CCNA 2 v7 SRWE v7.02 – Switching, Routing, and Wireless Essentials (Version 7.00) – Modules 1 – 4 – Switching Concepts, VLANs, and Inter-VLAN Routing Exam Answers 2023 2024 Full 100%
CCNA 2 v7 SRWE v7.02 – Switching, Routing, and Wireless Essentials (Version 7.00) – Modules 1 – 4 – Switching Concepts, VLANs, and Inter-VLAN Routing Exam Answers 2023 2024 Full 100%
This is NetAcad Cisco CCNA 2 v7 SRWE v7.02 Modules 1 – 4 Exam Answers 2023 2024 and Switching, Routing, and Wireless Essentials (Version 7.00) – Switching Concepts, VLANs, and Inter-VLAN Routing Exam Answers Full 100%. All answers have been verified by experts.
Cisco Netacad SRWE Version 7.00 CCNA 2 v7 Modules 1 – 4 – Switching Concepts, VLANs, and Inter-VLAN Routing Exam Answers 2023 2024 – Switching, Routing, and Wireless Essential
-
Which command displays information about the auto-MDIX setting for a specific interface?
- show interfaces
- show controllers
- show processes
- show running-config
Answers Explanation & Hints: To examine the auto-MDIX setting for a specific interface, the show controllers ethernet-controller command with the phy keyword should be used.
-
If one end of an Ethernet connection is configured for full duplex and the other end of the connection is configured for half duplex, where would late collisions be observed?
- on both ends of the connection
- on the full-duplex end of the connection
- only on serial interfaces
- on the half-duplex end of the connection
Answers Explanation & Hints: Full-duplex communications do not produce collisions. However, collisions often occur in half-duplex operations. When a connection has two different duplex configurations, the half-duplex end will experience late collisions. Collisions are found on Ethernet networks. Serial interfaces use technologies other than Ethernet.
-
Which command is used to set the BOOT environment variable that defines where to find the IOS image file on a switch?
- config-register
- boot system
- boot loader
- confreg
Answers Explanation & Hints: The boot system command is used to set the BOOT environment variable. The config-register and confreg commands are used to set the configuration register. The boot loader command supports commands to format the flash file system, reinstall the operating system software, and recover from a lost or forgotten password.
-
What does a switch use to locate and load the IOS image?
- BOOT environment variable
- IOS image file
- POST
- startup-config
- NVRAM
Answers Explanation & Hints: The BOOT environment variable contains the information about where to find the IOS image file.
-
Which protocol adds security to remote connections?
- FTP
- HTTP
- NetBEUI
- POP
- SSH
Answers Explanation & Hints: SSH allows a technician to securely connect to a remote network device for monitoring and troubleshooting. HTTP establishes web page requests. FTP manages file transfer. NetBEUI is not routed on the Internet. POP downloads email messages from email servers.
-
What is a characteristic of an IPv4 loopback interface on a Cisco IOS router?
- The no shutdown command is required to place this interface in an UP state.
- It is a logical interface internal to the router.
- Only one loopback interface can be enabled on a router.
- It is assigned to a physical port and can be connected to other devices.
Answers Explanation & Hints: The loopback interface is a logical interface internal to the router and is automatically placed in an UP state, as long as the router is functioning. It is not assigned to a physical port and can therefore never be connected to any other device. Multiple loopback interfaces can be enabled on a router.
-
What is the minimum Ethernet frame size that will not be discarded by the receiver as a runt frame?
- 64 bytes
- 512 bytes
- 1024 bytes
- 1500 bytes
Answers Explanation & Hints: The minimum Ethernet frame size is 64 bytes. Frames smaller than 64 bytes are considered collision fragments or runt frames and are discarded.
-
After which step of the switch bootup sequence is the boot loader executed?
- after CPU initialization
- after IOS localization
- after flash file system initialization
- after POST execution
Answers Explanation & Hints: The correct bootup sequence order is as follows:
1.- The switch loads and executes the POST.
2.- The switch loads the boot loader software.
3.- The boot loader performs low-level CPU initialization.
4.- The boot loader initializes the flash memory.
5.- The boot loader locates and loads the default IOS image.
-
Which impact does adding a Layer 2 switch have on a network?
- an increase in the number of dropped frames
- an increase in the size of the broadcast domain
- an increase in the number of network collisions
- an increase in the size of the collision domain
Answers Explanation & Hints: Adding a Layer 2 switch to a network increases the number of collision domains and increases the size of the broadcast domain. Layer 2 switches do not decrease the amount of broadcast traffic, do not increase the amount of network collisions and do not increase the number of dropped frames.
-
Which characteristic describes cut-through switching?
- Error-free fragments are forwarded, so switching occurs with lower latency.
- Frames are forwarded without any error checking.
- Only outgoing frames are checked for errors.
- Buffering is used to support different Ethernet speeds.
Answers Explanation & Hints: Cut-through switching reduces latency by forwarding frames as soon as the destination MAC address and the corresponding switch port are read from the MAC address table. This switching method does not perform any error checking and does not use buffers to support different Ethernet speeds. Error checking and buffers are characteristics of store-and-forward switching.
-
What is the significant difference between a hub and a Layer 2 LAN switch?
- A hub extends a collision domain, and a switch divides collision domains.
- A hub divides collision domains, and a switch divides broadcast domains.
- Each port of a hub is a collision domain, and each port of a switch is a broadcast domain.
- A hub forwards frames, and a switch forwards only packets.
Answers Explanation & Hints: Hubs operate only at the physical layer, forwarding bits as wire signals out all ports, and extend the collision domain of a network. Switches forward frames at the data link layer and each switch port is a separate collision domain which creates more, but smaller, collision domains. Switches do not manage broadcast domains because broadcast frames are always forwarded out all active ports.
-
Which statement is correct about Ethernet switch frame forwarding decisions?
- Frame forwarding decisions are based on MAC address and port mappings in the CAM table.
- Cut-through frame forwarding ensures that invalid frames are always dropped.
- Only frames with a broadcast destination address are forwarded out all active switch ports.
- Unicast frames are always forwarded regardless of the destination MAC address.
Answers Explanation & Hints: Cut-through frame forwarding reads up to only the first 22 bytes of a frame, which excludes the frame check sequence and thus invalid frames may be forwarded. In addition to broadcast frames, frames with a destination MAC address that is not in the CAM are also flooded out all active ports. Unicast frames are not always forwarded. Received frames with a destination MAC address that is associated with the switch port on which it is received are not forwarded because the destination exists on the network segment connected to that port.
-
How do switch buffers affect network performance?
- They provide error checking on the data received.
- They store frames received, thus preventing premature frame discarding when network congestion occurs.
- They provide extra memory for a particular port if autonegotiation of speed or duplex fails.
- They hold data temporarily when a collision occurs until normal data transmission resumes.
Answers Explanation & Hints: Switches have large frame buffers that allow data waiting to be transmitted to be stored so the data will not be dropped. This feature is beneficial especially if the incoming traffic is from a faster port than the egress port used for transmitting.
-
Which switch characteristic helps keep traffic local and alleviates network congestion?
- high port density
- fast port speed
- large frame buffers
- fast internal switching
Answers Explanation & Hints: Switches that have a lot of ports (high port density) reduce the number of switches required and keep some of the traffic locally on the switch, thus removing the need to send it between switches.
-
Which switch component reduces the amount of packet handling time inside the switch?
- ASIC
- dual processors
- large buffer size
- store-and-forward RAM
Answers Explanation & Hints: Application-specific integrated circuits (ASICs) are used in Cisco switches to speed up switch operations so that the switch can have an increased number of ports without degrading switch performance.
-
Refer to the exhibit. A switch receives a Layer 2 frame that contains a source MAC address of 000b.a023.c501 and a destination MAC address of 0050.0fae.75aa. Place the switch steps in the order they occur. (Not all options are used.)
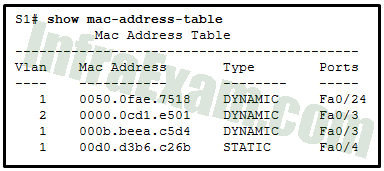
CCNA 2 v7 SRWE v7.02 – Modules 1 – 4 – Switching Concepts, VLANs, and Inter-VLAN Routing Exam Answers 02 
CCNA 2 v7 SRWE v7.02 – Modules 1 – 4 – Switching Concepts, VLANs, and Inter-VLAN Routing Exam Answers 001 Answers Explanation & Hints: The first step a switch does when processing a frame is to see if the source MAC address is in the MAC address table. If the address is not there, the switch adds it. The switch then examines the destination MAC address and compares it to the MAC address table. If the address is in the table, the switch forwards the frame out the corresponding port. If the address is missing from the table, the switch will forward the frame to all ports except the port through which the frame arrived.
-
What information is added to the switch table from incoming frames?
- source MAC address and incoming port number
- destination MAC address and incoming port number
- source IP address and incoming port number
- destination IP address and incoming port number
Answers Explanation & Hints: A switch “learns” or builds the MAC address table based on the source MAC address as a frame comes into the switch. A switch forwards the frame onward based on the destination MAC address.
-
Which switching method ensures that the incoming frame is error-free before forwarding?
- cut-through
- FCS
- fragment free
- store-and-forward
Answers Explanation & Hints: Two methods used by switches to transmit frames are store-and-forward and cut-through switching. The store-and-forward method performs error checking on the frame using the frame check sequence (FCS) value before sending the frame. In contrast, cut-through switching sends the frame as soon as the destination MAC address part of the header has been read and processed.
-
Refer to the exhibit. How many broadcast domains are displayed?
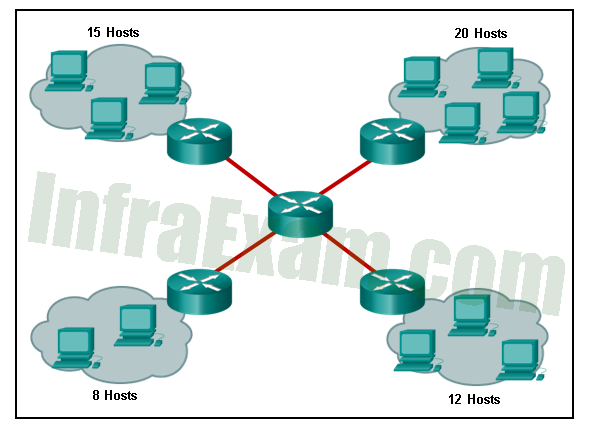
CCNA 2 v7 SRWE v7.02 – Modules 1 – 4 – Switching Concepts, VLANs, and Inter-VLAN Routing Exam Answers 10 - 1
- 4
- 8
- 16
- 55
Answers Explanation & Hints: A router defines a broadcast boundary, so every link between two routers is a broadcast domain. In the exhibit, 4 links between routers make 4 broadcast domains. Also, each LAN that is connected to a router is a broadcast domain. The 4 LANs in the exhibit result in 4 more broadcast domains, so there are 8 broadcast domains in all.
-
Under which two occasions should an administrator disable DTP while managing a local area network? (Choose two.)
- when connecting a Cisco switch to a non-Cisco switch
- when a neighbor switch uses a DTP mode of dynamic auto
- when a neighbor switch uses a DTP mode of dynamic desirable
- on links that should not be trunking
- on links that should dynamically attempt trunking
Answers Explanation & Hints: Cisco best practice recommends disabling DTP on links where trunking is not intended and when a Cisco switch is connected to a non-Cisco switch. DTP is required for dynamic trunk negotiation.
-
Which two characteristics describe the native VLAN? (Choose two.)
- Designed to carry traffic that is generated by users, this type of VLAN is also known as the default VLAN.
- The native VLAN traffic will be untagged across the trunk link.
- This VLAN is necessary for remote management of a switch.
- High priority traffic, such as voice traffic, uses the native VLAN.
- The native VLAN provides a common identifier to both ends of a trunk.
Answers Explanation & Hints: The native VLAN is assigned to 802.1Q trunks to provide a common identifier to both ends of the trunk link. Whatever VLAN native number is assigned to a port, or if the port is the default VLAN of 1, the port does not tag any frame in that VLAN as the traffic travels across the trunk. At the other end of the link, the receiving device that sees no tag knows the specific VLAN number because the receiving device must have the exact native VLAN number. The native VLAN should be an unused VLAN that is distinct from VLAN1, the default VLAN, as well as other VLANs. Data VLANs, also known as user VLANs, are configured to carry user-generated traffic, with the exception of high priority traffic, such as VoIP. Voice VLANs are configured for VoIP traffic. The management VLAN is configured to provide access to the management capabilities of a switch.
-
On a switch that is configured with multiple VLANs, which command will remove only VLAN 100 from the switch?
- Switch# delete flash:vlan.dat
- Switch(config-if)# no switchport access vlan 100
- Switch(config-if)# no switchport trunk allowed vlan 100
- Switch(config)# no vlan 100
Answers Explanation & Hints: To remove all VLANs from a switch, the delete flash:vlan.dat command would be used. To change the assigned VLAN for an interface, the no switchport access vlan 100 interface configuration command would be used. To remove VLAN 100 as an allowed VLAN on a trunk, the no switchport trunk allowed vlan 100 would be used, but this would not remove the VLAN from the switch. To delete a single VLAN, such as VLAN 100, the no vlan 100 global configuration command would be used.
-
Refer to the exhibit. A network administrator is reviewing port and VLAN assignments on switch S2 and notices that interfaces Gi0/1 and Gi0/2 are not included in the output. Why would the interfaces be missing from the output?
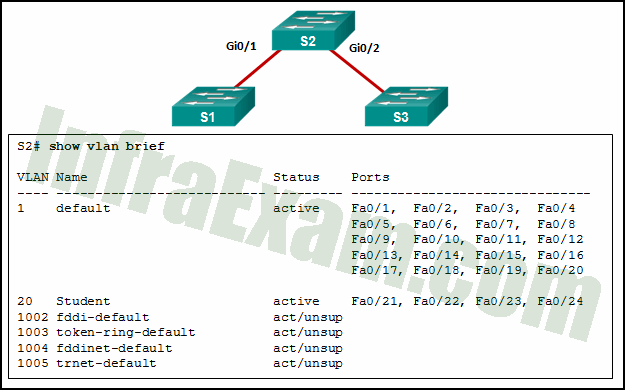
CCNA 2 v7 SRWE v7.02 – Modules 1 – 4 – Switching Concepts, VLANs, and Inter-VLAN Routing Exam Answers 11 - There is a native VLAN mismatch between the switches.
- There is no media connected to the interfaces.
- They are administratively shut down.
- They are configured as trunk interfaces.
Answers Explanation & Hints: Interfaces that are configured as trunks do not belong to a VLAN and therefore will not show in the output of the show vlan brief commands.
-
A network contains multiple VLANs spanning multiple switches. What happens when a device in VLAN 20 sends a broadcast Ethernet frame?
- All devices in all VLANs see the frame.
- Devices in VLAN 20 and the management VLAN see the frame.
- Only devices in VLAN 20 see the frame.
- Only devices that are connected to the local switch see the frame.
Answers Explanation & Hints: VLANs create logical broadcast domains that can span multiple VLAN segments. Ethernet frames that are sent by a device on a specific VLAN can only be seen by other devices in the same VLAN.
-
Refer to the exhibit. All workstations are configured correctly in VLAN 20. Workstations that are connected to switch SW1 are not able to send traffic to workstations on SW2. What could be done to remedy the problem?
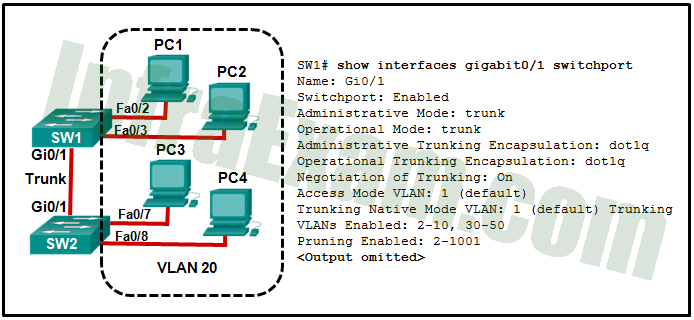
CCNA 2 v7 SRWE v7.02 – Modules 1 – 4 – Switching Concepts, VLANs, and Inter-VLAN Routing Exam Answers 12 - Allow VLAN 20 on the trunk link.
- Enable DTP on both ends of the trunk.
- Configure all workstations on SW1 to be part of the default VLAN.
- Configure all workstations on SW2 to be part of the native VLAN.
Answers Explanation & Hints: Enabling DTP on both switches simply allows negotiation of trunking. The “Negotiation of Trunking” line in the graphic shows that DTP is already enabled. The graphic also shows how the native VLAN is 1, and the default VLAN for any Cisco switch is 1. The graphic shows the PCs are to be in VLAN 20.
-
What happens to switch ports after the VLAN to which they are assigned is deleted?
- The ports are disabled.
- The ports are placed in trunk mode.
- The ports are assigned to VLAN1, the default VLAN.
- The ports stop communicating with the attached devices.
Answers Explanation & Hints: The affected ports must be reconfigured for an active VLAN.
-
Match the IEEE 802.1Q standard VLAN tag field with the description. (Not all options are used.)
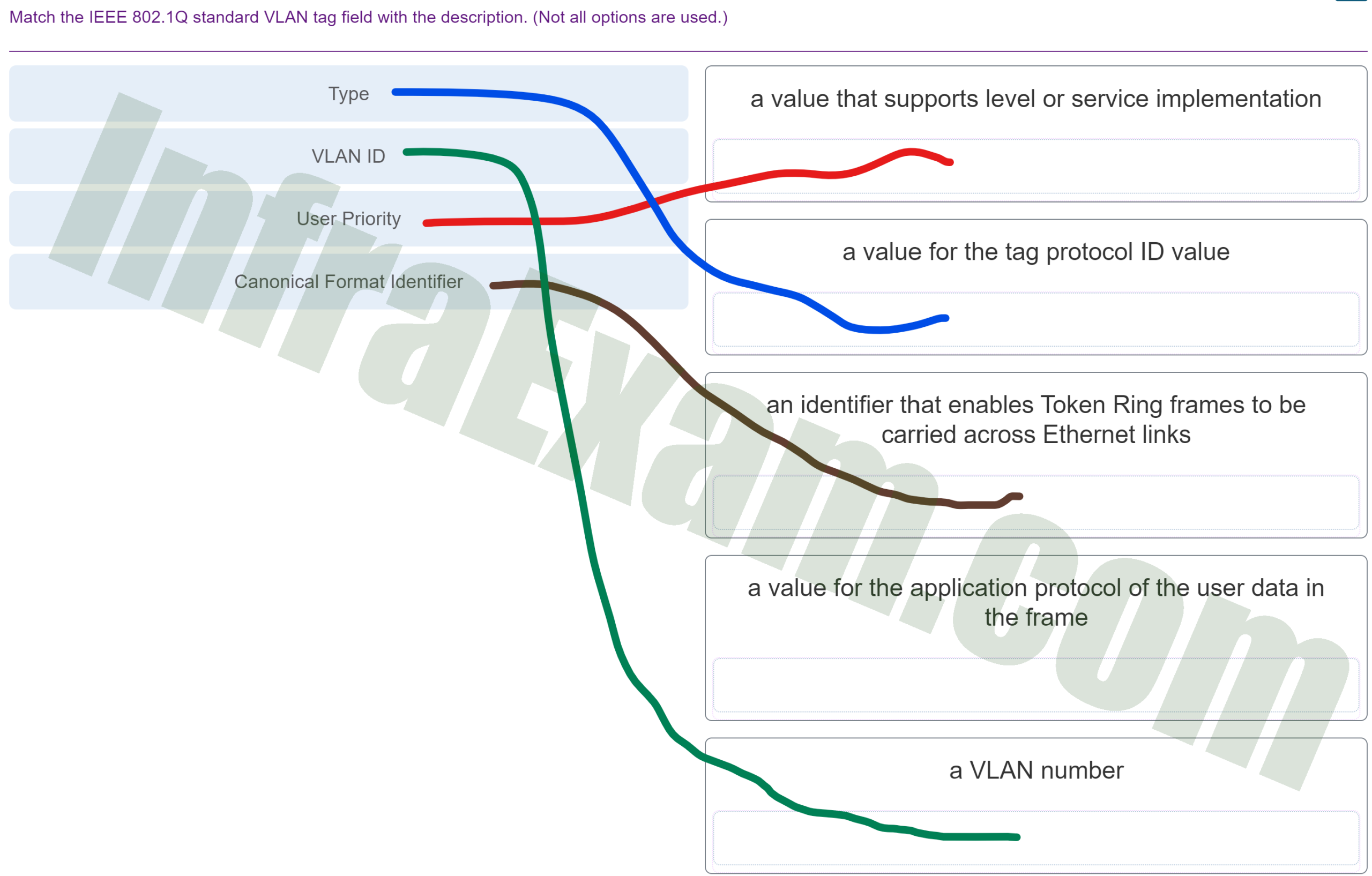
CCNA 2 v7 SRWE v7.02 – Modules 1 – 4 – Switching Concepts, VLANs, and Inter-VLAN Routing Exam Answers 002 Answers Explanation & Hints: The IEEE 802.1Q standard header includes a 4-byte VLAN tag:
- Type – A 2-byte value called the tag protocol ID (TPID) value.
- User priority – A 3-bit value that supports level or service implementation.
- Canonical Format Identifier (CFI) – A 1-bit identifier that enables Token Ring frames to be carried across Ethernet links.
- VLAN ID (VID) – A 12-bit VLAN identification number that supports up to 4096 VLAN IDs.
-
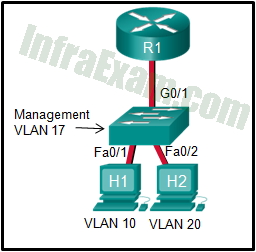
Refer to the exhibit. In what switch mode should port G0/1 be assigned if Cisco best practices are being used?
CCNA 2 v7 SRWE v7.02 – Modules 1 – 4 – Switching Concepts, VLANs, and Inter-VLAN Routing Exam Answers 15 - access
- trunk
- native
- auto
Answers Explanation & Hints: The router is used to route between the two VLANs, thus switch port G0/1 needs to be configured in trunk mode.
-
Match the DTP mode with its function. (Not all options are used.)
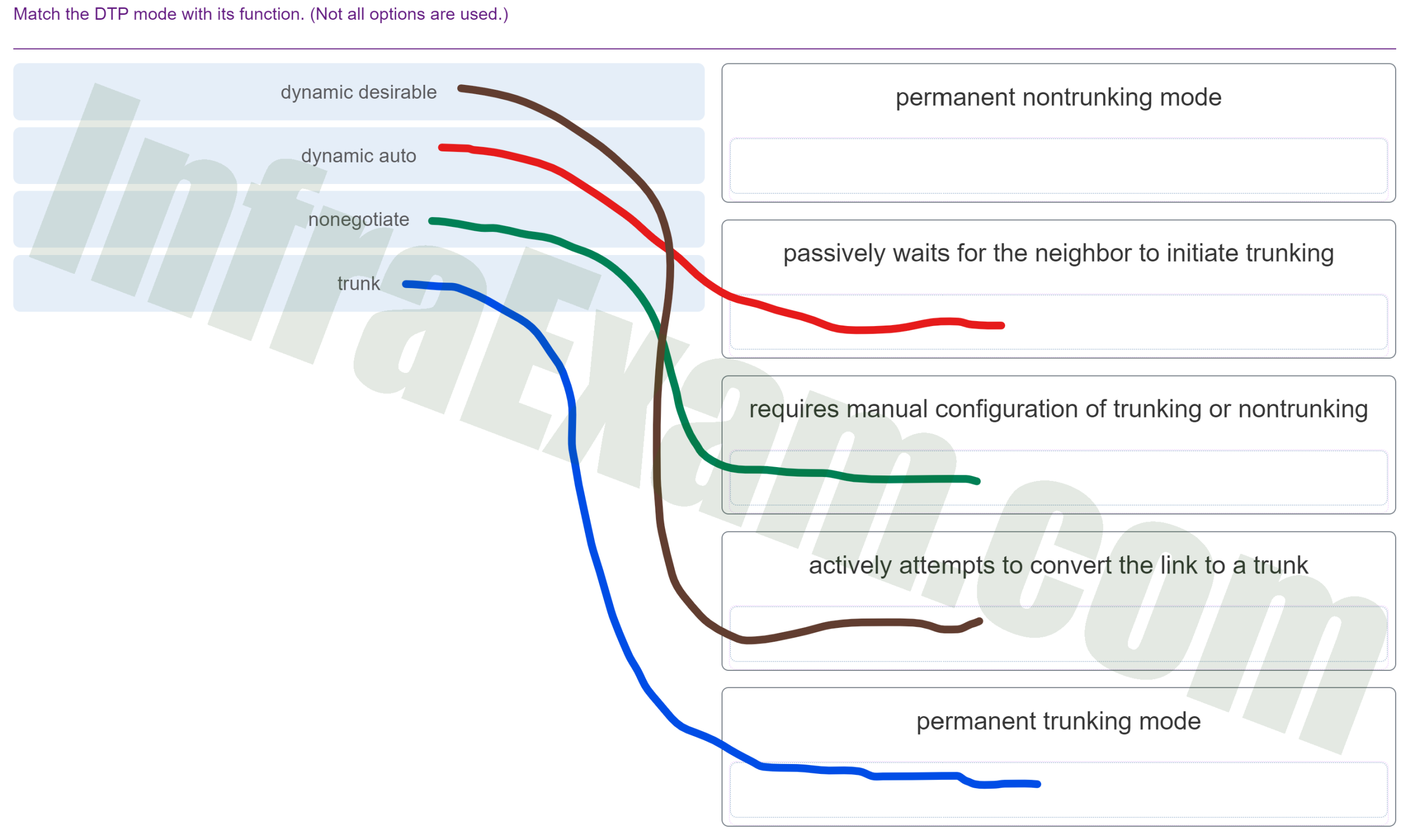
CCNA 2 v7 SRWE v7.02 – Modules 1 – 4 – Switching Concepts, VLANs, and Inter-VLAN Routing Exam Answers 003 Answers Explanation & Hints: The dynamic auto mode makes the interface become a trunk interface if the neighboring interface is set to trunk or desirable mode. The dynamic desirable mode makes the interface actively attempt to convert the link to a trunk link. The trunk mode puts the interface into permanent trunking mode and negotiates to convert the neighboring link into a trunk link. The nonegotiate mode prevents the interface from generating DTP frames.
-
Port Fa0/11 on a switch is assigned to VLAN 30. If the command no switchport access vlan 30 is entered on the Fa0/11 interface, what will happen?
- Port Fa0/11 will be shutdown.
- An error message would be displayed.
- Port Fa0/11 will be returned to VLAN 1.
- VLAN 30 will be deleted.
Answers Explanation & Hints: When the no switchport access vlan command is entered, the port is returned to the default VLAN 1. The port will remain active as a member of VLAN 1, and VLAN 30 will still be intact, even if no other ports are associated with it.
-
Which command displays the encapsulation type, the voice VLAN ID, and the access mode VLAN for the Fa0/1 interface?
- show vlan brief
- show interfaces Fa0/1 switchport
- show mac address-table interface Fa0/1
- show interfaces trunk
Answers Explanation & Hints: The show interfaces switchport command displays the following information for a given port:
Switchport
Administrative Mode
Operational Mode
Administrative Trunking Encapsulation
Operational Trunking Encapsulation
Negotiation of Trunking
Access Mode VLAN
Trunking Native Mode VLAN
Administrative Native VLAN tagging
Voice VLAN
-
Refer to the exhibit. A technician is programming switch SW3 to manage voice and data traffic through port Fa0/20. What, if anything, is wrong with the configuration?
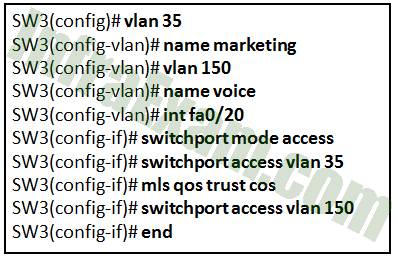
CCNA 2 v7 SRWE v7.02 – Modules 1 – 4 – Switching Concepts, VLANs, and Inter-VLAN Routing Exam Answers 17 - There is nothing wrong with the configuration.
- Interface Fa0/20 can only have one VLAN assigned.
- The mls qos trust cos command should reference VLAN 35.
- The command used to assign the voice VLAN to the switch port is incorrect.
Answers Explanation & Hints: The voice VLAN should be configured with the switchport voice vlan 150 command. A switch interface can be configured to support one data VLAN and one voice VLAN. The mls qos trust cos associates with the interface. Voice traffic must be trusted so that fields within the voice packet can be used to classify it for QoS.
-
Which four steps are needed to configure a voice VLAN on a switch port? (Choose four).
- Configure the interface as an IEEE 802.1Q trunk.
- Assign the voice VLAN to the switch port.
- Activate spanning-tree PortFast on the interface.
- Ensure that voice traffic is trusted and tagged with a CoS priority value.
- Add a voice VLAN.
- Configure the switch port interface with subinterfaces.
- Assign a data VLAN to the switch port.
- Configure the switch port in access mode.
Answers Explanation & Hints: To add an IP phone, the following commands should be added to the switch port:
SW3(config-vlan)# vlan 150
SW3(config-vlan)# name voice
SW3(config-vlan)# int fa0/20
SW3(config-if)# switchport mode access
SW3(config-if)# mls qos trust cos
SW3(config-if)# switchport access vlan 150
-
Refer to the exhibit. PC1 is unable to communicate with server 1. The network administrator issues the show interfaces trunk command to begin troubleshooting. What conclusion can be made based on the output of this command?
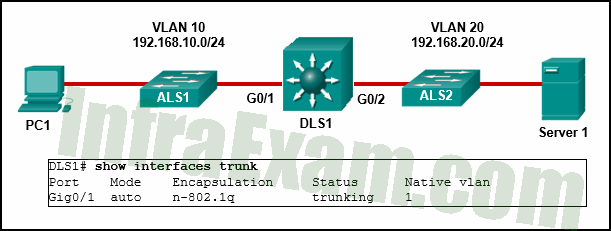
CCNA 2 v7 SRWE v7.02 – Modules 1 – 4 – Switching Concepts, VLANs, and Inter-VLAN Routing Exam Answers 18 - Interface G0/2 is not configured as a trunk.
- VLAN 20 has not been created.
- The encapsulation on interface G0/1 is incorrect.
- The DTP mode is incorrectly set to dynamic auto on interface G0/1.
Answers Explanation & Hints: In the show interfaces trunk output, the G0/2 interface of DLS1 is not listed. This indicates the interface has probably not been configured as a trunk link.
-
Refer to the exhibit. What is the cause of the error that is displayed in the configuration of inter-VLAN routing on router CiscoVille?
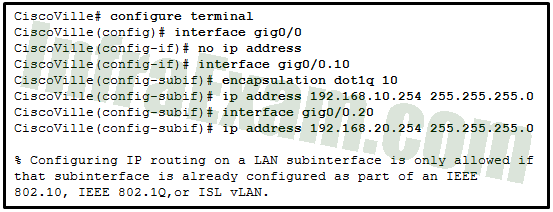
CCNA 2 v7 SRWE v7.02 – Modules 1 – 4 – Switching Concepts, VLANs, and Inter-VLAN Routing Exam Answers 05 - The gig0/0 interface does not support inter-VLAN routing.
- The no shutdown command has not been configured.
- The IP address on CiscoVille is incorrect.
- The encapsulation dot1Q 20 command has not been configured.
Answers Explanation & Hints: The steps to configure inter-VLAN routing must be completed in a specific order. Before configuring an IP address on a subinterface, the encapsulation dot1q VLAN_id command must be specified first.
-
Refer to the exhibit. A network administrator has configured router CiscoVille with the above commands to provide inter-VLAN routing. What command will be required on a switch that is connected to the Gi0/0 interface on router CiscoVille to allow inter-VLAN routing?
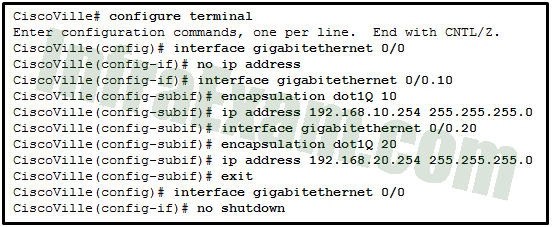
CCNA 2 v7 SRWE v7.02 – Modules 1 – 4 – Switching Concepts, VLANs, and Inter-VLAN Routing Exam Answers 06 - switchport mode access
- no switchport
- switchport mode trunk
- switchport mode dynamic desirable
Answers Explanation & Hints: When they are configured for inter-VLAN routing, routers do not support the dynamic trunking protocol that is used by switches. For router-on-a-stick configurations to function, a connected switch must use the command switchport mode trunk .
-
A high school uses VLAN15 for the laboratory network and VLAN30 for the faculty network. What is required to enable communication between these two VLANs while using the router-on-a-stick approach?
- A multilayer switch is needed.
- A router with at least two LAN interfaces is needed.
- Two groups of switches are needed, each with ports that are configured for one VLAN.
- A switch with a port that is configured as a trunk is needed when connecting to the router.
Answers Explanation & Hints: With router-on-a-stick, inter-VLAN routing is performed by a router with a single router interface that is connected to a switch port configured with trunk mode. Multiple subinterfaces, each configured for a VLAN, can be configured under the single physical router interface. Switches can have ports that are assigned to different VLANs, but communication between those VLANs requires routing function from the router. A multilayer switch is not used in a router-on-a-stick approach to inter-VLAN routing.
-
When routing a large number of VLANs, what are two disadvantages of using the router-on-a-stick inter-VLAN routing method rather than the multilayer switch inter-VLAN routing method? (Choose two.)
- Multiple SVIs are needed.
- A dedicated router is required.
- Router-on-a-stick requires subinterfaces to be configured on the same subnets.
- Router-on-a-stick requires multiple physical interfaces on a router.
- Multiple subinterfaces may impact the traffic flow speed.
Answers Explanation & Hints: With the router-on-a-stick inter-VLAN routing method, a dedicated router is required. It only needs one physical interface on the router to route traffic among multiple VLANs, by using subinterfaces on one physical interface. On the other hand, since traffic of all VLANs will have to go through the same physical interfaces, the throughput will be impacted. Also, a multilayer switch can use multiple SVIs to perform inter-VLAN routing.
-
Refer to the exhibit. A network administrator is verifying the configuration of inter-VLAN routing. Users complain that PCs on different VLANs cannot communicate. Based on the output, what are two configuration errors on switch interface Gi1/1? (Choose two.)
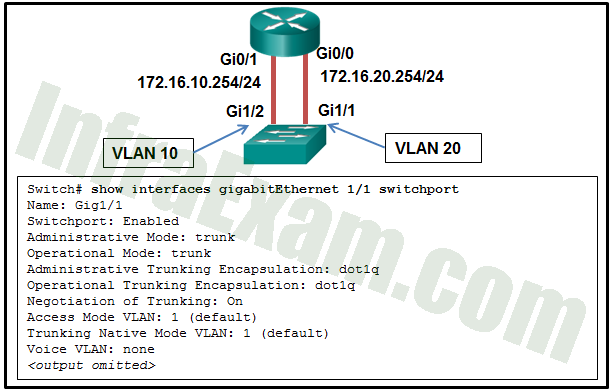
CCNA 2 v7 SRWE v7.02 – Modules 1 – 4 – Switching Concepts, VLANs, and Inter-VLAN Routing Exam Answers 08 - Gi1/1 is in the default VLAN.
- Voice VLAN is not assigned to Gi1/1.
- Gi1/1 is configured as trunk mode.
- Negotiation of trunking is turned on on Gi1/1.
- The trunking encapsulation protocol is configured wrong.
Answers Explanation & Hints: With legacy inter-VLAN routing methods, the switch ports that connect to the router should be configured as access mode and be assigned appropriate VLANs. In this scenario, the Gi1/1 interface should be in access mode with VLAN 10 assigned. The other options are default settings on the switch and have no effect on legacy inter-VLAN routing.
-
Refer to the exhibit. A network administrator is verifying the configuration of inter-VLAN routing. Users complain that PC2 cannot communicate with PC1. Based on the output, what is the possible cause of the problem?
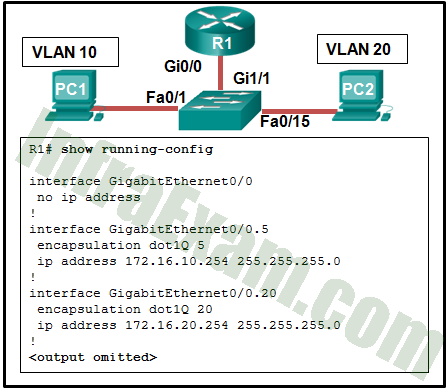
CCNA 2 v7 SRWE v7.02 – Modules 1 – 4 – Switching Concepts, VLANs, and Inter-VLAN Routing Exam Answers 09 - Gi0/0 is not configured as a trunk port.
- The command interface GigabitEthernet0/0.5 was entered incorrectly.
- There is no IP address configured on the interface Gi0/0.
- The no shutdown command is not entered on subinterfaces.
- The encapsulation dot1Q 5 command contains the wrong VLAN.
Answers Explanation & Hints: In router-on-a-stick, the subinterface configuration should match the VLAN number in the encapsulation command, in this case, the command encapsulation dot1Q 10 should be used for VLAN 10. Since subinterfaces are used, there is no need to configure IP on the physical interface Gi0/0. The trunk mode is configured on the switch port that connects to the router. The subinterfaces are turned on when they are added.
-
Refer to the exhibit. A network administrator has configured router CiscoVille with the above commands to provide inter-VLAN routing. What type of port will be required on a switch that is connected to Gi0/0 on router CiscoVille to allow inter-VLAN routing?
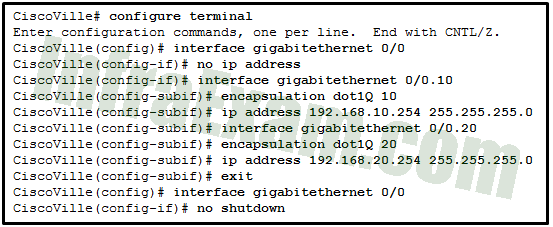
CCNA 2 v7 SRWE v7.02 – Modules 1 – 4 – Switching Concepts, VLANs, and Inter-VLAN Routing Exam Answers 07 - routed port
- access port
- trunk port
- SVI
Answers Explanation & Hints: To allow a router-on-a-stick configuration to function, a switch must be connected to the router via a trunk port to carry the VLANs to be routed. An SVI would be used on a multilayer switch where the switch is performing inter-VLAN routing.
-
Refer to the exhibit. A network administrator is configuring RT1 for inter-VLAN routing. The switch is configured correctly and is functional. Host1, Host2, and Host3 cannot communicate with each other. Based on the router configuration, what is causing the problem?
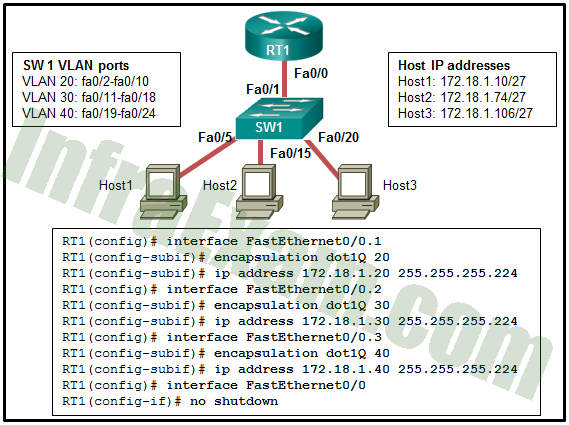
CCNA 2 v7 SRWE v7.02 – Modules 1 – 4 – Switching Concepts, VLANs, and Inter-VLAN Routing Exam Answers 13 - Interface Fa0/0 is missing IP address configuration information.
- IP addresses on the subinterfaces are incorrectly matched to the VLANs.
- Each subinterface of Fa0/0 needs separate no shutdown commands.
- Routers do not support 802.1Q encapsulation on subinterfaces.
Answers Explanation & Hints: Since Host 1 (in VLAN 20) has the IP 172.18.1.10/27, the subinterface Fa0/0.1 should be configured with an IP address in the network 172.168.1.0/27. Similarly, Fa0/0.2 should be with an IP address in the network 172.168.1.64/27 and Fa0/0.3 should be with an IP address in the network 172.168.1.96/27.
-
Refer to the exhibit. A router-on-a-stick configuration was implemented for VLANs 15, 30, and 45, according to the show running-config command output. PCs on VLAN 45 that are using the 172.16.45.0 /24 network are having trouble connecting to PCs on VLAN 30 in the 172.16.30.0 /24 network. Which error is most likely causing this problem?
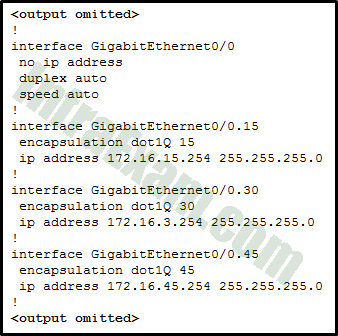
CCNA 2 v7 SRWE v7.02 – Modules 1 – 4 – Switching Concepts, VLANs, and Inter-VLAN Routing Exam Answers 14 - The wrong VLAN has been configured on GigabitEthernet 0/0.45.
- The command no shutdown is missing on GigabitEthernet 0/0.30.
- The GigabitEthernet 0/0 interface is missing an IP address.
- There is an incorrect IP address configured on GigabitEthernet 0/0.30.
Answers Explanation & Hints: he subinterface GigabitEthernet 0/0.30 has an IP address that does not correspond to the VLAN addressing scheme. The physical interface GigabitEthernet 0/0 does not need an IP address for the subinterfaces to function. Subinterfaces do not require the no shutdown command.
-
What is a characteristic of a routed port on a Layer 3 switch?
- It supports trunking.
- It is not assigned to a VLAN.
- It is commonly used as a WAN link.
- It cannot have an IP address assigned to it.
Answers Explanation & Hints: A routed port on a Layer 3 switch is commonly used for connecting between distribution and core layer switches or between a Layer 3 switch and a router. This port does not get VLAN or trunking commands assigned to it. Instead, the port is programmed with an IP address. This is commonly used when static routing is configured on the switch or when a routing protocol is being run between the Layer 3 switch and the router or another Layer 3 switch.
-
Refer to the exhibit. A network administrator needs to configure router-on-a-stick for the networks that are shown. How many subinterfaces will have to be created on the router if each VLAN that is shown is to be routed and each VLAN has its own subinterface?
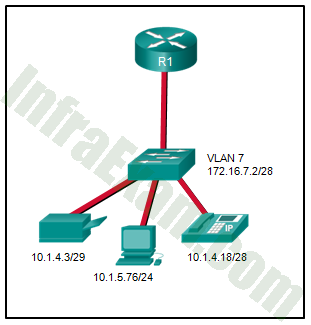
CCNA 2 v7 SRWE v7.02 – Modules 1 – 4 – Switching Concepts, VLANs, and Inter-VLAN Routing Exam Answers 04 - 1
- 2
- 3
- 4
- 5
Answers Explanation & Hints: Based on the IP addresses and masks given, the PC, printer, IP phone, and switch management VLAN are all on different VLANs. This situation will require four subinterfaces on the router.
-
A technician is configuring a new Cisco 2960 switch. What is the effect of issuing the BranchSw(config-if)# mdix auto command?
- It automatically adjusts the port to allow device connections to use either a straight-through or a crossover cable.
- It applies an IPv4 address to the virtual interface.
- It applies an IPv6 address to the virtual interface.
- It permits an IPv6 address to be configured on a switch physical interface.
- It updates the MAC address table for the associated port.
-
Explanation & Hint: - It automatically adjusts the port to allow device connections to use either a straight-through or a crossover cable.
- Correct Answer: This is the effect of the
mdix autocommand on a Cisco 2960 switch. Auto-MDIX (Automatic Medium-Dependent Interface Crossover) enables the switch to automatically detect the type of cable attached to a port (straight-through or crossover) and configure the interface accordingly to make the link operational. This feature simplifies network setup by allowing either type of cable to be used for connections without the need for manual crossover configuration.
- Correct Answer: This is the effect of the
- It applies an IPv4 address to the virtual interface.
- Incorrect Answer: The
mdix autocommand has nothing to do with configuring IP addresses. It is solely related to the physical layer (Layer 1) of the OSI model, dealing with the type of Ethernet cable used. Applying an IPv4 address to an interface is typically done with commands likeip address [IP address] [subnet mask].
- Incorrect Answer: The
- It applies an IPv6 address to the virtual interface.
- Incorrect Answer: Similar to the previous point, this command does not involve IPv6 address configuration. IPv6 address configuration on Cisco devices involves different commands, usually starting with
ipv6 address.
- Incorrect Answer: Similar to the previous point, this command does not involve IPv6 address configuration. IPv6 address configuration on Cisco devices involves different commands, usually starting with
- It permits an IPv6 address to be configured on a switch physical interface.
- Incorrect Answer: The
mdix autocommand does not influence the ability to configure IPv6 addresses on the interface. It is strictly related to the cable type detection and has no impact on the switch’s Layer 3 (network layer) capabilities, which includes IP address configuration.
- Incorrect Answer: The
- It updates the MAC address table for the associated port.
- Incorrect Answer: The MAC address table on a switch is used to map MAC addresses to their corresponding ports, a key function in forwarding Ethernet frames. The
mdix autocommand does not directly interact with or update the MAC address table; it is focused on the physical characteristics of the port connections. The MAC address table is typically updated dynamically as the switch learns the MAC addresses of devices connected to its ports.
- Incorrect Answer: The MAC address table on a switch is used to map MAC addresses to their corresponding ports, a key function in forwarding Ethernet frames. The
- It automatically adjusts the port to allow device connections to use either a straight-through or a crossover cable.
-
A technician is configuring a new Cisco 2960 switch. What is the effect of issuing the BranchSw(config-if)# ip address 172.18.33.88 255.255.255.0 command?
- It applies an IPv4 address to the virtual interface.
- It applies an IPv6 address to the virtual interface.
- It activates a virtual or physical switch interface.
- It permits an IPv6 address to be configured on a switch physical interface.
- It updates the MAC address table for the associated port.
-
Explanation & Hint: Let’s analyze the effects of the command
BranchSw(config-if)# ip address 172.18.33.88 255.255.255.0when issued on a Cisco 2960 switch:- It applies an IPv4 address to the virtual interface.
- Correct Answer: This command is used to assign an IPv4 address to an interface on a Cisco device. In this case, the IPv4 address
172.18.33.88with the subnet mask255.255.255.0is being applied. This can be done to both physical interfaces (like Ethernet ports) and virtual interfaces (like VLAN interfaces).
- Correct Answer: This command is used to assign an IPv4 address to an interface on a Cisco device. In this case, the IPv4 address
- It applies an IPv6 address to the virtual interface.
- Incorrect Answer: This command is specific to IPv4 addressing. For IPv6, a different command format is used, typically starting with
ipv6 address.
- Incorrect Answer: This command is specific to IPv4 addressing. For IPv6, a different command format is used, typically starting with
- It activates a virtual or physical switch interface.
- Partially Correct/Context-Dependent: While the command assigns an IP address to an interface, it does not itself activate the interface. Activation (or bringing the interface up) is typically done with the
no shutdowncommand. However, in many cases, assigning an IP address is part of the process of configuring and activating an interface for use.
- Partially Correct/Context-Dependent: While the command assigns an IP address to an interface, it does not itself activate the interface. Activation (or bringing the interface up) is typically done with the
- It permits an IPv6 address to be configured on a switch physical interface.
- Incorrect Answer: This command is strictly for assigning an IPv4 address and does not influence the ability to configure IPv6 addresses on the interface.
- It updates the MAC address table for the associated port.
- Incorrect Answer: This command is related to IP addressing and does not directly impact the MAC address table. The MAC address table on a switch is used to map MAC addresses to their corresponding ports for the purpose of forwarding Ethernet frames. It is updated based on the source MAC addresses seen in incoming frames, not through IP address configuration commands.
- It applies an IPv4 address to the virtual interface.
-
A technician is configuring a new Cisco 2960 switch. What is the effect of issuing the BranchSw# configure terminal command?
- It enters the global configuration mode.
- It enters configuration mode for a switch virtual interface.
- It applies an IPv4 address to the virtual interface.
- It updates the MAC address table for the associated port.
- It permits an IPv6 address to be configured on a switch physical interface.
-
Explanation & Hint: The command
BranchSw# configure terminalissued on a Cisco 2960 switch has a specific effect:- It enters the global configuration mode.
- Correct Answer: The command
configure terminal(often abbreviated asconf t) is used to enter the global configuration mode on Cisco devices. In this mode, a technician can make changes to the device’s configuration that affect the entire switch, such as setting system-wide parameters, configuring interfaces, setting up routing protocols, and more.
- Correct Answer: The command
- It enters configuration mode for a switch virtual interface.
- Incorrect Answer: While global configuration mode is the starting point for configuring various aspects of the switch, including virtual interfaces, this command by itself does not specifically enter the configuration mode for a virtual interface. To configure a virtual interface, you would further navigate from global configuration mode to the specific interface configuration mode.
- It applies an IPv4 address to the virtual interface.
- Incorrect Answer: This command is only for entering global configuration mode and does not apply an IPv4 address. Applying an IP address is a specific action taken within the interface configuration mode, which is accessed after entering global configuration mode.
- It updates the MAC address table for the associated port.
- Incorrect Answer: Entering global configuration mode does not directly impact the MAC address table. The MAC address table is automatically managed by the switch and is updated based on network traffic, not through entering a configuration mode.
- It permits an IPv6 address to be configured on a switch physical interface.
- Incorrect Answer: While entering global configuration mode is a prerequisite for many configuration tasks, including assigning IPv6 addresses to interfaces, this command alone does not specifically enable IPv6 address configuration. It’s a general command for accessing the various configuration modes on the switch. IPv6 configuration would be done in the respective interface configuration mode.
- It enters the global configuration mode.
-
A technician is configuring a new Cisco 2960 switch. What is the effect of issuing the BranchSw# configure terminal command?
- It enters the global configuration mode.
- It saves the running configuration to NVRAM.
- It disables a virtual or physical switch interface.
- It updates the MAC address table for the associated port.
- It saves the startup configuration to the running configuration.
-
Explanation & Hint: The command
BranchSw# configure terminalissued on a Cisco 2960 switch has a specific effect:- It enters the global configuration mode.
- Correct Answer: This command is used to enter the global configuration mode on Cisco devices. In this mode, a technician can make changes to the device’s configuration that affect the entire switch, such as setting system-wide parameters, configuring interfaces, setting up routing protocols, and more.
- It saves the running configuration to NVRAM.
- Incorrect Answer: The
configure terminalcommand does not save the running configuration to NVRAM. To save the current running configuration to NVRAM (so it persists after a reboot), the commandwrite memoryorcopy running-config startup-configis used.
- Incorrect Answer: The
- It disables a virtual or physical switch interface.
- Incorrect Answer: Entering global configuration mode does not disable any interfaces. To disable an interface, specific commands are used within the interface configuration mode, typically the
shutdowncommand.
- Incorrect Answer: Entering global configuration mode does not disable any interfaces. To disable an interface, specific commands are used within the interface configuration mode, typically the
- It updates the MAC address table for the associated port.
- Incorrect Answer: Entering global configuration mode does not directly impact the MAC address table. The MAC address table on a switch is automatically managed and updated based on the source MAC addresses of the frames received by the switch.
- It saves the startup configuration to the running configuration.
- Incorrect Answer: This command is for entering global configuration mode and does not involve copying the startup configuration to the running configuration. The startup configuration is the configuration loaded when the switch boots up, and to copy it to the running configuration, a different command, such as
copy startup-config running-config, would be used.
- Incorrect Answer: This command is for entering global configuration mode and does not involve copying the startup configuration to the running configuration. The startup configuration is the configuration loaded when the switch boots up, and to copy it to the running configuration, a different command, such as
- It enters the global configuration mode.
-
A technician is configuring a new Cisco 2960 switch. What is the effect of issuing the BranchSw(config-if)# shutdown command?
- It disables a virtual or physical switch interface.
- It saves the running configuration to NVRAM.
- It activates a virtual or physical switch interface.
- It updates the MAC address table for the associated port.
- It saves the startup configuration to the running configuration.
-
Explanation & Hint: The command
BranchSw(config-if)# shutdownissued on a Cisco 2960 switch, while in the interface configuration mode, has a specific effect:- It disables a virtual or physical switch interface.
- Correct Answer: The
shutdowncommand is used to administratively disable (or “shut down”) a network interface on a Cisco device. This can be applied to both virtual interfaces (like VLAN interfaces) and physical interfaces (like Ethernet ports). When this command is issued, the selected interface is turned off and will not transmit or receive traffic until it is re-enabled with theno shutdowncommand.
- Correct Answer: The
- It saves the running configuration to NVRAM.
- Incorrect Answer: The
shutdowncommand does not save the running configuration to the Non-Volatile Random-Access Memory (NVRAM). To save the current configuration so that it persists after a reboot, you would use thewrite memoryorcopy running-config startup-configcommand.
- Incorrect Answer: The
- It activates a virtual or physical switch interface.
- Incorrect Answer: This command does the opposite; it deactivates the selected interface. To activate an interface, the command
no shutdownis used.
- Incorrect Answer: This command does the opposite; it deactivates the selected interface. To activate an interface, the command
- It updates the MAC address table for the associated port.
- Incorrect Answer: The
shutdowncommand does not directly update the MAC address table. The MAC address table is managed automatically by the switch, updating based on the source MAC addresses of incoming frames. However, shutting down an interface may indirectly affect the MAC address table entries associated with that interface over time, as the switch will no longer see frames from that interface.
- Incorrect Answer: The
- It saves the startup configuration to the running configuration.
- Incorrect Answer: The
shutdowncommand does not involve saving or copying configurations. The startup configuration is the configuration the switch loads on booting, and the running configuration is the current active configuration. To copy the startup configuration to the running configuration, a different command, likecopy startup-config running-config, is used.
- Incorrect Answer: The
- It disables a virtual or physical switch interface.
-
A technician is configuring a new Cisco 2960 switch. What is the effect of issuing the BranchSw(config-if)# shutdown command?
- It disables a virtual or physical switch interface.
- It applies an IPv6 address to the virtual interface.
- It applies an IPv4 address to the virtual interface.
- It permits an IPv6 address to be configured on a switch physical interface.
- It updates the MAC address table for the associated port.
-
Explanation & Hint: The command
BranchSw(config-if)# shutdownissued on a Cisco 2960 switch has a specific effect:- It disables a virtual or physical switch interface.
- Correct Answer: The
shutdowncommand in the interface configuration mode is used to administratively disable a network interface on a Cisco device. This applies to both virtual interfaces (such as VLAN interfaces) and physical interfaces (like Ethernet ports). When issued, the selected interface is turned off and will not transmit or receive traffic until it is re-enabled using theno shutdowncommand.
- Correct Answer: The
- It applies an IPv6 address to the virtual interface.
- Incorrect Answer: The
shutdowncommand does not deal with IP address configuration. It is used exclusively for enabling or disabling interfaces. IPv6 addresses are applied using different commands, typically starting withipv6 address.
- Incorrect Answer: The
- It applies an IPv4 address to the virtual interface.
- Incorrect Answer: Similarly, the
shutdowncommand is not related to configuring IPv4 addresses. IPv4 address assignment is done using commands likeip address [IP address] [subnet mask].
- Incorrect Answer: Similarly, the
- It permits an IPv6 address to be configured on a switch physical interface.
- Incorrect Answer: The
shutdowncommand does not influence the ability to configure IPv6 addresses on the interface. It is solely for enabling or disabling the interface.
- Incorrect Answer: The
- It updates the MAC address table for the associated port.
- Incorrect Answer: The
shutdowncommand does not directly update the MAC address table. The MAC address table on a switch, which maps MAC addresses to corresponding switch ports, is managed automatically based on network traffic. However, disabling an interface might eventually impact its associated MAC address table entries, as the switch will no longer see frames from that interface.
- Incorrect Answer: The
- It disables a virtual or physical switch interface.
-
A technician is configuring a new Cisco 2960 switch. What is the effect of issuing the BranchSw(config-if)# ipv6 address 2001:db8:a2b4:88::1/64 command?
- It applies an IPv6 address to the virtual interface.
- It activates a virtual or physical switch interface.
- It applies an IPv4 address to the virtual interface.
- It permits an IPv6 address to be configured on a switch physical interface.
- It updates the MAC address table for the associated port.
-
Explanation & Hint: The command
BranchSw(config-if)# ipv6 address 2001:db8:a2b4:88::1/64issued on a Cisco 2960 switch has the following effect:- It applies an IPv6 address to the virtual interface.
- Correct Answer: This command is used to assign an IPv6 address to an interface on a Cisco device. In the given command, the IPv6 address
2001:db8:a2b4:88::1with a 64-bit subnet mask is being applied. This command can be used to configure IPv6 addresses on both physical interfaces (like Ethernet ports) and virtual interfaces (like VLAN interfaces).
- Correct Answer: This command is used to assign an IPv6 address to an interface on a Cisco device. In the given command, the IPv6 address
- It activates a virtual or physical switch interface.
- Incorrect Answer: While configuring an IPv6 address is part of setting up an interface, the command itself does not activate the interface. Interface activation (bringing it up) is typically achieved with the
no shutdowncommand.
- Incorrect Answer: While configuring an IPv6 address is part of setting up an interface, the command itself does not activate the interface. Interface activation (bringing it up) is typically achieved with the
- It applies an IPv4 address to the virtual interface.
- Incorrect Answer: This command is specific to IPv6 addressing and does not apply an IPv4 address. IPv4 addresses are configured with a different syntax, typically starting with
ip address.
- Incorrect Answer: This command is specific to IPv6 addressing and does not apply an IPv4 address. IPv4 addresses are configured with a different syntax, typically starting with
- It permits an IPv6 address to be configured on a switch physical interface.
- Partially Correct/Context-Dependent: The command indeed applies an IPv6 address, and in doing so, it demonstrates that the configuration of IPv6 addresses on the interface (be it physical or virtual) is permitted. However, the primary purpose of this command is to apply an IPv6 address, not just to permit its configuration.
- It updates the MAC address table for the associated port.
- Incorrect Answer: Assigning an IPv6 address to an interface does not directly update the MAC address table. The MAC address table, which maps MAC addresses to their corresponding switch ports, is primarily used in the forwarding of Ethernet frames based on Layer 2 information. The table is automatically updated based on network traffic, not through IP address configuration commands.
- It applies an IPv6 address to the virtual interface.
-
A technician is configuring a new Cisco 2960 switch. What is the effect of issuing the BranchSw(config-if)# exit command?
- It returns to global configuration mode.
- It returns to privileged mode.
- It configures the default gateway for the switch.
- It enters user mode.
- It saves the startup configuration to the running configuration.
-
Explanation & Hint: The command
BranchSw(config-if)# exitissued on a Cisco 2960 switch while in interface configuration mode has a specific effect:- It returns to global configuration mode.
- Correct Answer: The
exitcommand in the interface configuration mode is used to return to the global configuration mode. When you issue theexitcommand from the interface configuration mode, you move one level up in the hierarchy of the command-line interface, which is the global configuration mode in this context.
- Correct Answer: The
- It returns to privileged mode.
- Incorrect Answer: Privileged mode (also known as enable mode) is a higher level than global configuration mode. To return to privileged mode from interface configuration mode, you would typically issue the
exitcommand twice (once to return to global configuration mode, and again to return to privileged mode), or use theendcommand.
- Incorrect Answer: Privileged mode (also known as enable mode) is a higher level than global configuration mode. To return to privileged mode from interface configuration mode, you would typically issue the
- It configures the default gateway for the switch.
- Incorrect Answer: The
exitcommand does not configure any settings, including the default gateway. Setting the default gateway involves a specific command in the global configuration mode.
- Incorrect Answer: The
- It enters user mode.
- Incorrect Answer: User mode (also known as user exec mode) is the initial mode when you first log into a Cisco device. To return to user mode from interface configuration mode, you would need to issue the
exitcommand multiple times or use theendcommand to return to privileged mode and then exit to user mode.
- Incorrect Answer: User mode (also known as user exec mode) is the initial mode when you first log into a Cisco device. To return to user mode from interface configuration mode, you would need to issue the
- It saves the startup configuration to the running configuration.
- Incorrect Answer: The
exitcommand does not involve saving or copying configurations. To save the current running configuration to the startup configuration (so it’s loaded when the switch is restarted), you would use thewrite memoryorcopy running-config startup-configcommand. Theexitcommand is simply for navigating between different modes in the Cisco command-line interface.
- Incorrect Answer: The
- It returns to global configuration mode.
-
A technician is configuring a new Cisco 2960 switch. What is the effect of issuing the BranchSw> enable command?
- It enters privileged mode.
- It enters the global configuration mode.
- It enters configuration mode for a switch virtual interface.
- It updates the MAC address table for the associated port.
- It permits an IPv6 address to be configured on a switch physical interface.
-
Explanation & Hint: The command
BranchSw> enableissued on a Cisco 2960 switch has a specific effect:- It enters privileged mode.
- Correct Answer: The
enablecommand is used to enter privileged mode (also known as enable mode) from user mode on Cisco devices. In privileged mode, a user has access to a broader set of commands for managing and configuring the switch, including the ability to enter into global configuration mode.
- Correct Answer: The
- It enters the global configuration mode.
- Incorrect Answer: Entering global configuration mode is a separate step that requires an additional command (
configure terminal) after entering privileged mode. Theenablecommand alone does not take you directly to global configuration mode.
- Incorrect Answer: Entering global configuration mode is a separate step that requires an additional command (
- It enters configuration mode for a switch virtual interface.
- Incorrect Answer: Entering configuration mode for a virtual interface is done from global configuration mode, not directly from user mode. The
enablecommand is just the first step in a sequence of commands needed to configure a virtual interface.
- Incorrect Answer: Entering configuration mode for a virtual interface is done from global configuration mode, not directly from user mode. The
- It updates the MAC address table for the associated port.
- Incorrect Answer: The
enablecommand does not directly impact the MAC address table. The MAC address table, which is used to map MAC addresses to their corresponding switch ports, is managed automatically by the switch and is updated based on network traffic.
- Incorrect Answer: The
- It permits an IPv6 address to be configured on a switch physical interface.
- Incorrect Answer: While entering privileged mode (through the
enablecommand) is a necessary step before configuring IPv6 addresses on an interface, the command itself does not specifically permit IPv6 address configuration. To configure an IPv6 address, you would first enter privileged mode, then global configuration mode, and finally interface configuration mode where the IPv6 address can be assigned.
- Incorrect Answer: While entering privileged mode (through the
- It enters privileged mode.
-
A technician is configuring a new Cisco 2960 switch. What is the effect of issuing the BranchSw(config-if)# duplex full command?
- It allows data to flow in both directions at the same time on the interface.
- It allows data to flow in only one direction at a time on the interface
- It automatically adjusts the port to allow device connections to use either a straight-through or a crossover cable.
- It configures the switch as the default gateway.
- It encrypts user-mode passwords when users connect remotely.
-
Explanation & Hint: The command
BranchSw(config-if)# duplex fullissued on a Cisco 2960 switch in interface configuration mode has a specific effect:- It allows data to flow in both directions at the same time on the interface.
- Correct Answer: Setting an interface to
duplex fullenables full-duplex mode, which allows data to be transmitted and received simultaneously on that interface. This is beneficial for increasing the bandwidth and efficiency of the connection, as it effectively doubles the potential throughput compared to half-duplex.
- Correct Answer: Setting an interface to
- It allows data to flow in only one direction at a time on the interface.
- Incorrect Answer: This description pertains to half-duplex mode, not full-duplex mode. In half-duplex, data can flow in either direction, but not at the same time. The
duplex fullcommand is specifically for enabling full-duplex mode.
- Incorrect Answer: This description pertains to half-duplex mode, not full-duplex mode. In half-duplex, data can flow in either direction, but not at the same time. The
- It automatically adjusts the port to allow device connections to use either a straight-through or a crossover cable.
- Incorrect Answer: This functionality is related to the Auto-MDIX feature, not the duplex setting. Auto-MDIX automatically adjusts the port to support either type of Ethernet cable (straight-through or crossover), but it is independent of the duplex setting.
- It configures the switch as the default gateway.
- Incorrect Answer: The
duplex fullcommand has nothing to do with configuring a default gateway. The default gateway is typically configured with an IP routing command in the global configuration mode.
- Incorrect Answer: The
- It encrypts user-mode passwords when users connect remotely.
- Incorrect Answer: The
duplex fullcommand is solely for setting the duplex mode of an interface and does not relate to password encryption or user authentication methods. Encryption of passwords and remote user authentication is handled through different sets of commands and configurations.
- Incorrect Answer: The
- It allows data to flow in both directions at the same time on the interface.
-
What type of VLAN should not carry voice and network management traffic?
- data VLAN
- voice VLAN
- management VLAN
- security VLAN
-
Explanation & Hint: The type of VLAN that should not carry voice and network management traffic is the data VLAN.
- Data VLAN: This is specifically used for carrying user-generated traffic. It is designed to handle data specific to the end-users’ applications, such as file transfers, web browsing, and regular office data traffic. Voice and network management traffic are typically separated from user data traffic for efficiency, security, and quality of service reasons.
- Voice VLAN: This is specifically designed for VoIP (Voice over IP) traffic. It ensures quality of service for voice communications by prioritizing voice traffic over other types of traffic.
- Management VLAN: This VLAN is used for network management traffic. It is designed to allow network administrators to remotely manage and configure network devices like switches, routers, and access points.
- Security VLAN: Not a standard VLAN type by itself. However, if considering VLANs designed for security purposes (like segregating sensitive data or devices), these also would not typically carry voice or general network management traffic unless specifically related to those functions.
Each type of VLAN has its specific purpose and segregating different types of traffic ensures better network performance, security, and manageability.
-
What type of VLAN should not carry voice and network management traffic?
- data VLAN
- trunk VLAN
- security VLAN
- voice VLAN
-
Explanation & Hint: In this context, the type of VLAN that should not carry voice and network management traffic is the data VLAN.
- Data VLAN: This VLAN is intended for carrying regular user data traffic, such as file transfers, email, and web browsing. It is not designed for specialized traffic like voice or network management, which have different requirements in terms of quality of service and security.
- Trunk VLAN: The term “trunk VLAN” isn’t standard. Trunk ports on a switch carry traffic for multiple VLANs. These ports are configured to allow traffic from multiple VLANs, including data, voice, and management VLANs, across a single link. A trunk port isn’t a VLAN type but rather a method to pass multiple VLANs.
- Security VLAN: This isn’t a standard VLAN type in typical network terminology. However, if it refers to a VLAN set up for security-sensitive traffic or devices, it still wouldn’t be appropriate for voice and network management traffic unless specifically related to security functions.
- Voice VLAN: Specifically designed for VoIP (Voice over IP) traffic. It is optimized to carry voice traffic and ensure quality of service for voice communications.
Each type of VLAN has its specific purpose, and segregating different types of traffic ensures optimal network performance, security, and manageability. Voice and network management traffic have distinct requirements that are not typically met by a data VLAN.
-
What type of VLAN is designed to reserve bandwidth to ensure IP Phone quality?
- voice VLAN
- trunk VLAN
- security VLAN
- management VLAN
-
Explanation & Hint: The type of VLAN designed to reserve bandwidth to ensure IP Phone quality is the voice VLAN.
- Voice VLAN: This VLAN is specifically optimized for VoIP (Voice over IP) traffic. It helps in managing and prioritizing voice traffic over other types of network traffic, ensuring quality of service (QoS) for voice communications. This is crucial in maintaining the clarity and reliability of IP phone calls.
- Trunk VLAN: This term is a bit of a misnomer. In network terminology, a “trunk” is a port on a switch that carries traffic for multiple VLANs. It’s not a type of VLAN, but rather a configuration on network ports to allow multiple VLANs to pass through a single network link.
- Security VLAN: Not a standard VLAN type. If it refers to a VLAN set up for security-sensitive traffic or devices, its purpose would be to segregate and protect critical network segments and not specifically to enhance IP phone quality.
- Management VLAN: This VLAN is used for network management traffic. It is intended for managing network devices and services, not for prioritizing voice traffic.
Voice VLANs are essential in networks where voice and data traffic coexist, as they ensure that voice traffic gets the necessary bandwidth and priority to maintain call quality, which is critical in business environments.
-
What type of VLAN is initially the management VLAN?
- default VLAN
- native VLAN
- data VLAN
- management VLAN
-
Explanation & Hint: The type of VLAN that is initially the management VLAN is the default VLAN.
- Default VLAN: On Cisco switches, VLAN 1 is typically the default VLAN and is also used as the default management VLAN. This VLAN is active on all switch ports when the switch is first started and is often used for initial switch management access unless reconfigured.
- Native VLAN: The native VLAN is a concept used in trunk ports. It refers to the VLAN that carries untagged traffic on a trunk port. While the native VLAN can be used for management, it is not specifically designated as a management VLAN by default.
- Data VLAN: This term refers to VLANs typically used for carrying regular user data traffic, such as web browsing, file transfers, etc. Data VLANs are not specifically intended for management traffic.
- Management VLAN: While this term explicitly refers to VLANs used for management traffic, it’s not automatically set as such by default. A management VLAN must be explicitly configured. The default VLAN (VLAN 1) often serves this purpose until reconfigured.
-
What type of VLAN is designed to have a delay of less than 150 ms across the network?
- voice VLAN
- desirable VLAN
- trunk VLAN
- security VLAN
-
Explanation & Hint: The type of VLAN designed to have a delay of less than 150 ms across the network, especially to support quality of service for real-time voice communication, is the voice VLAN.
- Voice VLAN: Voice VLANs are specifically optimized for VoIP (Voice over IP) traffic. They are designed to prioritize voice traffic and manage network parameters such as delay (latency), jitter, and packet loss, which are critical for maintaining the quality of voice communications. The guideline of having a delay (latency) of less than 150 milliseconds is particularly important for voice traffic to ensure clear and uninterrupted voice communication.
- Desirable VLAN: This isn’t a standard VLAN type. It might be confused with a setting for Cisco’s Dynamic Trunking Protocol (DTP), where a port can be set to a “desirable” state to negotiate trunking, but this is unrelated to delay or latency specifications.
- Trunk VLAN: This term is not standard. A trunk in networking is a port configuration that allows multiple VLANs to be carried across the same physical link. It is not designed specifically for latency-sensitive applications like voice.
- Security VLAN: This is not a standard VLAN type. If it refers to a VLAN set up for security-sensitive traffic or devices, its purpose is focused on security rather than minimizing network delay.
-
What type of VLAN is used to separate the network into groups of users or devices?
- data VLAN
- management VLAN
- voice VLAN
- native VLAN
-
Explanation & Hint: The type of VLAN used to separate the network into groups of users or devices is the data VLAN.
- Data VLAN: This is used specifically for segregating and managing regular network traffic. Data VLANs are often created to divide a network into smaller parts based on factors like departmental or team boundaries, types of devices, or application categories. This segmentation helps in managing traffic flow, enhancing security, and improving network efficiency.
- Management VLAN: This VLAN is intended for network management traffic. It’s used for managing network devices and services, and is typically segregated from regular user data traffic for security and performance reasons.
- Voice VLAN: A voice VLAN is specifically optimized for VoIP (Voice over IP) traffic. It’s designed to prioritize voice traffic to ensure quality of service for voice communications, not for general user or device grouping.
- Native VLAN: The native VLAN is a concept associated with trunk ports. It refers to the VLAN that carries untagged traffic on a trunk port. The native VLAN is not specifically used for separating groups of users or devices, but rather for handling untagged traffic in a trunked network setup.
-
What type of VLAN is configured specifically for network traffic such as SSH, Telnet, HTTPS, HHTP, and SNMP?
- management VLAN
- security VLAN
- trunk VLAN
- voice VLAN
-
Explanation & Hint: The type of VLAN configured specifically for network traffic such as SSH, Telnet, HTTPS, HTTP, and SNMP is the management VLAN.
- Management VLAN: This VLAN is designated for managing network devices. It typically carries network management traffic used for administrative purposes, such as SSH (Secure Shell) for secure remote management, Telnet for terminal emulation, HTTPS and HTTP for web-based interfaces, and SNMP (Simple Network Management Protocol) for network management and monitoring. Segregating this traffic into a dedicated management VLAN enhances network security and efficiency.
- Security VLAN: While not a standard VLAN type, a VLAN set up for security purposes would focus more on segregating sensitive or critical network areas rather than specifically carrying management traffic.
- Trunk VLAN: This term isn’t standard. A trunk port on a switch carries traffic for multiple VLANs and is not dedicated to a specific type of traffic like management protocols.
- Voice VLAN: A voice VLAN is optimized for VoIP (Voice over IP) traffic. It’s designed to prioritize and manage voice communication traffic, not network management protocols.
-
What type of VLAN is configured specifically for network traffic such as SSH, Telnet, HTTPS, HHTP, and SNMP?
- management VLAN
- voice VLAN
- security VLAN
- native VLAN
-
Explanation & Hint: The type of VLAN configured specifically for network traffic such as SSH, Telnet, HTTPS, HTTP, and SNMP is the management VLAN.
- Management VLAN: This VLAN is used for network management traffic. It typically carries protocols used for administrative purposes, like SSH (Secure Shell) for secure remote management, Telnet for terminal emulation, HTTPS and HTTP for web-based interfaces, and SNMP (Simple Network Management Protocol) for network monitoring and management. Isolating this traffic in a dedicated management VLAN enhances network security and management efficiency.
- Voice VLAN: A voice VLAN is specifically optimized for VoIP (Voice over IP) traffic. It is designed for handling voice communication protocols, ensuring quality of service for voice calls, and is not typically used for network management traffic.
- Security VLAN: While not a standard VLAN type, a VLAN configured for security purposes would focus on segregating sensitive or critical network segments rather than carrying specific types of network management traffic.
- Native VLAN: The native VLAN is a concept associated with trunk ports on switches. It refers to the VLAN that carries untagged traffic on a trunk port. The native VLAN is not specifically used for carrying network management protocols but is more about handling VLAN tagging behavior on trunk links.
-
What type of VLAN supports untagged traffic?
- native VLAN
- voice VLAN
- security VLAN
- management VLAN
-
Explanation & Hint: The type of VLAN that supports untagged traffic is the native VLAN.
- Native VLAN: On a trunk port in a VLAN setup, the native VLAN is the one that carries traffic which is not tagged with any VLAN identifier. This concept is important in trunking configurations where multiple VLANs are carried over a single network link. The native VLAN is used for traffic that does not have a VLAN tag.
- Voice VLAN: This VLAN is specifically optimized for VoIP (Voice over IP) traffic. It is designed for carrying and prioritizing voice communication traffic and is not specifically related to untagged traffic.
- Security VLAN: This is not a standard VLAN type. If it refers to a VLAN set up for security-sensitive traffic or devices, it is not specifically associated with carrying untagged traffic.
- Management VLAN: This VLAN is used for managing network devices and typically carries network management traffic like SSH, Telnet, SNMP, etc. The management VLAN is not specifically defined by its ability to carry untagged traffic.
-
What type of VLAN supports untagged traffic?
- native VLAN
- desirable VLAN
- trunk VLAN
- security VLAN
-
Explanation & Hint: The type of VLAN that supports untagged traffic is the native VLAN.
- Native VLAN: On trunk ports in a VLAN configuration, the native VLAN is designated to carry traffic that is not tagged with a VLAN identifier. In a trunking setup where multiple VLANs are carried over a single link, the native VLAN is used for any untagged traffic that traverses the trunk.
- Desirable VLAN: This term does not refer to a type of VLAN. It might be confused with a setting in Cisco’s Dynamic Trunking Protocol (DTP), where a port can be set to a “desirable” state to actively negotiate forming a trunk link with another port. This setting is about trunk negotiation, not about the handling of untagged traffic.
- Trunk VLAN: This term is not standard. A trunk in network terminology is a link that can carry multiple VLANs. A trunk port itself is not a VLAN but a configuration that allows multiple VLANs, including the native VLAN, to pass over a single physical link.
- Security VLAN: This is not a standard VLAN type. A VLAN set up for security purposes would focus on segregating sensitive or critical parts of a network for security reasons and is not specifically related to the handling of untagged traffic.
-
Refer to the exhibit. A network administrator has configured R1 as shown. When the administrator checks the status of the serial interface, the interface is shown as being administratively down. What additional command must be entered on the serial interface of R1 to bring the interface up?
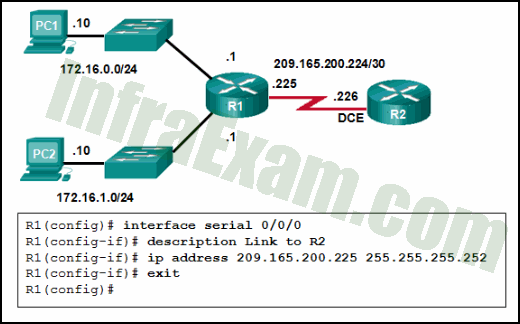
CCNA 2 v7 SRWE v7.02 – Modules 1 – 4 – Switching Concepts, VLANs, and Inter-VLAN Routing Exam Answers 01 - IPv6 enable
- clockrate 128000
- end
- no shutdown
Answers Explanation & Hints: By default all router interfaces are shut down. To bring the interfaces up, an administrator must issue the no shutdown command in interface mode.
-
Refer to the exhibit. The network administrator wants to configure Switch1 to allow SSH connections and prohibit Telnet connections. How should the network administrator change the displayed configuration to satisfy the requirement?
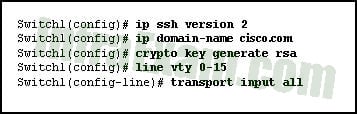
CCNA 2 v7 SRWE v7.02 – Modules 1 – 4 – Switching Concepts, VLANs, and Inter-VLAN Routing Exam Answers 16 - Use SSH version 1.
- Reconfigure the RSA key.
- Configure SSH on a different line.
- Modify the transport input command.
-
Explanation & Hint: To satisfy the requirement of allowing SSH connections and prohibiting Telnet connections, the network administrator should modify the
transport inputcommand. The currenttransport input allcommand allows all protocols, including Telnet, to be used to connect to the switch. To restrict the connections to only SSH, the command should be changed to:Switch(config-line)
This command will configure the switch to accept only SSH connections on the VTY lines, effectively prohibiting Telnet and enhancing the security of the switch’s remote management. The other options presented would not achieve the desired requirement:
- Using SSH version 1 would not be advised since it is less secure than version 2, which is already correctly configured with
ip ssh version 2. - Reconfiguring the RSA key is not necessary unless there is a specific issue with the key itself. The RSA key is used as part of the encryption process for establishing SSH connections.
- Configuring SSH on a different line is not required because the necessary lines (0-15) are already specified. The change needed is simply to restrict the protocols allowed on these lines.
- Using SSH version 1 would not be advised since it is less secure than version 2, which is already correctly configured with
-
Which solution would help a college alleviate network congestion due to collisions?
- a firewall that connects to two Internet providers
- a high port density switch
- a router with two Ethernet ports
- a router with three Ethernet ports
Answers Explanation & Hints: Switches provide microsegmentation so that one device does not compete for the same Ethernet network bandwidth with another network device, thus practically eliminating collisions. A high port density switch provides very fast connectivity for many devices.
-
Which two statements are correct with respect to SVI inter-VLAN routing? (Choose two.)
- Switching packets is faster with SVI.
- There is no need for a connection to a router.
- Virtual interfaces support subinterfaces.
- SVIs can be bundled into EtherChannels.
- SVIs eliminate the need for a default gateway in the hosts.
Answers Explanation & Hints: The SVI inter-VLAN routing method is faster than other methods. The switch can route the existing VLANs without the need for a router.
-
Refer to the exhibit. A network administrator is configuring inter-VLAN routing on a network. For now, only one VLAN is being used, but more will be added soon. What is the missing parameter that is shown as the highlighted question mark in the graphic?
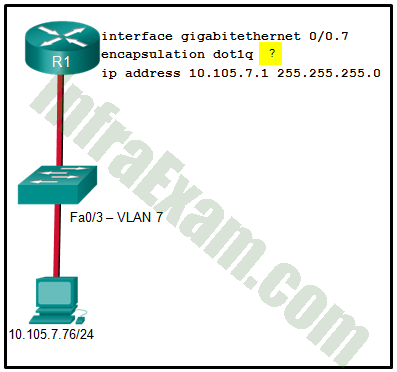
CCNA 2 v7 SRWE v7.02 – Modules 1 – 4 – Switching Concepts, VLANs, and Inter-VLAN Routing Exam Answers 03 - It identifies the subinterface.
- It identifies the VLAN number.
- It identifies the native VLAN number.
- It identifies the type of encapsulation that is used.
- It identifies the number of hosts that are allowed on the interface.
Answers Explanation & Hints: The completed command would be encapsulation dot1q 7 . The encapsulation dot1q part of the command enables trunking and identifies the type of trunking to use. The 7 identifies the VLAN number.
-
Which type of VLAN is used to designate which traffic is untagged when crossing a trunk port?
- data
- default
- native
- management
Answers Explanation & Hints: A native VLAN is the VLAN that does not receive a VLAN tag in the IEEE 802.1Q frame header. Cisco best practices recommend the use of an unused VLAN (not a data VLAN, the default VLAN of VLAN 1, or the management VLAN) as the native VLAN whenever possible.
-
A network administrator issues the show vlan brief command while troubleshooting a user support ticket. What output will be displayed?
- the VLAN assignment and membership for device MAC addresses
- the VLAN assignment and membership for all switch ports
- the VLAN assignment and trunking encapsulation
- the VLAN assignment and native VLAN
Answers Explanation & Hints: The show vlan brief command will provide information displaying the VLAN assignment and membership for all switch ports on a switch.
-
Open the PT Activity. Perform the tasks in the activity instructions and then answer the question.
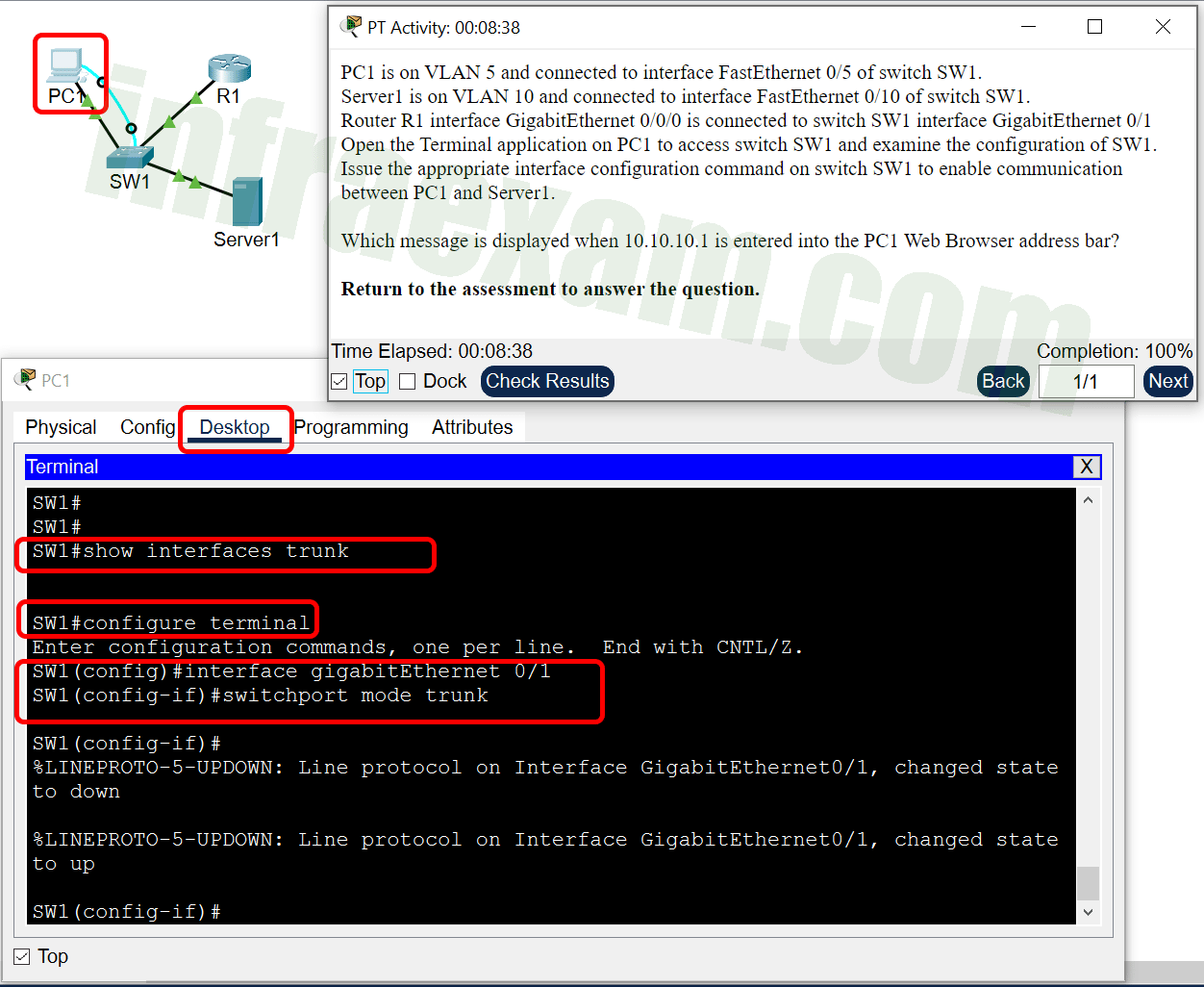
CCNA2 v7 SRWE – Modules 1 – 4 Switching Concepts, VLANs, and InterVLAN Routing Exam Answers PT 001A 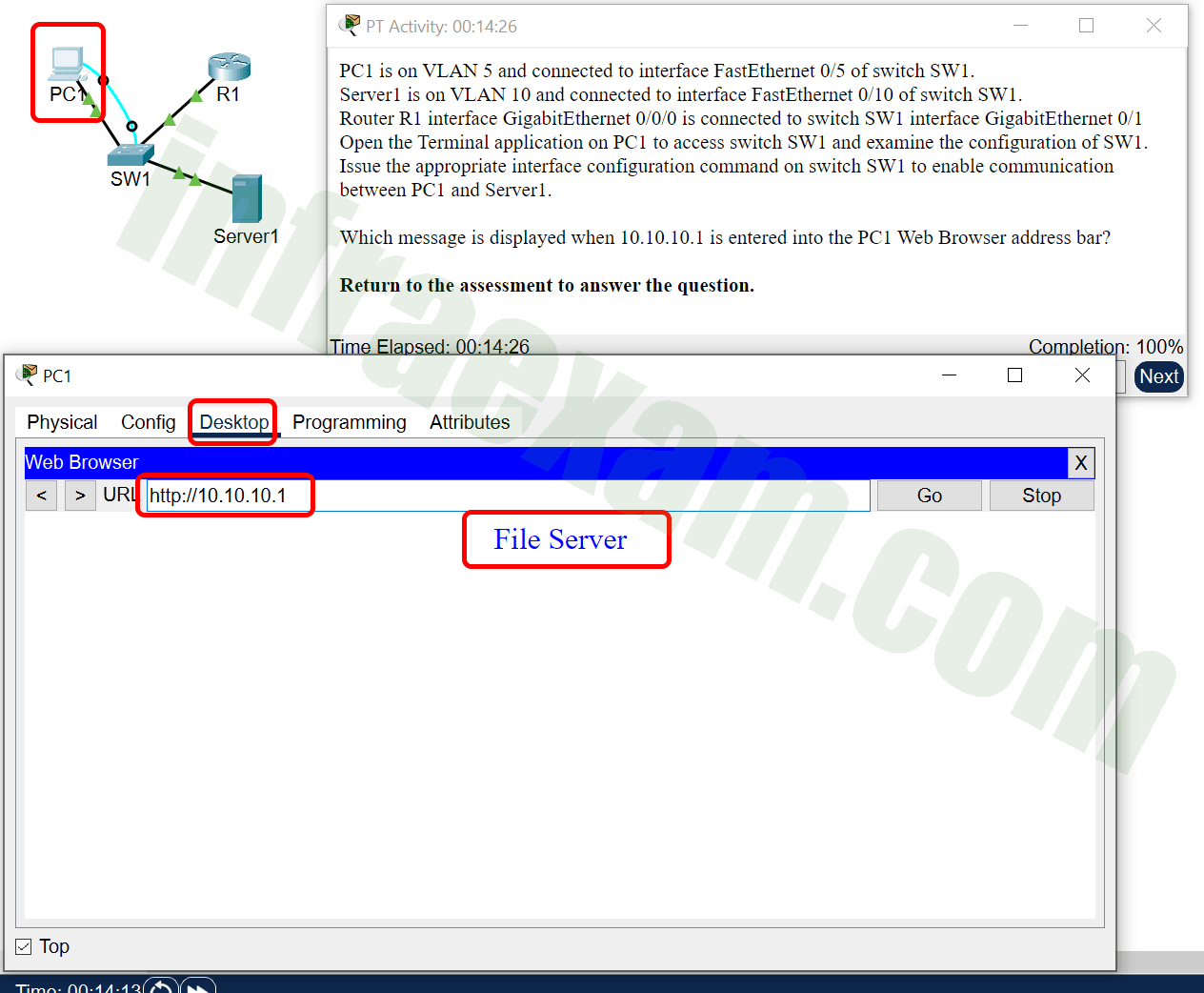
CCNA2 v7 SRWE – Modules 1 – 4 Switching Concepts, VLANs, and InterVLAN Routing Exam Answers PT 001B Which message is displayed when 10.10.10.1 is entered into the PC1 Web Browser address bar?
- Local Server
- Test Server
- File Server
- Cisco Server
Answers Explanation & Hints: Examining the configuration of switch SW1 shows that interface Gi0/1 is not configured as a trunk. Issuing the interface configuration command switchport mode trunk on this interface will enable communications between PC1 and Server1.