4.2.8 Lab – Configure Router-on-a-Stick Inter-VLAN Routing Answers Full 100% 2023 2024
This is Cisco 4.2.8 Lab – Configure Router-on-a-Stick Inter-VLAN Routing Answers Full 100% 2023 2024 for Cisco CCNA 2 v7 SRWE v7.02.
Lab – Configure Router-on-a-Stick Inter-VLAN Routing (Answers Version)
Answers Note: Red font color or gray highlights indicate text that appears in the Answers copy only.
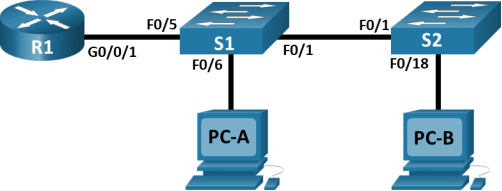
Topology
Addressing Table
|
Device |
Interface |
IP Address |
Subnet Mask |
Default Gateway |
|
R1 |
G0/0/1.3 |
192.168.3.1 |
255.255.255.0 |
N/A |
|
R1 |
G0/0/1.4 |
192.168.4.1 |
255.255.255.0 |
N/A |
|
R1 |
G0/0/1.8 |
N/A |
N/A |
N/A |
|
S1 |
VLAN 3 |
192.168.3.11 |
255.255.255.0 |
192.168.3.1 |
|
S2 |
VLAN 3 |
192.168.3.12 |
255.255.255.0 |
192.168.3.1 |
|
PC-A |
NIC |
192.168.3.3 |
255.255.255.0 |
192.168.3.1 |
|
PC-B |
NIC |
192.168.4.3 |
255.255.255.0 |
192.168.4.1 |
VLAN Table
|
VLAN |
Name |
Interface Assigned |
|
3 |
Management |
S1: VLAN 3 S2: VLAN 3 S1: F0/6 |
|
4 |
Operations |
S2: F0/18 |
|
7 |
ParkingLot |
S1: F0/2-4, F0/7-24, G0/1-2 S2: F0/2-17, F0/19-24, G0/1-2 |
|
8 |
Native |
N/A |
Objectives
Part 1: Build the Network and Configure Basic Device Settings
Part 2: Create VLANs and Assign Switch Ports
Part 3: Configure an 802.1Q Trunk between the Switches
Part 4: Configure Inter-VLAN Routing on the Router
Part 5: Verify Inter-VLAN Routing is working
Background / Scenario
Modern switches use virtual local-area networks (VLANs) to provide segmentation services traditionally provided by routers in LAN configurations. VLANs address scalability, security, and network management. In general, VLANs make it easier to design a network to support the goals of an organization. Communication between VLANs requires a device operating at Layer 3 of the OSI model. Routers in VLAN topologies provide additional security and traffic flow management.
VLAN trunks are used to span VLANs across multiple devices. Trunks allow the traffic from multiple VLANS to travel over a single link, while keeping the VLAN identification and segmentation intact. A particular kind of inter-VLAN routing, called “Router-On-A-Stick”, uses a trunk from the router to the switch to enable all VLANs to pass to the router.
In this lab, you will create VLANs on both switches in the topology, assign VLANs to switch access ports, verify that VLANs are working as expected, create VLAN trunks between the two switches and between S1 and R1, and configure Inter-VLAN routing on R1 to allow hosts in different VLANs to communicate, regardless of which subnet the host resides.
Note: The routers used with CCNA hands-on labs are Cisco 4221 with Cisco IOS XE Release 16.9.4 (universalk9 image). The switches used in the labs are Cisco Catalyst 2960s with Cisco IOS Release 15.2(2) (lanbasek9 image). Other routers, switches, and Cisco IOS versions can be used. Depending on the model and Cisco IOS version, the commands available and the output produced might vary from what is shown in the labs. Refer to the Router Interface Summary Table at the end of the lab for the correct interface identifiers.
Note: Ensure that the routers and switches have been erased and have no startup configurations. If you are unsure, contact your Answers.
Answers Note: Refer to the Answers Lab Manual for the procedures to initialize and reload devices.
Required Resources
- 1 Router (Cisco 4221 with Cisco IOS XE Release 16.9.4 universal image or comparable)
- 2 Switches (Cisco 2960 with Cisco IOS Release 15.2(2) lanbasek9 image or comparable)
- 2 PCs (Windows with a terminal emulation program, such as Tera Term)
- Console cables to configure the Cisco IOS devices via the console ports
- Ethernet cables as shown in the topology
Instructions
Part 1:Build the Network and Configure Basic Device Settings
In Part 1, you will set up the network topology and configure basic settings on the PC hosts and switches.
Step 1:Cable the network as shown in the topology.
Attach the devices as shown in the topology diagram, and cable as necessary.
Step 2:Configure basic settings for the router.
Open configuration window
- Console into the router and enable privileged EXEC mode.
router> enable
- Enter configuration mode.
router# config terminal
- Assign a device name to the router.
router(config)# hostname R1
- Disable DNS lookup to prevent the router from attempting to translate incorrectly entered commands as though they were host names.
R1(config)# no ip domain-lookup
- Assign class as the privileged EXEC encrypted password.
R1(config)# enable secret class
- Assign cisco as the console password and enable login.
R1(config)# line console 0
R1(config-line)# password cisco
R1(config-line)# login
- Assign cisco as the VTY password and enable login.
R1(config)# line vty 0 4
R1(config-line)# password cisco
R1(config-line)# login
- Encrypt the plaintext passwords.
R1(config)# service password-encryption
- Create a banner that warns anyone accessing the device that unauthorized access is prohibited.
R1(config)# banner motd $ Authorized Users Only! $
- Save the running configuration to the startup configuration file.
R1(config)# exit
R1# copy running-config startup-config
- Set the clock on the router.
R1# clock set 15:30:00 19 September 2019
Note: Use the question mark (?) to help with the correct sequence of parameters needed to execute this command.
Close configuration window
Step 3:Configure basic settings for each switch.
Open configuration window
- Console into the switch and enable privileged EXEC mode.
switch> enable
- Enter configuration mode.
switch# config terminal
- Assign a device name to the switch.
switch(config)# hostname S1
switch(config)# hostname S2
- Disable DNS lookup to prevent the router from attempting to translate incorrectly entered commands as though they were host names.
S1(config)# no ip domain-lookup
S2(config)# no ip domain-lookup
- Assign class as the privileged EXEC encrypted password.
S1(config)# enable secret class
S2(config)# enable secret class
- Assign cisco as the console password and enable login.
S1(config)# line console 0
S1(config-line)# password cisco
S1(config-line)# login
S2(config)# line console 0
S2(config-line)# password cisco
S2(config-line)# login
- Assign cisco as the vty password and enable login.
S1(config)# line vty 0 15
S1(config-line)# password cisco
S1(config-line)# login
S2(config)# line vty 0 15
S2(config-line)# password cisco
S2(config-line)# login
- Encrypt the plaintext passwords.
S1(config)# service password-encryption
S2(config)# service password-encryption
- Create a banner that warns anyone accessing the device that unauthorized access is prohibited.
S1(config)# banner motd $ Authorized Users Only! $
S2(config)# banner motd $ Authorized Users Only! $
- Set the clock on the switch.
S1# clock set 15:30:00 19 September 2019
S2# clock set 15:30:00 19 September 2019
Note: Use the question mark (?) to help with the correct sequence of parameters needed to execute this command.
- Copy the running configuration to the startup configuration.
S1# copy running-config startup-config
S2# copy running-config startup-config
Close configuration window
Step 4:Configure PC hosts.
Refer to the Addressing Table for PC host address information.
Part 2:Create VLANs and Assign Switch Ports
In Part 2, you will create VLANs, as specified in the table above, on both switches. You will then assign the VLANs to the appropriate interface. The show vlan command is used to verify your configuration settings. Complete the following tasks on each switch.
Step 1:Create VLANs on both switches.
Open configuration window
- Create and name the required VLANs on each switch from the table above.
S1(config)# vlan 3
S1(config-vlan)# name Management
S1(config-vlan)# vlan 4
S1(config-vlan)# name Operations
S1(config-vlan)# vlan 7
S1(config-vlan)# name ParkingLot
S1(config-vlan)# vlan 8
S1(config-vlan)# name Native
S2(config)# vlan 3
S2(config-vlan)# name Management
S2(config-vlan)# vlan 4
S2(config-vlan)# name Operations
S2(config-vlan)# vlan 7
S2(config-vlan)# name ParkingLot
S1(config-vlan)# vlan 8
S1(config-vlan)# name Native
- Configure the management interface and default gateway on each switch using the IP address information in the Addressing Table.
S1(config)# interface vlan 3
S1(config-if)# ip address 192.168.3.11 255.255.255.0
S1(config-if)# no shutdown
S1(config-if)# exit
S1(config)# ip default-gateway 192.168.3.1
S2(config)# interface vlan 3
S2(config-if)# ip address 192.168.3.12 255.255.255.0
S2(config-if)# no shutdown
S2(config-if)# exit
S2(config)# ip default-gateway 192.168.3.1
- Assign all unused ports on both switches to the ParkingLot VLAN, configure them for static access mode, and administratively deactivate them.
Note: The interface range command is helpful to accomplish this task with as few commands as necessary.
S1(config)# interface range f0/2 – 4 , f0/7 – 24 , g0/1 – 2
S1(config-if-range)# switchport mode access
S1(config-if-range)# switchport access vlan 7
S1(config-if-range)# shutdown
S2(config)# interface range f0/2 – 17, f0/19 – 24 , g0/1 – 2
S2(config-if-range)# switchport mode access
S2(config-if-range)# switchport access vlan 7
S2(config-if-range)# shutdown
Step 2:Assign VLANs to the correct switch interfaces.
- Assign used ports to the appropriate VLAN (specified in the VLAN table above) and configure them for static access mode. Be sure to do this on both switches
S1(config)# interface f0/6
S1(config-if)# switchport mode access
S1(config-if)# switchport access vlan 3
S2(config)# interface f0/18
S2(config-if)# switchport mode access
S2(config-if)# switchport access vlan 4
- Issue the show vlan brief command and verify that the VLANs are assigned to the correct interfaces.
S1# show vlan brief
VLAN NameStatusPorts
—- ——————————– ——— ——————————-
1defaultactiveFa0/1, Fa0/5
3ManagementactiveFa0/6
4Operationsactive
7ParkingLotactiveFa0/2, Fa0/3, Fa0/4, Fa0/7
Fa0/8, Fa0/9, Fa0/10, Fa0/11
Fa0/12, Fa0/13, Fa0/14, Fa0/15
Fa0/16, Fa0/17, Fa0/18, Fa0/19
Fa0/20, Fa0/21, Fa0/22, Fa0/23
Fa0/24, Gi0/1, Gi0/2
8Nativeactive
<output omitted>
S2# show vlan brief
VLAN NameStatusPorts
—- ——————————– ——— ——————————-
1defaultactiveFa0/1
3Managementactive
4OperationsactiveFa0/18
7ParkingLotactiveFa0/2, Fa0/3, Fa0/4, Fa0/5
Fa0/6, Fa0/7, Fa0/8, Fa0/9
Fa0/10, Fa0/11, Fa0/12, Fa0/13
Fa0/14, Fa0/15, Fa0/16, Fa0/17
Fa0/19, Fa0/20, Fa0/21, Fa0/22
Fa0/23, Fa0/24, Gi0/1, Gi0/2
8Nativeactive
<output omitted>
Close configuration window
Part 3:Configure an 802.1Q Trunk Between the Switches
In Part 3, you will manually configure interface F0/1 as a trunk.
Step 1:Manually configure trunk interface F0/1.
Open configuration window
- Change the switchport mode on interface F0/1 to force trunking. Make sure to do this on both switches.
S1(config)# interface f0/1
S1(config-if)# switchport mode trunk
S2(config)# interface f0/1
S2(config-if)# switchport mode trunk
- As a part of the trunk configuration, set the native VLAN to 8 on both switches. You may see error messages temporarily while the two interfaces are configured for different native VLANs.
S1(config-if)# switchport trunk native vlan 8
S2(config-if)# switchport trunk native vlan 8
- As another part of trunk configuration, specify that VLANs 3, 4, and 8 are only allowed to cross the trunk.
S1(config-if)# switchport trunk allowed vlan 3,4,8
S2(config-if)# switchport trunk allowed vlan 3,4,8
- Issue the show interfaces trunk command to verify trunking ports, the Native VLAN and allowed VLANs across the trunk.
S1# show interfaces trunk
PortModeEncapsulationStatusNative vlan
Fa0/3on802.1qtrunking8
PortVlans allowed on trunk
Fa0/33-4,8
PortVlans allowed and active in management domain
Fa0/33-4,8
PortVlans in spanning tree forwarding state and not pruned
Fa0/33-4,8
S2#show interfaces trunk
PortModeEncapsulationStatusNative vlan
Fa0/1on802.1qtrunking8
PortVlans allowed on trunk
Fa0/13-4,8
PortVlans allowed and active in management domain
Fa0/13-4,8
PortVlans in spanning tree forwarding state and not pruned
Fa0/13-4,8
Step 2:Manually configure S1’s trunk interface F0/5
- Configure the F0/5 on S1 with the same trunk parameters as F0/1. This is the trunk to the router.
S1(config)# interface f0/5
S1(config-if)# switchport mode trunk
S1(config-if)# switchport trunk native vlan 8
S1(config-if)# switchport trunk allowed vlan 3,4,8
- Save the running configuration to the startup configuration file on S1 and S2.
S1# copy running-config startup-config
S2# copy running-config startup-config
- Issue the show interfaces trunk command to verify trunking.
Question:
Why does F0/5 not appear in the list of trunks?
S1 port 5 will not be displayed because the GigabitEthernet 0/0/1 interface status on the router is administratively down.
Close configuration window
Part 4:Configure Inter-VLAN Routing on the Router
Open configuration window
- Activate interface G0/0/1 on the router.
R1(config)# interface g0/0/1
R1(config-if)# no shutdown
R1(config-if)# exit
- Configure sub-interfaces for each VLAN as specified in the IP addressing table. All sub-interfaces use 802.1Q encapsulation. Ensure the sub-interface for the native VLAN does not have an IP address assigned. Include a description for each sub-interface.
R1(config)# interface g0/0/1.3
R1(config-subif)# description Management Network
R1(config-subif)# encapsulation dot1q 3
R1(config-subif)# ip address 192.168.3.1 255.255.255.0
R1(config-subif)# interface g0/0/1.4
R1(config-subif)# description Operations Network
R1(config-subif)# encapsulation dot1q 4
R1(config-subif)# ip address 192.168.4.1 255.255.255.0
R1(config-subif)# interface g0/0/1.8
R1(config-subif)# description Native VLAN
R1(config-subif)# encapsulation dot1q 8 native
- Use the show ip interface brief command to verify the sub-interfaces are operational.
R1# show ip interface brief
InterfaceIP-AddressOK? Method StatusProtocol
GigabitEthernet0/0/0unassignedYES unsetupup
GigabitEthernet0/0/1unassignedYES unsetupup
GigabitEthernet0/0/1.3 192.168.3.1YES manual upup
GigabitEthernet0/0/1.4 192.168.4.1YES manual upup
GigabitEthernet0/0/1.8 unassignedYES unsetupup
<output omitted>
Close configuration window
Part 5:Verify Inter-VLAN Routing is Working
Step 1:Complete the following tests from PC-A. All should be successful.
Note: You may have to disable the PC firewall for pings to be successful.
- Ping from PC-A to its default gateway.
- Ping from PC-A to PC-B
- Ping from PC-A to S2
Step 2:Complete the following test from PC-B.
From the command prompt on PC-B, issue the tracert command to the address of PC-A.
Question:
What intermediate IP addresses are shown in the results?
The tracert output shows two entries in the results. The first hop is G0/0/1.4 on the R1 interface address, which is the Gateway address for PC-B. The second hop is PC-A’s address.
Router Interface Summary Table
|
Router Model |
Ethernet Interface #1 |
Ethernet Interface #2 |
Serial Interface #1 |
Serial Interface #2 |
|
1800 |
Fast Ethernet 0/0 (F0/0) |
Fast Ethernet 0/1 (F0/1) |
Serial 0/0/0 (S0/0/0) |
Serial 0/0/1 (S0/0/1) |
|
1900 |
Gigabit Ethernet 0/0 (G0/0) |
Gigabit Ethernet 0/1 (G0/1) |
Serial 0/0/0 (S0/0/0) |
Serial 0/0/1 (S0/0/1) |
|
2801 |
Fast Ethernet 0/0 (F0/0) |
Fast Ethernet 0/1 (F0/1) |
Serial 0/1/0 (S0/1/0) |
Serial 0/1/1 (S0/1/1) |
|
2811 |
Fast Ethernet 0/0 (F0/0) |
Fast Ethernet 0/1 (F0/1) |
Serial 0/0/0 (S0/0/0) |
Serial 0/0/1 (S0/0/1) |
|
2900 |
Gigabit Ethernet 0/0 (G0/0) |
Gigabit Ethernet 0/1 (G0/1) |
Serial 0/0/0 (S0/0/0) |
Serial 0/0/1 (S0/0/1) |
|
4221 |
Gigabit Ethernet 0/0/0 (G0/0/0) |
Gigabit Ethernet 0/0/1 (G0/0/1) |
Serial 0/1/0 (S0/1/0) |
Serial 0/1/1 (S0/1/1) |
|
4300 |
Gigabit Ethernet 0/0/0 (G0/0/0) |
Gigabit Ethernet 0/0/1 (G0/0/1) |
Serial 0/1/0 (S0/1/0) |
Serial 0/1/1 (S0/1/1) |
Note: To find out how the router is configured, look at the interfaces to identify the type of router and how many interfaces the router has. There is no way to effectively list all the combinations of configurations for each router class. This table includes identifiers for the possible combinations of Ethernet and Serial interfaces in the device. The table does not include any other type of interface, even though a specific router may contain one. An example of this might be an ISDN BRI interface. The string in parenthesis is the legal abbreviation that can be used in Cisco IOS commands to represent the interface.
End of Document
Device Configs – Final
Switch S1
S1# show run
Building configuration…
Current configuration : 3128 bytes
!
! Last configuration change at 21:13:27 UTC Thu Sep 19 2019
!
version 15.2
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
!
hostname S1
!
boot-start-marker
boot-end-marker
!
enable secret 5 $1$mjNn$IB.7cD5jpb2CpFN72u.w81
!
no aaa new-model
system mtu routing 1500
!
no ip domain-lookup
!
spanning-tree mode rapid-pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
interface FastEthernet0/1
switchport trunk allowed vlan 3,4,8
switchport trunk native vlan 8
switchport mode trunk
!
interface FastEthernet0/2
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/3
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/4
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/5
switchport trunk allowed vlan 3,4,8
switchport trunk native vlan 8
switchport mode trunk
!
interface FastEthernet0/6
switchport access vlan 3
switchport mode access
!
interface FastEthernet0/7
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/8
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/9
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/10
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/11
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/12
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/13
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/14
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/15
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/16
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/17
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/18
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/19
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/20
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/21
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/22
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/23
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/24
switchport access vlan 7
switchport mode access
shutdown
!
interface GigabitEthernet0/1
switchport access vlan 7
switchport mode access
shutdown
!
interface GigabitEthernet0/2
switchport access vlan 7
switchport mode access
shutdown
!
interface Vlan1
no ip address
shutdown
!
interface Vlan3
ip address 192.168.3.11 255.255.255.0
!
ip default-gateway 192.168.3.1
ip http server
ip http secure-server
!
banner motd ^C Authorized Users Only! ^C
!
line con 0
password 7 104D000A0618
login
line vty 0 4
password 7 104D000A0618
login
line vty 5 15
password 7 104D000A0618
login
!
end
Switch S2
S2# show run
Building configuration…
Current configuration : 3096 bytes
!
! Last configuration change at 21:14:03 UTC Thu Sep 19 2019
!
version 15.2
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
!
hostname S2
!
boot-start-marker
boot-end-marker
!
enable secret 5 $1$xNwL$Yvok3XJfU3OAjd91Jl6m2.
!
no aaa new-model
system mtu routing 1500
!
no ip domain-lookup
!
spanning-tree mode rapid-pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
interface FastEthernet0/1
switchport trunk allowed vlan 3,4,8
switchport trunk native vlan 8
switchport mode trunk
!
interface FastEthernet0/2
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/3
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/4
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/5
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/6
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/7
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/8
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/9
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/10
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/11
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/12
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/13
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/14
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/15
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/16
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/17
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/18
switchport access vlan 4
switchport mode access
!
interface FastEthernet0/19
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/20
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/21
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/22
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/23
switchport access vlan 7
switchport mode access
shutdown
!
interface FastEthernet0/24
switchport access vlan 7
switchport mode access
shutdown
!
interface GigabitEthernet0/1
switchport access vlan 7
switchport mode access
shutdown
!
interface GigabitEthernet0/2
switchport access vlan 7
switchport mode access
shutdown
!
interface Vlan1
no ip address
shutdown
!
interface Vlan3
ip address 192.168.3.12 255.255.255.0
!
ip default-gateway 192.168.3.1
ip http server
ip http secure-server
!
banner motd ^C Authorized Users Only! ^C
!
line con 0
password 7 01100F175804
login
line vty 0 4
password 7 01100F175804
login
line vty 5 15
password 7 01100F175804
login
!
end
Router R1
R1# show run
Building configuration…
Current configuration : 1940 bytes
!
version 16.9
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
platform qfp utilization monitor load 80
no platform punt-keepalive disable-kernel-core
!
hostname R1
!
boot-start-marker
boot-end-marker
!
!
vrf definition Mgmt-intf
!
address-family ipv4
exit-address-family
!
address-family ipv6
exit-address-family
!
enable secret 5 $1$o5iu$mWblQ/HSFMXl8z3PGLI../
!
no aaa new-model
!
no ip domain lookup
!
login on-success log
!
subscriber templating
!
multilink bundle-name authenticated
!
license boot level appxk9
license boot level securityk9
no license smart enable
diagnostic bootup level minimal
!
spanning-tree extend system-id
!
redundancy
mode none
!
interface GigabitEthernet0/0/0
no ip address
negotiation auto
!
interface GigabitEthernet0/0/1
no ip address
negotiation auto
!
interface GigabitEthernet0/0/1.3
description Management Network
encapsulation dot1Q 3
ip address 192.168.3.1 255.255.255.0
!
interface GigabitEthernet0/0/1.4
description Operations Network
encapsulation dot1Q 4
ip address 192.168.4.1 255.255.255.0
!
interface GigabitEthernet0/0/1.8
description Native VLAN
encapsulation dot1Q 8 native
!
interface Serial0/1/0
no ip address
!
interface Serial0/1/1
no ip address
!
interface GigabitEthernet0
vrf forwarding Mgmt-intf
no ip address
negotiation auto
!
ip forward-protocol nd
no ip http server
ip http secure-server
!
control-plane
!
banner motd ^C Authorized Users Only! ^C
!
line con 0
password 7 01100F175804
login
transport input none
stopbits 1
line aux 0
stopbits 1
line vty 0 4
password 7 070C285F4D06
login
!
end