely effective suggestion. The inability to connect to remote devices but being able to communicate within the LAN typically indicates an issue with the default gateway configuration. The default gateway is responsible for routing traffic from the local network to external networks (like the internet). The user should verify that the IP address, subnet mask, and especially the default gateway are correctly configured on the new PC. These settings should match the configuration of other devices on the network that can connect to external networks.
- Set the file permissions to read and execute: This suggestion is not relevant to the issue. File permissions relate to the accessibility and security of files within the system and have no bearing on network connectivity problems.
- If using Windows, set the idle timeout and screen lock: This advice is unrelated to the problem at hand. Idle timeout and screen lock settings are for power management and security purposes and do not impact network connectivity or configuration.
- Create a virtual machine with an OS that supports the application: This suggestion does not address the stated problem. Creating a virtual machine is an unrelated process and would not resolve a network connectivity issue on the host machine.
Additional steps the help desk agent might suggest include:
- Checking DNS Settings: If the default gateway is correct, the user should also check the DNS settings. Incorrect DNS settings can prevent access to remote networks and the internet.
- Firewall or Security Software: Verify that no firewall settings or security software on the new PC is blocking outbound connections to remote networks.
- Network Troubleshooter: If using Windows, running the built-in network troubleshooter can help identify and possibly resolve connectivity issues.
- Restarting the Router/Modem: Sometimes, simply restarting the network hardware (router/modem) can resolve connectivity issues.
- Contacting the ISP or Network Administrator: If the problem persists, the user might need to contact their Internet Service Provider or network administrator for further assistance, especially if there are specific configurations or restrictions in place for the network.
The help desk agent should guide the user through these steps, starting with checking the default gateway and then moving on to other potential issues if the problem persists.
-
A technician calls the help desk with the following situation. “I added a new PC to my LAN. I can ping other devices on my LAN but not any remote devices.” What advice should the help desk agent give to the caller?
- Check the IP address configuration on the new PC, because the default gateway may be incorrect.
- Set the file permissions to read and execute.
- If using Windows, set the idle timeout and screen lock.
- Create a virtual machine with an OS that supports the application.
-
Explanation & Hint: For a technician who has added a new PC to a Local Area Network (LAN) and is able to ping devices within the LAN but not remote devices, the most relevant and effective advice would be:
Check the IP address configuration on the new PC, because the default gateway may be incorrect. This is the most appropriate suggestion for the described issue. The inability to reach remote devices while being able to communicate within the LAN often points to an issue with the default gateway setting. The default gateway is essential for directing traffic from the LAN to external networks (like the internet). The technician should verify that the IP address, subnet mask, and default gateway are correctly configured on the new PC. These settings should be consistent with those of other devices on the network that can successfully connect to external networks.
The other suggestions provided are not relevant to the described networking issue:
- Set the file permissions to read and execute: This advice does not apply to network connectivity problems. File permissions are related to the security and accessibility of files on the system and do not influence the ability to connect to remote networks.
- If using Windows, set the idle timeout and screen lock: These settings pertain to security and power management of the system and have no impact on network connectivity or configuration.
- Create a virtual machine with an OS that supports the application: Creating a virtual machine is unrelated to resolving a network connectivity issue on a physical machine. This would not address the problem of being unable to ping remote devices.
If the default gateway setting is correct and the issue persists, the technician might also want to:
- Check DNS Settings: Ensure that DNS settings are configured correctly. Incorrect DNS settings can prevent access to remote networks.
- Review Firewall or Security Software: Confirm that no firewall settings or security software is blocking outbound connections.
- Use Network Diagnostics Tools: Employ network diagnostics tools to further investigate the issue, which could include checking for any routing issues or misconfigurations beyond the local network.
- Restart Network Devices: Sometimes, restarting network devices like routers or modems can resolve connectivity issues.
- Consult Network Documentation or Administrator: If the technician is part of a larger organization, consulting available network documentation or a network administrator might provide insights into specific configurations or restrictions that could be impacting connectivity.
-
A technician calls the help desk with the following situation. “I am trying to save a file to my RAID drive but my system cannot find it.” What advice should the help desk agent give to the caller?
- Check the RAID controller, because it may need to be replaced.
- Set the file permissions to read and execute.
- If using Windows, set the idle timeout and screen lock.
- Create a virtual machine with an OS that supports the application.
-
Explanation & Hint: For a technician experiencing an issue where their system cannot find the RAID drive when trying to save a file, the help desk agent should provide advice that specifically addresses potential problems with RAID configuration or detection. Here’s an evaluation of the provided suggestions:
- Check the RAID controller, because it may need to be replaced: This is a relevant suggestion. If the RAID drive is not being detected, one possible issue could be with the RAID controller. The technician should first check whether the RAID controller is properly recognized by the system in the device manager. If there are any issues or error symbols, updating the driver or reseating the controller (if it’s a hardware component) could be necessary. If these steps do not resolve the issue, the controller might indeed need to be replaced. However, recommending replacement right away might be premature without first attempting other troubleshooting steps.
- Set the file permissions to read and execute: This suggestion is not relevant to the issue. File permissions are related to the security and accessibility of files within the system, not to the detection or configuration of hardware like a RAID drive.
- If using Windows, set the idle timeout and screen lock: This advice is unrelated to the problem. Idle timeout and screen lock settings are for security and power management and do not influence hardware detection or configuration issues.
- Create a virtual machine with an OS that supports the application: This suggestion does not address the immediate problem. The issue is with detecting the RAID drive, not with application support, so creating a virtual machine would not be a relevant solution.
Additional steps the help desk agent might suggest include:
- Check RAID Configuration in BIOS/UEFI: Ensure that the RAID configuration is correctly set up in the system’s BIOS or UEFI settings. Sometimes, settings might revert or change, causing the RAID array to not be recognized correctly.
- Verify Physical Connections: Ensure that all physical connections to the RAID array (such as SATA or power cables) are secure and intact.
- RAID Management Software: If applicable, use RAID management software to check the status of the RAID array. This software can often diagnose issues or provide more detailed information about the state of the RAID drives.
- Check Disk Management: In Windows, use Disk Management to see if the RAID drive is recognized by the operating system but not assigned a drive letter or needs to be initialized.
- Review System Logs: Check system logs for any errors or warnings related to the RAID controller or drives. This can provide clues about what might be going wrong.
- Consult RAID Documentation: If the RAID setup is specific to a particular manufacturer or has unique configurations, consulting the documentation or support resources from the RAID controller or motherboard manufacturer might be helpful.
The help desk agent should guide the technician through these troubleshooting steps, starting with the simplest and most common solutions, before suggesting more complex or costly actions like replacing the RAID controller.
-
A technician calls the help desk with the following situation. “I am trying to save a file to my RAID drive but my system cannot find it.” What advice should the help desk agent give to the caller?
- Check the RAID controller, because it may need to be replaced.
- Check the permissions for this file.
- Create a virtual machine with an OS that supports the application.
- Set the file permissions to read and execute.
-
Explanation & Hint: For a technician who is unable to save a file to a RAID drive because the system cannot find it, the help desk agent should provide advice that directly addresses potential issues with RAID configuration or access. Here’s an evaluation of the suggested courses of action:
- Check the RAID controller, because it may need to be replaced: This is a relevant first step. The RAID controller is crucial for managing the RAID array. The technician should verify if the RAID controller is properly recognized by the system, which can be done through the device manager in Windows. If there are issues or error symbols, they could try updating the driver, reseating the controller (if applicable), or checking for any physical connection issues. If these steps don’t resolve the problem, then considering a replacement could be appropriate, but only after ruling out other less drastic measures.
- Check the permissions for this file: While file permissions can be an issue when accessing or modifying files, they wouldn’t typically prevent a drive from being recognized by the system. If the RAID drive itself is not visible or accessible, then the problem is more likely related to the drive configuration or hardware, rather than specific file permissions.
- Create a virtual machine with an OS that supports the application: This suggestion is not relevant to the issue at hand. The problem described is related to hardware recognition (RAID drive), not software or application compatibility. Creating a virtual machine would not resolve a hardware detection issue.
- Set the file permissions to read and execute: Again, this suggestion is not directly relevant to the problem of the RAID drive not being detected. File permissions affect access to files and directories within a system that is already functioning correctly, and wouldn’t be a factor in the system’s ability to recognize or access a physical drive.
In addition to checking the RAID controller, the help desk agent might advise the technician to:
- Examine RAID Configuration in BIOS/UEFI: Ensure the RAID configuration in the system’s BIOS/UEFI settings is correct. Incorrect settings here can lead to the RAID array not being recognized.
- Inspect Physical Connections: Confirm that all physical connections (SATA, power cables) to the RAID drives are secure.
- Use RAID Management Software: If available, RAID management software can be used to check the status and health of the RAID array.
- Check Disk Management: In Windows, the Disk Management tool can help identify if the RAID drive is visible to the OS but perhaps lacks a drive letter or requires initialization.
- Review System Logs: System logs can provide valuable information about hardware-related errors that might be affecting the RAID drive.
- Consult RAID Documentation and Support: Refer to any specific documentation or support resources from the RAID controller or motherboard manufacturer for additional troubleshooting steps or known issues.
These steps should help diagnose the root cause of the issue and guide towards an appropriate solution.
-
An administrator calls the help desk with the following situation. “An application on my computer is not responding and it is slowing down other applications. What should I do?” What advice should the help desk agent give to the caller?
- Use Task Manager to release system resources from the unresponsive application.
- Check the permissions for this file.
- Create a virtual machine with an OS that supports the application.
- Set the file permissions to read and execute.
-
Explanation & Hint: For an administrator experiencing an issue where an application on their computer is not responding and slowing down other applications, the help desk agent should provide advice to directly address and resolve the application’s unresponsiveness. Here’s an evaluation of the provided suggestions:
- Use Task Manager to release system resources from the unresponsive application: This is the most relevant and effective suggestion. The administrator should open the Task Manager, which can be done by pressing Ctrl + Shift + Esc, or Ctrl + Alt + Del and selecting Task Manager. Within Task Manager, they can find the unresponsive application, right-click on it, and select “End Task” to forcibly close it. This action should release any system resources that the application is using and potentially improve the performance of other applications.
- Check the permissions for this file: This suggestion is not directly relevant to the issue of an application being unresponsive. File permissions typically affect the ability to access or modify a file and are not related to application performance or responsiveness.
- Create a virtual machine with an OS that supports the application: This is a more complex and less immediate solution that might not be necessary. Creating a virtual machine could be considered if there are ongoing compatibility issues with the application, but it doesn’t directly address the immediate problem of the application being unresponsive.
- Set the file permissions to read and execute: Again, this suggestion does not directly address the issue at hand. Setting file permissions impacts access to files but is not related to resolving an unresponsive application.
In addition to using Task Manager to end the unresponsive application, the help desk agent might also advise the administrator to:
- Check for Software Updates: Ensure that the unresponsive application, as well as the operating system, are up to date. Sometimes, performance issues can be resolved with the latest updates.
- Restart the Computer: If the application remains unresponsive and Task Manager is unable to close it, a system restart might be necessary.
- Check System Resource Usage: Use Task Manager to observe if the system’s resources (CPU, memory, disk usage) are being overly taxed, which could be a reason for the slowdown.
- Run a Virus Scan: Occasionally, malware or a virus can cause applications to become unresponsive. Running a virus scan can help rule out this possibility.
- Seek Application-Specific Troubleshooting: If the problem persists, look for troubleshooting steps specific to the problematic application, which might include reinstalling the application or seeking support from the software vendor.
These steps should help the administrator resolve the immediate issue and potentially diagnose any underlying problems causing the application’s unresponsiveness.
-
An administrator calls the help desk with the following situation. “I need to make changes to a file. I can open it but I am unable to make changes.” What advice should the help desk agent give to the caller?
- Check the permissions for this file.
- Create a virtual machine with an OS that supports the application.
- Set the file permissions to read and execute.
- If using Windows, set the idle timeout and screen lock.
-
Explanation & Hint: For an administrator who can open a file but is unable to make changes to it, the help desk agent should provide advice focused on file access and permissions. Here’s an evaluation of the provided suggestions:
- Check the permissions for this file: This is the most relevant and effective suggestion for the described issue. The inability to modify a file despite being able to open it often indicates a permissions issue. The administrator should check the file’s properties to see if they have the necessary permissions to edit it. On Windows, this can be done by right-clicking the file, selecting ‘Properties’, and then navigating to the ‘Security’ tab. Here, they can view and modify the permissions, ensuring they have ‘Write’ access.
- Create a virtual machine with an OS that supports the application: This suggestion is not directly relevant to the issue. The problem described is about modifying a file, not about compatibility or support of the application with the operating system. Creating a virtual machine would be a more complex and likely unnecessary step for resolving a file permission issue.
- Set the file permissions to read and execute: Setting the file permissions to ‘Read and Execute’ specifically might not resolve the issue if the problem is that the user needs ‘Write’ access to make changes to the file. The focus should be on ensuring that the user has ‘Write’ permissions.
- If using Windows, set the idle timeout and screen lock: This advice is unrelated to the problem. Idle timeout and screen lock settings are for security and power management and have no bearing on file access or editing permissions.
In addition to checking and adjusting the file permissions, the help desk agent might also suggest:
- Checking File Ownership: Sometimes, ownership of the file needs to be taken or transferred to the user attempting to make changes. This can also be done from the file’s properties under the ‘Security’ tab.
- Verify If the File is Read-Only: Check if the file is marked as read-only. This can be changed by right-clicking the file, selecting ‘Properties’, and unchecking the ‘Read-only’ attribute.
- Check for Open Instances of the File: Ensure the file is not open in another application or by another user in a shared environment, as this might prevent editing.
- Look for Locked Files: Some applications or system processes might lock a file for editing. Tools like ‘Resource Monitor’ can be used to identify if any process is using the file.
- Consider Network Permissions: If the file is on a network drive, network permissions might also play a role. The administrator should ensure they have the necessary network permissions to edit files on that drive.
- Consult Documentation or Support: If the file is part of a specific application or system, consulting the relevant documentation or support channels might provide more targeted solutions.
These steps should help the administrator identify and resolve the issue preventing them from making changes to the file.
-
An administrator calls the help desk with the following situation. “I need to use an application that is not supported by Windows on my PC.” What advice should the help desk agent give to the caller?
- Create a virtual machine with an OS that supports the application.
- Check the permissions for this file.
- Set the file permissions to read and execute.
- If using Windows, set the idle timeout and screen lock
-
Explanation & Hint: For an administrator needing to use an application that is not supported by Windows on their PC, the help desk agent should provide advice that addresses this compatibility issue. Here’s an evaluation of the provided suggestions:
- Create a virtual machine with an OS that supports the application: This is the most relevant and practical suggestion. If the application is not supported by the current version of Windows on the administrator’s PC, one effective workaround is to create a virtual machine (VM) that runs an operating system which does support the application. Tools like VMware, VirtualBox, or Microsoft’s Hyper-V (if available) can be used to set up a VM. This approach allows the administrator to run the application in an environment where it is supported without having to replace or dual-boot the entire operating system on their PC.
- Check the permissions for this file: This suggestion is not relevant to the issue described. The problem is about application compatibility with the operating system, not about file access or permissions.
- Set the file permissions to read and execute: Similarly, setting file permissions is not relevant to resolving an OS compatibility issue with an application. This suggestion doesn’t address the core problem of the application not being supported by Windows.
- If using Windows, set the idle timeout and screen lock: This advice is unrelated to the problem. Idle timeout and screen lock settings pertain to security and power management and do not impact software compatibility or application support.
In addition to the suggestion of creating a virtual machine, the help desk agent might also advise the administrator to:
- Check for Alternative Versions or Updates: Sometimes, software developers release updates or alternative versions of their applications that are compatible with newer or different operating systems. It’s worth checking if such a version is available for the application in question.
- Consider Compatibility Mode: If the application is supported by an older version of Windows, the administrator can try running it in Compatibility Mode. Right-clicking on the application’s executable file, selecting ‘Properties’, and then navigating to the ‘Compatibility’ tab allows setting the application to run as if it were in an older version of Windows.
- Explore Third-Party Compatibility Layers: For some applications, third-party tools or compatibility layers (like Wine for running certain Windows applications on Linux) might be available. However, this can vary greatly in terms of effectiveness and might require technical expertise to set up.
- Consult the Software Vendor or Community Forums: The software vendor’s support resources or community forums may offer specific advice or workarounds for running the application on unsupported versions of Windows.
These additional steps provide a range of options that the administrator can consider based on the specific circumstances and their technical comfort level.
-
Which statement describes a logical drive?
- It is a section of an extended partition on an MBR. It can be used to separate information for administrative purposes.
- It takes the first 512 bytes on the disk and contains the boot loader, an executable program that allows a user to choose from multiple operating systems.
- It is a standard for the layout of the hard drive partition table using globally unique identifiers. All partitions are primary.
- It is a physical section of a hard disk. It can contain an operating system to boot the system and cannot be subdivided.
-
Explanation & Hint: - “It is a section of an extended partition on an MBR. It can be used to separate information for administrative purposes.” This statement accurately describes a logical drive. In the context of an MBR (Master Boot Record) partitioned disk, you can have a maximum of four primary partitions. However, to overcome this limitation, one of these can be made into an extended partition. This extended partition can then be subdivided into multiple logical drives. Logical drives are not physical partitions themselves but are ways to segment and manage data within an extended partition. They are often used for organizing and managing data separately from the operating system and other primary partitions.
- “It takes the first 512 bytes on the disk and contains the boot loader, an executable program that allows a user to choose from multiple operating systems.” This describes the Master Boot Record (MBR) itself, not a logical drive. The MBR is a special type of boot sector at the very beginning of partitioned computer mass storage devices like fixed disks or removable drives. It contains information about how the logical partitions, containing file systems, are organized on that medium. The MBR also includes a boot loader, which is a small program that loads the operating system.
- “It is a standard for the layout of the hard drive partition table using globally unique identifiers. All partitions are primary.” This statement refers to the GUID Partition Table (GPT). GPT is a modern standard for the layout of the partition table on a physical storage device used in a desktop or server PC, such as a hard disk drive or solid-state drive. Unlike MBR partitioned disks, GPT does not have a limitation on the number of partitions, and all partitions are considered primary, eliminating the need for extended partitions and logical drives.
- “It is a physical section of a hard disk. It can contain an operating system to boot the system and cannot be subdivided.” This is a description of a primary partition. Primary partitions are physical portions of a hard disk drive. They can be used to boot an operating system and are limited in number (up to four per disk in MBR). Unlike logical drives within an extended partition, primary partitions cannot be subdivided into smaller segments within the same partitioning scheme.
In summary, the statement that best describes a logical drive is the first one, which mentions it being a section of an extended partition on an MBR disk, used for administrative purposes.
-
Which statement describes the globally unique identifier (GUID) partition table (GPT)?
- It is a standard for the layout of the hard drive partition table using globally unique identifiers. All partitions are primary.
- It takes the first 512 bytes on the disk and contains the boot loader, an executable program that allows a user to choose from multiple operating systems.
- It is a physical section of a hard disk. It can contain an operating system to boot the system and cannot be subdivided.
- It is used to boot an operating system by default.
-
Explanation & Hint: The statement that describes the Globally Unique Identifier (GUID) Partition Table (GPT) is:
“It is a standard for the layout of the hard drive partition table using globally unique identifiers. All partitions are primary.”
This statement accurately encapsulates the key features of GPT. The GUID Partition Table is a standard for the layout of the partition table on a physical hard drive. Unlike its predecessor, the Master Boot Record (MBR) partitioning scheme, GPT uses globally unique identifiers for partitioning and allows for a virtually unlimited number of partitions. In GPT, all partitions are considered primary, which eliminates the need for extended and logical partitions that are present in MBR.
The other statements refer to different aspects or different types of partitioning:
- “It takes the first 512 bytes on the disk and contains the boot loader, an executable program that allows a user to choose from multiple operating systems.” This describes the Master Boot Record (MBR), not GPT. The MBR is located in the first sector of the storage device and contains the boot loader and the partition table for MBR-partitioned disks.
- “It is a physical section of a hard disk. It can contain an operating system to boot the system and cannot be subdivided.” This statement describes a primary partition, a concept more commonly associated with MBR-partitioned disks. Primary partitions can contain operating systems and are directly bootable.
- “It is used to boot an operating system by default.” This statement is too vague and could apply to various boot-related technologies or configurations, including both MBR and GPT, but it doesn’t specifically describe what GPT is.
-
Which statement describes a dynamic disk?
- It is a type of disk with the ability to create volumes that span across more than one disk even if the unallocated space is noncontiguous.
- It takes the first 512 bytes on the disk and contains the boot loader, an executable program that allows a user to choose from multiple operating systems.
- It is a standard for the layout of the hard drive partition table using globally unique identifiers. All partitions are primary.
- It is often used to organize data storage by subdividing it into as many as 23 logical sections.
-
Explanation & Hint: The statement that describes a dynamic disk is:
“It is a type of disk with the ability to create volumes that span across more than one disk even if the unallocated space is noncontiguous.”
This statement accurately represents the key feature of dynamic disks. Dynamic disks are a type of disk management in Windows that offers more flexibility than basic disks. They allow for the creation of volumes that span multiple disks (spanned and striped volumes), as well as the ability to create volumes that can be extended without the need to restart the system. Dynamic disks can also support RAID-5 volumes and mirrored volumes. One of their notable capabilities is creating a single logical volume that spans across noncontiguous unallocated space on multiple physical disks.
The other statements describe different concepts:
- “It takes the first 512 bytes on the disk and contains the boot loader, an executable program that allows a user to choose from multiple operating systems.” This describes the Master Boot Record (MBR), not a dynamic disk. The MBR is located in the first sector of a storage device and contains the boot loader and partition table for MBR-partitioned disks.
- “It is a standard for the layout of the hard drive partition table using globally unique identifiers. All partitions are primary.” This statement refers to the GUID Partition Table (GPT). GPT is a modern partitioning scheme that uses globally unique identifiers for partitions and does not differentiate between primary and extended partitions.
- “It is often used to organize data storage by subdividing it into as many as 23 logical sections.” This description is more akin to logical partitions in an extended partition within the MBR partitioning scheme. MBR allows up to four primary partitions, or three primary and one extended partition, which can then be subdivided into multiple logical drives (though the number 23 is not a standard limit for logical drives).
-
Which statement describes the globally unique identifier (GUID) partition table (GPT)?
- It is a standard for the layout of the hard drive partition table using globally unique identifiers. All partitions are primary.
- It is often used to organize data storage by subdividing it into as many as 23 logical sections.
- It is used to boot an operating system by default.
- It is a section of an extended partition on an MBR. It can be used to separate information for administrative purposes.
-
Explanation & Hint: The statement that describes the Globally Unique Identifier (GUID) Partition Table (GPT) is:
“It is a standard for the layout of the hard drive partition table using globally unique identifiers. All partitions are primary.”
This statement accurately defines GPT. The GUID Partition Table is a modern partitioning scheme for hard drives, and it uses globally unique identifiers for each partition. One of the key features of GPT is that it does not differentiate between primary and extended partitions, unlike its predecessor, the Master Boot Record (MBR). In GPT, all partitions are treated as primary, which simplifies partition management and allows for a larger number of partitions compared to MBR.
The other statements describe different concepts:
- “It is often used to organize data storage by subdividing it into as many as 23 logical sections.” This is more indicative of logical partitions within an extended partition in an MBR scheme. MBR allows for up to four primary partitions, or three primaries and one extended partition, which can be subdivided into multiple logical drives.
- “It is used to boot an operating system by default.” This statement is somewhat ambiguous and could apply to various boot-related technologies or configurations, including both MBR and GPT, but it doesn’t specifically describe what GPT is.
- “It is a section of an extended partition on an MBR. It can be used to separate information for administrative purposes.” This statement describes a logical drive within an extended partition on an MBR-partitioned disk, not GPT.
-
Which statement describes a dynamic disk?
- It is a type of disk with the ability to create volumes that span across more than one disk even if the unallocated space is noncontiguous.
- It is used to boot an operating system by default.
- It is a physical section of a hard disk. It can contain an operating system to boot the system and cannot be subdivided.
- It is often used to organize data storage by subdividing it into as many as 23 logical sections.
-
Explanation & Hint: The statement that describes a dynamic disk is:
“It is a type of disk with the ability to create volumes that span across more than one disk even if the unallocated space is noncontiguous.”
This statement correctly characterizes dynamic disks. Dynamic disks are a feature in Windows that provides more flexibility than traditional basic disks. They allow for the creation of volumes that can span multiple hard drives (spanned and striped volumes), and these volumes can use noncontiguous space on the disk. Dynamic disks also support other advanced features like mirroring (RAID-1) and RAID-5 volumes, offering more resilience and performance options compared to basic disks.
The other statements do not accurately describe dynamic disks:
- “It is used to boot an operating system by default.” This statement is too vague and could apply to various disk types or configurations. It does not specifically pertain to the defining characteristics of dynamic disks.
- “It is a physical section of a hard disk. It can contain an operating system to boot the system and cannot be subdivided.” This describes a primary partition, typically found on basic disks, rather than a dynamic disk. Primary partitions can contain an operating system and are bootable, but this is not specific to dynamic disks.
- “It is often used to organize data storage by subdividing it into as many as 23 logical sections.” This statement is more indicative of logical drives within an extended partition on a basic disk using the Master Boot Record (MBR) partitioning scheme. It is not a description of dynamic disks.
-
Which statement describes a primary partition?
- It is a physical section of a hard disk. It can contain an operating system to boot the system and cannot be subdivided.
- It is often used to organize data storage by subdividing it into as many as 23 logical sections.
- It is used to boot an operating system by default.
- It is a section of an extended partition on an MBR. It can be used to separate information for administrative purposes.
-
Explanation & Hint: The statement that describes a primary partition is:
“It is a physical section of a hard disk. It can contain an operating system to boot the system and cannot be subdivided.”
This statement correctly defines a primary partition. In the context of disk partitioning, a primary partition is a physical portion of a hard disk. Each primary partition can be used to install and boot an operating system, and it appears to the operating system as a separate disk. A primary partition cannot be subdivided into smaller sections (in contrast to an extended partition, which can be subdivided into logical drives). On a disk using the Master Boot Record (MBR) partitioning scheme, up to four primary partitions can be created.
The other statements refer to different concepts:
- “It is often used to organize data storage by subdividing it into as many as 23 logical sections.” This describes logical drives within an extended partition, not a primary partition. An extended partition can be subdivided into multiple logical drives, which can be used for organizing data.
- “It is used to boot an operating system by default.” While this statement could be true for a primary partition, it’s a bit too vague and general. It doesn’t specifically define what a primary partition is.
- “It is a section of an extended partition on an MBR. It can be used to separate information for administrative purposes.” This statement accurately describes logical drives within an extended partition. Logical drives are subdivisions of an extended partition and are used for data organization and storage, but they are different from primary partitions.
-
Which statement describes formatting?
- It is a process to create a file system in a partition or volume for file storage.
- It is used to boot an operating system by default.
- It is a physical section of a hard disk. It can contain an operating system to boot the system and cannot be subdivided.
- It is often used to organize data storage by subdividing it into as many as 23 logical sections.
-
Explanation & Hint: The statement that describes formatting is:
“It is a process to create a file system in a partition or volume for file storage.”
This statement accurately defines formatting. Formatting is the process of preparing a data storage device such as a hard disk drive, solid-state drive, or USB flash drive for initial use. In the context of a hard drive, formatting involves setting up a file system (like NTFS, FAT32, or exFAT) within a partition or volume. This file system determines how data is stored and retrieved on the disk. Formatting is essential for a storage device to be usable by an operating system for file storage and retrieval.
The other statements do not accurately describe formatting:
- “It is used to boot an operating system by default.” This statement does not pertain to formatting. Booting an operating system is related to how the system starts and loads the OS, not to the process of formatting a storage device.
- “It is a physical section of a hard disk. It can contain an operating system to boot the system and cannot be subdivided.” This describes a primary partition, not the process of formatting. A primary partition is a segment of a hard disk that can be used to install and boot an operating system.
- “It is often used to organize data storage by subdividing it into as many as 23 logical sections.” This statement refers to logical drives within an extended partition, which is a method of organizing data storage on a disk. It is not a description of the formatting process.
-
Which statement describes the active partition?
- It is used to boot an operating system by default.
- It is often used to organize data storage by subdividing it into as many as 23 logical sections.
- It is a physical section of a hard disk. It can contain an operating system to boot the system and cannot be subdivided.
- It is a section of an extended partition on an MBR. It can be used to separate information for administrative purposes.
-
Explanation & Hint: The statement that describes the active partition is:
“It is used to boot an operating system by default.”
This statement accurately defines an active partition. In the context of disk partitioning, especially with Master Boot Record (MBR) partitioning, the active partition is the one that the computer’s BIOS identifies as the partition to boot the operating system from. It is typically marked as ‘active’ in the disk partitioning utility. This designation tells the system’s startup program which partition contains the operating system’s boot loader, which is then used to start the operating system.
The other statements refer to different concepts:
- “It is often used to organize data storage by subdividing it into as many as 23 logical sections.” This statement describes logical drives within an extended partition, not an active partition. An extended partition can be subdivided into multiple logical drives, which can be used for organizing data storage.
- “It is a physical section of a hard disk. It can contain an operating system to boot the system and cannot be subdivided.” This statement describes a primary partition. A primary partition can indeed contain an operating system and be made bootable, but this statement on its own doesn’t specifically denote the active partition used for booting.
- “It is a section of an extended partition on an MBR. It can be used to separate information for administrative purposes.” This statement describes a logical drive within an extended partition, not the active partition. These logical drives are used for organizing and storing data but are not typically used for booting an operating system.
-
Which statement describes a recovery partition?
- It is a section of the disk, that is inaccessible to the user, containing an image that can be used to restore the computer to its original configuration.
- It is used to boot an operating system by default.
- It is a physical section of a hard disk. It can contain an operating system to boot the system and cannot be subdivided.
- It is often used to organize data storage by subdividing it into as many as 23 logical sections.
-
Explanation & Hint: The statement that describes a recovery partition is:
“It is a section of the disk, that is inaccessible to the user, containing an image that can be used to restore the computer to its original configuration.”
This statement accurately defines a recovery partition. A recovery partition is a partition on the hard disk of a computer that contains system recovery data, typically a saved image of the operating system in its original configuration. It’s often created by the computer manufacturer and is used to restore the computer to the state it was in when it left the factory. This can be useful for troubleshooting and fixing problems with the operating system. Generally, the recovery partition is hidden and not directly accessible under normal use to prevent accidental modification or deletion.
The other statements refer to different concepts:
- “It is used to boot an operating system by default.” This statement is more applicable to an active or primary partition, which contains the boot loader or operating system files necessary to start the system.
- “It is a physical section of a hard disk. It can contain an operating system to boot the system and cannot be subdivided.” This describes a primary partition. A primary partition can hold an operating system and is used to boot the system, but it does not specifically describe a recovery partition.
- “It is often used to organize data storage by subdividing it into as many as 23 logical sections.” This statement describes logical drives within an extended partition, which is a way to organize data storage on a disk. It is not a description of a recovery partition.
-
Which statement describes the active partition?
- It is used to boot an operating system by default.
- It is often used to organize data storage by subdividing it into as many as 23 logical sections.
- It is a physical section of a hard disk. It can contain an operating system to boot the system and cannot be subdivided.
- It is a standard for the layout of the hard drive partition table using globally unique identifiers. All partitions are primary.
-
Explanation & Hint: The statement that describes the active partition is:
“It is used to boot an operating system by default.”
This statement correctly identifies the purpose of an active partition. In disk partitioning, particularly in systems using the Master Boot Record (MBR) scheme, the active partition is the one that the computer’s BIOS (Basic Input/Output System) or UEFI (Unified Extensible Firmware Interface) looks to for the boot loader. The boot loader is a small program that starts the operating system’s loading process. In most cases, only one partition is marked as active, and this is typically the partition where the operating system is installed.
The other statements describe different concepts:
- “It is often used to organize data storage by subdividing it into as many as 23 logical sections.” This statement refers to logical drives within an extended partition, not to an active partition. Logical drives are a way to organize data storage and are a feature of the MBR partitioning scheme where there are limitations on the number of primary partitions.
- “It is a physical section of a hard disk. It can contain an operating system to boot the system and cannot be subdivided.” This describes a primary partition. A primary partition can indeed contain an operating system and be bootable, but this statement does not specifically address the concept of an active partition.
- “It is a standard for the layout of the hard drive partition table using globally unique identifiers. All partitions are primary.” This statement describes the GUID Partition Table (GPT), which is a different partitioning scheme from MBR and does not use the concept of an active partition in the same way. In GPT, all partitions are primary and there is no specific ‘active’ flag as in MBR.
-
A user has completed a project and wants to erase or delete one or more files from a Windows directory. What is the best Windows command to select to do the job?
- del
- bootrec
- ipconfig
- diskpart
- history
-
Explanation & Hint: The best Windows command to use for erasing or deleting one or more files from a directory is
del.The
delcommand in Windows is used specifically for deleting files. It can be used to delete one file, multiple files, or even a group of files matching a specified pattern.The other commands have different purposes:
bootrec: This is used to repair the boot process for Windows. It’s useful in fixing boot-related issues but not for deleting files.ipconfig: This command is used to display and manage the network configuration on a Windows computer, particularly IP addressing. It’s not used for file management.diskpart: While this is a utility for managing disk partitions, it’s more powerful and complex and is generally used for tasks like creating, deleting, or resizing disk partitions, not for individual file operations.history: In the context of Windows Command Prompt, there isn’t a built-inhistorycommand. In PowerShell,historyshows a history of the commands entered during the current session, but it’s not for file deletion.
Therefore, for deleting files,
delis the appropriate command.
-
A user is trying to repair, prepare, and fix Windows images and the recovery image within an installation of the operating system. What is the best Windows command to select to do the job?
- DISM
- diskpart
- bootrec
- format
- path
-
Explanation & Hint: The best Windows command for repairing, preparing, and fixing Windows images, including the recovery image within an installation of the operating system, is
DISM.DISMstands for Deployment Image Servicing and Management. It is a command-line tool that is used for a variety of functions related to Windows images, including:- Repairing and preparing Windows images, including those used for Windows Setup, Windows Recovery Environment, and Windows PE.
- Managing features within images.
- Enabling or disabling Windows features.
The other commands have different purposes:
diskpart: This command is used for disk partition management, such as creating, deleting, or formatting partitions. It’s not used for managing Windows images.bootrec: This tool is used to repair the boot configuration data (BCD). It’s useful in fixing boot-related issues but is not for managing Windows images.format: This command is used to format a disk drive to a particular file system, wiping all data on the drive. It does not serve the purpose of repairing or managing Windows images.path: Thepathcommand is used to set or display the command path in the command line environment, which isn’t related to image management or repair.
Therefore, for the tasks related to Windows image and recovery environment,
DISMis the appropriate command.
-
A user is deleting old files and wants to see all files in the current directory. What is the best Windows command to select to do the job?
- dir
- bootrec
- ipconfig
- diskpart
- exit
-
Explanation & Hint: The best Windows command for a user who wants to see all files in the current directory is
dir.The
dircommand in Windows Command Prompt lists all files and directories in the current directory. It’s a useful command for quickly viewing the contents of a directory, including file and folder names, their sizes, and the date and time they were last modified.The other commands serve different purposes:
bootrec: This is used for troubleshooting and repairing issues with the boot process in Windows. It’s not used for listing files or directories.ipconfig: This command displays the network configuration, including IP addresses, on a Windows computer. It’s unrelated to file management.diskpart: This is a command-line utility for disk partition management, such as creating, deleting, or formatting partitions. It does not list files in a directory.exit: This command is used to close the Command Prompt window or end the current script or batch file. It’s not for viewing files or directories.
Thus, for viewing all files in the current directory,
diris the appropriate command.
-
A user suspects issues with the MBR and is trying to repair it. What is the best Windows command to select to do the job?
- bootrec
- diskpart
- ipconfig
- format
- net user
-
Explanation & Hint: The best Windows command for a user trying to repair issues with the Master Boot Record (MBR) is
bootrec.The
bootreccommand is a utility available in Windows Recovery Environment (WinRE) that is used specifically for troubleshooting and repairing boot-related issues, including problems with the Master Boot Record (MBR), Boot Configuration Data (BCD), and boot sector. It offers various options like/FixMbr,/FixBoot, and/RebuildBcdto handle different boot issues.The other commands serve different purposes:
diskpart: This is a command-line utility for disk partition management, such as creating, deleting, or formatting partitions. While it can be used to manage partitions, it’s not specifically for repairing the MBR.ipconfig: This command is used to display the network configuration, such as IP addresses, on a Windows computer. It’s unrelated to boot or MBR issues.format: Theformatcommand is used to format a disk to a specific file system, erasing all data on it. This command does not repair the MBR and would actually remove it if used on the boot drive.net user: This command is for managing user accounts on Windows. It’s used to add, remove, or modify user accounts and has no relation to boot issues or the MBR.
Therefore, for repairing the MBR,
bootrecis the appropriate command.
-
A user notices that the PC behaves a bit differently from the organization group policies. The user believes that the group policy settings may have been applied incorrectly and wants to verify the settings. What is the best Windows command to select to do the job?
- gpresult
- tasklist
- DISM
- sfc
- cls
-
Explanation & Hint: The best Windows command for a user who wants to verify and check the group policy settings that have been applied to their PC is
gpresult.The
gpresultcommand is a Group Policy tool that provides information about the group policies that are currently applied to a system for the user or computer. It can be used to display both the Group Policy settings and the Resultant Set of Policy (RSoP) for a user or a computer. This command is especially useful for troubleshooting group policy application issues.The other commands serve different purposes:
tasklist: This command displays a list of currently running processes on the system. It is useful for seeing what programs are running but does not provide information about group policies.DISM: Deployment Image Servicing and Management (DISM) is a command-line tool used to service and prepare Windows images, including those used for Windows PE, Windows Recovery Environment, and Windows Setup. It’s not related to group policy.sfc: The System File Checker (sfc) is a utility that scans and repairs corrupted system files in Windows. While it’s a valuable tool for system integrity, it does not provide information about group policy settings.cls: This command clears the command prompt screen. It has no relation to group policies or system configuration.
Therefore, for verifying group policy settings,
gpresultis the appropriate command.
-
A user cannot reach a familiar web server and wants to verify connectivity by sending echo-request messages to the server in the hope that the server will respond to confirm connectivity. What is the best Windows command to select to do the job?
- ping
- tasklist
- DISM
- sfc
- recover
-
Explanation & Hint: The best Windows command for a user who wants to verify connectivity to a web server by sending echo-request messages and hoping for a response is
ping.The
pingcommand is used to test the reachability of a host on an IP network and to measure the round-trip time for messages sent from the originating host to a destination computer. It operates by sending Internet Control Message Protocol (ICMP) echo request packets to the target host and listening for ICMP echo response replies. This tool is commonly used for network troubleshooting to confirm connectivity and assess response times.The other commands have different purposes:
tasklist: This command displays a list of currently running processes on the system. It is used to see what programs are running but does not test network connectivity.DISM: Deployment Image Servicing and Management (DISM) is a command-line tool used for servicing and preparing Windows images. It’s unrelated to network connectivity testing.sfc: The System File Checker (sfc) is a utility that scans for and restores corrupted Windows system files. While important for system integrity, it does not help with network connectivity issues.recover: This command is used to recover readable data from a bad or defective disk. It’s not used for network testing or connectivity verification.
Therefore, for verifying connectivity to a web server, the
pingcommand is the most suitable choice.
-
A user has completed a project and wants to erase or delete one or more files from a Windows directory. What is the best Windows command to select to do the job?
- del
- tasklist
- DISM
- sfc
- history
-
Explanation & Hint: The best Windows command for a user who has completed a project and wants to erase or delete one or more files from a Windows directory is
del.The
del(ordelete) command in Windows is specifically used for deleting files from a directory. It can be used to delete one file, multiple files, or a group of files matching a specified pattern. It’s a straightforward and direct way to remove files that are no longer needed.The other commands serve different purposes:
tasklist: This command displays a list of currently running processes on the system. It’s useful for monitoring system activities but is not related to file deletion.DISM: Deployment Image Servicing and Management (DISM) is a command-line tool used for servicing and preparing Windows images. This tool is not used for deleting files.sfc: The System File Checker (sfc) is a utility that scans and repairs corrupted system files in Windows. While it’s important for system maintenance, it doesn’t have a function for deleting user files.history: In the context of Windows Command Prompt, there isn’t a built-inhistorycommand. In PowerShell,historyshows a history of the commands entered during the current session, but it’s not for file deletion.
So, for the purpose of deleting files, the
delcommand is the appropriate choice.
-
A user notices errors for some Windows operations and suspects that some system files might be corrupted. The user wants to scan and verify the integrity of all system files and replace corrupted files with correct versions. What is the best Windows command to select to do the job?
- sfc
- tasklist
- DISM
- shutdown
- path
-
Explanation & Hint: The best Windows command for a user who wants to scan and verify the integrity of all system files, and replace corrupted files with correct versions, is
sfc.The
sfccommand stands for System File Checker. It’s a utility in Microsoft Windows that allows users to scan for and restore corruptions in Windows system files. The most common use of this command issfc /scannow, which scans the integrity of all protected system files and replaces incorrect versions with genuine, correct Microsoft versions.The other commands have different purposes:
tasklist: This command displays a list of currently running processes on the system. It’s used for monitoring system activities but does not deal with system file integrity.DISM: Deployment Image Servicing and Management (DISM) is a command-line tool used for servicing and preparing Windows images, including the Windows Recovery Environment, Windows Setup, and Windows PE. While it can repair the Windows image, it’s not primarily used for scanning and fixing individual system file corruptions likesfc.shutdown: This command is used to shut down or restart the computer. It has no functionality for scanning or repairing system files.path: Thepathcommand is used to set or display the command path in the command line environment, which is not related to system file integrity or repair.
Therefore, for scanning and repairing corrupted system files,
sfcis the appropriate command.
-
A user wants to copy a group of files from one Windows directory to another. What is the best Windows command to select to do the job?
- robocopy
- tasklist
- DISM
- sfc
- regsrv32
-
Explanation & Hint: The best Windows command for a user who wants to copy a group of files from one directory to another is
robocopy.robocopy(short for “Robust File Copy”) is a command-line directory and file replication command. It is designed for reliable copy or mirroring of directories or directory trees. It has many options to control its operation, including the ability to copy file attributes, NTFS permissions, owner information, and timestamps.robocopyis particularly well-suited for copying a large number of files and for copying files over a network.The other commands serve different purposes:
tasklist: This command displays a list of currently running processes on the system. It’s not used for file management or file copying tasks.DISM: Deployment Image Servicing and Management (DISM) is a command-line tool used for servicing and preparing Windows images. This tool is not used for copying files.sfc: The System File Checker (sfc) is a utility that scans and repairs corrupted system files in Windows. It’s used for system maintenance and repair, not for file copying.regsvr32: This command is used to register and unregister DLL (Dynamic Link Library) files in the Windows registry. It is unrelated to file copying or directory management.
Therefore, for the purpose of copying a group of files from one directory to another,
robocopyis the most suitable command.
| IT Essentials 8 | |
| IT Essentials 8 Final - Mid-term - Cert | |
| Chapter 1 -9 Skills Assessment | NA |
| Chapter 10 - 14 Skills Assessment | NA |
| Practice Final Exam Answers Ch 1 - 9 | Online Test |
| Practice Final Exam Answers Ch 10 - 14 | Online Test |
| Final Exam Answers Ch 1 - 9 | Online Test |
| Final Exam Answers Ch 10 - 14 | Online Test |
| Final Exam Composite Answers Ch 1 - 14 | Online Test |
| A+ 220-1001 | Online Test |
| A+ 220-1002 | Online Test |