CV0-002 : CompTIA Cloud+ (CV0-002) : Part 03
-
A recent advertisement campaign has increased traffic to an e-commerce application that is hosted within a public cloud environment. Customers are reporting that it takes too long to load their pages and submit orders. A cloud administrator looks at the metrics from the environment and sees high utilization of the CPU and memory resources. The cloud provider offers several preconfigured sizes for server template: x-small, small, medium, large, x-large, and 2x-large.

CV0-002 Part 03 Q01 015 Given an expected increase in workload, which of the following is the BEST solution to improve application performance?
- Change the server template size for Inxpc003 to 2x-large.
- Provision additional Inxpc servers using the 2x-large template.
- Add memory to Inxpc002, Inxpc003, and Inxpc003.
- Change the role of Inxw001 from web to application.
-
A company wants to leverage a SaaS provider for its back-office services, and security is paramount. Which of the following solutions should a cloud engineer deploy to BEST meet the security requirements?
- Firewall
- IPS/IDS
- Proxy gateway
- CASB
-
A company upgraded a hosted vulnerability scanner to the latest version, and now tickets are not being created to assign critical vulnerabilities. After confirming the ticketing issue, all the scanning services are confirmed to be running on the VM. Which of the following is the MOST likely cause and best method to fix the issue?
- There was an IP change to the VM. Make changes to the server properties.
- The upgrade has a bug Reboot the server and attempt the upgrade again.
- The vulnerability scanner is on a different subnet. Open the ports, and it will reconnect.
- There is an application compatibility issue. Roll back to the previous working backup.
-
A system’s application servers need to be patched. The requirements for maintenance work are as follows:
System downtime is not allowed.
The application server in use must be in the sane patch status.
System performance must be maintained during patching work.
Testing after patching must be done before the application server is in use.
If any trouble occurs, recover the previous version in ten minutes.Which of the following methodologies should be selected?
- Rolling update
- Patching directly
- Blue-green deployment
- Three staging environments
-
A software development company is building cloud-ready applications and needs to determine the best approach for releasing software. Which of the following approaches should be used?
- Perform QA, develop, test, and release to production
- Test, perform QA, develop, and release to production
- Develop, perform QA, test, and release to production
- Develop, test, perform QA, and release to production
-
A customer recently provisioned a new server on the IaaS. The IP address assigned from the pool resolves to another hostname. Some user traffic is being dumped or is causing slowness because of this issue. Which of the following maintenance activities does the provider need to perform to prevent this issue?
- Use cloud provider tools to remove orphaned resources.
- Initiate resource reclamation.
- Run a script to remove stale DNS entries.
- Update outdated security firewall configurations.
-
A development team released a new version of an application and wants to deploy it to the cloud environment with a faster rollback and minimal downtime. Which of the following should the cloud administrator do to achieve this goal?
- Use a rolling deployment to update all the servers in the PROD cloud environment with the new application. To switch to the previous version, repeat the process.
- Deploy the application to the PROD cloud environment and the previous version to QA. To switch to the previous version, promote the QA environment to PROD.
- Deploy the application to a subset of servers in the environment and route traffic to these servers. To switch to the previous version, change the route to the non-updated servers.
- Deploy the application to a staging environment and force a failover to this environment. To restore the previous version, create a backup and restore from the previous night’s backup.
-
A university is running a DNA decoding project that will take seven years if it runs on its current internal mainframe. The university negotiated a deal with a large cloud provider, which will donate its cloud resource to process the DNA decoding during the low peak time throughout the world. Which of the following is the MOST important resource the university should ask the cloud provider to donate?
- A large storage for the DNA decoding results
- A larger pipe to transfer the results
- A closer datacenter to the university
- Any available compute resource
-
A business is demanding faster IT services turnaround from its IT groups. The current lead time between request and delivery is three weeks for a task that would take a competitor two days. An architect is asked to develop a solution to reduce the lead time of the request while ensuring adherence to the company policies. Which of the following is the BEST approach to achieve the stated objective?
- Document the desired state, complete a root cause analysis, and execute the flow.
- Revise the schedule, implement a waterfall methodology, and flatten the network.
- Identify deficiencies, optimize change management, and automate the workflow.
- Follow the company policies, execute the flow, and document results.
-
A storage administrator must choose the best replication methodology for storage.
The datacenters are on opposite sides of the country.
The RPO is 24 hours.
Replication and customer access use the same connections.
Replication should not impact customer access during the day.Which of the following solutions would BEST meet these requirements?
- Asynchronous
- Regional
- Multiregional
- Synchronous
-
The InfoSec team has directed compliance database activity monitoring without agents on a hosted database server in the public IaaS. Which of the following configurations is needed to ensure this requirement is achieved?
- Configure the agent configuration file to log to the syslog server.
- Configure sniffing mode on database traffic.
- Implement built-in database tracking functionality.
- Implement database encryption and secure copy to the NAS.
-
Ann. a user, has tried to connect to a VM hosted in a private cloud using her directory services credentials. After three attempts, she realizes the keyboard was set to German instead of English, and she was typing “z” instead of “y”. After fixing this issue, Ann is still unable to log in; however, other users can access the VM. Which of the following is the MOST likely cause?
- The default language on Ann’s computer is German.
- The account was locked.
- Directory services are offline.
- There is an account mismatch.
- The account localization settings are incorrect.
-
A cloud administrator is integrating account logins with Facebook, LinkedIn, and Twitter for marketing and to increase market presence using social media platforms. Given this scenario, which of the following components are needed to match these requirements? (Select TWO).
- SOAP
- SAML assertion
- Security token
- Identity provider
- Session state
-
A company uses its own private cloud, which has few available resources. Mission-critical systems and other information systems are running on it. A new system will be deployed on the private cloud. The following tests are included in the test plan:
Load test (2h)
Backup/restore test (6h)
Functional test (8h)
Failover test (1h)The work schedule of the existing system is shown below.
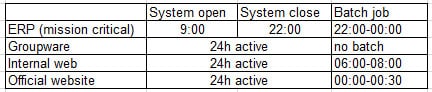
CV0-002 Part 03 Q14 016 To minimize the effect to the existing system, which of the following schedules is MOST suitable for the load test?
- 02:00-04:00
- 09:00-12:00
- 18:00-20:00
- 22:00-00:00
-
A cloud administrator is required to implement a solution to handle data-at-rest encryption requirements for a database. Which of the following would BEST satisfy the requirements?
- Install an SSL certificate and only allow secure connections to the server.
- Enable two-factor authentication on connections to the database server and log activities.
- Activate memory encryption on the virtual server and store the certificates remotely.
- Create a virtual encrypted disk, add it to the virtual server, and have the database write to it.
Explanation:
The question talks about data at rest. The only option given that offers a solution for data at rest is to encrypt the disk that the database writes to.
-
A cloud administrator is tasked with ensuring redundancy and high availability of an IaaS cloud platform environment. The administrator is given the following requirements:
Two web servers must share the same configurations and service client connections evenly.
Two database servers must share data and configurations, with only one being used at a time.Given the above, which of the following should the administrator propose to BEST meet these requirements? (Select TWO).
- The web server should be configured with a round-robin DNS with a CNAME record.
- The web server should be configured with a load balancer with a virtual IP address.
- The database server should be configured as an active-active cluster.
- The database server should be configured as an active-passive cluster.
- The availability aspect of the request does not currently exist in the IaaS cloud platform.
- The redundancy aspect of the request does not currently exist in the IaaS cloud platform.
-
In an IaaS model, to which of the following methodologies would the client apply a list of OS patches, assuming approval from CAB has been given?
- Using a patch management system, identify the hypervisor type, select a group of hypervisors to be patched, and perform a rolling application of patches.
- Using a patch management system, identify the guests that require patching, and select and apply the patches.
- Using a patch management system, identify the applications needing the patch, select the required application in a patch management console, and apply the patches.
- Using a patch management system, identify the services that require patching, and select and apply the patches.
-
A cloud administrator has finished building a virtual server template in a public cloud environment. The administrator is now cloning six servers from that template. Each server is configured with one private IP address and one public IP address. After starting the server instances, the cloud administrator notices that two of the servers do not have a public IP address. Which of the following is the MOST likely cause?
- The maximum number of public IP addresses has already been reached.
- The two servers are not attached to the correct public subnet.
- There is no Internet gateway configured in the cloud environment.
- The two servers do not have enough virtual network adapters attached.
-
A public cloud provider recently updated one of its services to provide a new type of application load balancer. The cloud administrator is tasked with building out a proof-of-concept using this new service type. The administrator sets out to update the scripts and notices the cloud provider does not list the load balancer as an available option type for deploying this service. Which of the following is the MOST likely reason?
- The administrator can deploy the new load balancer via the cloud provider’s web console.
- The administrator needs to update the version of the CLI tool.
- The administrator needs to write a new script function to call this service.
- The administrator is not using the correct cloud provider account.
-
A cloud service provider wants to offer hardened virtual server images for provisioning purposes. This will enable users to use only the operating system services that are allowed by the provider. Which of the following tasks are MOST appropriate for the hardening process? (Select TWO).
- Disable automatic updates.
- Disable the command prompt.
- Disable unneeded ports and services.
- Disable the local administrator account.
- Disable the remote desktop connection.
- Disable complex passwords.