ITE 8 – IT Essentials ( Version 7.0) – IT Essentials 8.0 Final Exam Ch 1 – 14 Answers 2025 Full 100%
ITE 8 – IT Essentials 8 Final Exam – Composite Chapter 1 – 14 Exam Answers 2025 Full 100%
This is Cisco Netacad ITE v7 – IT Essentials (Version 7.00) – IT Essentials 7.02 Final Exam Ch 1 – 14 Exam Answers – Final Exam – Composite (Chapters 1-14) 2025 and IT Essentials (Version 8.0) – IT Essentials 8.0 Final Exam Ch 1 – 14 Exam Answers 2023 2024.
| IT Essentials 8 | |
| IT Essentials 8 Final - Mid-term - Cert | |
| Chapter 1 -9 Skills Assessment | NA |
| Chapter 10 - 14 Skills Assessment | NA |
| Practice Final Exam Answers Ch 1 - 9 | Online Test |
| Practice Final Exam Answers Ch 10 - 14 | Online Test |
| Final Exam Answers Ch 1 - 9 | Online Test |
| Final Exam Answers Ch 10 - 14 | Online Test |
| Final Exam Composite Answers Ch 1 - 14 | Online Test |
| A+ 220-1001 | Online Test |
| A+ 220-1002 | Online Test |
ITE 8.01 – IT Essentials (Version 8.0) – IT Essentials 8.0 Final Exam Ch 1 – 14 2025 Full 100%
-
When a new motherboard is being installed, between which two components must thermal compound be applied? (Choose two.)
- CPU
- RAM
- chassis
- heat sink
- chipset
- motherboard
Answers Explanation & Hints: You must apply thermal compound between the new CPU and the heat sink/fan assembly to avoid overheating the CPU. The thermal paste helps to conduct heat from the CPU to the heat sink.
-
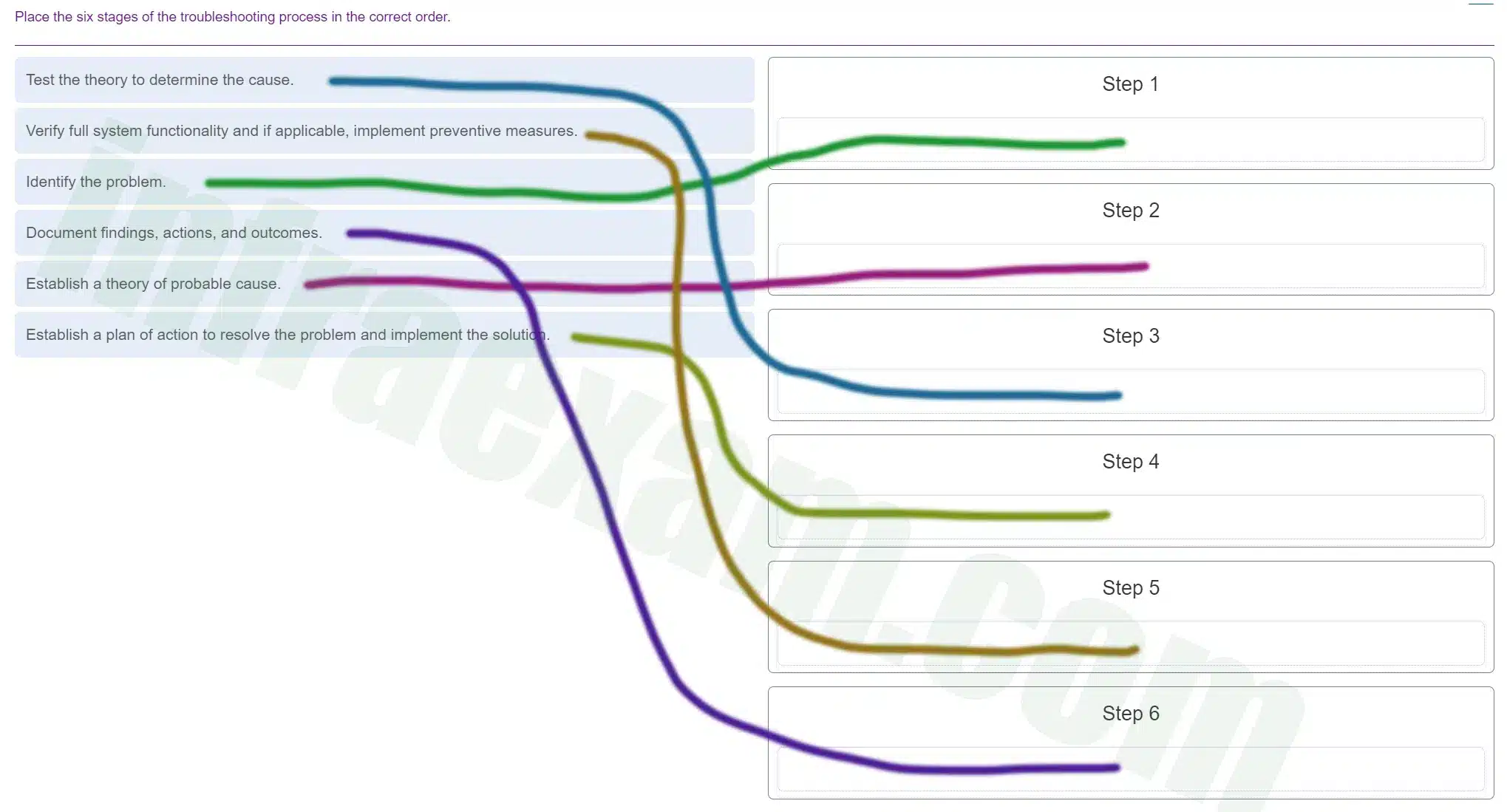
Place the six stages of the troubleshooting process in the correct order.
ITE v8.0 – IT Essentials ( Version 8.0) – IT Essentials 8 Final Exam 1 – 14 Answers 001 -
Explanation & Hint: The image you’ve uploaded appears to show a flowchart or a process diagram that’s meant to be ordered correctly. Since I can’t directly read the text or interpret the flow lines in the image, I can’t provide the exact order. However, I can tell you that a typical troubleshooting process usually follows these steps in order:
- Identify the problem. Determine what is not functioning correctly.
- Establish a theory of probable cause. List the possible reasons why the system is not working correctly.
- Test the theory to determine the cause. Once the theory is established, test to see if it’s the correct cause of the problem.
- Establish a plan of action to resolve the problem and implement the solution. Develop a strategy to fix the issue and then implement the solution.
- Verify full system functionality and if applicable, implement preventive measures. Make sure that the system is working correctly after the fix and take measures to prevent future issues.
- Document findings, actions, and outcomes. Record the problem and the steps taken to resolve it for future reference.
To properly assist you in verifying the order, you would need to transcribe the text from the image or describe the connections between the steps.
-
-
A technician is explaining the differences between inkjet printers and laser printers to a customer. Which two comparisons should the technician make? (Choose two.)
- Inkjet printers are less expensive as an initial purchase than laser printers.
- A laser printer is significantly slower than an inkjet printer.
- Both laser and inkjet printers produce poor quality images.
- The laser printer output is dry after printing, but an inkjet printer may still have wet ink on the paper after printing.
- Inkjet printers use plain paper to make economical prints, but laser printers require more expensive thermal paper.
-
Explanation & Hint: When comparing inkjet and laser printers, the technician should focus on accurate and relevant differences that would help a customer make an informed decision. Here are two correct comparisons from the options provided:
- Inkjet printers are less expensive as an initial purchase than laser printers. This is generally true, as inkjet printers typically have a lower upfront cost compared to laser printers.
- The laser printer output is dry after printing, but an inkjet printer may still have wet ink on the paper after printing. Laser printers use toner and a heat process to fuse the toner to the paper, resulting in a dry print immediately after printing. Inkjet printers use liquid ink, which can sometimes require a short time to dry fully and may smudge if handled immediately after printing.
The other comparisons provided contain inaccuracies:
- A laser printer is significantly slower than an inkjet printer. This is typically not true; laser printers are generally faster, especially for larger volume printing jobs.
- Both laser and inkjet printers produce poor quality images. Both types of printers can produce high-quality images, especially if they are higher-end models. Quality can vary based on the printer model and the type of ink or toner used.
- Inkjet printers use plain paper to make economical prints, but laser printers require more expensive thermal paper. This is incorrect. Laser printers do not require thermal paper; they also use plain paper. Thermal paper is specifically used with thermal printers, which are a different type of printing technology.
-
Which three components are typically found in laser printer maintenance kits? (Choose three.)
- fuser assembly
- primary corona
- pickup rollers
- transfer rollers
- secondary corona
- paper trays
Answers Explanation & Hints: Laser printer maintenance kits typically contain components that wear and can be installed with minimal disassembly of the printer. Corona wires are internal components that would require a trained technician to replace. Paper trays are components that are not typically replaced during maintenance, but would be replaced any time if damaged.
-
Which three features can be configured in the BIOS settings to secure a computer? (Choose three.)
- MAC filtering
- drive encryption
- TPM
- file encryption
- TKIP key
- passwords
Answers Explanation & Hints: Passwords, drive encryption, and TPM are BIOS configurable security features. File encryption, TKIP key, and MAC filtering are security features not configured within BIOS.
-
What are two safety hazards when dealing with laser printers? (Choose two.)
- high voltage
- hot components
- heavy metals
- proprietary power bricks
- unwieldy card cages
Answers Explanation & Hints: Laser printers require high voltage when initially powered on and to charge the drum in preparation for writing data to the drum. This high voltage requirement is why most laser printers are not normally connected to a UPS. A laser printer also has a fuser assembly used to apply heat and pressure to the toner to permanently attach it to the paper. The laser printer must be unplugged and the fuser assembly must be allowed to cool before working inside the printer.
-
What three values must be added to the IPv4 properties of a NIC in order for a computer to have basic connectivity with the network? (Choose three.)
- subnet mask
- DHCP server address
- domain name
- default gateway
- speed and duplex
- IP address
Answers Explanation & Hints: The IP address, subnet mask, and default gateway address values should be added to the NIC properties in order for the computer to have basic network connectivity. This can be done either statically or dynamically with DHCP. An additional value that should be present if the computer is to be used to connect to the Internet is the DNS server value. A computer automatically attempts to locate a DHCP server if configured to do so. A DHCP server address is not used. Finally, NAT is configured on a router, not on a computer host, and speed and duplex settings are NIC hardware settings and not IPv4 properties of the NIC.
-
After a technician tests a theory of probable causes, what two actions should the technician take if the testing did not identify an exact cause? (Choose two.)
- Establish a new theory of probable causes.
- Randomly replace components one at a time until the problem is solved.
- Document each test tried that did not correct the problem.
- Verify full system functionality.
- Test all remaining possible causes starting with the most complex.
Answers Explanation & Hints: If the exact cause of the problem has not been determined after you have tested all your theories, establish a new theory of probable causes and test it.
-
What two motherboard components control the system boot operations? (Choose two.)
- BIOS chip
- UEFI chip
- Northbridge chip
- Southbridge chip
- CPU
Answers Explanation & Hints: System boot services are provided by the motherboard BIOS and UEFI chips.
-
What are two types of wired high-speed Internet connections? (Choose two.)
- cable
- satellite
- cellular
- DSL
- dial-up
Answers Explanation & Hints: Cable and DSL Internet technologies both use physical cabling to provide an Internet connection to a residence or a small business. Although dial-up is a wired technology, it does not provide a high-speed Internet connection. Satellite and cellular connections provide a wireless Internet connection.
-
In what two situations would UDP be better than TCP as the preferred transport protocol? (Choose two.)
- when applications need to guarantee that a packet arrives intact, in sequence, and unduplicated
- when a faster delivery mechanism is needed
- when delivery overhead is not an issue
- when applications do not need to guarantee delivery of the data
- when destination port numbers are dynamic
Answers Explanation & Hints: UDP is a very simple transport layer protocol that does not guarantee delivery. Devices on both ends of the conversation are not required to keep track of the conversation. UDP is used as the transport protocol for applications that need a speedy, best-effort delivery.
-
Which two laptop components are considered replaceable by the customer. (Choose two.)
- battery
- integrated card reader
- mini-PCIe module
- RAM
- display
Answers Explanation & Hints: Customer-replaceable units (CRUs) do not typically require a lot of technical skill to replace. RAM and a battery are two examples of a CRU. In contrast, a field-replaceable unit (FRU), such as a display, motherboard, keyboard, or touchpad, commonly requires a technician to install.
-
A user wants to synchronize some apps, movies, music, and ebooks between mobile devices. What are the two types of connections used to synchronize this type of data? (Choose two.)
- cellular
- Wi-Fi
- USB
- Bluetooth
- NFC
Answers Explanation & Hints: Because of the amount of data transferred during video synchronization, synchronization occurs through either a Wi-Fi connection or a wired USB connection.
-
A technician is upgrading an ATX motherboard with another ATX motherboard. Which component might be affected by this and need to be upgraded and bought as an additional purchase?
- BIOS
- chipset
- CMOS battery
- CPU
- PCIe adapter
Answers Explanation & Hints: The motherboard, CPU, and power supply must be compatible.
-
Which memory module used to hold instructions for booting a PC and loading the OS, but is still used on adapters even though the memory contents cannot be changed?
- RAM
- ROM
- cache
- main memory
Answers Explanation & Hints: ROM stands for read-only memory.
-
Which negative environmental factor does cleaning the inside of a computer reduce?
- dust
- EMI
- rust
- ESD
Answers Explanation & Hints: Accumulated dust inside the computer can prevent the flow of air and can hinder cooling.
-
What is a recommended procedure to follow when cleaning computer components?
- Remove the CPU before cleaning.
- Blow compressed air on cooling fans so that they will spin when dust is being removed.
- Use window cleaner on LCD screens.
- Hold cans of compressed air upright while spraying.
Answers Explanation & Hints: When using compressed air, keep the can upright to prevent the fluid from leaking onto computer components.
-
On the production floor, a furniture plant has laptops for process monitoring and reporting. The production floor environment is around 80 degrees Fahrenheit (27 degrees Celsius). The humidity level is fairly high around 70 percent. Fans are mounted in the ceiling for air circulation. Wood dust is prevalent. Which condition is most likely to adversely affect a laptop that is used in this environment?
- the temperature
- the humidity
- the air flow
- the dust
Answers Explanation & Hints: Most laptops are created to be tolerant of a wide range of humidity levels and room temperatures. Dust, however, can cause overheating and failures.
-
What would happen if a PC that contains a power supply that does not automatically adjust for input voltage is set to 230 volts and attaches to an outlet in the United States?
- The power supply would explode.
- The PC would not turn on.
- The PC would display an error code.
- The PC would emit a series of beeps.
Answers Explanation & Hints: In the United States, the wall outlet electrical power is standardized at 120 volts AC.
-
A student is helping a friend with a home computer that can no longer access the Internet. Upon investigation, the student discovers that the computer has been assigned the IP address 169.254.100.88. What could cause a computer to get such an IP address?
- static IP addressing with incomplete information
- interference from surrounding devices
- reduced computer power supply output
- unreachable DHCP server
Answers Explanation & Hints: When a PC does not have a static IP address or cannot pick one up from a DHCP server, Windows will automatically assign the PC an IP address using APIPA, that uses the range of addresses 169.254.0.0 to 169.254.255.255.
-
What is the purpose of RAID adapters?
- to allow older PCI technology expansion slots to be used
- to provide enhanced audio and graphic capabilities
- to connect multiple storage devices for redundancy or speed
- to connect peripheral devices to a PC to improve performance
Answers Explanation & Hints: RAID 0 allows “striping” or writing data across two hard drives, but provides no redundancy. The other RAID versions provide redundancy.
-
A technician is troubleshooting a computer that is experiencing hardware failure detected by the BIOS. What is one way this failure is indicated?
- The computer automatically boots into Safe Mode and displays a warning on the screen.
- The screen flashes with a red background and displays a warning message.
- The computer emits a pattern of beeps indicating the failing device.
- The computer returns an error message that indicates the I/O address of the failing device.
Answers Explanation & Hints: Beep codes are a result of POST and these vary between computer vendors based on what BIOS is installed.
-
Which statement is true about laptops?
- Most of the internal components that are designed for laptops cannot be used for desktops.
- Laptop motherboards have standard form factors.
- Laptops use fewer components than desktops use.
- Laptop CPUs do not use cooling devices.
Answers Explanation & Hints: Laptop internal components are designed with a small form factor and are proprietary. Although a laptop CPU uses less power, it needs a cooling device (heat sink and fan).
-
What is a characteristic of DDR SDRAM?
- It transfers data twice per clock cycle compared to once per clock cycle for SDRAM.
- DDR SDRAM modules have double the number of pins of SDRAM memory modules.
- It is dynamic memory whereas SDRAM is static memory.
- It operates at double the voltage of SDRAM memory.
Answers Explanation & Hints: DDR SDRAM transfers data twice per clock cycle, whereas SDRAM transfers data once each clock cycle. Both DDR SDRAM and SDRAM are forms of dynamic memory. The difference in data transfer rate between DDR SDRAM and SDRAM is not determined by the number of pins, nor the operating voltage.
-
A data center has recently updated a physical server to host multiple operating systems on a single CPU. The data center can now provide each customer with a separate web server without having to allocate an actual discrete server for each customer. What is the networking trend that is being implemented by the data center in this situation?
- BYOD
- virtualization
- maintaining communication integrity
- online collaboration
Answers Explanation & Hints: Virtualization technology can run several different operating systems in parallel on a single CPU.
-
How can a user prevent specific applications from accessing a Windows computer over a network?
- Enable MAC address filtering.
- Disable automatic IP address assignment.
- Block specific TCP or UDP ports in Windows Firewall.
- Change default usernames and passwords.
Answers Explanation & Hints: Network applications have specific TCP or UDP ports that can be left open or blocked in Windows Firewall. Disabling automatic IP address assignment may result in the computer not being able to connect to the network at all. Enabling MAC address filtering is not possible in Windows and would only block specific network hosts, not applications. Changing default usernames and passwords will secure the computer from unauthorized users, not from applications.
-
When a PC is being assembled, what component is connected to the motherboard with a SATA cable?
- the optical drive
- the network interface card
- the video card
- the power supply
Answers Explanation & Hints: SATA cables, or serial ATA cables, are used to carry data from drives to the motherboard.
-
How does virtualization help with disaster recovery within a data center?
- Power is always provided.
- Less energy is consumed.
- Server provisioning is faster.
- Hardware does not have to be identical.
Answers Explanation & Hints: Disaster recovery is how a company goes about accessing applications, data, and the hardware that might be affected during a disaster. Virtualization provides hardware independence which means the disaster recovery site does not have to have the exact equipment as the equipment in production. Server provisioning is relevant when a server is built for the first time. Although data centers do have backup generators, the entire data center is designed for disaster recovery. One particular data center could never guarantee that the data center itself would never be without power.
-
What is the purpose of a Safety Data Sheet?
- to specify procedures for dealing with potentially hazardous materials
- to specify procedures in designing and building common computer systems
- to specify procedures for the operation of sensitive components and prevention of electrostatic discharge
- to specify procedures in the use of humidity control and prevention of moisture damage
Answers Explanation & Hints: A Safety Data Sheet is a fact sheet that summarizes information about material identification, including hazardous ingredients that can affect personal health, fire hazards, and first-aid requirements. The SDS explains how to dispose of potentially hazardous materials in the safest manner.
-
A customer has requested that a PC be built that will support eSATA. Which component should be checked to be sure that this feature is supported?
- CPU
- chipset
- hard disk
- RAM module
Answers Explanation & Hints: The chipset on a motherboard consists of integrated circuits that control how system hardware interacts with the CPU and motherboard. It also provides the capability and features needed, such as the maximum memory supported on the motherboard, multiple USB ports, eSATA connections, surround sound, and video.
-
What service is available for Windows to provide software print server services to MAC OS clients?
- Bonjour Print Server
- Print to XPS
- Apple AirPort Extreme
- Apple AirPrint
Answers Explanation & Hints: Bonjour Printer Server from Apple comes with MAC OS X and is a free download for Windows users to be used as a software print server. Airport Extreme, a dedicated print server, and a PC with a printer attached serving as a print server are all hardware print sharing solutions.
-
A user chooses the collate option and prints two copies of a three-page document. What is the order in which the pages are printed?
- pages 1, 1, 2, 2, 3, 3
- pages 1, 2, 3, 1, 2, 3
- pages 3, 3, 2, 2, 1, 1
- pages 3, 2, 1, 3, 2, 1
Answers Explanation & Hints: The collate feature enables a printer to sort multiple copies of a document with the proper page order for each copy.
-
A color laser printer is used to print documents with graphics and photographs. Users are complaining that printing takes too long. Which component of the printer should be upgraded in order to improve printing performance?
- CPU
- RAM
- hard drive
- toner cartridges
Answers Explanation & Hints: Because documents with graphics and photographs generate much larger print jobs, the printing process will run more efficiently if the printer memory is adequate to store the entire job before the job starts.
-
A technician is installing a new printer in a cool, damp environment. After the printer cabling is done, and the software and print driver are installed, the printer test page jams. What is the most likely cause of the print failure?
- incorrect printer driver
- too much humidity
- not enough printer memory
- loose printer cables
Answers Explanation & Hints: Paper jams are commonly caused when the paper being used is dirty, affected by humidity, or is the wrong type of paper for the printer.
-
The current IP configuration of a small company is done manually and is time-consuming. Because of increased network growth, a technician needs a simpler way for IP configuration of workstations. Which service would simplify the workstation IP configuration task?
- APIPA
- DHCP
- DNS
- ICMP
Answers Explanation & Hints: In networks with more than a few hosts, DHCP simplifies the addressing process. A DHCP server automatically assigns host IP addresses.
-
A device has an IPv6 address of 2001:0DB8:75a3:0214:0607:1234:aa10:ba01 /64. What is the host identifier of the device?
- 2001:0DB8:75a3
- 0607:1234:aa10:ba01
- 2001:0DB8
- ba01
Answers Explanation & Hints: An IPv6 address is made up of 128 bits that are represented as eight blocks of four hexadecimal digits that are called hextets. Because each hexadecimal digit represents four bits, each hextet represents 16 bits. The /64 network prefix indicates that the first 64 bits, or first four hextets, represent the network portion of the address. Because there are 128 bits in an IPv6 address, this leaves the last 64 bits, or last four hextets, to represent the host identifier. The value for the last four hextets is 0607:1234:aa10:ba01.
-
Which Cloud computing service would be best for an organization that needs to collaboratively create applications and deliver them over the web?
- PaaS
- IaaS
- SaaS
- ITaaS
Answers Explanation & Hints: Platform as a service (PaaS) provides a collaborative environment where multiple developers can create software and host an application through a Cloud provider.
-
Which type of network spans a single building or campus and provides services and applications to people within a common organizational structure?
- PAN
- WAN
- LAN
- MAN
Answers Explanation & Hints: A LAN is smaller or more contained than a WAN, which can span several cities. A MAN is usually contained in one city. A PAN is a very small network of devices that are located in close proximity to one another, usually within range of a single person.
-
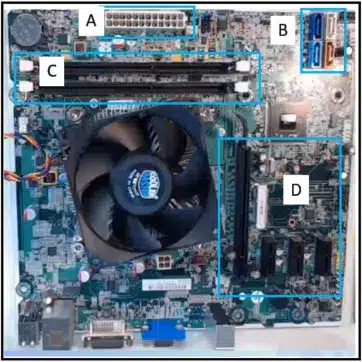
Refer to the exhibit. A technician has been asked to install a video card. Which section of the motherboard will the technician use to install the card?
ITE v8.0 – IT Essentials ( Version 8.0) – IT Essentials 8 Final Exam 1 – 14 Answers 02 - section A
- section B
- section C
- section D
Answers Explanation & Hints: Graphics cards, also known as video cards, are installed into a PCIe x16 expansion slot. The expansion slots on a motherboard are located near the motherboard ports.
-
A technician is installing an internal HDD. To which motherboard connector will the technician connect the data cable?
- ATX
- PCI
- PWR_SW
- SATA
Answers Explanation & Hints: Internal hard drives are commonly SATA drives that have a data cable that extends from the drive to a motherboard SATA connector..
-
Which component requires a technician to install screws externally through the PC case?
- RAM
- CPU
- motherboard
- power supply
Answers Explanation & Hints: The power supply commonly has four screws that attach from outside the case through case holes into screw holes on the power supply.
-
A company is looking for a next-generation firewall that provides VPN functionality, IDS/IPS functionality, and DoS/DDoS protection. Which device would be best suited for this task?
- multipurpose device
- router
- endpoint management server
- UTM
- TPM
Answers Explanation & Hints: A universal threat management (UTM) device is a security device that can provide firewall, IDS/IPS, and proxy server functionality as well as email filtering and DoS/DDoS protection.
-
A web designer accesses a company Windows 10 computer remotely. The designer often needs to simultaneously open multiple applications, such as a web page editor and a graphics editor. Rather than opening them in multiple windows, the designer opens them in different virtual desktops. What technology is being used by the designer?
- virtual reality
- Windows Virtual Desktop
- cloud-based applications
- virtual desktop infrastructure
Answers Explanation & Hints: Windows 10 has a feature called Windows Virtual Desktop (WVD). A user can create multiple virtual desktops and navigate among them easily. This feature reduces the clutter on a desktop of Windows caused by opening multiple applications. With WVD, a user can have each application open in a separate desktop.
-
A technician has been asked to configure Wi-Fi calling on a corporate mobile device. In which situation would this feature be most advantageous?
- in an emergency situation and no minutes are left on the phone
- when sending WEA updates
- when in an area with poor cellular coverage
- in a store transaction making a payment using the mobile device
Answers Explanation & Hints: Wi-Fi calling is not supported on all mobile devices, but when enabled, it uses a Wi-Fi network to make voice calls. It is very useful in areas with poor cellular coverage.
-
Which standard provides a bridge between laptop hardware and the operating system and a way for technicians to configure power management schemes to get the best performance?
- ACPI
- PCIe
- Bluetooth
- 802.11
Answers Explanation & Hints: The Advanced Configuration and Power Interface (ACPI) standard has specific sleep states that can be assigned to a device in order to conserve power. PCIe is a motherboard interface. Bluetooth and 802.11 are wireless standards.
-
Which statement describes a feature of SDRAM?
- It requires constant power to function.
- Its connector always has 240 pins.
- It can process overlapping instructions in parallel.
- It is able to support two writes and two reads per CPU clock cycle.
Answers Explanation & Hints: SDRAM ( Synchronous Dynamic RAM) works in synchronization with the memory bus and has higher transfer rates because it can process overlapping instructions in parallel.
-
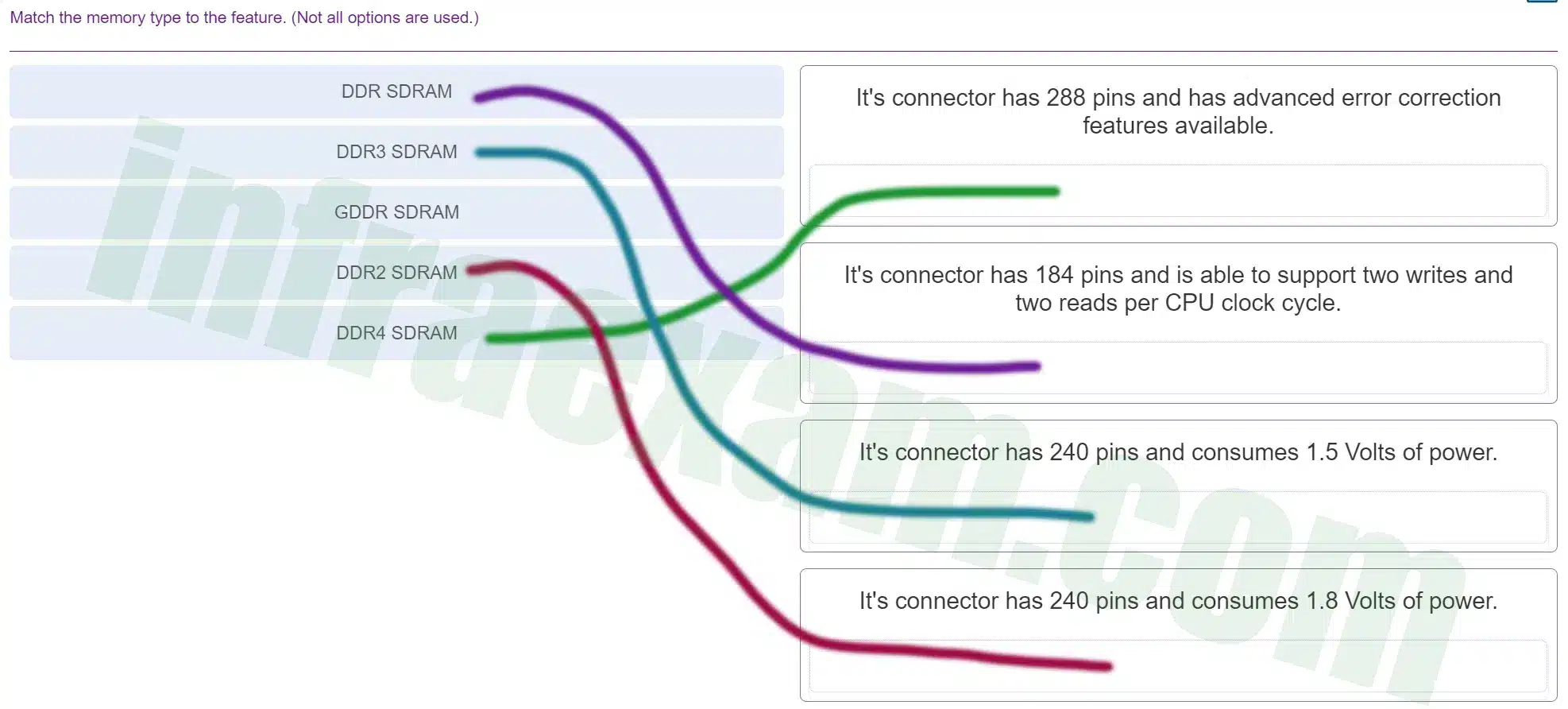
Match the memory type to the feature. (Not all options are used.)
ITE v8.0 – IT Essentials ( Version 8.0) – IT Essentials 8 Final Exam 1 – 14 Answers 002 -
Explanation & Hint: The image you’ve uploaded seems to be a matching exercise where different types of RAM (Random Access Memory) are to be matched with their respective features. I’m unable to view the image content directly, but I can provide information on the features generally associated with the different types of RAM listed:
- DDR SDRAM: DDR stands for Double Data Rate Synchronous Dynamic RAM. The original DDR RAM (also known as DDR1) typically has a 184-pin connector and is designed to perform two data transfers per clock cycle.
- DDR2 SDRAM: This is the second generation of DDR memory. DDR2 modules are usually 240-pin and operate at lower power levels than DDR1, around 1.8 Volts.
- DDR3 SDRAM: The third generation of DDR memory, DDR3, also uses a 240-pin connector but operates at even lower voltages, commonly 1.5 Volts, offering a balance of performance and power consumption.
- DDR4 SDRAM: As the fourth iteration of DDR memory, DDR4 modules have 288 pins and offer higher module density, greater speed, and more power efficiency. They include advanced features such as error correction code (ECC).
- GDDR SDRAM: Graphics Double Data Rate SDRAM is designed for graphics cards and is not usually used as main system memory. Its specifications vary widely depending on the version (like GDDR3, GDDR5, GDDR6), and they are optimized for high bandwidth rather than low latency.
Based on this information, you can match the types of RAM to their respective features listed in your exercise. For example, DDR4 SDRAM would match with the 288-pin connector and advanced error correction features. If you need more specific matching, you would need to transcribe the text or provide more context from the image.
-
-
A technician is troubleshooting a server that displays the error message “RAID not found” after a power outage over the weekend. What is a possible cause for this?
- The BIOS firmware needs updating.
- The FSB settings have changed and are wrong.
- The external RAID controller is not receiving power.
- The CPU multiplier is set too high.
Answers Explanation & Hints: The loss of the RAID controller can be caused by the external RAID controller not receiving power, incorrect BIOS settings, failure of the RAID controller or incorrect drivers for the RAID controller.
-
What are two probable causes of a user unable to access local resources such as file shares or printers on a wired network? (Choose two.)
- bad cabling
- DNS name resolution not working
- ISP down
- incorrect gateway address
- poor Wi-Fi signal
Answers Explanation & Hints: There are many issues which can cause local resources to be unavailable. These include bad cabling, a switch or router not functioning, a firewall blocking traffic, DNS name resolution not working, or failed services.
-
Which change management process component is concerned with the business processes that are affected by changes?
- assessment
- approval
- implementation
- identification
Answers Explanation & Hints: There are several change management process components that help changes, installations, and upgrades go more easily. The assessment component identifies the business processes that are affected and the costs and resources required.
-
What are two security risks associated with sharing printers in a corporate environment? (Choose two.)
- user authentication
- cached files
- document viewing in the print queue
- dumpster diving
- shoulder surfing
Answers Explanation & Hints: Three security concerns related to shared printers include (1) cached print files could contain sensitive data; (2) user authentication is needed to control access to the printer; and (3) print jobs could be read by others, intercepted, copied, or modified. Although the names of documents can be viewed in the print queue, document viewing is not possible. Dumpster diving and shoulder surfing are security concerns whether the printer is shared or not.
-
Which protocol is used by Windows for file and printer sharing?
- SMB
- SMTP
- HTTPS
- IMAP
Answers Explanation & Hints: SMB (Server Message Block) is the protocol used for file and printer sharing by Windows. SMTP and IMAP are protocols used in email services. HTTPS is the protocol used for secure web browsing.
-
Which laptop LCD technology uses tilting crystals to provide a much higher contrast ratio than other types?
- Vertical alignment (VA)
- In-Plane switching (IPS)
- Twisted Nematic (TN)
- Organic light-emitting diode (OLED)
Answers Explanation & Hints: Vertical alignment (VA) laptop display technology uses tilting crystals to provide a much higher contrast ratio than other types. In-Plane switching (IPS) and Twisted Nematic (TN) do not have this feature. Organic light-emitting diode (OLED) displays are not used in laptops.
-
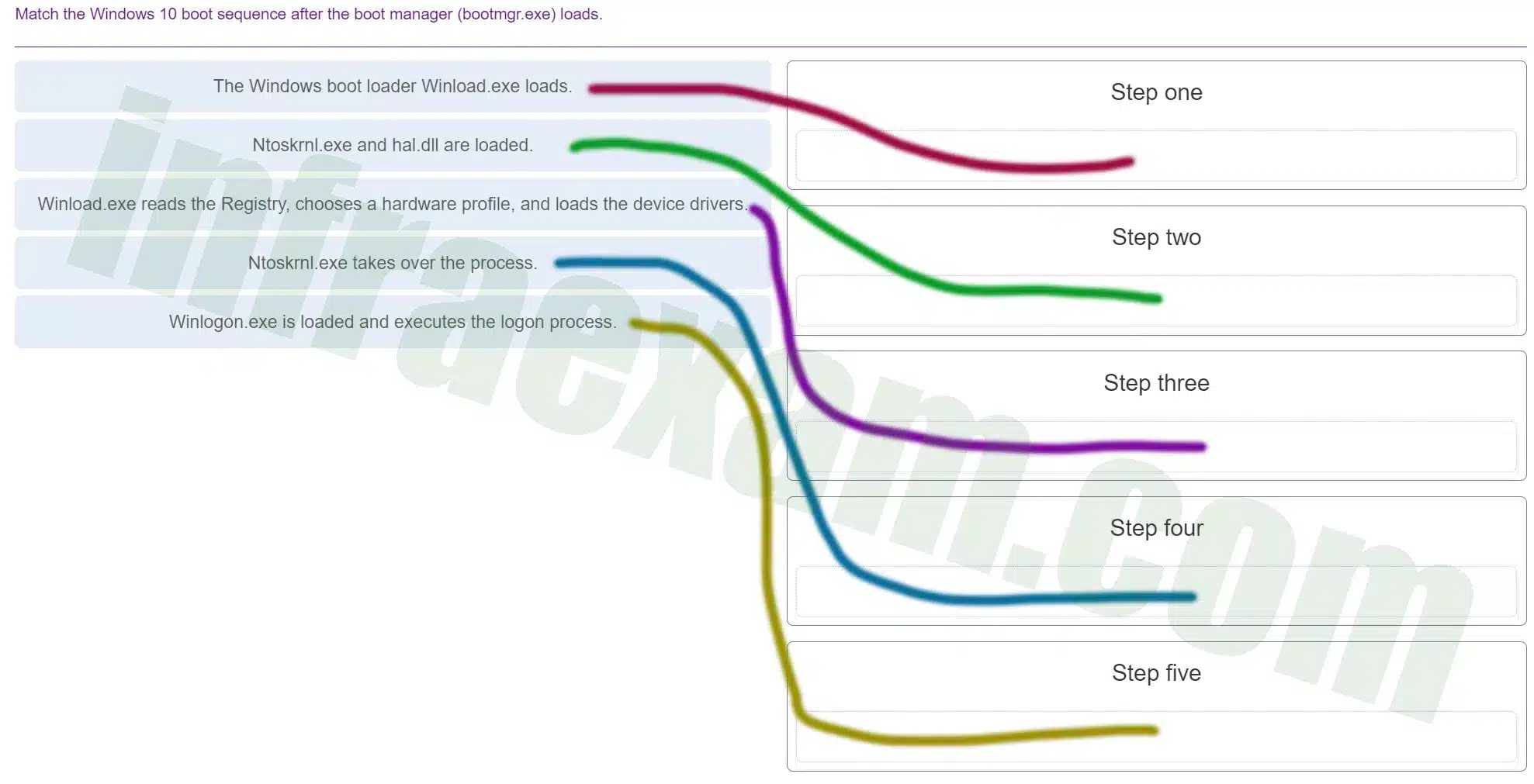
Match the Windows 10 boot sequence after the boot manager (bootmgr.exe) loads.
ITE v8.0 – IT Essentials ( Version 8.0) – IT Essentials 8 Final Exam 1 – 14 Answers 003 -
Explanation & Hint:
-
-
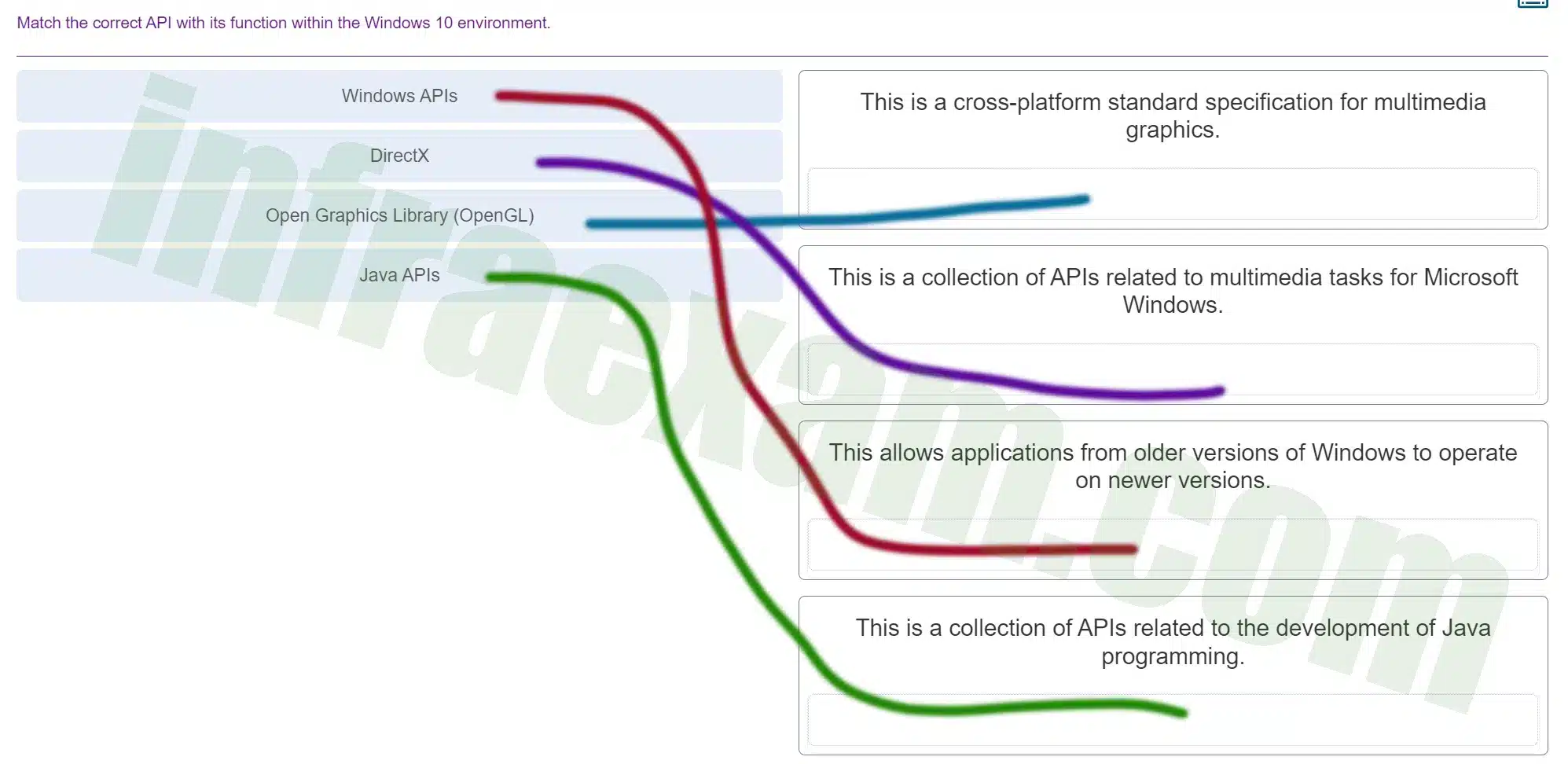
Match the correct API with its function within the Windows 10 environment.
ITE v8.0 – IT Essentials ( Version 8.0) – IT Essentials 8 Final Exam 1 – 14 Answers 004 -
Explanation & Hint:
-
-
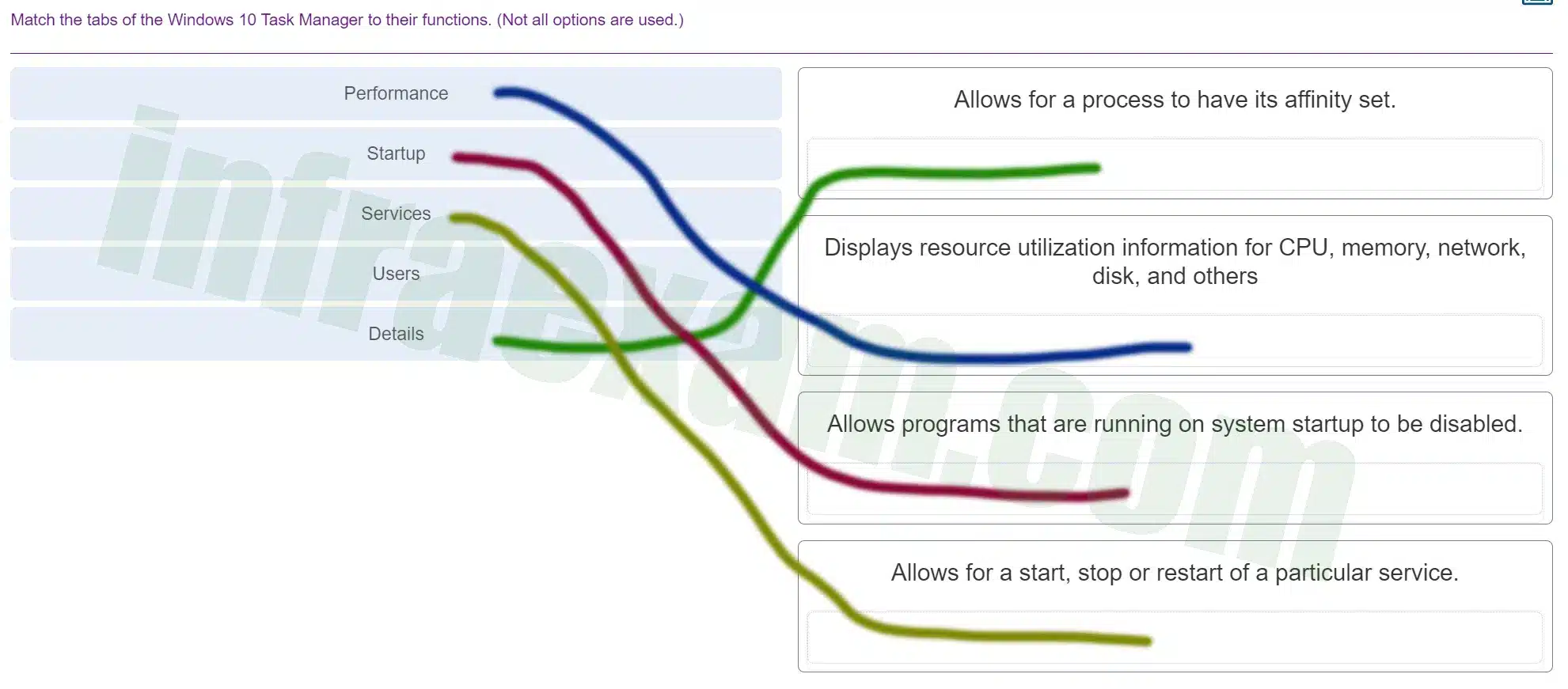
Match the tabs of the Windows 10 Task Manager to their functions. (Not all options are used.)
ITE v8.0 – IT Essentials ( Version 8.0) – IT Essentials 8 Final Exam 1 – 14 Answers 005 -
Explanation & Hint:
-
-
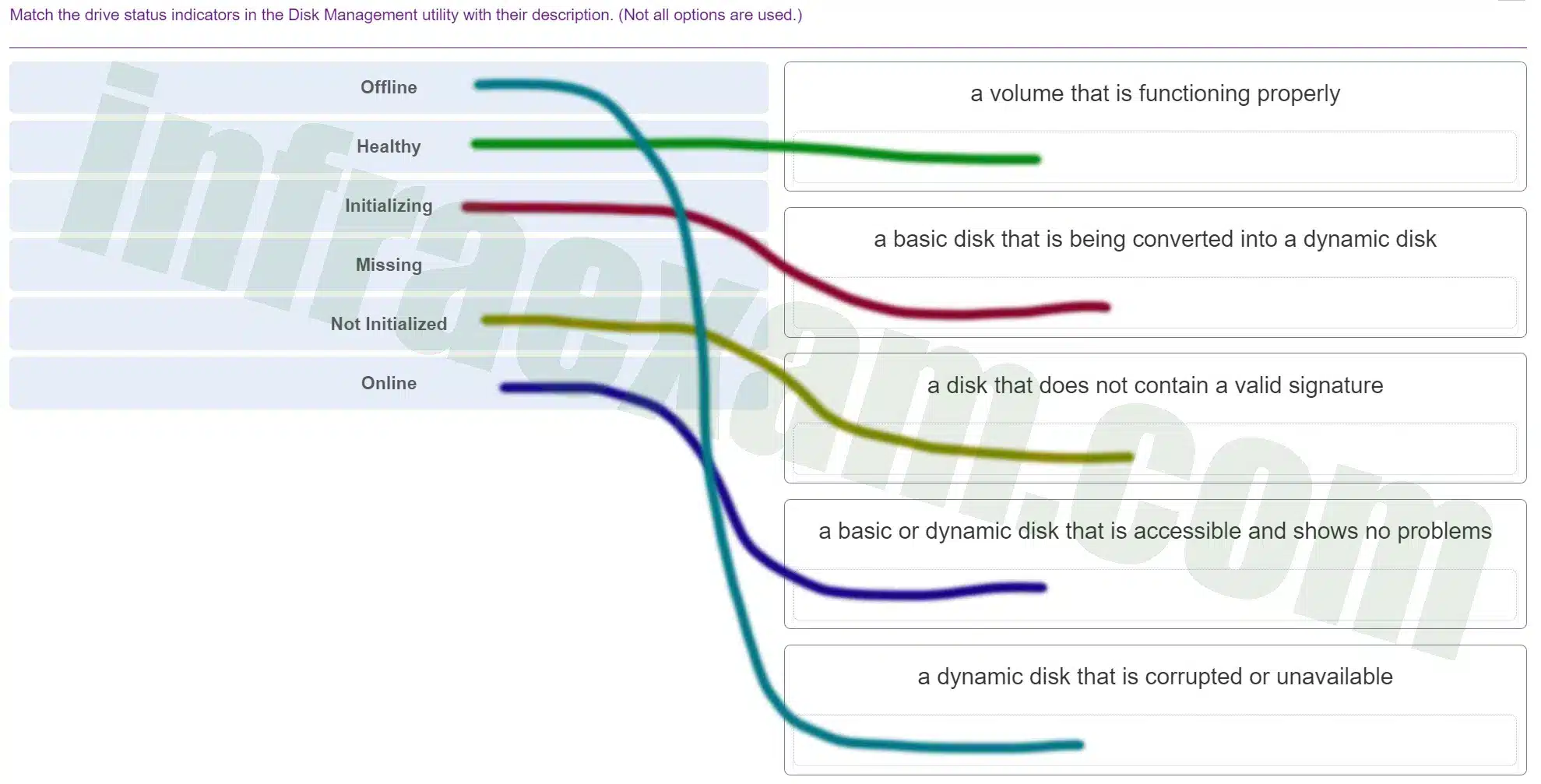
Match the drive status indicators in the Disk Management utility with their description. (Not all options are used.)
ITE v8.0 – IT Essentials ( Version 8.0) – IT Essentials 8 Final Exam 1 – 14 Answers 006 -
Explanation & Hint:
-
-
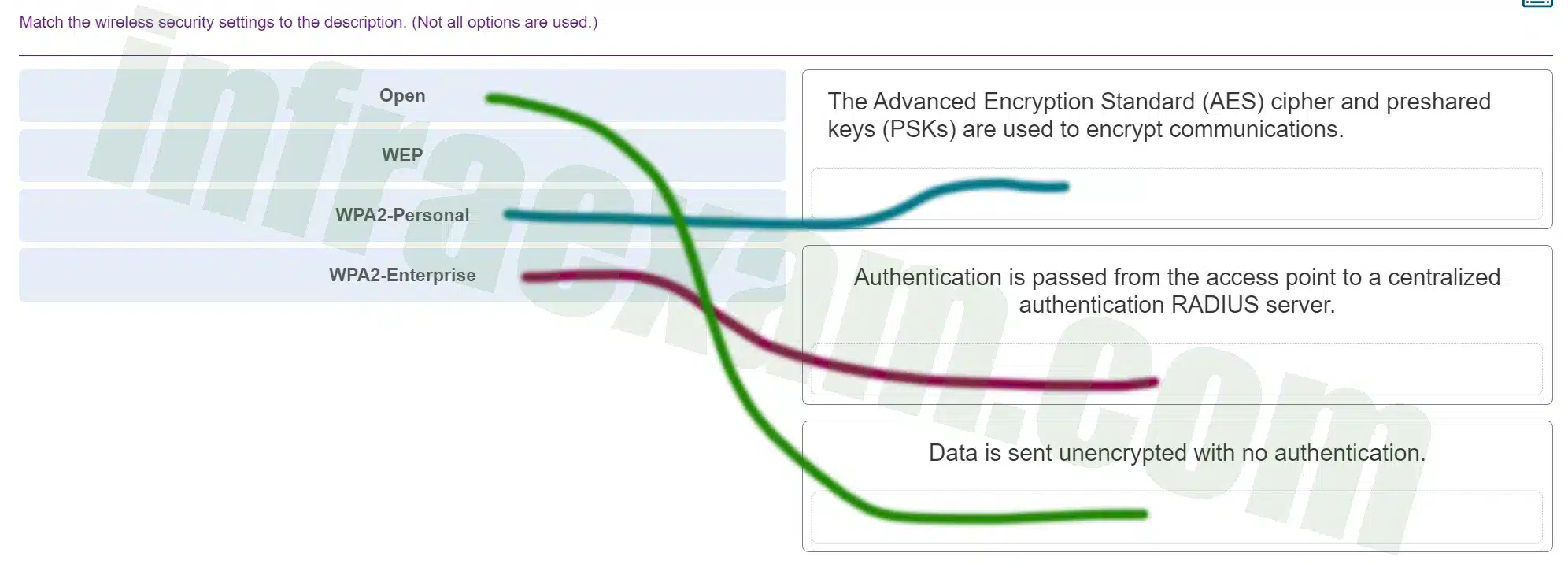
Match the wireless security settings to the description. (Not all options are used.)
ITE v8.0 – IT Essentials ( Version 8.0) – IT Essentials 8 Final Exam 1 – 14 Answers 007 -
Explanation & Hint:
-
-
When responding to a call from a customer who is experiencing problems with a computer, the technician notices that a number of system files on the computer have been renamed. Which two possible solutions could the technician implement to resolve the problem? (Choose two.)
- Use antivirus software to remove a virus.
- Restore the computer from a backup.
- Change the folder and file permissions of the user.
- Reset the password of the user.
- Upgrade the file encryption protocol.
Answers Explanation & Hints: Renamed system files are usually the result of a virus on the computer. Removing the virus and restoring the computer from a backup are the only two possible solutions in this case.
-
A technician suspects that a security issue is causing problems with a computer. What two actions could be performed to test theories of probable cause when troubleshooting the PC? (Choose two.)
- Log in as a different user.
- Disconnect the computer from the network.
- Search helpdesk repair logs for more information.
- Discuss solutions with the customer.
- Ask the customer open-ended questions about the problem.
Answers Explanation & Hints: Several actions can be taken by a technician when security issues are suspected as the possible cause of a problem with a computer. Logging in as a different user or disconnecting the PC from the network to isolate the cause of the problem are two possible actions.
-
What are three features of GPS on mobile devices? (Choose three.)
- phone number lookup
- navigation
- specialized search results
- device tracking
- remote wipe
- gas mileage calculations
Answers Explanation & Hints: Navigation, specialized search results, and device tracking are features of GPS on mobile devices. Remote wipe may be a feature on some mobile devices, but is not related to GPS. Phone number lookup and gas mileage calculations are not GPS features.
-
The CIO wants to secure data on company laptops by implementing file encryption. The technician determines the best method is to encrypt each hard drive using Windows BitLocker. Which two things are needed to implement this solution? (Choose two.)
- at least two volumes
- USB stick
- password management
- TPM
- EFS
- backup
Answers Explanation & Hints: Windows provides a method to encrypt files, folders, or entire hard drives depending on need. However, certain BIOS settings and configurations are necessary to implement encryption on an entire hard disk.
-
Which three components are used to assign file and directory permissions in Linux systems? (Choose three.)
- root
- group
- owner
- all users
- super group
- admin group
Answers Explanation & Hints: In Linux, file and directory permissions are assigned as follows:
- Owner – the owner user of the file or directory
- Group – the user group that has been assigned to the file or directory
- All users – all other users on the system
-
A user downloads a widget onto his Android phone but is puzzled to see that when the widget is touched an app is launched. What is a possible cause?
- The user has downloaded a virus.
- The widget is corrupt.
- The security settings of the Android OS have been compromised.
- The widget is associated with the app and this is the normal behavior.
Answers Explanation & Hints: Widgets are programs that when installed associate with the application they were built for. This will cause the application to launch when the widget icon is touched on the touchscreen of the Android device.
-
What is an accurate description of asymmetric encryption technology?
- Asymmetric encryption is an encryption process that compares traffic on both ends to make sure the traffic has not been altered.
- It is an encryption process that uses identical keys on both ends to establish the VPN.
- It is an encryption protocol that is used to encrypt data as the data is sent over the VPN.
- It is an encryption process that uses a public and private key pair to encrypt/decrypt data.
-
Explanation & Hint:
-
Which type of security threat can be transferred through email and is used to gain sensitive information by recording the keystrokes of the email recipient?
- adware
- Trojan
- worm
- virus
- grayware
Answers Explanation & Hints: Adware does not record keystrokes. A worm self-replicates across the network. A Trojan appears to be a legitimate program while carrying malware, and grayware is a general term for software that may be malware.
-
A user wants to extend a primary partition formatted with the NTFS file system with the unallocated space on the hard disk. What must the user do after the primary partition is extended to make it usable?
- Convert the disk type to dynamic.
- Ensure that the disk type is basic.
- Format the disk with the FAT64 file system.
- Partition the new space as a basic disk.
Answers Explanation & Hints: A partition must be formatted with the NTFS file system in order to extend it by using the unallocated space on the disk. Once the partition has been extended, the disk type must be converted to a dynamic disk in order for the new partition to be accessible.
-
What is the purpose of running mobile device apps in a sandbox?
- to enable the phone to run multiple operating systems
- to prevent malicious programs from infecting the device
- to enable separate app icons to be displayed on the home screen
- to bypass phone carrier restrictions that prevent access to unauthorized apps
Answers Explanation & Hints: Mobile device apps are run in a sandbox that isolates them from other resources. Bypassing the phone carrier from preventing access to unauthorized apps is jailbreaking or rooting the device.
-
Why is a full format more beneficial than a quick format when preparing for a clean OS installation?
- A full format is the only method of installing Windows 8.1 on a PC that has an operating system currently installed.
- A full format will delete files from the disk while analyzing the disk drive for errors.
- A full format will delete every partition on the hard drive.
- A full format uses the faster FAT32 file system, whereas a quick format uses the slower NTFS file system.
Answers Explanation & Hints: A full format removes files from a partition while scanning the disk for bad sectors. A quick format will remove files from a partition but does not scan a disk for bad sectors.
-
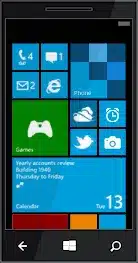
Refer to the exhibit. What is true of this mobile device screen?
ITE v8.0 – IT Essentials ( Version 8.0) – IT Essentials 8 Final Exam 1 – 14 Answers 03 - Tapping and holding the arrow at the bottom left will display the Home screen.
- Text messages, news, photos and other content can be displayed in the different tiles.
- Icons and buttons are used to represent the different apps on the phone.
- Unpinning an app from this view will uninstall the app from the phone.
- Tile sizes depend on the size of the app.
Answers Explanation & Hints: The Windows Phone interface uses tiles to represent apps. Tiles are rectangular areas of a screen that identify the app and may also contain active content such as text messages, news feeds, and photos.
-
Which built-in tool is available on a Mac OS X machine to perform disk backups?
- Disk Utility
- Deja Dup
- Finder
- Time Machine
Answers Explanation & Hints: Time Machine is an automatic backup utility in the Mac OS. The Mac Disk Utility allows an administrator to configure disk backups. The Deja Dup tool is a tool built into the Linux OS for backing up data. Finder is similar to the Windows File Explorer tool and is used to navigate the Mac OS file system.
-
A user calls the help desk reporting that a laptop with Linux freezes on startup and displays kernel panic. What could cause this problem?
- A driver has become corrupted.
- GRUB or LILO has been deleted.
- GRUB or LILO has been corrupted.
- An application is using a resource that has become unavailable.
Answers Explanation & Hints: A corrupted driver or failing hardware could cause kernel panic for Linux or Mac OS. The laptop will not be able to boot successfully. Either GRUB or LILO corruption or GRUB or LILO deletion would cause the stop screen to display a “Missing GRUB” or “Missing LILO” message. A resource unavailable to an application will cause the application to stop responding, but not prevent a laptop from starting up.
-
A user calls the help desk to report that a mobile device exhibits very slow performance. What could cause this problem?
- The touchscreen is not calibrated.
- An app is not compatible with the device.
- The operating system is corrupt.
- A power-intensive app is running in the background.
Answers Explanation & Hints: A power-intensive app that is running in the background could consume most of the CPU cycles and thus the device would exhibit very slow performance for other apps. If an app is not compatible with the device, the device operating system would freeze. If the operating system has encountered an error, the device will fail to respond.
-
A technician wishes to prepare the computers in the network for disaster recovery. The network consists of a variety of desktops and laptops from different vendors. All the computers are running either a 32-bit version of Windows 10 Pro or a 64-bit version of Windows 10 Pro. How would the technician prepare the recovery media?
- Prepare one 64-bit recovery disc for all the computers.
- Prepare one 32-bit recovery disc for all the computers.
- Prepare individual recovery discs for all the computers.
- Prepare one image restore for all the computers.
Answers Explanation & Hints: All the PCs are from different vendors and thus have dissimilar hardware configurations. Furthermore, all the PCs have a variety of 32-bit Windows 10 and 64-bit Windows 10. Because the PCs have different versions of the OS and dissimilar hardware, you cannot use the same image on all the PCs . In order to use a single image, Sysprep must be used to strip out machine specific information like the SID, and all PCs must have the same hardware configuration and the same version of the Windows operating system.
-
A technician uses Microsoft Deployment Image Servicing and Management (DISM) tool to create a Windows image file on one of the workstations running Windows 10. When the technician tries to clone another workstation with the image file, the workstation exhibits network connectivity issues on completion. What could cause this?
- The SID of the original PC is not cleared when creating the image with DISM.
- The technician used the wrong tool to create the image file.
- The network drivers were not added to the image file.
- The Sysprep utility should have been turned off prior to the creation of the image file.
Answers Explanation & Hints: The technician must use Sysprep to clean up the local specific configuration, such as the SID, otherwise the cloned systems will not work properly.
-
A technician wishes to deploy Windows 10 Pro to multiple PCs through the remote network installation process. The technician begins by connecting the new PCs to the network and booting them up. However, the deployment fails because the target PCs are unable to communicate with the deployment server. What is the possible cause?
- The wrong network drivers are loaded in the image file.
- The SID has not been changed in the image file.
- The NIC cards on the new PCs are not PXE-enabled.
- Sysprep was not used before building the image file.
Answers Explanation & Hints: The NIC cards on the new PCs have to be PXE-enabled in order for them to communicate with the remote installation services on the server.
-
Which condition is required when planning to install Windows on a GPT disk?
- The computer must be UEFI-based.
- Only one primary partition can contain an OS.
- The maximum partition size cannot exceed 2 TB.
- The maximum number of primary partitions that can co-exist is 4.
Answers Explanation & Hints: The globally unique identifier (GUID) partition table (GPT) makes use of a number of modern techniques to expand on the older MBR partitioning scheme. GPT is commonly used in computers with UEFI firmware. For Windows 10 to be installed on, and boot, from a GPT disk UEFI must be used.
-
A user complains that user files cannot be synced with the network file server while the user is traveling out of the office. The user had access to the internet but no access to the company network server. How can this be addressed?
- Ensure that the user only uses a single device and not multiple devices when accessing networked files.
- Turn off the activation of Offline Files feature in the Sync Center.
- Setup a Sync partnership with the networked file location.
- Setup a Sync partnership between the network server, Microsoft OneDrive, and the user.
Answers Explanation & Hints: Because the user has access to the internet, access to the Microsoft OneDrive cloud based service is possible and thus the user can sync with Microsoft OneDrive, which in turn can sync with the company network server from across the internet.
-
A technician has connected a new internal hard drive to a Windows 10 PC. What must be done in order for Windows 10 to use the new hard drive?
- Initialize the new hard drive.
- Extend the partition on an existing hard drive to the new hard drive.
- Run chkdsk on the new hard drive.
- Mount the new hard drive.
Answers Explanation & Hints: The new hard drive needs to be initialized before it can be used in Windows. This will involve formatting the disk which will erase any existing data on the drive.
-
A manager reports that unusual things are happening on a Windows computer. The technician determines that malware is the culprit. What can the technician do to remove stubborn malware?
- Ensure that the computer is connected to the wired network so that antimalware updates can be installed.
- Enter Safe Mode and do a system restore.
- Install adware protection.
- Train the user on identifying trusted and untrusted sources.
Answers Explanation & Hints: Booting the computer in Safe Mode prevents most drivers from loading. Additional antimalware software can then be installed to remove or quarantine malware. Sometimes the storage drive must be wiped, the operating system reinstalled, and data restored from a backup.
-
What service does PRINT$ provide?
- It provides a network share for accessing shared printers.
- It provides printer drivers for printer administrators.
- It provides a group of hidden printers that only administrative users have permissions to send print jobs to.
- It provides an administrative Printer share accessible by all local user accounts.
Answers Explanation & Hints: PRINT$ is a hidden share for printer drivers. It is shared by default and used to access remote shared printers or provide drivers to clients when sharing a printer.
-
An employee that has worked at the company for many years has started a home-based business selling crafts. While leaving an office meeting, a company supervisor notices the employee buying supplies for the personal crafting business of the employee. What section of the security policy should the supervisor review when determining how to handle this situation?
- acceptable use policies
- identification and authentication policies
- incident handling policies
- remote access policies
Answers Explanation & Hints: The acceptable use policies section of a security policy commonly identifies network resources and usages that are acceptable to the organization. They might also state the ramifications that can occur if this security policy is violated.
-
What Windows utility should be used to configure password rules and account lockout policies on a system that is not part of a domain?
- Event Viewer security log
- Local Security Policy tool
- Active Directory Security tool
- Computer Management
Answers Explanation & Hints: A technician must be aware of the technologies and measures that are used as countermeasures to protect the organization from threats and vulnerabilities. A Windows Domain Security Policy is used and applied when a user logs in to a computer that is on a corporate network. A Windows Local Security Policy is used for stand-alone computers to enforce security settings.
-
A customer brings in a computer that is asking for a password as soon as it powers on, even before the operating system boots. Which type of password is enabled?
- BIOS
- login
- multifactor
- network
- synchronous
Answers Explanation & Hints: A BIOS password is configured by entering the BIOS Setup program. If unknown, it can be removed by placing a jumper over two motherboard pins. Some motherboards support BIOS password removal by removing the CMOS battery, but if this is done, all BIOS settings will be reset to the default values.
-
A technician is troubleshooting a Windows 10 laptop infected with a virus that has damaged the master boot record. The technician has booted the laptop using the installation media and is attempting to repair the laptop from the command line interface. Which command can the technician use to repair the corrupt master boot record?
- bootrec /fixmbr
- chkdsk
- msconfig
- sfc /scannow
Answers Explanation & Hints: The sfc /scannow command is used to check the integristy of the system files. The msconfig command allows for viewing the startup configuration mode, while the chkdsk command is used to repair the Windows file system. The bootrec /fixmbr command is used to repair a corrupt master boot record in a Windows 10 environment.
-
A user reports that a Windows 10 PC displays the error message “Invalid Boot Disk” during the boot process. The IT technician attempts to boot the computer and finds that the error message occurs immediately after the POST. What could be the possible cause?
- A recently installed device driver is incompatible with the boot controller.
- BOOTMGR is corrupted.
- The MBR/GPT is corrupted.
- A service failed to start during the booting process.
Answers Explanation & Hints:
The message “invalid Boot Disk” could be a symptom of a missing or damaged MBR/GPT, a missing or damaged Boot Configuration Data file, a boot sector virus, a boot order not set correctly in BIOS, media without an operating system being in a drive, a hard drive not detected or damaged, or the absence of an installed operating system.
-
A technician wishes to perform a customized unattended network installation of Windows 10 on a PC. The requirements include the installation of specific applications and device drivers through the use of an answer file. What would the technician use to create the answer file?
- Recovery partition
- Windows SIM
- disk cloning
- System Restore
Answers Explanation & Hints: To perform a custom Windows Unattended installation, setup.exe must be run with the user options found in the answer file. Additional packages, such as applications or drivers, can be added to the answer file. The Windows System Image Manager (SIM) is used to create the setup answer file.
-
The IT department has just purchased 15 wireless access points in order to provide full wireless coverage for all 100 employees within the company and is looking to deploy the most secure and scalable wireless implementation. Which open source authentication method would perform authentication on behalf of all 15 wireless network devices?
- TACACS+
- TKIP
- RADIUS
- WPA2-PSK
Answers Explanation & Hints: RADIUS and TACACS+ both use a separate server that performs authentication on behalf of network devices. However, RADIUS is an open standard and provides greater compatibility.
-
Which feature is included with macOS and provides the ability for a remote user to view and change files, folders, and applications on the local computer?
- Screen Sharing
- Remote Assistance
- Virtual Network Computing
- Remote Desktop
Answers Explanation & Hints: In macOS, remote access functionality is provided by the Screen Sharing feature, which is based on Virtual Network Computing (VNC). VNC is a freeware product that is similar in functionality to RDP and works over port 5900.
-
When attempting to improve system performance for Linux computers with a limited amount of memory, why is increasing the size of the swap file system not considered the best solution?
- A swap file system only supports the ex2 file system.
- A swap file system does not have a specific file system.
- A swap file system cannot be mounted on an MBR partition.
- A swap file system uses hard disk space to store inactive RAM content.
Answers Explanation & Hints: The swap file system is used by Linux when it runs out of physical memory. When needed, the kernel moves inactive RAM content to the swap partition on the hard disk. Storing and retrieving content in the swap partition is much slower than RAM is, and therefore using the swap partition should not be considered the best solution to improving system performance.
-
Which methods can be used to implement multifactor authentication?
- VPNs and VLANs
- IDS and IPS
- passwords and fingerprints
- tokens and hashes
Answers Explanation & Hints: A cybersecurity specialist must be aware of the technologies available that support the CIA triad.
-
Which area of concern falls under the operations and planning category in IT documentation?
- inventory management
- disaster recovery policies and procedures
- logical and physical network topology diagrams
- end-user manual for hardware and software
Answers Explanation & Hints: There are four broad categories of IT documentation: Policies, Operations, Projects, and User documentation. Operations is concerned with inventory management.
-
Which two statements are true regarding GPT partitions? (Choose two.)
- They are commonly used in computers with UEFI firmware.
- They are commonly used in computers with BIOS based firmware.
- They store a backup of the partition table.
- They have a maximum partition size of 2TB.
- They store the partition and boot data in one place.
Answers Explanation & Hints: GPT partitions are commonly used in computers with UEFI firmware. They store a backup of the partition table and can support up to 128 partitions. The maximum partition size is 9.4ZB.
-
A technician wishes to use the reset option to repair a Windows 10 installation and chooses the option that will retain the user’s personal files. Which statement is true based on using this option?
- All user files and applications will be restored together with the complete reinstallation of Windows 10.
- Only user files will be restored together with the complete reinstallation of Windows 10.
- All user files and applications will be deleted, and a complete reinstallation of Windows 10 will occur.
- Only corrupt files of the Windows 10 installation will be replaced and repaired.
Answers Explanation & Hints: By using the reset process from within the recovery area, it will remove all apps and programs, change the computer’s settings back to their defaults, and reinstall Windows 10 without removing any user personal data files.
-
A user is trying to execute a file using elevated permission. The user right-clicks the file, chooses Run as Administrator, and chooses Yes in the User Account Control (UAC) window. The operation fails. What is the reason?
- The UAC does not have the elevated privileges option.
- The user is not a member of the administrator group.
- The directory housing the file is read-only.
- The login password of the user is invalid.
Answers Explanation & Hints: An administrator password is required to open or execute a file using elevated permission, or the current user must belong to the Administrator group.
-
What is a possible situation when it might be necessary to boot Windows 10 from a bootable recovery USB device?
- to disable background services
- to delete registry keys
- to partition the hard drive
- to repair the operating system
Answers Explanation & Hints: You can boot Windows 10 from a repair boot USB drive and repair your computer with corresponding recovery tools, such as bootrec commands. A Windows 10 repair boot USB is a bootable recovery drive made with USB.
-
An accountant is booting a PC that has Windows 10 installed. The boot process is currently working on the following step: BIOS locates and reads the configuration settings that are stored in the CMOS memory. What is the next step that will happen in the boot process?
- The BIOS boots the computer using the first drive that contains a valid boot sector.
- WinLoad reads the registry files, chooses a hardware profile, and loads the device drivers.
- The Windows kernel takes over the boot process.
- WinLoad loads two files that make up the core of Windows: NTOSKRNL.EXE and HAL.DLL.
Answers Explanation & Hints: The Windows 10 boot process is as follows:
1 . PreBoot: POST or Power-On Self-Test loads firmware settings. It checks for a valid disk system, and if the system is good to go for the next phase. If the computer has a valid MBR, i.e. Master Boot Record, the boot process moves further and loads Windows Boot Manager.
2 . Windows Boot Manager: This step determines if you have multiple OS installed on your computer. If yes, then it offers a menu with the names of the OSs. When you select the OS, it will load the right program, i.e. Winload.exe to boot you into the correct OS.
3 . Windows OS Loader: WinLoad.exe loads important drivers to kick start the Windows Kernel. The kernel uses the drivers to talk to the hardware and do rest of the things required for the boot process to continue.
4 . Windows NT OS Kernel: This is the last stage which picks up the Registry settings, additional drivers, etc. Once that has been read, the control is taken by the system manager process. It loads up the UI, the rest of the hardware and software. That’s when you finally get to see your Windows 10 Login screen.
-
A manager is booting a tablet that has Windows 10 installed. The boot process is currently working on the following step: The Windows kernel takes over the boot process. What is the next step that will happen in the boot process?
- NTOSKRNL.EXE starts the login file called WINLOGON.EXE.
- The Windows kernel takes over the boot process.
- WinLoad reads the registry files, chooses a hardware profile, and loads the device drivers.
- WINLOGON.EXE displays the Windows Welcome screen
Answers Explanation & Hints: The Windows 10 boot process is as follows:
1. PreBoot: POST or Power-On Self-Test loads firmware settings. It checks for a valid disk system, and if the system is good to go for the next phase. If the computer has a valid MBR, i.e. Master Boot Record, the boot process moves further and loads Windows Boot Manager.
2. Windows Boot Manager: This step determines if you have multiple OS installed on your computer. If yes, then it offers a menu with the names of the OSs. When you select the OS, it will load the right program, i.e. Winload.exe to boot you into the correct OS.
3. Windows OS Loader: WinLoad.exe loads important drivers to kick start the Windows Kernel. The kernel uses the drivers to talk to the hardware and do rest of the things required for the boot process to continue.
4. Windows NT OS Kernel: This is the last stage which picks up the Registry settings, additional drivers, etc. Once that has been read, the control is taken by the system manager process. It loads up the UI, the rest of the hardware and software. That’s when you finally get to see your Windows 10 Login screen.
-
A manager is booting a tablet that has Windows 10 installed. The boot process is currently working on the following step: WINLOGON.EXE displays the Windows Welcome screen What is the next step that will happen in the boot process?
- There are no more steps, the boot process is complete.
- The BIOS boots the computer using the first drive that contains a valid boot sector.
- The code in the boot sector is executed and the control of the boot process is given to Windows Boot Manager.
- Winload uses the path specified in BOOTMGR to find the boot partition.
Answers Explanation & Hints: The Windows 10 boot process is as follows:
1 . PreBoot: POST or Power-On Self-Test loads firmware settings. It checks for a valid disk system, and if the system is good to go for the next phase. If the computer has a valid MBR, i.e. Master Boot Record, the boot process moves further and loads Windows Boot Manager.
2 . Windows Boot Manager: This step determines if you have multiple OS installed on your computer. If yes, then it offers a menu with the names of the OSs. When you select the OS, it will load the right program, i.e. Winload.exe to boot you into the correct OS.
3 . Windows OS Loader: WinLoad.exe loads important drivers to kick start the Windows Kernel. The kernel uses the drivers to talk to the hardware and do rest of the things required for the boot process to continue.
4 . Windows NT OS Kernel: This is the last stage which picks up the Registry settings, additional drivers, etc. Once that has been read, the control is taken by the system manager process. It loads up the UI, the rest of the hardware and software. That’s when you finally get to see your Windows 10 Login screen
-
An analyst is booting a desktop that has Windows 10 installed with 4 GB RAM. The boot process is currently working on the following step: Winload uses the path specified in BOOTMGR to find the boot partition. What is the next step that will happen in the boot process?
- WinLoad loads two files that make up the core of Windows: NTOSKRNL.EXE and HAL.DLL.
- The BIOS boots the computer using the first drive that contains a valid boot sector.
- The code in the boot sector is executed and the control of the boot process is given to Windows Boot Manager.
- The Windows kernel takes over the boot process.
Answers Explanation & Hints: The Windows 10 boot process is as follows:
1. PreBoot: POST or Power-On Self-Test loads firmware settings. It checks for a valid disk system, and if the system is good to go for the next phase. If the computer has a valid MBR, i.e. Master Boot Record, the boot process moves further and loads Windows Boot Manager.
2. Windows Boot Manager: This step determines if you have multiple OS installed on your computer. If yes, then it offers a menu with the names of the OSs. When you select the OS, it will load the right program, i.e. Winload.exe to boot you into the correct OS.
3. Windows OS Loader: WinLoad.exe loads important drivers to kick start the Windows Kernel. The kernel uses the drivers to talk to the hardware and do rest of the things required for the boot process to continue.
4. Windows NT OS Kernel: This is the last stage which picks up the Registry settings, additional drivers, etc. Once that has been read, the control is taken by the system manager process. It loads up the UI, the rest of the hardware and software. That’s when you finally get to see your Windows 10 Login screen
-
A user notes that the username and password are automatically populated in the Microsoft Edge browser when logging into a secure site. When the user tries to log into the same site using Google Chrome, the username and password do not save automatically. Why is this occurring?
- Google Chrome does not support that secure site.
- The certificate for that site has not been authenticated.
- Google Chrome does not automatically save web credentials.
- The Google Chrome browser is corrupt.
Answers Explanation & Hints: Web credentials do not save for sites accessed by browsers other than Internet Explorer and Edge. Credentials created with other browsers must be managed from within that browser.
-
Which statement is true regarding libraries in Windows 10?
- Libraries allow Windows 10 to support file names longer than 20 characters.
- Libraries allow Windows 10 to link multiple different directories.
- Libraries allow Windows 10 to enforce the EFS file system.
- Libraries allow Windows 10 to index files faster.
Answers Explanation & Hints: Libraries in Windows 10 allow multiple different directories to be linked together in one location.
-
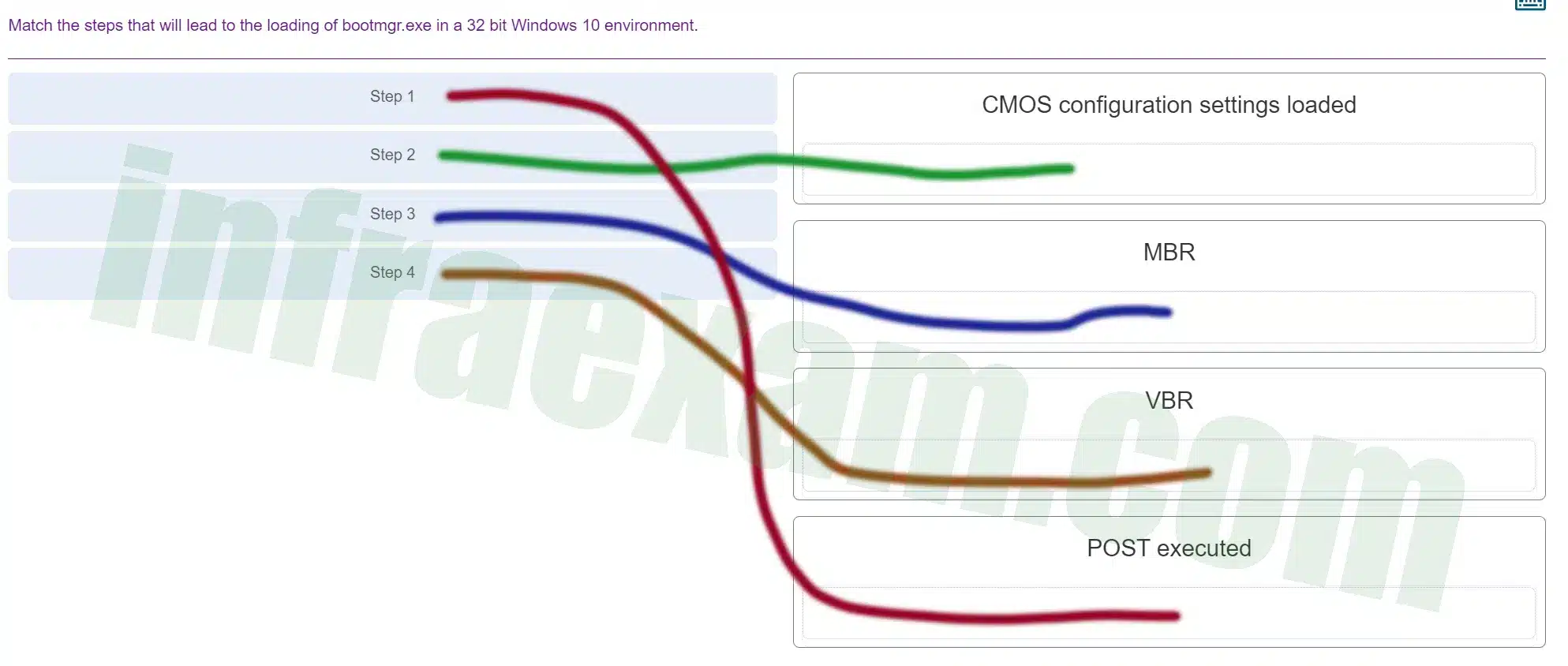
Match the steps that will lead to the loading of bootmgr.exe in a 32 bit Windows 10 environment.
ITE v8.0 – IT Essentials ( Version 8.0) – IT Essentials 8 Final Exam 1 – 14 Answers 008 -
Explanation & Hint:
-
-
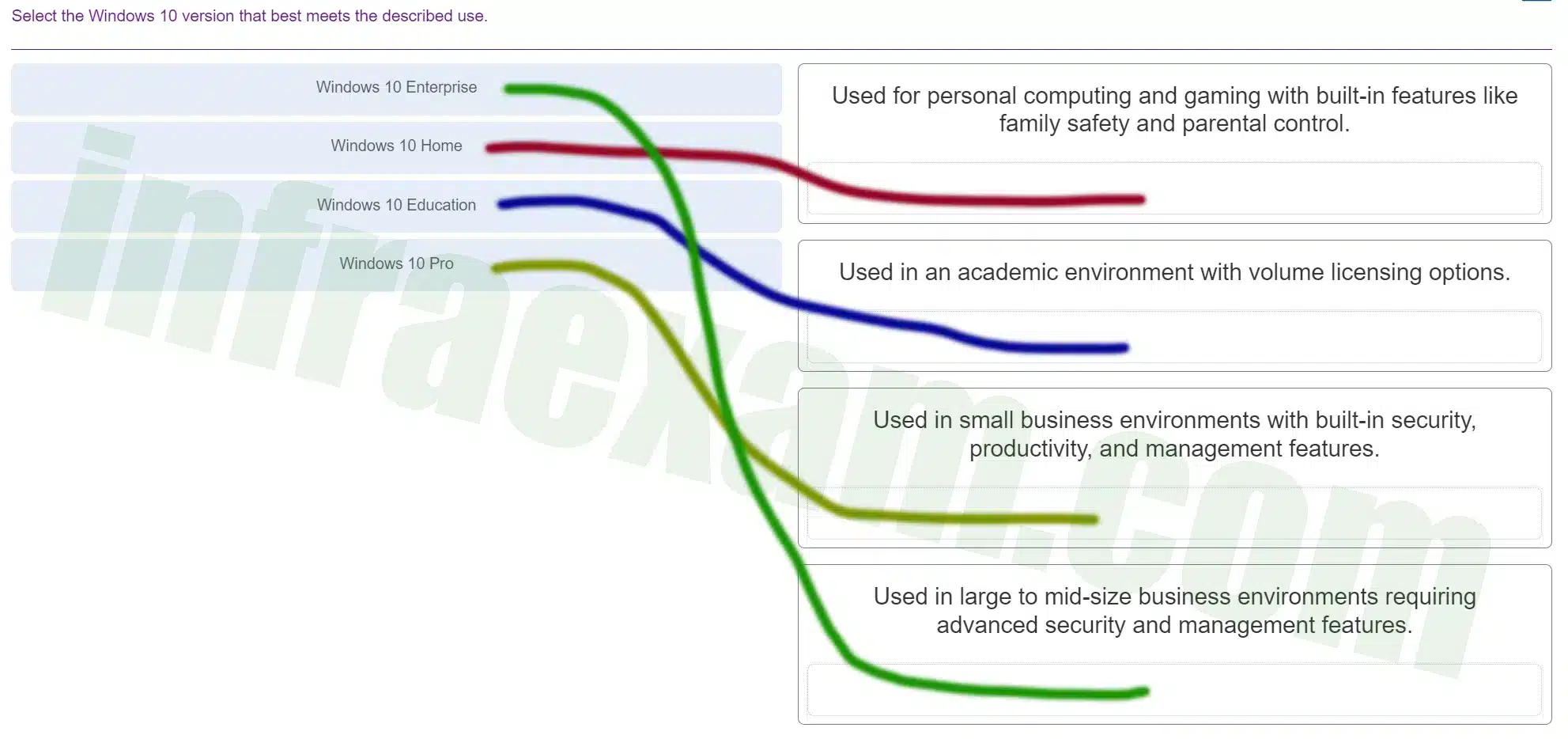
Select the Windows 10 version that best meets the described use.
ITE v8.0 – IT Essentials ( Version 8.0) – IT Essentials 8 Final Exam 1 – 14 Answers 009 -
Explanation & Hint:
-
-
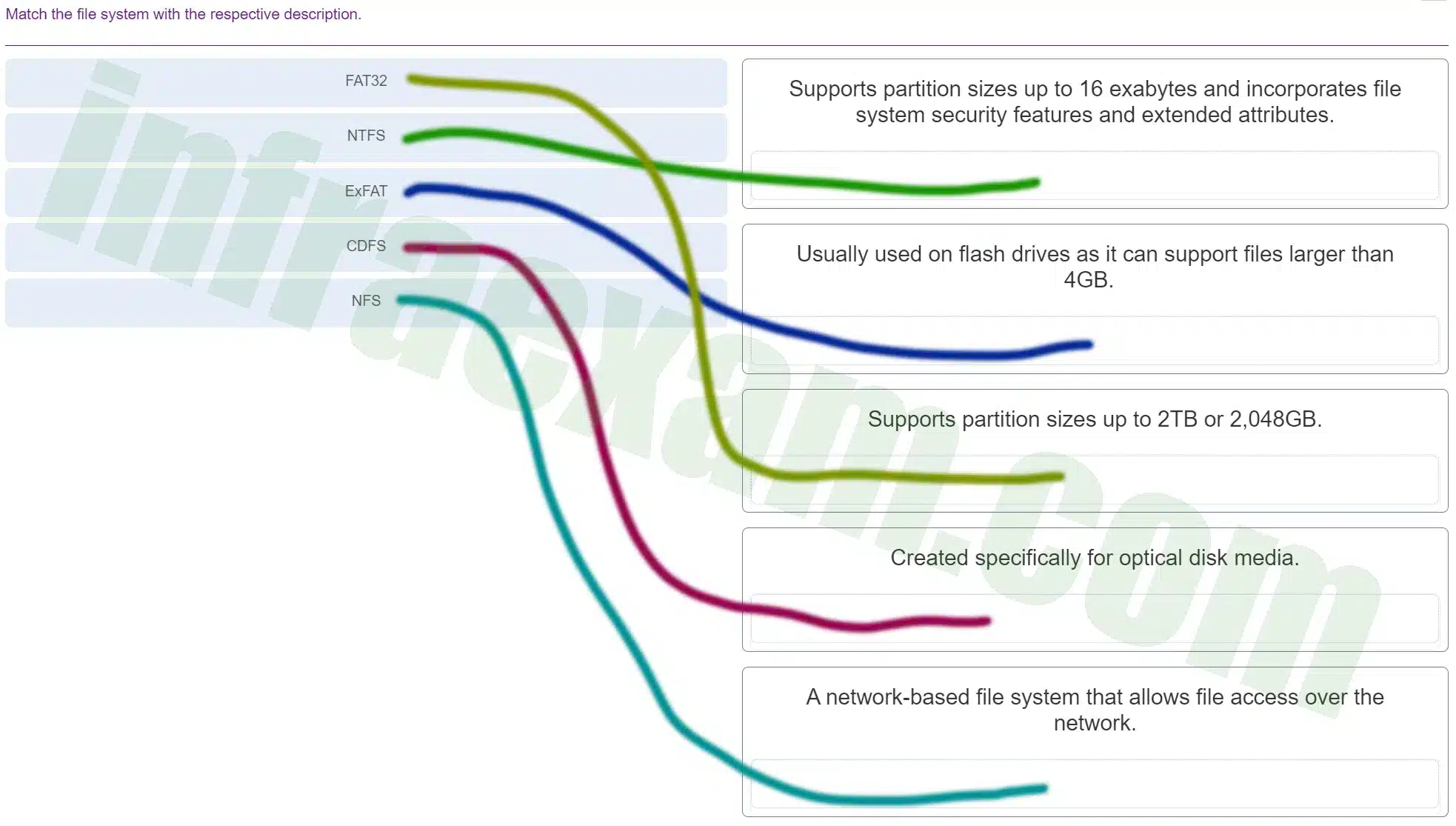
Match the file system with the respective description.
ITE v8.0 – IT Essentials ( Version 8.0) – IT Essentials 8 Final Exam 1 – 14 Answers 010 -
Explanation & Hint:
-
-
A corporation would like to use three or more factors for the password authentication policy. How can this be achieved?
- 2FA
- SFA
- bitlocker
- MFA
Answers Explanation & Hints: MFA (Multi-Factor Authentication) requires users to present at least two, if not more, types of authentication. 2FA (Two-Factor authentication), also sometimes referred to as 2-step verification, is a security approach requiring users to present two factors for authentication for accessing an account. SFA (Single-Factor Authentication) requires users to authenticate with only one type of evidence for authentication, usually a password. Bitlocker encrypts drives.
-
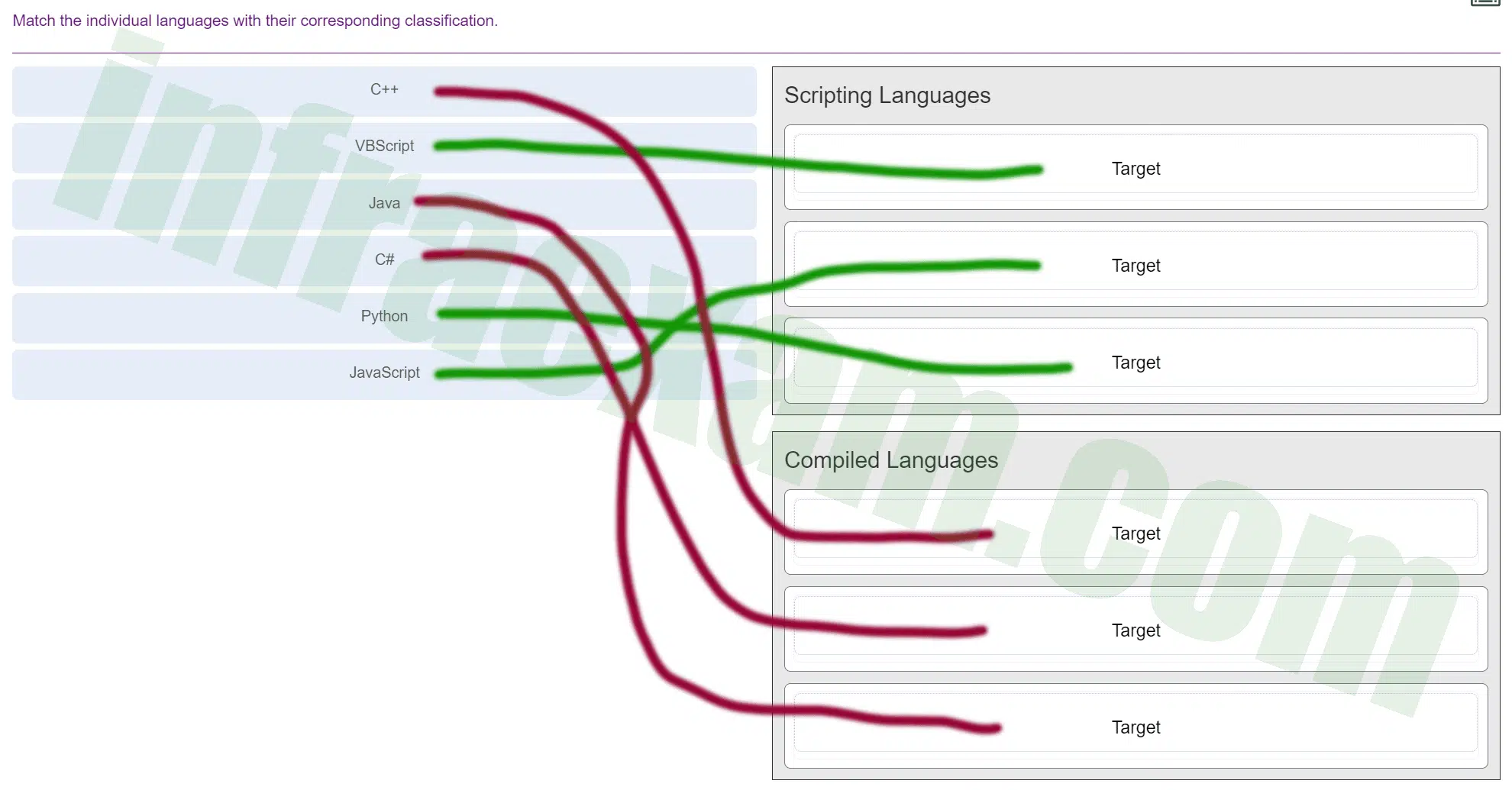
Match the individual languages with their corresponding classification.
ITE v8.0 – IT Essentials ( Version 8.0) – IT Essentials 8 Final Exam 1 – 14 Answers 011 Answers Explanation & Hints: Scripting languages include Windows batch files, PowerShell, Linux shell script, VBScript, JavaScript, and Python. Compiled languages include C, C++, C#, and Java.
-
Which two actions should a technician take if illegal content, such as child pornography, is discovered on the hard drive of a customer computer? (Choose two.)
- Confront the customer immediately.
- Remove and destroy the hard drive.
- Contact a first responder.
- Shut down the computer until authorities arrive.
- Document as much information as possible.
Answers Explanation & Hints: If illegal content is found, begin documentation to build a chain of custody and contact a first responder immediately.
-
What are three pieces of information a level one technician should gather from a customer? (Choose three.)
- contact information
- description of the problem
- details of any recent changes to the computer
- output from diagnostic software
- output from a remote connection to the customer computer
- current CMOS settings
Answers Explanation & Hints: A level one technician should gather information from the customer and solve simple problems. For more advanced diagnostics, opening the computer case, running diagnostics software, and performing remote connections, the problem should be escalated to a level two technician.
-
What two actions are appropriate for a support desk technician to take when assisting customers? (Choose two.)
- Interrupt customers if they start to solve their own problems.
- Comfort a customer by minimizing the customer problem.
- Let a customer finish talking before asking additional questions.
- If you have to put the customer on hold, ask the customer for permission.
- As soon as you detect customer anger, pass the angry customer to the next level.
Answers Explanation & Hints: When dealing with customers, a technician should show professionalism in all aspects. A technician should observe the process before putting a customer on hold. First, let the customer finish speaking. Then, explain that there is need to put the customer on hold for a short period, and ask the customer for permission to do so. Tell the customer that it will be only a few minutes and explain what you will do during the period. When the customer agrees to be put on hold, thank the customer.
-
A support desk technician is dealing with an angry customer. Which two approaches should the technician take in dealing with the customer? (Choose two.)
- Ask socially related questions to direct the customer away from the problem.
- Work to redirect the conversation to solving the problem.
- Immediately transfer the customer to a higher level technician.
- Reply to the customer with the same level of anger.
- Let the customer explain the problem without interrupting.
Answers Explanation & Hints: Angry customers should be allowed to explain the problem, then be redirected to discussing how the problem can be solved. Transferring the customer, replying in a rude tone, and asking unrelated questions will usually increase, not ease, the anger being expressed by the customer.
-
What two kinds of problems should be escalated from a level one technician to a level two technician? (Choose two.)
- problems that require rebooting the equipment
- problems that can be solved in a short time
- problems that are complicated and will take a long time to resolve
- problems that do not fit into the “down call” category
- problems that are beyond the scope of the knowledge of the level one technician
Answers Explanation & Hints: A problem should be escalated to a level two technician when the problem is going to take a long time to fix, is affecting a large number of users, or requires knowledge or expertise that the level one technician does not possess.
-
An IT technician in a service company has provided extensive remote IT support with product deployment for a customer. After the completion of the contract, a complaint is filed against the IT technician for not following company policy by sending unsolicited emails about services and products that are not related to the contract. What two things should the IT support technician have done differently? (Choose two.)
- The IT technician should have researched the company policy about personal communication with customers on company time.
- The IT technician should have used encryption to hide the purpose of the emails.
- The IT technician should have added the customer to a chain letter with many recipients instead.
- The IT technician should have asked the customer if the customer was interested in receiving information regarding other new services and products.
- The IT technician should have requested permission from a supervisor to send the customer emails.
Answers Explanation & Hints: While working with customers both briefly and over an extended period of time, it is possible to form friendly relationships. It is important to always follow company policy and never send unsolicited messages to a customer. Also do not send unsolicited mass mailings or chain letters to customers from a company email address. Any personal relationships should be kept via personal email accounts and should not reflect the IT organization of the employer.
-
A third-party security firm is performing a security audit of a company and recommends the company utilize the Remote Desktop Protocol. What are two characteristics of the Microsoft Remote Desktop Protocol (RDP)? (Choose two.)
- RDP connects on TCP port 22.
- RDP requires a Windows client.
- RDP uses an encrypted session.
- RDP is a command-line network virtual terminal protocol.
- RDP connects on TCP port 3389.
Answers Explanation & Hints: The Remote Desktop protocol (RDP) is used to remotely access a Windows OS. It is a client/server protocol.The port number for RDP is TCP port 3389 and it uses encryption.
-
Which subject area describes collecting and analyzing data from computer systems, networks, and storage devices, as part of an investigation of alleged illegal activity?
- cyber law
- computer forensics
- cryptography
- disaster recovery
Answers Explanation & Hints: The field of computer forensics involves collecting and analyzing data from computer systems, networks, wireless communications, and storage devices.
-
In a computer forensics investigation, which type of data is considered volatile data and can be lost if power is removed from the computer?
- data stored on magnetic disks
- data stored on an internal drive
- data in transit between RAM and the CPU
- data stored on an external drive
Answers Explanation & Hints: Volatile data is a data that is lost when power is turned off, and is located in temporary storage such as RAM, cache, CPU or in transit between them.
-
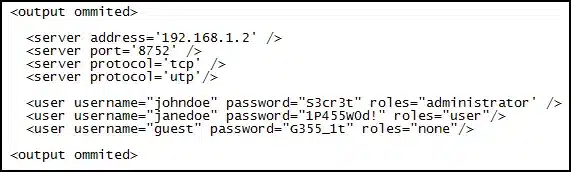
Refer to the exhibit. During the troubleshooting of software that is installed on a computer system, a level one technician requires help from a level two technician. The file shown in the exhibit must be sent to the level two technician. How should the level one technician deliver this file?
ITE v8.0 – IT Essentials ( Version 8.0) – IT Essentials 8 Final Exam 1 – 14 Answers 01 - This file should not be shared with the level two technician.
- Replace all passwords in the file with <password omitted> before emailing the file and then supply the passwords by secure means, if required.
- Send the file as it is to the level two technician.
- Deliver the file in printed format only.
Answers Explanation & Hints: Customer privacy should be maintained. The easiest way to preserve it is removing any occurrence of passwords from the documentation that is being sent to another technician.
If a client password is required to solve the problem, it should be sent to another technician through a specific document.
-
What skill is essential for a level one technician to have?
- the ability to gather relevant information from the customer and pass it to the level two technician so it can be entered into the work order
- the ability to ask the customer relevant questions, and as soon as this information is included in the work order, escalate it to the level two technician
- the ability to translate a description of a customer problem into a few succinct sentences and enter it into the work order
- ability to take the work order prepared by the level two technician and try to resolve the problem
Answers Explanation & Hints: The level one technician must be able to translate the description of a customer problem into a succinct sentence or two that is entered into the work order.
-
What is used to control illegal use of software and content?
- chain of custody
- service level agreement
- End User License Agreement
- digital rights management
Answers Explanation & Hints: Digital rights management, or DRM, is software that is designed to prevent illegal access to digital content.
-
What determines the level of support that a call center technician will provide to an individual customer?
- Support is based on the SLA for that customer.
- All customers receive the same level of support by the call center.
- A level one technician will provide a higher level of support than a level two technician.
- An individual call center technician chooses the level of support based on the time available to assist the customer.
Answers Explanation & Hints: A call center technician must provide the level of support that is outlined in the SLA for that individual customer.
-
A bench technician enters the server room and finds the backup server computer case open. The hard drives containing patient medical data are all physically disconnected from the motherboard and the SATA data cables are hanging outside the case. Which step should the technician immediately take?
- Reconnect the SATA data cables to ensure continued data backup.
- Disconnect the SATA power cables to prevent the loss of persistent data.
- Place the hard drives in an external enclosure and begin backing up the data before releasing the drives to first responders.
- Locate an employee qualified to collect evidence.
- Dust the server computer case for fingerprints.
Answers Explanation & Hints: When a potential crime scene is found, a chain of custody must be observed and followed. The technician should immediately locate another employee who is qualified to collect evidence. Disconnecting or reconnecting the drives or attempting to move data may adversely affect the chain of custody.
-
What is the difference between a scripting language and a compiled language?
- Scripting languages need to be converted into executable code using a compiler, while compiled languages are interpreted as they are executed.
- Compiled languages are executed by the operating system, while scripting languages are executed by the CPU.
- Scripting languages are interpreted and executed line by line when a script is run, while compiled languages need to be converted into executable code.
- Compiled languages are executed by a command interpreter, while scripting languages are executed by the CPU.
Answers Explanation & Hints: A scripting language is different than a compiled language because each line is interpreted and then executed when the script is run. Compiled languages need to be converted into executable code using a compiler. Another difference between the two types of languages is that compiled languages are executed by the CPU while scripting languages are executed by a command interpreter or by the operating system.
-
A technician is upgrading many PCs used within the company. How should the technician dispose of an old power supply?
- Recycle following local regulations.
- Burn it.
- Take it to the garbage dump.
- Destroy it with a hammer.
-
Explanation & Hint: Recycle following local regulations.
When disposing of old power supplies, it is crucial to adhere to local e-waste recycling regulations. These regulations are designed to ensure that the toxic materials often found in electronic components, such as heavy metals and chemicals, are not released into the environment. Recycling also allows for the recovery of valuable materials that can be reused, reducing the need for new raw materials and the energy used to produce them.
Incorrect methods of disposal:
- Burn it: Burning electronic waste is extremely hazardous. It can release toxic fumes and chemicals into the air, which can be harmful to human health and the environment. Moreover, it is illegal in many jurisdictions due to the environmental damage it causes.
- Take it to the garbage dump: Simply throwing electronic waste into the garbage dump is not recommended and often against local laws. Landfills are not equipped to handle e-waste safely, and the toxic substances can leach into the soil and groundwater.
- Destroy it with a hammer: Physical destruction does not eliminate the environmental risk posed by electronic waste. The toxic substances within the power supply can still contaminate the environment, and moreover, this method can be dangerous to the person performing the destruction due to the risk of exposure to hazardous materials and sharp fragments.
-
A technician is upgrading many PCs used within the company. How should the technician dispose of old RAM?
- Recycle following local regulations.
- Take it to the garbage dump.
- Burn it.
- Destroy it with a hammer.
-
Explanation & Hint: Recycle following local regulations.
The correct way to dispose of old RAM (Random Access Memory) modules from computers is to recycle them in accordance with local e-waste recycling regulations. Proper recycling ensures that any valuable materials within the RAM, such as gold, copper, and other metals, can be recovered and reused. Additionally, recycling prevents potentially harmful substances contained in electronic components from damaging the environment.
Incorrect methods of disposal:
- Take it to the garbage dump: Discarding RAM at a garbage dump can lead to environmental harm since landfills are not designed to handle the specific needs of e-waste recycling. Metals and other materials can contaminate soil and water.
- Burn it: Burning RAM is dangerous because it can release toxic chemicals into the air, which is harmful to both human health and the environment. It is also typically illegal to burn e-waste.
- Destroy it with a hammer: Physically destroying RAM does not properly address the environmental and health risks associated with e-waste. It can also be unsafe, potentially creating sharp fragments and exposing the individual to harmful substances.
-
A technician is upgrading many PCs used within the company. How should the technician dispose of old RAM?
- Recycle following local regulations.
- Destroy it with a hammer.
- Take it home.
- Seal in a plastic bag before putting in the garbage.
-
Explanation & Hint: Recycle following local regulations.
Old RAM modules should be recycled according to the e-waste recycling guidelines set by local authorities. Recycling centers have specific processes to safely handle and recover valuable materials from electronic components, and this approach helps to minimize environmental impact.
Incorrect methods of disposal:
- Destroy it with a hammer: This method can be dangerous, potentially causing injury from sharp fragments. It also does not prevent the release of harmful materials into the environment.
- Take it home: Keeping old RAM modules at home serves no purpose if they are no longer useful and could lead to accumulation of hazardous waste.
- Seal in a plastic bag before putting in the garbage: Sealing electronic waste in a plastic bag does not prevent the harmful substances from eventually contaminating the environment. It also likely violates local regulations for e-waste disposal.
-
A technician is upgrading many PCs used within the company. How should the technician dispose of old RAM?
- Recycle following local regulations.
- Give it to your neighbor.
- Take it home.
- Seal in a plastic bag before putting in the garbage.
-
Explanation & Hint: Recycle following local regulations.
The most appropriate and responsible method to dispose of old RAM is to recycle it in accordance with local e-waste regulations. These regulations are designed to ensure the safe and environmentally sound recycling of electronics, which may contain harmful substances as well as recoverable valuable materials.
Incorrect methods of disposal:
- Give it to your neighbor: Passing on electronic waste to another individual does not ensure proper disposal and could potentially pass on the responsibility of proper disposal to someone else who may not be aware of the correct procedures.
- Take it home: Keeping obsolete RAM modules at home does not address their disposal and can lead to unnecessary accumulation of electronic waste.
- Seal in a plastic bag before putting in the garbage: Sealing RAM in a plastic bag and discarding it with regular trash is not environmentally responsible. This method of disposal risks environmental contamination and usually violates local regulations on electronic waste disposal.
-
A technician is upgrading many PCs used within the company. How should the technician dispose of an old inkjet printer cartridge?
- Recycle following local regulations.
- Give it to your neighbor.
- Take it home.
- Seal in a plastic bag before putting in the garbage.
-
Explanation & Hint: Recycle following local regulations.
Old inkjet printer cartridges should be recycled according to local regulations. Many manufacturers and retailers offer recycling programs specifically for ink cartridges, as these can often be refilled or remanufactured, reducing environmental impact and saving resources.
Incorrect methods of disposal:
- Give it to your neighbor: This does not ensure the cartridge will be disposed of responsibly and simply transfers the responsibility to someone else.
- Take it home: Keeping old cartridges at home does not solve the problem of disposal and may lead to unnecessary accumulation of waste.
- Seal in a plastic bag before putting in the garbage: Disposing of ink cartridges in the regular trash, even if sealed in a plastic bag, can be harmful to the environment. The residual ink can leak and contaminate soil and water, and the plastic used in cartridges can take a very long time to decompose.
-
A technician is upgrading many PCs used within the company. How should the technician dispose of an old motherboard?
- Recycle following local regulations.
- Take it home.
- Give it to your neighbor.
- Seal in a plastic bag before putting in the garbage.
-
Explanation & Hint: Recycle following local regulations.
An old motherboard should be disposed of through recycling in accordance with local e-waste regulations. Motherboards contain various precious metals and potentially hazardous materials that need to be properly handled to prevent environmental contamination and to recover valuable resources.
Incorrect methods of disposal:
- Take it home: Keeping an old motherboard at home doesn’t ensure proper disposal and may lead to the accumulation of electronic waste.
- Give it to your neighbor: This action doesn’t guarantee that the motherboard will be disposed of properly and is simply passing the responsibility to another person.
- Seal in a plastic bag before putting in the garbage: Disposing of a motherboard in the regular trash is not recommended and could be against local regulations. Motherboards can contain toxic substances that can leach into the environment if not disposed of properly.
-
A technician is upgrading many PCs used within the company. How should the technician dispose of an old hard drive?
- Recycle following local regulations.
- Seal in a cardboard box.
- Give it to your neighbor.
- Take it home.
-
Explanation & Hint: Recycle following local regulations.
Old hard drives should be disposed of by recycling according to local e-waste regulations. Hard drives can contain both recyclable materials and hazardous substances, and proper recycling ensures that these materials are handled responsibly. Additionally, hard drives often contain sensitive data, so they should be wiped or destroyed to prevent data breaches before recycling.
Incorrect methods of disposal:
- Seal in a cardboard box: Simply sealing a hard drive in a cardboard box does not address the proper disposal of electronic waste or the potential for data breach.
- Give it to your neighbor: This could result in a security risk if the hard drive still contains data, and it also shifts the responsibility of proper disposal to someone else.
- Take it home: Keeping an old hard drive at home does not ensure that it will be properly disposed of and can lead to the accumulation of e-waste.
-
A technician is upgrading many PCs used within the company. How should the technician dispose of an old hard drive?
- Recycle following local regulations.
- Fix it with duct tape and reuse it.
- Give it to your neighbor.
- Take it home.
-
Explanation & Hint: Recycle following local regulations.
Disposing of an old hard drive should be done by recycling in accordance with local e-waste regulations. This ensures that the device is disposed of in an environmentally responsible way and that any data contained on the drive is properly handled to prevent any security issues.
Incorrect methods of disposal:
- Fix it with duct tape and reuse it: Repairing a hard drive with duct tape is not a reliable fix and could lead to data loss or hardware failure. Reusing a potentially faulty hard drive is not recommended.
- Give it to your neighbor: This does not ensure that the hard drive will be disposed of securely or responsibly. There is also a risk of unintended data transfer.
- Take it home: Keeping an old hard drive at home does not solve the issue of disposal and can result in the accumulation of electronic waste. It also poses a risk if there is any sensitive data on the drive that has not been securely erased.
-
A technician is upgrading many PCs used within the company. How should the technician dispose of an old battery?
- Recycle following local regulations.
- Fix it with duct tape and reuse it.
- Throw it away.
- Bury it.
-
Explanation & Hint: Recycle following local regulations.
The proper way to dispose of an old battery from a PC or any electronic device is to recycle it in accordance with local regulations. Batteries contain chemicals and metals that can be harmful to the environment if not disposed of correctly. Recycling programs are designed to handle these materials safely.
Incorrect methods of disposal:
- Fix it with duct tape and reuse it: Repairing a battery with duct tape is not safe and is generally ineffective. Batteries that are damaged or no longer hold a charge should be properly recycled, not reused.
- Throw it away: Disposing of batteries in regular trash can be dangerous and is often illegal. Batteries can leak harmful chemicals into the environment and pose a risk to waste management workers.
- Bury it: Burying a battery is extremely harmful to the environment. It can lead to soil and water contamination and poses significant ecological risks.
-
A technician is upgrading many PCs used within the company. How should the technician dispose of an old battery?
- Recycle following local regulations.
- Throw it away.
- Bury it.
- Burn it.
-
Explanation & Hint: Recycle following local regulations.
The most appropriate way to dispose of an old battery is to recycle it in accordance with local e-waste recycling regulations. This ensures that the battery is handled in an environmentally responsible manner and that any hazardous materials within the battery are safely processed.
Incorrect methods of disposal:
- Throw it away: Disposing of batteries in regular trash is not recommended and often against local regulations. Batteries can contain harmful chemicals that can leak into the environment.
- Bury it: Burying batteries can lead to soil and water contamination as the toxic substances in batteries can leach into the ground.
- Burn it: Burning batteries is extremely dangerous. It can lead to the release of toxic fumes and chemicals, posing a significant health and environmental risk.
-
What ACPI power state describes when the CPU is off and the RAM is set to a slow refresh rate, often called suspend mode?
- S3
- S4
- S2
- S5
-
Explanation & Hint:
-
What ACPI power state describes when the computer is on and the CPU is running?
- S0
- S4
- S3
- S5
-
Explanation & Hint:
-
What ACPI power state describes when the CPU and RAM are off and the contents of RAM have been saved to a temporary file on the hard drive?
- S4
- S3
- S2
- S5
-
Explanation & Hint:
-
What ACPI power state describes when the CPU and RAM are still receiving power but unused devices are powered down?
- S1
- S4
- S3
- S5
-
Explanation & Hint:
-
What ACPI power state describes when the CPU and RAM are still receiving power but unused devices are powered down?
- S1
- S4
- S3
- S2
-
Explanation & Hint:
-
What ACPI power state describes when the CPU and RAM are off and the contents of RAM have been saved to a temporary file on the hard drive?
- S4
- S2
- S3
- S1
-
Explanation & Hint:
-
What ACPI power state describes when the computer is off?
- S5
- S2
- S3
- S1
-
Explanation & Hint:
-
What ACPI power state describes when the CPU is off, but the RAM is refreshed?
- S2
- S3
- S4
- S1
-
Explanation & Hint:
-
What ACPI power state describes when the CPU and RAM are still receiving power but unused devices are powered down?
- S1
- S2
- S3
- S0
-
Explanation & Hint:
-
What ACPI power state describes when the CPU and RAM are off and the contents of RAM have been saved to a temporary file on the hard drive?
- S4
- S1
- S2
- S0
-
Explanation & Hint:
-
In which situation would an ESD strike potentially cause harm to the PC?
- when replacing a mechanical hard drive with an M.2 SSD
- when replacing high voltage laser printer parts
- when working in a corporate environment that has carpet installed under tower PCs
- when walking across a carpeted area and then touching a keyboard that is attached to a tower PC
-
Explanation & Hint: An ESD (Electrostatic Discharge) strike can potentially cause harm to a PC in the following situation:
When replacing a mechanical hard drive with an M.2 SSD
During this process, there’s direct interaction with the internal components of the PC. ESD can easily damage sensitive electronic parts like SSDs, especially if proper ESD protection measures (like using an ESD wrist strap or mat) are not taken. The other scenarios, while they may involve the generation of static electricity, are less likely to directly result in ESD damage to the PC’s internal components:
- When replacing high voltage laser printer parts: While working with high voltage parts does require caution, it’s more about electrical safety than ESD harm to the PC.
- When working in a corporate environment that has carpet installed under tower PCs: The presence of carpet can increase the likelihood of building up static electricity, but the risk of ESD damage is more about the direct handling of the internal components than just being in an environment with carpet.
- When walking across a carpeted area and then touching a keyboard that is attached to a tower PC: While this can generate static, the keyboard itself often has enough insulation to prevent ESD from reaching the internal components of the PC. The risk of damaging the PC through ESD in this scenario is relatively low compared to directly handling internal components like an SSD.
-
An instructor has given a student an assignment to assemble a PC. In which situation should the student be aware that ESD is an issue?
- when installing RAM
- when working in a corporate environment that has carpet installed under tower PCs
- when walking across a carpeted area and then touching a keyboard that is attached to a tower PC
- when installing a UPS
-
Explanation & Hint: The student should be aware that ESD (Electrostatic Discharge) is an issue when installing RAM. RAM modules are sensitive to static electricity, and ESD can cause damage to these components. When handling and installing RAM, it’s important to take precautions against ESD, such as using an ESD wrist strap or working on an anti-static mat.
The other situations, while they involve environments or actions that could generate static electricity, are less directly related to the risk of ESD damage to sensitive internal PC components:
- When working in a corporate environment that has carpet installed under tower PCs: While carpeted floors can increase the risk of generating static electricity, the risk of ESD damage is more significant when directly handling internal components.
- When walking across a carpeted area and then touching a keyboard that is attached to a tower PC: This action can generate static electricity, but the risk of transferring that static to the PC’s internal components through a keyboard is relatively low.
- When installing a UPS (Uninterruptible Power Supply): The main concern with installing a UPS is electrical safety, rather than ESD. While it’s always good to be cautious about static electricity, the components of a UPS are not as sensitive to ESD as components like RAM or a motherboard.
-
In which situation would an ESD strike potentially cause harm to the PC?
- when replacing a mechanical hard drive with an M.2 SSD
- when installing an additional display in a workplace cubicle
- when working in a corporate environment that has carpet installed under tower PCs
- when walking across a carpeted area and then touching a keyboard that is attached to a tower PC
-
Explanation & Hint: An ESD (Electrostatic Discharge) strike could potentially cause harm to the PC in the following situation:
When replacing a mechanical hard drive with an M.2 SSD
This scenario involves direct handling of sensitive internal PC components. M.2 SSDs, like many other internal computer components, are susceptible to damage from electrostatic discharge. It’s crucial to use proper ESD protection measures, such as grounding yourself with an ESD wrist strap, when performing such tasks.
The other scenarios, while they may involve situations where static electricity can be generated, are less likely to result in ESD damage to sensitive internal components of the PC:
- When installing an additional display in a workplace cubicle: This typically involves external peripherals, which are generally designed to be more robust against ESD compared to internal components.
- When working in a corporate environment that has carpet installed under tower PCs: While carpets can contribute to the generation of static electricity, the risk of ESD damage is more significant when directly handling internal components rather than merely working in an environment with carpet.
- When walking across a carpeted area and then touching a keyboard that is attached to a tower PC: Although walking across a carpet can generate static electricity, the risk of transferring that static through a keyboard to damage internal PC components is relatively low. Keyboards and other external peripherals usually have some level of ESD protection built-in.
-
An instructor has given a student an assignment to assemble a PC. In which situation should the student be aware that ESD is an issue?
- when installing a processor
- when using a grounded mat and working on a computer on an ungrounded workbench
- when working in a corporate environment that has carpet installed under tower PCs
- when walking across a carpeted area and then touching a keyboard that is attached to a tower PC
-
Explanation & Hint: The student should be most aware that ESD (Electrostatic Discharge) is an issue when installing a processor. The processor (CPU) is a highly sensitive component, and even a small amount of electrostatic discharge can cause damage. When handling and installing the processor, it’s crucial to use ESD protection measures like grounding yourself with an ESD wrist strap and working on an anti-static mat.
The other scenarios, while related to environments or actions that could generate static electricity, are less directly related to a high risk of ESD damage:
- Using a grounded mat and working on a computer on an ungrounded workbench: While using a grounded mat is a good practice, the ideal setup is to have both the mat and the workbench grounded. However, the risk is lower compared to directly handling sensitive components like a CPU.
- When working in a corporate environment that has carpet installed under tower PCs: Carpeted floors can increase the risk of generating static electricity, but the risk of ESD damage is more significant when directly handling internal components of the PC.
- When walking across a carpeted area and then touching a keyboard that is attached to a tower PC: This can generate static electricity, but the risk of transferring that static to internal PC components via a keyboard is relatively low. Keyboards generally have some level of ESD protection.
-
A technician is about to begin preventive maintenance on a company PC. In which situation would ESD be an issue?
- when replacing a motherboard
- while attaching speakers to a surround sound card
- when working in a corporate environment that has carpet installed under tower PCs
- when walking across a carpeted area and then touching a keyboard that is attached to a tower PC
-
Explanation & Hint: ESD (Electrostatic Discharge) would be an issue when replacing a motherboard. The motherboard is a crucial component of the PC that contains many sensitive electronic parts. Handling the motherboard without proper ESD precautions (like using an ESD wrist strap or working on an anti-static mat) could result in damaging the board due to static discharge.
The other scenarios, while related to static electricity generation, pose a lesser risk of ESD damage to sensitive internal PC components:
- While attaching speakers to a surround sound card: This involves external peripherals, which are generally more robust against ESD compared to internal components like a motherboard.
- When working in a corporate environment that has carpet installed under tower PCs: While carpets can increase the generation of static electricity, the risk of ESD damage is more about direct handling of internal PC components than the environment itself.
- When walking across a carpeted area and then touching a keyboard that is attached to a tower PC: This action can generate static electricity, but transferring this static to internal components of the PC via a keyboard is relatively low risk. External devices like keyboards typically have some level of ESD protection.
-
A person has started a new technical job. In which situation would ESD be an issue?
- when installing a processor
- when installing a dual-voltage power supply
- when replacing high voltage laser printer parts
- while exchanging one laptop AC adapter with one that is not from the original equipment manufacturer
-
Explanation & Hint: ESD (Electrostatic Discharge) would be an issue when installing a processor. The processor, or CPU, is a highly sensitive component within a computer, and exposure to ESD can cause damage to it. It’s crucial for the person to use proper ESD protection measures, such as grounding themselves with an ESD wrist strap or working on an anti-static mat, when handling and installing the processor.
The other scenarios, while important in terms of safety and compatibility, are less about ESD risks:
- When installing a dual-voltage power supply: The primary concern here is ensuring the correct setting for the local power voltage and safe installation, rather than ESD.
- When replacing high voltage laser printer parts: Safety concerns with high voltage parts are more about electrical shock hazards rather than ESD.
- While exchanging one laptop AC adapter with one that is not from the original equipment manufacturer: The main concern here is ensuring that the replacement adapter is compatible and meets the required specifications for the laptop. ESD is not a significant issue in this scenario.
-
A technician is about to begin preventive maintenance on a company PC. In which situation would ESD be an issue?
- when replacing a motherboard
- when installing a UPS
- while exchanging one laptop AC adapter with one that is not from the original equipment manufacturer
- when installing a dual-voltage power supply
-
Explanation & Hint: ESD (Electrostatic Discharge) would be an issue when replacing a motherboard. During this process, the technician is directly handling sensitive electronic components within the PC. The motherboard is particularly susceptible to damage from ESD, and appropriate precautions, such as using an ESD wrist strap or working on an anti-static mat, are essential to prevent damaging the motherboard.
The other scenarios, while important for safety and compatibility, are less concerned with ESD risks:
- When installing a UPS (Uninterruptible Power Supply): The main concern here is electrical safety, ensuring that the UPS is correctly installed and compatible with the system, rather than ESD.
- While exchanging one laptop AC adapter with one that is not from the original equipment manufacturer: The key concern in this situation is ensuring that the replacement adapter is compatible and meets the laptop’s voltage and current requirements. ESD is not a significant risk in this scenario.
- When installing a dual-voltage power supply: The primary focus here is on safely installing the power supply and setting it to the correct voltage for the region. ESD is less of a concern compared to handling sensitive internal components like a motherboard.
-
In which situation would an ESD strike potentially cause harm to the PC?
- when replacing a mechanical hard drive with an M.2 SSD
- while exchanging one laptop AC adapter with one that is not from the original equipment manufacturer
- when replacing high voltage laser printer parts
- when installing a dual-voltage power supply
-
Explanation & Hint: An ESD (Electrostatic Discharge) strike could potentially cause harm to the PC when replacing a mechanical hard drive with an M.2 SSD. This situation involves direct handling of sensitive internal PC components. Solid State Drives (SSDs), including M.2 types, are susceptible to damage from electrostatic discharge. Therefore, it’s crucial to take ESD precautions, such as using an ESD wrist strap or working on an anti-static mat, when handling and installing these components.
The other scenarios involve less risk of ESD damage:
- While exchanging one laptop AC adapter with one that is not from the original equipment manufacturer: This involves handling external components, where the risk of ESD damage to the internal parts of the laptop is minimal.
- When replacing high voltage laser printer parts: The primary concern in this case is ensuring electrical safety due to the high voltage, rather than ESD.
- When installing a dual-voltage power supply: Here, the main focus should be on electrical safety and correctly setting the voltage. ESD is not a major concern in this situation as it involves less direct interaction with sensitive internal electronic components.
-
An instructor has given a student an assignment to assemble a PC. In which situation should the student be aware that ESD is an issue?
- when installing RAM
- when walking across a carpeted area and then touching a keyboard that is attached to a tower PC
- while exchanging one laptop AC adapter with one that is not from the original equipment manufacturer
- when installing a dual-voltage power supply
-
Explanation & Hint: The student should be aware that ESD (Electrostatic Discharge) is an issue when installing RAM. RAM (Random Access Memory) modules are sensitive to static electricity, and ESD can cause damage to these components. When handling and installing RAM, it’s important to take precautions against ESD, such as using an ESD wrist strap or working on an anti-static mat.
The other situations, while related to environments or actions that could generate static electricity, are less directly related to a high risk of ESD damage:
- When walking across a carpeted area and then touching a keyboard that is attached to a tower PC: This can generate static electricity, but the risk of transferring that static to the internal components of the PC through a keyboard is relatively low.
- While exchanging one laptop AC adapter with one that is not from the original equipment manufacturer: This involves handling external peripherals, where the risk of ESD damage to the laptop’s internal components is minimal.
- When installing a dual-voltage power supply: The main concern here is ensuring proper installation and electrical safety, especially the correct voltage setting. The risk of ESD damage is not as pronounced in this scenario compared to handling sensitive components like RAM.
-
In which situation would an ESD strike potentially cause harm to the PC?
- when replacing a mechanical hard drive with an M.2 SSD
- when installing an additional display in a workplace cubicle
- while exchanging one laptop AC adapter with one that is not from the original equipment manufacturer
- when installing a dual-voltage power supply
-
Explanation & Hint: An ESD (Electrostatic Discharge) strike could potentially cause harm to the PC when replacing a mechanical hard drive with an M.2 SSD. This situation involves directly handling sensitive internal PC components. M.2 SSDs, like many other internal computer parts, are susceptible to damage from electrostatic discharge. It’s important to use proper ESD protection measures, such as grounding yourself with an ESD wrist strap, when performing such tasks.
The other scenarios, while they may involve situations where static electricity can be generated, are less likely to result in ESD damage to sensitive internal components of the PC:
- When installing an additional display in a workplace cubicle: This typically involves external peripherals, which are generally designed to be more robust against ESD compared to internal components like an SSD.
- While exchanging one laptop AC adapter with one that is not from the original equipment manufacturer: This action involves external components and peripherals, where the risk of ESD damage to the internal parts of the laptop is minimal.
- When installing a dual-voltage power supply: The main concern here is electrical safety, ensuring that the power supply is correctly installed and set to the appropriate voltage, rather than ESD.
-
A client packet is received by a server. The packet has a destination port number of 3389. What service application is the client requesting?
- RDP
- SSH
- Telnet
- SMTP
-
Explanation & Hint: The client is requesting the RDP (Remote Desktop Protocol) service. The port number 3389 is commonly associated with RDP, which is used for remote desktop connections to Windows-based systems. This protocol allows users to connect to and control another computer over a network connection.
The other services mentioned use different port numbers:
- SSH (Secure Shell) typically uses port 22.
- Telnet usually operates on port 23.
- SMTP (Simple Mail Transfer Protocol), used for email transmission, typically uses port 25.
-
A client packet is received by a server. The packet has a destination port number of 427. What service application is the client requesting?
- SLP
- SSH
- Telnet
- SMTP
-
Explanation & Hint: The client is requesting the SLP (Service Location Protocol) service. The port number 427 is commonly associated with SLP, which is used for network service discovery in local area networks. This protocol allows computers and other devices to find services in a local area network without prior configuration.
The other services mentioned use different port numbers:
- SSH (Secure Shell) typically uses port 22.
- Telnet usually operates on port 23.
- SMTP (Simple Mail Transfer Protocol), used for email transmission, typically uses port 25.
-
A client packet is received by a server. The packet has a destination port number of 53. What service application is the client requesting?
- DNS
- SSH
- Telnet
- SMTP
-
Explanation & Hint: The client is requesting the DNS (Domain Name System) service. The port number 53 is commonly associated with DNS, which is used for translating domain names into IP addresses.
The other services mentioned use different port numbers:
- SSH (Secure Shell) typically uses port 22.
- Telnet usually operates on port 23.
- SMTP (Simple Mail Transfer Protocol), used for email transmission, typically uses port 25.
-
A client packet is received by a server. The packet has a destination port number of 67. What service application is the client requesting?
- DHCP
- SSH
- Telnet
- SMTP
-
Explanation & Hint: The client is requesting the DHCP (Dynamic Host Configuration Protocol) service. The port number 67 is commonly associated with the server side of the DHCP process, which is used for automatically assigning IP addresses and other network configuration parameters to devices on a network.
The other services mentioned use different port numbers:
- SSH (Secure Shell) typically uses port 22.
- Telnet usually operates on port 23.
- SMTP (Simple Mail Transfer Protocol), used for email transmission, typically uses port 25.
-
A client packet is received by a server. The packet has a destination port number of 443. What service application is the client requesting?
- HTTPS
- SSH
- Telnet
- SMTP
-
Explanation & Hint: The client is requesting the HTTPS (Hypertext Transfer Protocol Secure) service. The port number 443 is commonly associated with HTTPS, which is used for secure communication over a computer network within a web browser. HTTPS provides encrypted communication and secure identification of a network web server.
The other services mentioned use different port numbers:
- SSH (Secure Shell) typically uses port 22.
- Telnet usually operates on port 23.
- SMTP (Simple Mail Transfer Protocol), used for email transmission, typically uses port 25.
-
A client packet is received by a server. The packet has a destination port number of 69. What service application is the client requesting?
- TFTP
- SSH
- Telnet
- SMTP
-
Explanation & Hint: The client is requesting the TFTP (Trivial File Transfer Protocol) service. The port number 69 is commonly associated with TFTP, which is a simple protocol used for transferring files. TFTP is often used for transferring small files such as boot images or configurations over a network.
The other services mentioned use different port numbers:
- SSH (Secure Shell) typically uses port 22.
- Telnet usually operates on port 23.
- SMTP (Simple Mail Transfer Protocol), used for email transmission, typically uses port 25.
-
A client packet is received by a server. The packet has a destination port number of 445. What service application is the client requesting?
- SMB/CIFS
- SSH
- Telnet
- SMTP
-
Explanation & Hint: The client is requesting the SMB/CIFS (Server Message Block/Common Internet File System) service. The port number 445 is commonly associated with SMB/CIFS, which is a network file sharing protocol used for providing shared access to files, printers, and serial ports, as well as miscellaneous communications between nodes on a network.
The other services mentioned use different port numbers:
- SSH (Secure Shell) typically uses port 22.
- Telnet usually operates on port 23.
- SMTP (Simple Mail Transfer Protocol), used for email transmission, typically uses port 25.
-
A client packet is received by a server. The packet has a destination port number of 548. What service application is the client requesting?
- AFP
- HTTP
- TFTP
- POP3
-
Explanation & Hint: The client is requesting the AFP (Apple Filing Protocol) service. The port number 548 is commonly associated with AFP, which is a protocol that offers file services for macOS and other Apple devices. AFP is primarily used for file sharing and network backups within Apple’s ecosystem.
The other services mentioned use different port numbers:
- HTTP (Hypertext Transfer Protocol) typically uses port 80.
- TFTP (Trivial File Transfer Protocol) usually operates on port 69.
- POP3 (Post Office Protocol version 3), used for email retrieval, typically uses port 110.
-
A client packet is received by a server. The packet has a destination port number of 80. What service application is the client requesting?
- HTTP
- POP3
- TFTP
- NetBIOS (NetBT)
-
Explanation & Hint: The client is requesting the HTTP (Hypertext Transfer Protocol) service. The port number 80 is commonly associated with HTTP, which is the primary protocol used for transmitting web pages on the internet. When a user accesses a website through a web browser without specifying a port, it typically defaults to port 80 for HTTP.
The other services mentioned use different port numbers:
- POP3 (Post Office Protocol version 3), used for email retrieval, typically uses port 110.
- TFTP (Trivial File Transfer Protocol) usually operates on port 69.
- NetBIOS (NetBT), used for network basic input/output system services, typically uses ports 137-139.
-
A client packet is received by a server. The packet has a destination port number of 3389. What service application is the client requesting?
- RDP
- HTTP
- TFTP
- POP3
-
Explanation & Hint: The client is requesting the RDP (Remote Desktop Protocol) service. The port number 3389 is commonly associated with RDP, which is used for remote desktop connections to Windows-based systems. This protocol allows users to connect to and control another computer over a network connection.
The other services mentioned use different port numbers:
- HTTP (Hypertext Transfer Protocol) typically uses port 80.
- TFTP (Trivial File Transfer Protocol) usually operates on port 69.
- POP3 (Post Office Protocol version 3), used for email retrieval, typically uses port 110.
-
A computer technician is installing a RAID. If the RAID uses striping with parity, which RAID level is the technician using?
- 5
- 0
- 1
- 4
-
Explanation & Hint: The technician is installing a RAID 5. RAID 5 uses striping with parity, allowing for data and parity information to be distributed across all the drives in the array. This setup provides a balance of performance, good data throughput, fault tolerance, and efficient use of disk capacity. RAID 5 requires a minimum of three disks to implement.
The other RAID levels mentioned have different characteristics:
- RAID 0 uses striping without parity or mirroring, offering improved performance but no fault tolerance.
- RAID 1 involves mirroring, where data is duplicated on two or more disks, offering fault tolerance but no performance improvement in writing data.
- RAID 4 uses block-level striping with a dedicated parity disk, which is different from RAID 5’s distributed parity approach.
-
A computer technician is installing a RAID. If the RAID uses mirroring and striping, which RAID level is the technician using?
- 10
- 0
- 1
- 8
-
Explanation & Hint: The technician is installing a RAID 10 (also known as RAID 1+0). RAID 10 combines mirroring and striping: it mirrors each drive in the RAID (this is the RAID 1 aspect) and then stripes across these mirrored sets (this is the RAID 0 aspect). RAID 10 offers both the high performance of striping (RAID 0) and the redundancy of mirroring (RAID 1). This configuration requires a minimum of four drives and provides fault tolerance as well as improved read/write speeds.
The other RAID levels mentioned have different characteristics:
- RAID 0 involves striping data across multiple disks for performance improvement but does not offer redundancy.
- RAID 1 consists of data mirroring, where data is duplicated on two or more disks, offering redundancy and fault tolerance but no striping for performance.
- RAID 8 is not a standard RAID level.
-
A computer technician is installing a RAID. If the RAID uses striping with parity, which RAID level is the technician using?
- 5
- 10
- 6
- 4
-
Explanation & Hint: If the RAID configuration uses striping with parity, the technician could be installing either RAID 5 or RAID 6.
- RAID 5 uses striping with parity and distributes both data and parity information across all the drives in the array. It requires a minimum of three disks and can tolerate the failure of one drive.
- RAID 6 also uses striping with parity but adds an extra layer of fault tolerance by using two parity blocks instead of one. RAID 6 can withstand the failure of two drives. It requires a minimum of four disks.
RAID 4 is similar to RAID 5 in that it uses striping with parity, but it dedicates a single disk to storing parity information, which is different from RAID 5’s distributed parity approach.
RAID 10 (not listed in your options) uses mirroring and striping but does not use parity.
-
A computer technician is installing a RAID. If the RAID uses striping, which RAID level is the technician using?
- 0
- 10
- 6
- 2
-
Explanation & Hint: If the RAID configuration uses only striping (without mirroring or parity), the technician is installing RAID 0.
- RAID 0 involves striping data across multiple disks, which improves performance by increasing read/write speeds. However, it does not provide redundancy or fault tolerance. If one disk fails in a RAID 0 array, all data on the array is lost.
The other RAID levels mentioned have different characteristics:
- RAID 10 combines mirroring and striping, offering both performance improvements and fault tolerance.
- RAID 6 uses striping with double parity, providing fault tolerance by allowing two disk failures within the array.
- RAID 2, which is rarely used and largely obsolete, uses bit-level striping with a Hamming code for error correction. RAID 2 is not typically found in modern implementations.
-
A computer technician is installing a RAID. If the RAID uses striping with double parity, which RAID level is the technician using?
- 6
- 10
- 5
- 7
-
Explanation & Hint: If the RAID configuration uses striping with double parity, the technician is installing RAID 6.
- RAID 6 uses striping with double parity, which means it provides fault tolerance by allowing for the failure of up to two drives within the array without data loss. It provides a higher level of redundancy compared to RAID 5, which uses single parity.
The other RAID levels mentioned have different characteristics:
- RAID 10 combines mirroring and striping for both performance improvement and fault tolerance.
- RAID 5 uses striping with single parity, allowing for the failure of one drive without data loss.
- RAID 7 is not a commonly used RAID level in standard configurations.
-
A computer technician is installing a RAID. If the RAID uses mirroring, which RAID level is the technician using?
- 1
- 10
- 6
- 3
-
Explanation & Hint: If the RAID configuration uses mirroring, the technician is installing RAID 1.
- RAID 1 involves mirroring, where data is duplicated on two or more drives. This provides fault tolerance, as if one drive fails, the data is still accessible from the mirrored drive(s). It doesn’t provide the striping for performance improvement seen in RAID 10 (which combines mirroring and striping) or the parity used in RAID 3 or RAID 6 for fault tolerance.
The other RAID levels mentioned have different characteristics:
- RAID 10 combines mirroring and striping for both performance improvement and fault tolerance.
- RAID 6 uses striping with double parity for fault tolerance.
- RAID 3 uses byte-level striping with dedicated parity, while RAID 3 is a bit-level striping with dedicated parity. Both are less common RAID levels compared to RAID 1 and RAID 10.
-
A computer technician is installing a RAID. If the RAID uses striping with double parity, which RAID level is the technician using?
- 6
- 0
- 1
- 7
-
Explanation & Hint: If the RAID configuration uses striping with double parity, the technician is installing RAID 6.
- RAID 6 uses striping with double parity, which provides a high level of fault tolerance by allowing for the failure of up to two drives within the array without data loss. It is a robust choice for data protection in RAID configurations.
The other RAID levels mentioned have different characteristics:
- RAID 0 involves striping without parity or mirroring, offering improved performance but no fault tolerance.
- RAID 1 involves mirroring, where data is duplicated on two or more drives, offering fault tolerance but no striping for performance.
- RAID 7 is not a commonly used RAID level in standard configurations.
-
A computer technician is installing a RAID. If the RAID uses mirroring, which RAID level is the technician using?
- 1
- 0
- 5
- 3
-
Explanation & Hint: If the RAID configuration uses mirroring, the technician is installing RAID 1.
- RAID 1 involves mirroring, where data is duplicated on two or more drives. This provides fault tolerance, as if one drive fails, the data is still accessible from the mirrored drive(s). RAID 1 is primarily focused on redundancy and does not provide the striping for performance improvement seen in other RAID levels like RAID 0 or the distributed parity used in RAID 5.
The other RAID levels mentioned have different characteristics:
- RAID 0 involves striping data across multiple disks for performance improvement but does not offer redundancy.
- RAID 5 uses striping with single parity, offering a balance of performance and fault tolerance.
- RAID 3 uses byte-level striping with dedicated parity, while RAID 3 is a bit-level striping with dedicated parity. Both are less common RAID levels compared to RAID 1 and RAID 5.
-
A computer technician is installing a RAID. If the RAID uses striping, which RAID level is the technician using?
- 0
- 1
- 5
- 2
-
Explanation & Hint: If the RAID configuration uses striping without mirroring or parity, the technician is installing RAID 0.
- RAID 0 involves striping data across multiple disks, which improves performance by increasing read/write speeds. However, it does not provide redundancy or fault tolerance. If one drive fails in a RAID 0 array, all data on the array is lost. RAID 0 is primarily used for performance improvement and does not provide data protection.
The other RAID levels mentioned have different characteristics:
- RAID 1 involves mirroring, where data is duplicated on two or more drives, offering fault tolerance but not striping for performance.
- RAID 5 uses striping with single parity, offering both performance improvement and fault tolerance.
- RAID 2 is not a commonly used RAID level in standard configurations.
-
A computer technician is installing a RAID. If the RAID uses striping with parity, which RAID level is the technician using?
- 5
- 6
- 1
- 4
-
Explanation & Hint: If the RAID configuration uses striping with parity, the technician is installing RAID 5.
- RAID 5 uses striping with distributed parity, where both data and parity information are distributed across all the drives in the array. It provides a good balance between performance and fault tolerance and can tolerate the failure of one drive without data loss. RAID 5 is a commonly used RAID level for data protection in many environments.
The other RAID levels mentioned have different characteristics:
- RAID 6 uses striping with double parity and can tolerate the failure of up to two drives.
- RAID 1 involves mirroring, where data is duplicated on two or more drives, offering fault tolerance but not striping for performance.
- RAID 4 uses block-level striping with a dedicated parity disk, which is different from RAID 5’s distributed parity approach.
-
A PC technician has been asked by a supervisor to recommend a security solution for drive redundancy. Which security technique should the technician recommend?
- Implement a RAID.
- Buy an ASA.
- Buy an IPS.
- Implement dual authentication.
-
Explanation & Hint: The security technique that the PC technician should recommend for drive redundancy is to implement a RAID (Redundant Array of Independent Disks).
- RAID provides drive redundancy by combining multiple physical disks into a single logical unit. Depending on the RAID level chosen (such as RAID 1 or RAID 5), it can provide redundancy and fault tolerance, ensuring data is not lost in case of drive failures. RAID is a commonly used technique for both data redundancy and performance improvement.
The other options mentioned are not related to drive redundancy:
- Buying an ASA (Adaptive Security Appliance) refers to acquiring a network security appliance used for firewall and VPN (Virtual Private Network) functions, not drive redundancy.
- Buying an IPS (Intrusion Prevention System) is a security device that monitors network traffic for suspicious activity and attempts to block or mitigate potential threats, but it does not address drive redundancy.
- Implementing dual authentication is a security measure for user authentication, which enhances access security but does not provide drive redundancy.
-
A PC technician has been asked by a supervisor to recommend a security solution for phishing. Which security technique should the technician recommend?
- Provide security awareness training.
- Buy an ASA.
- Buy an IPS.
- Employ ping sweeps.
-
Explanation & Hint: The security technique that the PC technician should recommend for phishing protection is to provide security awareness training.
- Security awareness training is a proactive approach to educate employees and users about the risks of phishing attacks. It helps individuals recognize phishing attempts, understand how to respond to suspicious emails, and avoid falling victim to phishing scams. It is an essential component of cybersecurity to reduce the risk of successful phishing attacks.
The other options mentioned are not directly related to phishing protection:
- Buying an ASA (Adaptive Security Appliance) refers to acquiring a network security appliance used for firewall and VPN (Virtual Private Network) functions, but it doesn’t specifically address phishing.
- Buying an IPS (Intrusion Prevention System) is a security device that monitors network traffic for suspicious activity and attempts to block or mitigate potential threats, but it is not focused solely on phishing protection.
- Employing ping sweeps is a network scanning technique used to discover active hosts on a network and is not a security solution for phishing.
-
A PC technician has been asked by a supervisor to recommend a security solution for protecting a computer used to log in at a dental clinic from someone using a bootable disk containing hacking tools. Which security technique should the technician recommend?
- Disable ports.
- Buy an ASA.
- Buy an IPS.
- Employ ping sweeps.
-
Explanation & Hint: To protect a computer used to log in at a dental clinic from someone using a bootable disk containing hacking tools, the PC technician should recommend disabling ports.
- Disabling ports involves physically or logically blocking the computer’s access to certain ports, such as USB ports or optical drives, where bootable disks can be inserted. This prevents unauthorized users from booting the computer from external devices, including bootable disks containing hacking tools. It is an effective security measure to prevent unauthorized access.
The other options mentioned are not directly related to this specific security concern:
- Buying an ASA (Adaptive Security Appliance) refers to acquiring a network security appliance used for firewall and VPN functions but does not address the issue of unauthorized booting from external devices.
- Buying an IPS (Intrusion Prevention System) is a security device that monitors network traffic for suspicious activity but is not focused on preventing bootable disk usage.
- Employing ping sweeps is a network scanning technique used to discover active hosts on a network and is not a direct solution for preventing unauthorized booting from external disks.
-
A PC technician has been asked by a supervisor to recommend a security solution for protecting a computer used to log in at a dental clinic from someone using a bootable disk containing hacking tools. Which security technique should the technician recommend?
- Disable ports.
- Buy an ASA.
- Buy an IPS.
- Run vulnerability scanners.
-
Explanation & Hint: To protect a computer used to log in at a dental clinic from someone using a bootable disk containing hacking tools, the PC technician should recommend disabling ports.
- Disabling ports involves physically or logically blocking the computer’s access to certain ports, such as USB ports or optical drives, where bootable disks can be inserted. This prevents unauthorized users from booting the computer from external devices, including bootable disks containing hacking tools. It is an effective security measure to prevent unauthorized access.
The other options mentioned are not directly related to this specific security concern:
- Buying an ASA (Adaptive Security Appliance) refers to acquiring a network security appliance used for firewall and VPN functions but does not address the issue of unauthorized booting from external devices.
- Buying an IPS (Intrusion Prevention System) is a security device that monitors network traffic for suspicious activity but is not focused on preventing bootable disk usage.
- Running vulnerability scanners is a process for identifying and assessing vulnerabilities in a computer system but does not specifically address the issue of booting from unauthorized disks.
-
A PC technician has been asked by a supervisor to recommend a security solution for protecting a computer used to log in at a dental clinic from someone using a bootable disk containing hacking tools. Which security technique should the technician recommend?
- Disable ports.
- Use a VPN.
- Buy an ASA.
- Run vulnerability scanners.
-
Explanation & Hint: To protect a computer used to log in at a dental clinic from someone using a bootable disk containing hacking tools, the PC technician should recommend disabling ports.
- Disabling ports involves physically or logically blocking the computer’s access to certain ports, such as USB ports or optical drives, where bootable disks can be inserted. This prevents unauthorized users from booting the computer from external devices, including bootable disks containing hacking tools. It is an effective security measure to prevent unauthorized access.
The other options mentioned are not directly related to this specific security concern:
- Using a VPN (Virtual Private Network) is a network technology that provides secure communication over the internet but does not address the issue of booting from unauthorized disks.
- Buying an ASA (Adaptive Security Appliance) refers to acquiring a network security appliance used for firewall and VPN functions but does not specifically address the issue of bootable disks.
- Running vulnerability scanners is a process for identifying and assessing vulnerabilities in a computer system but does not directly prevent unauthorized booting from external disks.
-
A PC technician has been asked by a supervisor to recommend a security solution for a manager traveling who needs access to internal corporate resources. Which security technique should the technician recommend?
- Use a VPN.
- Disable ports.
- Buy an ASA.
- Run vulnerability scanners.
-
Explanation & Hint: To provide secure access to internal corporate resources for a manager traveling, the PC technician should recommend using a VPN (Virtual Private Network).
- A VPN allows remote users, in this case, the traveling manager, to securely connect to the corporate network over the internet. It encrypts the communication between the manager’s device and the corporate network, ensuring that sensitive data remains confidential and secure during transmission. This is a common and effective security solution for remote access to internal corporate resources.
The other options mentioned are not directly related to providing secure remote access:
- Disabling ports is a security measure to prevent unauthorized access via physical or logical ports but does not provide secure remote access for traveling managers.
- Buying an ASA (Adaptive Security Appliance) refers to acquiring a network security appliance used for firewall and VPN functions but is not a solution for secure remote access on its own.
- Running vulnerability scanners is a process for identifying and assessing vulnerabilities in a computer system but does not provide secure remote access for traveling managers.
-
A PC technician has been asked by a supervisor to recommend a security solution for a small company that wants stateful firewall services. Which security technique should the technician recommend?
- Buy an ASA.
- Disable ports.
- Use a VPN.
- Setup footprinting.
-
Explanation & Hint: To provide stateful firewall services for a small company, the PC technician should recommend buying an ASA (Adaptive Security Appliance).
- An ASA is a hardware or software firewall device that provides stateful firewall services. It can inspect and track the state of network connections, making decisions based on the context of the traffic, and provide advanced security features. ASA devices are commonly used for firewall protection in various network environments, including small businesses.
The other options mentioned are not directly related to providing stateful firewall services:
- Disabling ports is a security measure to prevent unauthorized access via physical or logical ports but does not provide the comprehensive firewall services of an ASA.
- Using a VPN (Virtual Private Network) is a technology for secure remote access and communication but is not the same as a stateful firewall.
- Setting up footprinting is not a security solution; it refers to the process of gathering information about a target system or network, often for malicious purposes, and is not relevant to providing stateful firewall services.
-
A PC technician has been asked by a supervisor to recommend a security solution for a company that wants a device to monitor incoming and outgoing traffic and stop any malicious activity. Which security technique should the technician recommend?
- Buy an IPS.
- Disable ports.
- Use a VPN.
- Setup footprinting.
-
Explanation & Hint: To monitor incoming and outgoing traffic and stop malicious activity, the PC technician should recommend buying an IPS (Intrusion Prevention System).
- An IPS is a security device or software that monitors network traffic for suspicious or malicious activity and takes actions to prevent or block such activity. It can analyze traffic patterns, detect known attack signatures, and block malicious traffic in real-time. IPS is a crucial component of network security for identifying and mitigating threats.
The other options mentioned are not directly related to the specific task of monitoring and preventing malicious activity in network traffic:
- Disabling ports is a security measure to prevent unauthorized access via physical or logical ports but does not provide the monitoring and prevention capabilities of an IPS.
- Using a VPN (Virtual Private Network) is a technology for secure communication but does not serve as a primary tool for monitoring and stopping malicious network activity.
- Setting up footprinting is not a security solution; it refers to the process of gathering information about a target system or network, often for malicious purposes, and is not relevant to monitoring and preventing malicious network traffic.
-
A PC technician has been asked by a supervisor to recommend a security solution for a company that wants a device to monitor incoming and outgoing traffic and stop any malicious activity. Which security technique should the technician recommend?
- Buy an IPS.
- Disable ports.
- Use a VPN.
- Use SSL.
-
Explanation & Hint: To monitor incoming and outgoing traffic and stop malicious activity, the PC technician should recommend buying an IPS (Intrusion Prevention System).
- An IPS is a security device or software that monitors network traffic for suspicious or malicious activity and takes actions to prevent or block such activity. It can analyze traffic patterns, detect known attack signatures, and block malicious traffic in real-time. IPS is a crucial component of network security for identifying and mitigating threats.
The other options mentioned are not directly related to the specific task of monitoring and preventing malicious activity in network traffic:
- Disabling ports is a security measure to prevent unauthorized access via physical or logical ports but does not provide the monitoring and prevention capabilities of an IPS.
- Using a VPN (Virtual Private Network) is a technology for secure communication but does not serve as a primary tool for monitoring and stopping malicious network activity.
- Using SSL (Secure Sockets Layer) is a protocol for encrypting data in transit and securing communications but is not a standalone solution for monitoring and preventing malicious network activity.
-
A PC technician has been asked by a supervisor to recommend a security solution for a machine where the antimalware software cannot remove all of the malware. Which security technique should the technician recommend?
- Use Windows Safe Mode.
- Disable ports.
- Use a VPN.
- Use SSL.
-
Explanation & Hint: In the scenario where a PC technician is dealing with a machine where the antimalware software cannot remove all of the malware, the most appropriate security technique to recommend would be:
- Use Windows Safe Mode: Booting the computer in Windows Safe Mode is a recommended approach for dealing with stubborn malware. Safe Mode starts the computer with a minimal set of drivers and services. Without all the usual software and malware running in the background, it may be easier for antimalware tools to detect and remove malicious software. This environment often prevents malware from loading automatically, which can give the antimalware software a better chance at successfully removing the infection.
The other options are less directly relevant to the task of malware removal:
- Disable Ports: While disabling unused ports can enhance overall security, it doesn’t directly assist in the removal of malware that is already present on the system.
- Use a VPN (Virtual Private Network): A VPN is useful for securing a network connection and ensuring privacy, but it does not directly help in removing malware from a system.
- Use SSL (Secure Sockets Layer): SSL is used to secure communications over a network (especially the internet) and is important for data protection during transmission. However, it does not contribute to the removal of existing malware on a system.
Given the situation, booting in Windows Safe Mode and then running the antimalware software would be the most effective recommendation.
-
Which term describes a file system that supports a partition size up to 16 exabytes?
- formatting
- NTFS
- dynamic disk
- basic disk
-
Explanation & Hint: The term that describes a file system supporting a partition size up to 16 exabytes is NTFS (New Technology File System).
Here’s a brief overview of each term:
- NTFS (New Technology File System): This is a file system developed by Microsoft. It is known for its high capacity for partition size, supporting partitions up to 16 exabytes in theory. NTFS is used in Windows operating systems and is recognized for its robustness, security features, and large volume support.
- Formatting: This is the process of preparing a storage device for data storage, which involves setting up a file system (such as NTFS, FAT32, or exFAT) on the device. The term “formatting” itself does not refer to a specific file system or its capabilities.
- Dynamic Disk: This refers to a disk type in Windows that supports features like volume spanning, RAID configurations, and disk mirroring. It’s a method for managing the storage space on a hard drive and is not itself a file system.
- Basic Disk: This is a disk type that uses primary partitions, extended partitions, and logical drives for data storage. The term “basic disk” relates to how a disk is partitioned and managed but is not a file system.
In the context of a file system that can support a partition size up to 16 exabytes, NTFS is the correct term.
-
Which term describes a partition that is used to store and boot an operating system by default?
- FAT32
- active partition
- formatting
- dynamic disk
-
Explanation & Hint: The term that describes a partition used to store and boot an operating system by default is active partition.
Here’s a brief explanation of each term:
- Active Partition: In the context of disk partitioning, an active partition is the one that a computer’s BIOS identifies as the partition to boot from. It contains the boot loader, which is necessary to start the operating system. On an MBR (Master Boot Record) disk, the active partition is used to boot the system.
- FAT32: This is a file system type (File Allocation Table 32). While it can be used on a partition that contains an operating system, FAT32 itself does not describe the bootability or functionality of a partition.
- Formatting: This refers to the process of preparing a storage device for data storage by setting up a file system (like NTFS, FAT32, or exFAT). Formatting is a general process and doesn’t specify a partition’s role in storing or booting an operating system.
- Dynamic Disk: This is a disk type in Windows that supports volumes spanning multiple disks and other advanced features. It is not specifically related to the bootability of a partition.
In the context of storing and booting an operating system by default, the “active partition” is the correct term.
-
Which term describes a file system for USB flash drives that supports files larger than 4 GB?
- formatting
- exFAT
- dynamic disk
- basic disk
-
Explanation & Hint: The term that describes a file system for USB flash drives that supports files larger than 4 GB is exFAT (Extended File Allocation Table).
Here’s an overview of each term for clarity:
- exFAT (Extended File Allocation Table): This is a file system introduced by Microsoft, optimized for flash memory devices like USB flash drives and SD cards. exFAT is designed to handle large files and is known for supporting files larger than 4 GB, which is a limitation in older file systems like FAT32.
- Formatting: This is the process of preparing a storage device (like a hard drive, SSD, or USB flash drive) for data storage. Formatting involves setting up a file system (such as NTFS, FAT32, or exFAT) on the device, but the term “formatting” itself does not refer to a specific file system.
- Dynamic Disk: This refers to a disk type in Windows that supports features like volume spanning, RAID, and disk mirroring. It is a method of managing the storage space on a hard drive, rather than a file system.
- Basic Disk: A basic disk is a disk type that uses primary partitions, extended partitions, and logical drives for data storage. This term is related to the way a disk is partitioned and managed and is not a file system.
In the context of a file system for USB flash drives that can handle large files (over 4 GB), exFAT is the correct term.
-
Which term describes a partition that supports up to 23 logical drives?
- FAT32
- extended partition
- formatting
- dynamic disk
-
Explanation & Hint: The term that describes a partition that supports up to 23 logical drives is extended partition.
Here’s a brief overview of each term:
- Extended Partition: On a hard disk using the MBR (Master Boot Record) partitioning scheme, you can have up to four primary partitions, or three primary partitions and one extended partition. The extended partition is unique in that it can be subdivided into multiple logical drives. While traditionally limited to 23 due to operating system constraints, the actual limit can vary depending on the operating system and the disk management tools used.
- FAT32: This is a file system format (File Allocation Table 32) and does not describe a partition type. It can be used on both primary and logical partitions but doesn’t define the number of partitions or logical drives a disk can have.
- Formatting: Formatting refers to the process of preparing a storage device for use by an operating system, which includes setting up a file system. This term does not pertain to the number of partitions or logical drives.
- Dynamic Disk: This refers to a storage disk type in Windows that offers features like spanning volumes across multiple disks and RAID configurations. It’s a disk management scheme and not a type of partition.
In the context of supporting up to 23 logical drives, the term “extended partition” is the most relevant.
-
Which term describes a type of partition that would only exist on a hard disk that has an MBR?
- FAT32
- logical drive
- formatting
- dynamic disk
-
Explanation & Hint: The term that describes a type of partition that would only exist on a hard disk that has an MBR (Master Boot Record) is logical drive.
Here’s a brief explanation of each term:
- Logical Drive: In the context of MBR-partitioned disks, a logical drive is a partition within an extended partition. MBR allows for up to four primary partitions, or three primary partitions and one extended partition. Within this extended partition, you can create multiple logical drives. This concept is specific to MBR-partitioned disks.
- FAT32: This is a file system format and not specific to MBR. FAT32 (File Allocation Table 32) can be used on various storage devices, including those with MBR or GPT (GUID Partition Table) partitioning schemes.
- Formatting: Formatting is a process of preparing a storage device for use by an operating system, which includes setting up a file system. It is not specific to MBR and is a general process applicable to all storage devices regardless of their partitioning scheme.
- Dynamic Disk: This is a disk type in Windows that allows for more advanced features than basic disks, like spanning volumes across multiple disks. It is not exclusive to MBR or GPT and refers to how the disk is managed in Windows rather than its partition structure.
In the context of MBR-partitioned disks, logical drives within an extended partition are the specific term related to the type of partition.
-
Which term describes a file system for optical disk media?
- formatting
- CDFS
- dynamic disk
- basic disk
-
Explanation & Hint: The term that describes a file system specifically used for optical disk media (such as CDs and DVDs) is CDFS (Compact Disc File System).
Here’s a brief overview of each term:
- CDFS (Compact Disc File System): This is a file system for optical disc media. CDFS is a standard file system format for CDs and is used by operating systems to read data from CDs and DVDs. It allows users to access and retrieve files and directories stored on optical discs.
- Formatting: This is the process of preparing a data storage device such as a hard disk drive, solid-state drive, or USB flash drive for initial use. In the context of file systems, formatting is the process of setting up a file system on a partition or disk. It doesn’t refer to a specific file system type but to the process of applying one.
- Dynamic Disk: This refers to a disk type in Windows that supports volumes that span multiple disks (spanned and striped volumes) and fault tolerance (mirrored and RAID-5 volumes). Dynamic disks are not a file system but a method for managing the storage space on hard drives.
- Basic Disk: A basic disk is a disk type that uses primary partitions, extended partitions, and logical drives for data storage. It is the opposite of a dynamic disk and is not a file system itself.
In the context of optical disc media, CDFS is the correct term related to file systems.
-
Which term describes a file system for optical disk media?
- partition
- CDFS
- MBR
- GPT
-
Explanation & Hint: The term that describes a file system specifically used for optical disk media (such as CDs and DVDs) is CDFS (Compact Disc File System).
Here’s a brief explanation of the mentioned terms for context:
- CDFS (Compact Disc File System): This is the file system for optical disc media. CDFS is a standard file system for CDs and is used by operating systems to read data from CDs and DVDs. It allows users to view and retrieve files and directories stored on optical discs.
- Partition: A partition is a segment of a hard disk drive. It is a division of the storage space where a particular file system can be installed, but it does not refer to a specific file system itself.
- MBR (Master Boot Record): MBR is a type of boot sector used at the beginning of partitioned computer storage devices like hard drives. It contains information about how the logical partitions are organized on that storage device and includes a bootloader for the installed operating system. MBR is not a file system, but rather a partitioning scheme.
- GPT (GUID Partition Table): GPT is another partitioning scheme used on hard drives, particularly as part of the UEFI standard. It allows for a larger number of partitions and larger disk sizes than MBR, but like MBR, it is not a file system.
In the context of optical disc media, CDFS is the correct term related to file systems.
-
Which term describes a type of storage device that supports a partition to be extended into adjacent unallocated space as long as it is contiguous?
- partition
- basic disk
- MBR
- GPT
-
Explanation & Hint: The term that describes a type of storage device that supports a partition to be extended into adjacent, contiguous unallocated space is basic disk.
Here’s a brief explanation of each term:
- Basic Disk: This is a disk type in Windows that can be partitioned with a simple layout. Partitions on a basic disk are referred to as basic volumes, which include primary partitions and extended partitions. A basic disk allows for extending a partition into contiguous unallocated space on the same drive.
- Partition: A partition is a specific, logical division of a hard drive. It doesn’t inherently describe the ability to extend into unallocated space but is more about the division itself.
- MBR (Master Boot Record): MBR is a boot sector at the beginning of partitioned storage devices, like hard drives. It contains a bootloader for the installed operating system and information about the disk’s partitions. The MBR partitioning scheme itself doesn’t directly relate to the ability to extend partitions.
- GPT (GUID Partition Table): GPT is a standard for the layout of the partition table on a physical hard disk. Like MBR, it’s more about the structure and organization of the disk’s partitions and doesn’t inherently describe the feature of extending partitions.
In the context of extending a partition into adjacent, contiguous unallocated space, a basic disk is the correct term.
-
Which term describes a general name for physical areas on a hard drive?
- MBR
- partition
- GPT
- primary partition
-
Explanation & Hint: The term that describes a general name for physical areas on a hard drive is partition.
Here’s a brief overview of each term for clarity:
- Partition: This is the term used to describe a specific, logical division of a hard drive. A partition is essentially a way to segment a hard drive into separate, distinct sections, each of which can be managed independently and can have different file systems.
- MBR (Master Boot Record): This refers to a special type of boot sector at the beginning of partitioned computer mass storage devices like hard drives. It contains the information on how the logical partitions, containing file systems, are organized on that medium.
- GPT (GUID Partition Table): GPT is a standard for the layout of the partition table on a physical storage device like a hard disk, used in newer systems as an alternative to MBR. It is part of the UEFI standard and allows for a larger number of partitions and larger disk sizes.
- Primary Partition: This is a specific type of partition on a hard disk. A hard drive can have a limited number of primary partitions (up to four with MBR), and these partitions can contain an operating system.
In the context of describing physical areas on a hard drive, “partition” is the most suitable term.
-
Which term describes a partition scheme that takes a portion of disk space of 512 bytes long and that contains the boot loader?
- partition
- MBR
- GPT
- primary partition
-
Explanation & Hint: The term that describes a partition scheme involving a portion of disk space that is 512 bytes long and contains the boot loader is MBR (Master Boot Record).
Here’s a brief explanation of each term for clarity:
- MBR (Master Boot Record): This is a type of boot sector at the beginning of mass storage devices like hard drives. The MBR is 512 bytes long and contains the boot loader, which is a small program that starts the computer’s operating system when the computer is turned on. It also contains information about the partitions on the disk.
- Partition: A partition is a distinct region of a hard disk, which can be used to separate different kinds of data and can be formatted with different file systems.
- GPT (GUID Partition Table): This is a standard for the layout of the partition table on a physical hard disk. It is part of the UEFI standard and is used as a more modern and robust alternative to the older MBR partitioning scheme.
- Primary Partition: This is one of the partitions on a hard drive. A primary partition can contain one operating system and is one of the partitions that can be made bootable. A hard disk can have a maximum of four primary partitions.
In your scenario, where the focus is on a 512-byte section that includes a boot loader, MBR is the correct term.
-
Users in a company have complained about network performance. After investigation, the IT staff has determined that the attacker is using a vulnerability that is known to the software vendor, but not patched yet. What is the type of network attack?
- zero-day
- DDoS
- DNS poisoning
- DoS
-
Explanation & Hint: The type of network attack described, where the attacker is exploiting a vulnerability that is known to the software vendor but has not yet been patched, is known as a Zero-Day Attack.
Here’s an explanation of each of the mentioned attack types:
- Zero-Day Attack: This type of attack exploits a vulnerability that is not yet known to the public or the software vendor has not yet released a patch for it. The term “zero-day” refers to the fact that the developers have had zero days to fix the vulnerability since it became known or was exploited.
- DDoS (Distributed Denial of Service): In a DDoS attack, multiple compromised systems are used to flood a target (like a server or network) with traffic, overwhelming it and causing performance issues or downtime.
- DNS Poisoning: This involves manipulating the DNS (Domain Name System) records to redirect traffic to malicious sites or servers.
- DoS (Denial of Service): Similar to a DDoS, but typically involves a single attacker or source. It aims to make a network resource unavailable by overwhelming it with traffic or triggering a crash.
In the situation you described, where the attack is based on an unpatched vulnerability known to the software vendor, it is correctly categorized as a Zero-Day Attack.
-
Users in a company have complained about network performance. After investigation, the IT staff has determined that zombies were used to attack the firewall. What is the type of network attack?
- DDoS
- DNS poisoning
- SYN flood
- DoS
-
Explanation & Hint: The type of network attack described, where zombies (compromised computers) were used to attack the firewall, is known as a DDoS (Distributed Denial of Service) attack.
In a DDoS attack, multiple compromised systems, often referred to as “zombies” or “bots,” are used to target a single system such as a server, website, or firewall. The aim is to overwhelm the target with a flood of internet traffic, which can come from many different sources, making it difficult to stop the attack by blocking a single source.
Here’s a brief overview of the other mentioned attack types for comparison:
- DNS Poisoning: This involves corrupting the DNS (Domain Name System) records to redirect users to malicious sites or servers.
- SYN Flood: A type of Denial of Service attack that specifically targets the TCP three-way handshake mechanism, overwhelming a target with a flood of SYN requests.
- DoS (Denial of Service): Similar in intent to DDoS, but typically involves a single attacker/source. It aims to make a machine or network resource unavailable to its intended users by overwhelming it with traffic or sending information that triggers a crash.
In your scenario, where multiple compromised systems are used to attack the firewall, it is classified as a DDoS attack.
-
Users in a company have complained about network performance. After investigation, the IT staff has determined that the attacker is using a table of words that potentially could be used as passwords. What is the type of network attack?
- dictionary
- SYN flood
- DNS poisoning
- zero-day
-
Explanation & Hint: The type of network attack described, where the attacker uses a table of words that potentially could be used as passwords, is known as a Dictionary Attack.
In a Dictionary Attack, the attacker attempts to gain unauthorized access to a user’s account by systematically entering every word from a list (the ‘dictionary’) into a password field. This list typically contains common passwords and phrases that people often use. The attacker’s goal is to guess the correct password from this predefined list of potential passwords.
The other types of attacks mentioned are different:
- SYN Flood: This is a type of Denial-of-Service attack where the attacker floods a server with TCP/SYN packets, typically aiming to consume server resources by creating many half-open connections.
- DNS Poisoning: In this attack, the attacker corrupts the DNS (Domain Name System) records to redirect users to malicious sites instead of the intended destinations.
- Zero-Day: This refers to an attack that exploits a previously unknown vulnerability in software or hardware, meaning the vendor has had zero days to create a patch for the vulnerability.
In your scenario, where the focus is on using a list of potential passwords to gain unauthorized access, a Dictionary Attack is the correct term.
-
Users in a company have complained about network performance. After investigation, the IT staff has determined that the attacker injected false records on the server that translates IP addresses to domain names. What is the type of network attack?
- DNS poisoning
- zero-day
- SYN flood
- dictionary
-
Explanation & Hint: The type of network attack described, where the attacker injects false records into the server that translates IP addresses to domain names, is known as DNS Poisoning (also referred to as DNS spoofing).
Here’s a brief overview of each of the mentioned attack types for clarity:
- DNS Poisoning: This type of attack involves corrupting the DNS (Domain Name System) records in a DNS server. By doing so, the attacker can redirect traffic to fraudulent websites or servers. This is typically achieved by introducing false information into the DNS cache of a server, causing the server to return incorrect IP addresses for specific domain names.
- Zero-Day: This term refers to a security vulnerability that is exploited by attackers before the vendor has released a patch or even become aware of it. “Zero-Day” indicates that developers have had zero days to address and patch the vulnerability before it was exploited.
- SYN Flood: A SYN flood is a form of Denial-of-Service attack that targets the TCP three-way handshake process. The attacker sends a high volume of SYN requests to a target server but does not complete the handshake, leaving connections half-open and potentially overwhelming the server.
- Dictionary Attack: This is a technique used to break passwords or encryption keys by systematically entering every word in a predefined list (like a dictionary) into a login field or decryption algorithm.
In the scenario you described, where false records are introduced into the DNS resolution process, DNS Poisoning is the correct identification of the attack type.
-
Users in a company have complained about network performance. After investigation, the IT staff has determined that the attacker is using a technique that compares hashed passwords to potential hashes the hacker has. What is the type of network attack?
- rainbow table
- SYN flood
- DNS poisoning
- zero-day
-
Explanation & Hint: The type of network attack described, where the attacker is comparing hashed passwords to a precomputed list of potential hashes, is known as a Rainbow Table attack.
Here’s a brief description of each of the mentioned attack types:
- Rainbow Table: This is a technique used to crack encrypted passwords. Instead of brute-forcing the encryption, attackers use a rainbow table, which is a precomputed table for reversing cryptographic hash functions, mainly for cracking password hashes. By comparing the hashed passwords (usually stored in the company’s databases) to the hashes in the rainbow table, attackers can find matches and thereby discover the original password.
- SYN Flood: This is a type of Denial-of-Service attack that targets the TCP three-way handshake mechanism by flooding the target with SYN requests and not completing the handshake.
- DNS Poisoning: This attack involves corrupting the DNS resolution process to redirect users to malicious websites instead of the intended destinations.
- Zero-Day: This refers to an attack that takes advantage of a security vulnerability on the same day that the vulnerability becomes generally known. There is no prior knowledge or defense against the vulnerability until it’s exploited.
In the context of your scenario where hashed passwords are being compared to potential hashes, a Rainbow Table attack is the appropriate term for the technique being used by the attacker.
-
Users in a company have complained about network performance. After investigation, the IT staff has determined that the attacker was using a specific technique that affected the TCP three-way handshake. What is the type of network attack?
- SYN flood
- zero-day
- DNS poisoning
- dictionary
-
Explanation & Hint: The type of network attack described, where the attacker is affecting the TCP three-way handshake, is known as a SYN flood attack.
In a SYN flood attack, the attacker sends a large number of SYN (synchronize) requests to a target’s server in an attempt to overwhelm it. This is done as part of the TCP/IP three-way handshake process, which is used to establish a connection between a client and a server over a network. The attacker sends SYN requests but does not complete the handshake by sending the final acknowledgment (ACK). This leaves the connections half-open, consuming server resources and potentially leading to denial of service as the server becomes unable to handle legitimate requests.
The other options mentioned refer to different types of attacks:
- Zero-day: This refers to a vulnerability that is exploited by attackers before the vendor has released a fix or even become aware of it.
- DNS Poisoning: This involves corrupting the DNS (Domain Name System) records to redirect traffic to malicious sites.
- Dictionary Attack: This is a method used to break passwords or encryption keys by systematically entering every word in a predefined list (like a dictionary).
In your scenario, SYN flood is the correct identification of the attack type.
-
A technician is working on a laptop and an error message about decryption appears when opening an email. What is a possible solution for this situation?
- Install an appropriate certificate.
- Check the screen refresh rate.
- Ensure that only one app is open at a time.
- Ensure that Wi-Fi is turned off.
-
Explanation & Hint: In the situation where a technician is faced with an error message about decryption when opening an email on a laptop, the most appropriate solution would be:
- Install an Appropriate Certificate: This error typically indicates a problem with digital certificates used for encrypting or decrypting emails. If the necessary certificate is not installed, is expired, or is corrupted, it can lead to issues with decryption. The technician should verify and ensure that the correct digital certificate is installed and properly configured on the laptop. This may involve obtaining a new certificate from a trusted certificate authority, or checking the validity and configuration of an existing certificate.
The other options are unlikely to resolve a decryption issue:
- Check the Screen Refresh Rate: The refresh rate of the screen is related to the visual display of the laptop and has no connection to the decryption process of emails.
- Ensure that Only One App is Open at a Time: While running fewer applications can help with overall system performance, it is unlikely to have any impact on issues related to email decryption.
- Ensure that Wi-Fi is Turned Off: Wi-Fi connectivity is generally not related to decryption problems. Decryption issues are typically due to certificate-related problems and not network connectivity.
Installing or ensuring proper configuration of the appropriate digital certificate is the most relevant and effective approach to addressing the issue with the decryption error in email.
-
A technician is working on a laptop and an error message about decryption appears when opening an email. What is a possible solution for this situation?
- Install an appropriate certificate.
- Replace the digitizer.
- Ensure that only one app is open at a time.
- Ensure that Wi-Fi is turned off.
-
Explanation & Hint: When addressing an issue with an error message about decryption appearing when opening an email on a laptop, the most appropriate solution would be:
- Install an Appropriate Certificate: This error is likely related to the digital certificates used for encrypting or decrypting emails. If the necessary certificate is not installed, is expired, or is corrupted, it can lead to decryption errors. The technician should ensure that the correct digital certificate is installed and properly configured on the laptop. This might involve obtaining and installing a new certificate from a trusted certificate authority, or ensuring that the existing certificate is valid and correctly implemented.
The other suggestions are less likely to be effective for a decryption issue:
- Replace the Digitizer: The digitizer, part of the screen hardware for touch input, is unrelated to decryption or the processing of emails.
- Ensure that Only One App is Open at a Time: While limiting the number of open applications can help with general performance issues, it’s unlikely to specifically address a problem with email decryption.
- Ensure that Wi-Fi is Turned Off: Turning off Wi-Fi does not typically affect the ability to decrypt emails. Decryption issues are usually related to certificate problems, not connectivity issues.
Therefore, installing or ensuring the correct configuration of the appropriate digital certificate is the most directly relevant solution for resolving the decryption error message when opening an email.
-
A technician is working on a laptop and an error message about decryption appears when opening an email. What is a possible solution for this situation?
- Install an appropriate certificate.
- Replace the digitizer.
- Check the screen refresh rate.
- Check the display settings.
-
Explanation & Hint: For a technician addressing an issue where an error message about decryption appears when opening an email on a laptop, the most suitable solution would be:
- Install an Appropriate Certificate: This error message is likely related to digital certificates used for encrypting or decrypting emails. If the necessary certificate is not installed or if it’s expired or corrupted, decryption errors can occur. The technician should ensure that the correct digital certificate is installed and properly configured. This might involve obtaining a new certificate from a certificate authority or ensuring that the existing certificate is up to date and not corrupted.
The other options are unlikely to resolve a decryption issue:
- Replace the Digitizer: The digitizer, which is part of the screen’s hardware responsible for touch input, is unrelated to decryption or email functionality.
- Check the Screen Refresh Rate: The screen refresh rate pertains to how often the display updates with new images and has no connection to decryption processes or email functionality.
- Check the Display Settings: Display settings, which control aspects like resolution and color calibration, are also unrelated to issues with email decryption.
Installing or updating the appropriate digital certificate is the most relevant approach to resolving the issue with decryption errors when opening an email.
-
A technician is working on a laptop and a key on the keyboard is not responding as it should. What is a possible solution for this situation?
- Clean with compressed air.
- Update all security apps.
- Check the screen refresh rate.
- Check the display settings.
-
Explanation & Hint: For a technician addressing a situation where a key on a laptop keyboard is not responding properly, the most suitable solution would be:
- Clean with Compressed Air: This is a common and effective method for resolving issues with keyboard keys. Dust, dirt, or other debris can get lodged under the keys, causing them to stick or not respond correctly. Using compressed air can help dislodge and remove this debris, potentially restoring the key’s functionality.
The other options are unlikely to resolve a keyboard key issue:
- Update All Security Apps: While keeping security applications updated is important for overall system security, it’s unlikely to have any impact on the functionality of a keyboard key.
- Check the Screen Refresh Rate: The screen refresh rate is related to the display’s performance and has no connection to the functioning of the keyboard.
- Check the Display Settings: Similarly, the display settings, which involve aspects like resolution, brightness, and color calibration, do not affect the physical operation of the keyboard.
Therefore, cleaning the affected key with compressed air is the most relevant and direct approach to address the issue with the non-responsive key on the laptop keyboard.
-
A technician is working on a laptop and a key on the keyboard is not responding as it should. What is a possible solution for this situation?
- Clean with compressed air.
- Ensure that Bluetooth is not activated.
- Check the screen refresh rate.
- Check the display settings.
-
Explanation & Hint: For a technician addressing an issue with a key on a laptop keyboard not responding as it should, the most appropriate solution would be:
- Clean with Compressed Air: If a key on a laptop keyboard is not functioning properly, it could be due to dust, debris, or other particles trapped under the key. Using compressed air to clean around and under the key can often dislodge and remove this debris, potentially restoring the key’s functionality.
The other options are less likely to be relevant for a keyboard issue:
- Ensure that Bluetooth is Not Activated: Bluetooth settings typically do not affect the functioning of a laptop’s keyboard, as the keyboard is usually connected directly to the motherboard (unless it’s an external Bluetooth keyboard, which is not indicated in this scenario).
- Check the Screen Refresh Rate: The screen refresh rate pertains to how often the display updates with new image data and is unrelated to issues with keyboard functionality.
- Check the Display Settings: The display settings, which involve aspects such as resolution, brightness, and color, are also unrelated to the functioning of the keyboard.
Cleaning with compressed air is a practical and common first step in resolving physical issues with keyboard keys.
-
A technician is working on a laptop and GPS is not functioning. What is a possible solution for this situation?
- Verify that airplane mode is not activated.
- Ensure that Bluetooth is not activated.
- Check the screen refresh rate.
- Check the display settings.
-
Explanation & Hint: For a technician working on a laptop where the GPS is not functioning, the following solutions could be considered:
- Verify that Airplane Mode is Not Activated: This is a crucial step. When airplane mode is activated on a laptop, it disables all wireless communications, which may include GPS functionality, along with Wi-Fi and Bluetooth. Ensuring that airplane mode is off is essential, as this could be the primary reason for the GPS not working.
- Ensure that Bluetooth is Not Activated: While it’s less common, in some instances, Bluetooth might interfere with other wireless services, including GPS. However, this is relatively rare, and GPS and Bluetooth typically do not interfere with each other. Still, it might be worth checking, especially if other troubleshooting steps don’t resolve the issue.
The other options are less likely to impact the functionality of GPS:
- Check the Screen Refresh Rate: The screen refresh rate, which deals with how often the display updates, is unrelated to GPS functionality. Adjusting the screen refresh rate is unlikely to have any effect on the operation of GPS.
- Check the Display Settings: Display settings control the visual output of the device (like resolution, brightness, and color settings) and do not generally affect the GPS’s ability to receive or process signals.
In summary, verifying that airplane mode is not activated and ensuring that Bluetooth is not causing interference are more relevant steps for troubleshooting a non-functioning GPS on a laptop.
-
A technician is working on a laptop and GPS is not functioning. What is a possible solution for this situation?
- Verify that airplane mode is not activated.
- Check the fan on the GPU.
- Check the screen refresh rate.
- Check the display settings.
-
Explanation & Hint: In the scenario where a laptop’s GPS is not functioning, the most suitable solution to try would be:
- Verify that Airplane Mode is Not Activated: This is a crucial step to take because activating airplane mode on a laptop typically disables all wireless communication functions, including Wi-Fi, Bluetooth, and potentially GPS (if the laptop is equipped with GPS capabilities). Ensuring that airplane mode is turned off is important, as this could be the primary reason for the GPS not functioning.
The other options provided are less likely to be relevant to resolving a GPS functionality issue:
- Check the Fan on the GPU: The functionality of the GPU (Graphics Processing Unit) and its cooling fan is generally unrelated to GPS operation. The GPU is responsible for rendering images, video, and animations on the laptop’s display, whereas GPS issues are typically related to wireless communication or software settings.
- Check the Screen Refresh Rate: The screen refresh rate, which refers to how often the display is updated with new images, is unrelated to GPS signal reception or processing. Adjusting the screen refresh rate is unlikely to have any effect on GPS functionality.
- Check the Display Settings: The display settings, which involve adjustments to the laptop’s visual output such as resolution, brightness, and color calibration, do not impact the laptop’s ability to receive or process GPS signals.
Therefore, verifying that airplane mode is not activated is the most appropriate and direct solution to address the GPS issue in this situation.
-
A technician is working on a laptop and GPS is not functioning. What is a possible solution for this situation?
- Verify that airplane mode is not activated.
- Ensure that Wi-Fi is turned off.
- Check the screen refresh rate.
- Check the display settings.
-
Explanation & Hint: In the scenario where a laptop’s GPS is not functioning, the most appropriate solution to consider would be:
- Verify that Airplane Mode is Not Activated: When airplane mode is activated on a laptop, it typically disables all wireless communications, including Wi-Fi, Bluetooth, and possibly GPS (if the laptop has integrated GPS capabilities). Ensuring that airplane mode is turned off is a crucial step, as this could be the reason why the GPS is not functioning.
The other provided options are less likely to directly impact GPS functionality:
- Ensure that Wi-Fi is Turned Off: Generally, Wi-Fi does not interfere with GPS functionality. Both systems can operate simultaneously without affecting each other. Turning off Wi-Fi is unlikely to have an impact on GPS performance.
- Check the Screen Refresh Rate: The screen refresh rate pertains to the display’s performance and is unrelated to GPS functionality. It refers to how many times per second the display updates the image it shows and does not affect GPS signal reception or processing.
- Check the Display Settings: Display settings, which deal with the visual output of the laptop, are also unlikely to affect the functionality of the GPS. These settings control aspects such as resolution, brightness, and color calibration, none of which are related to GPS operation.
Therefore, verifying that airplane mode is not activated is the most relevant and effective approach to addressing the GPS issue in this context.
-
A technician is working on a laptop and GPS is not functioning. What is a possible solution for this situation?
- Verify the status of service.
- Ensure that Wi-Fi is turned off.
- Check the screen refresh rate.
- Check the display settings.
-
Explanation & Hint: In the given scenario where a laptop’s GPS is not functioning, the most appropriate solution to consider would be:
- Verify the Status of the GPS Service: This is the most relevant step. The technician should check if the GPS service is enabled on the laptop and if it is functioning correctly. Sometimes, the GPS might be disabled, not properly configured, or experiencing service interruptions, which could lead to its malfunction. Ensuring that the GPS service is active and correctly set up in the system settings is a critical step in troubleshooting GPS-related issues on a laptop.
The other provided options are less likely to be effective in resolving GPS functionality issues:
- Ensure that Wi-Fi is Turned Off: While Wi-Fi and GPS are different systems, in some rare cases, Wi-Fi could potentially cause interference with other wireless services. However, it’s generally uncommon for Wi-Fi to disrupt GPS functionality, especially in a laptop.
- Check the Screen Refresh Rate: The screen refresh rate, which deals with how often the display updates, is unrelated to GPS signal reception or processing. It’s primarily a display parameter and does not impact the functionality of GPS.
- Check the Display Settings: Display settings, which concern the visual output of the device, also do not influence the laptop’s ability to receive or process GPS signals.
Considering these points, verifying the status of the GPS service is the most directly applicable solution to the problem at hand.
-
A technician is working on a laptop and GPS is not functioning. What is a possible solution for this situation?
- Verify the status of service.
- Ensure that only one app is open at a time.
- Recharge the battery.
- Check the display settings.
-
Explanation & Hint: When dealing with a GPS not functioning on a laptop, a technician might consider the following possible solutions:
- Verify the Status of the GPS Service: The first step should be to check if the GPS service is enabled and functioning properly. This includes checking the laptop’s settings to ensure that the GPS feature is turned on. In some cases, the GPS service may be disabled or not properly configured, leading to functionality issues.
- Update or Reinstall GPS Drivers: If the GPS service is on but not working correctly, the issue might be related to outdated or corrupted drivers. The technician should check for any available updates for the GPS drivers and install them. If the drivers are already up to date, reinstalling them might resolve any corruption issues.
- Check for Interfering Software: Sometimes, other software running on the laptop can interfere with GPS functionality. The technician should check for any recently installed applications or background processes that might be causing conflicts with the GPS system.
- Hardware Check: If the software checks do not resolve the issue, it’s possible that there might be a hardware problem with the GPS module. The technician should inspect the hardware or consider getting it checked by a professional if it’s beyond their expertise.
The other solutions you mentioned are less likely to be effective in this scenario:
- Ensure that only one app is open at a time: While reducing the number of running applications can help with general performance issues, it’s unlikely to specifically address a problem with GPS functionality.
- Recharge the Battery: Low battery can affect device performance, but it’s unlikely to be the sole cause of GPS malfunctions unless the device is shutting down or entering a low-power mode.
- Check the Display Settings: GPS issues are generally not related to display settings, as GPS functionality is more about connectivity and sensor operation rather than how things are displayed on screen.
-
Why would a manager need to use the tracert command?
- to display a list of the near-side router interfaces between the source device and the destination device
- to move that file to a different Windows directory while also leaving the file in the current location
- to copy a group of files from one Windows directory to another
- to relocate a file from one Windows directory to another one
-
Explanation & Hint: A manager might need to use the
tracert(Trace Route) command for the following reason:- To display a list of the near-side router interfaces between the source device and the destination device: The
tracertcommand is used in network diagnostics to determine the path taken by packets across an IP network from the source to the destination. It shows each hop sequentially and the time taken to reach each hop. This can be crucial for a manager in identifying network issues such as slow connections or to trace the path data takes to reach a specific server or system. Understanding the network route can help in diagnosing where delays or data losses are occurring in the network.
The other options you mentioned are related to different commands or actions:
- To move that file to a different Windows directory while also leaving the file in the current location: This describes copying a file, not moving it, and is typically done with the
copycommand. - To copy a group of files from one Windows directory to another: This action is performed using the
copycommand. - To relocate a file from one Windows directory to another one: Moving a file (which removes it from the original location) is done using the
movecommand.
Each of these commands serves a different purpose in managing files, directories, or diagnosing network paths within a computer’s operating system and network.
- To display a list of the near-side router interfaces between the source device and the destination device: The
-
Why would a manager need to use the sfc command?
- to scan and verify the integrity of all protected system files and replace incorrect versions with correct versions
- to move that file to a different Windows directory while also leaving the file in the current location
- to copy a group of files from one Windows directory to another
- to relocate a file from one Windows directory to another one
-
Explanation & Hint: A manager might need to use the
sfc(System File Checker) command for the following reason:- To scan and verify the integrity of all protected system files and replace incorrect versions with correct versions: The
sfccommand is a Windows utility that allows users to scan for and restore corruptions in Windows system files. If a manager suspects that there are issues with the system files on their computer, perhaps causing operational problems or security vulnerabilities, they could use thesfc /scannowcommand. This tool is critical for maintaining the integrity and smooth operation of the Windows operating system by ensuring that all system files are correct and intact.
The other options you mentioned are related to different commands or actions:
- To move that file to a different Windows directory while also leaving the file in the current location: This describes copying a file, not moving it, and is typically done with the
copycommand. - To copy a group of files from one Windows directory to another: This action is performed using the
copycommand. - To relocate a file from one Windows directory to another one: Moving a file (which removes it from the original location) is done using the
movecommand.
Each of these commands serves a different purpose in managing files, directories, or system integrity within a computer’s operating system.
- To scan and verify the integrity of all protected system files and replace incorrect versions with correct versions: The
-
Why would a technician need to use the DISM command?
- to repair, prepare, and fix Windows images and the recovery image within an installation of the operating system
- to move that file to a different Windows directory while also leaving the file in the current location
- to copy a group of files from one Windows directory to another
- to relocate a file from one Windows directory to another one
-
Explanation & Hint: A technician would need to use the
DISM(Deployment Image Servicing and Management) command for the following reason:- To repair, prepare, and fix Windows images and the recovery image within an installation of the operating system: The DISM tool in Windows is a versatile command-line tool that is used for servicing and preparing Windows images, including those used for Windows PE, Windows Recovery Environment, and Windows Setup. Technicians commonly use DISM for repairing system images, managing features and packages, and fixing issues with the Windows installation itself or its recovery environment. This is especially important for resolving system corruption issues or preparing systems for deployment.
The other options you mentioned are related to different commands or actions:
- To move that file to a different Windows directory while also leaving the file in the current location: This describes copying a file, not moving it, and is typically done with the
copycommand. - To copy a group of files from one Windows directory to another: This action is performed using the
copycommand. - To relocate a file from one Windows directory to another one: Moving a file (which removes it from the original location) is done using the
movecommand.
Each of these commands serves a different purpose in managing files, directories, or system images within a computer’s operating system.
-
Why would a technician need to use the tasklist command?
- to display a list of current processes running on a local or a remote computer
- to create a new Windows directory
- to remove an empty directory
- to change from the current working folder to another folder
-
Explanation & Hint: A technician would need to use the
tasklistcommand for the following reason:- To display a list of current processes running on a local or a remote computer: The
tasklistcommand in Windows is used to provide information about the processes that are currently running on a system. This can be incredibly useful for a technician who needs to monitor, diagnose, or troubleshoot system performance or application issues. By usingtasklist, they can identify which processes are running and gather details such as process ID, memory usage, and more, which are crucial for effective system management and problem resolution.
The other options you mentioned are related to different commands:
- To create a new Windows directory: The appropriate command for this action is
mkdir(make directory). - To remove an empty directory: The command for this in Windows would typically be
rmdirorrd. - To change from the current working folder to another folder: The command used for this is
cd(change directory).
Each of these commands serves a different purpose in managing files, directories, or processes within a computer’s operating system.
- To display a list of current processes running on a local or a remote computer: The
-
Why would an analyst need to use the taskkill command?
- to end one or more processes on a PC based on process ID or image name
- to create a new Windows directory
- to remove an empty directory
- to change from the current working folder to another folder
-
Explanation & Hint: An analyst would need to use the
taskkillcommand for the following reason:- To end one or more processes on a PC based on process ID or image name: The
taskkillcommand in Windows is used to forcefully close (kill) one or more tasks or processes. Analysts may find this command useful to terminate unresponsive or unnecessary processes that are consuming too many system resources, potentially affecting the performance of other important tasks or analysis software they are running.
The other options you mentioned are associated with different commands:
- To create a new Windows directory: The appropriate command for this action is
mkdir(make directory). - To remove an empty directory: The command for this in Windows would typically be
rmdirorrd. - To change from the current working folder to another folder: The command used for this is
cd(change directory).
Each of these commands serves a distinct purpose in managing files, directories, or processes within a computer’s operating system.
- To end one or more processes on a PC based on process ID or image name: The
-
Why would an analyst need to use the msconfig command?
- to select some programs that will automatically run at startup
- to remove an empty directory
- to erase one or more files from a Windows directory
- to create a new Windows directory
-
Explanation & Hint: An analyst would need to use the
msconfigcommand for the following reason:- To select some programs that will automatically run at startup: The
msconfigcommand (System Configuration Utility) in Windows is used to troubleshoot the startup process. It allows users to enable or disable startup programs, services, and other settings that affect how the computer starts up. An analyst might use this tool to configure certain programs to run automatically upon startup, which can be essential for ensuring that necessary applications or scripts are launched as needed for their work.
The other options you mentioned are not related to the
msconfigcommand:- To remove an empty directory: The command for this in Windows would typically be
rmdirorrd. - To erase one or more files from a Windows directory: The command for this would be
delorerase. - To create a new Windows directory: The appropriate command for this action is
mkdir(make directory).
Each of these commands serves a different purpose in managing files and directories or system settings within a computer’s operating system.
- To select some programs that will automatically run at startup: The
-
Why would an analyst need to use the dir command?
- to show all of the files in the current directory
- to remove an empty directory
- to erase one or more files from a Windows directory
- to create a new Windows directory
-
Explanation & Hint: An analyst would need to use the
dircommand for the following reason:- To show all of the files in the current directory: The
dircommand in Windows is primarily used to list the files and directories contained in the current directory. This can be very useful for an analyst who needs to quickly view and assess the contents of a directory, perhaps to locate specific data files, reports, spreadsheets, or other relevant documents for analysis.
The other options you mentioned are associated with different commands:
- To remove an empty directory: The command used for this in Windows is typically
rmdirorrd. - To erase one or more files from a Windows directory: The command for this would be
delorerase. - To create a new Windows directory: The appropriate command for this action would be
mkdir(make directory).
Each of these commands serves a distinct purpose in managing files and directories within a computer’s file system.
- To show all of the files in the current directory: The
-
Why would a bank manager need to use the gpupdate command?
- to make the PC synchronize with new group policy settings
- to remove an empty directory
- to erase one or more files from a Windows directory
- to create a new Windows directory
-
Explanation & Hint: A bank manager might need to use the
gpupdatecommand for the following reason:- To make the PC synchronize with new group policy settings: The
gpupdatecommand in Windows is used to refresh Group Policy settings, ensuring that any changes or updates to the Group Policy are applied immediately without needing to restart the computer. In a banking environment, where security and policy adherence are crucial, a manager may use this command to quickly apply new security policies or updates across the network to maintain compliance and protect sensitive information.
The other options you mentioned are unrelated to the
gpupdatecommand:- To remove an empty directory: The command for this in Windows would typically be
rmdirorrd. - To erase one or more files from a Windows directory: The command for this would be
delorerase. - To create a new Windows directory: The appropriate command for this action is
mkdir(make directory).
Each of these commands serves a different purpose in managing files and directories or system settings within a computer’s operating system.
- To make the PC synchronize with new group policy settings: The
-
Why would a bank manager need to use the gpresult command?
- to verify the settings that are suspected to be incorrect
- to remove an empty directory
- to erase one or more files from a Windows directory
- to create a new Windows directory
-
Explanation & Hint: A bank manager might need to use the
gpresultcommand for the following reason:- To verify the settings that are suspected to be incorrect: The
gpresultcommand in Windows is used to display the Resultant Set of Policy (RSoP) information for a remote user and computer. This can be particularly useful for verifying Group Policy settings. In the context of a bank, where security and policy compliance are critical, a manager might use this command to ensure that the computer systems are adhering to the required security policies and configurations.
The other options you mentioned are not related to the
gpresultcommand:- To remove an empty directory: The command for this in Windows would typically be
rmdirorrd. - To erase one or more files from a Windows directory: The command for this would be
delorerase. - To create a new Windows directory: The appropriate command for this action is
mkdir(make directory).
Each of these commands serves a different purpose in managing files and directories or system settings within a computer’s operating system.
- To verify the settings that are suspected to be incorrect: The
-
Why would a lawyer need to use the cd command?
- to change from the current working folder to another folder
- to remove an empty directory
- to erase one or more files from a Windows directory
- to create a new Windows directory
-
Explanation & Hint: A lawyer, like any other professional who might use a computer, may need to use the
cd(change directory) command for the following reason:- To change from the current working folder to another folder: This is the primary purpose of the
cdcommand. It allows the user to navigate between different directories or folders within a file system. For a lawyer, this might be necessary to access different case files, documents, or other legal resources stored in various directories on their computer.
The other options you mentioned are associated with different commands:
- To remove an empty directory: The command used for this is typically
rmdir(orrm -don Unix/Linux systems). - To erase one or more files from a Windows directory: The command for this would be
delorerasein Windows. - To create a new Windows directory: The appropriate command for this action would be
mkdir(make directory).
Each of these commands serves a distinct purpose in managing files and directories within a computer’s file system.
- To change from the current working folder to another folder: This is the primary purpose of the
| IT Essentials 8 | |
| IT Essentials 8 Final - Mid-term - Cert | |
| Chapter 1 -9 Skills Assessment | NA |
| Chapter 10 - 14 Skills Assessment | NA |
| Practice Final Exam Answers Ch 1 - 9 | Online Test |
| Practice Final Exam Answers Ch 10 - 14 | Online Test |
| Final Exam Answers Ch 1 - 9 | Online Test |
| Final Exam Answers Ch 10 - 14 | Online Test |
| Final Exam Composite Answers Ch 1 - 14 | Online Test |
| A+ 220-1001 | Online Test |
| A+ 220-1002 | Online Test |