CV0-002 : CompTIA Cloud+ (CV0-002) : Part 05
-
A technician is configuring a new web application to be highly available. The technician has configured multiple web servers in different availability zones at a public cloud provider. The application requires users to be directed to the same server each time they visit. Which of the following network components is MOST likely to accomplish this?
- Network firewall
- Intrusion prevention system
- Global load balancer
- Virtual private network
-
Which of the following would be appropriate when considering inbound access security for a web-based SaaS solution?
- Antivirus/anti-malware
- IPSec
- Firewall
- Obfuscation
-
A company has an SLA of 15ms for storage latency.
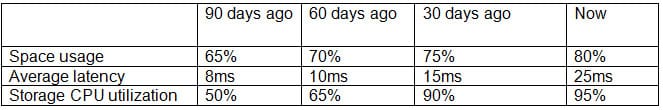
CV0-002 Part 05 Q03 019 Given the above metrics, which of the following is the MOST appropriate change to the environment?
- Add computing nodes and data nodes on the storage side.
- Add more storage shelves to the current array.
- Enable compression on the storage side.
- Enable deduplication on the storage side.
-
A VM was deleted by mistake today at 11:05 a.m. Below are the backups currently available for the VM:
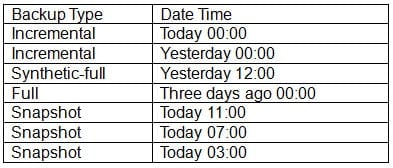
CV0-002 Part 05 Q04 020 Crash-consistent restore is acceptable. Which of the following backups should be chosen?
- Snapshot from today at 11:00
- Full from three days ago at 00:00
- Incremental from today at 00:00
- Synthetic-full from yesterday at 12:00
-
After deploying multiple copies of database servers, data scrambling is started on them to anonymize user data. A few minutes later, the systems administrator receives multiple complaints regarding the performance of other VMs. CPU and memory have been eliminated as possible bottlenecks. Which of the following should be verified NEXT as a possible bottleneck?
- Storage array
- Database drivers
- Hardware load balancer
- Internet connection speed
-
A cloud administrator is configuring a bastion host. The bastion host will be used to administer systems in the cloud remotely from the administrator’s on-premises desktop. The administrator is given the following requirements:
Ensure port 22 is open on the host and only allow the public IP of the on-premises router/firewall.
Ensure port 3389 is open on the host and only allow the public IP of the on-premises router/firewall.
Harden these services with PKI (where applicable).Given this scenario, which of the following should the administrator utilize to BEST address these requirements? (Select THREE).
- RDP protocol from the desktop to the bastion host
- Telnet protocol from the desktop to the bastion host
- SSH protocol from the desktop to the bastion host
- MD5 and RC4 with a signed certificate
- RSA and AES with a signed certificate
- Blowfish and SHA-1 with a signed certificate
- VNC protocol from the desktop to the bastion host
-
After scheduled network maintenance, users report that an externally hosted web application is particularly slow to load. Small items on the page load such as text documents and markup, but larger multimedia files do not load. Which of the following is the MOST likely cause of the reported issues?
- Incorrect MTU in the network segment
- Misconfiguration of QoS settings
- Incorrect VLAN for the affected PCs
- Excessive latency on the local LAN segment
-
A cloud administrator for a state government agency is tasked with giving access to the voter registration application to a government agency in another state. Only authorized officials from each state should access the application. These agencies have a common environment where applications have been deployed in the past. Which of the following should the cloud administrator do to give access to the application?
- Deploy part of the application into a public cloud and establish secure connections to a private cloud environment.
- Deploy the application to a community cloud that is shared with multiple state government agencies only.
- Deploy the application to a public cloud and implement ACLs and security access policies to limit access.
- Deploy the application to the state’s private cloud and give authentication credentials to the other state’s authorized officials.
-
A software solution must be deployed based on the most granular access level. Which of the following methods should be used to meet the requirements?
- Group
- RBAC
- File-based
- LDAP
-
Worldwide users from an organization are experiencing intermittent access to a global cloud application. The cloud provider availability dashboard shows all resource availability has been 100% in the last two weeks. No network outages have been reported. Which of the following should the organization’s administrator do BEFORE calling the cloud provider?
- Check the firewall rules on the headquarters site.
- Restart the application and applicable services.
- Allow all traffic at the cloud provider side from any private IP address.
- Evaluate the DNS to ensure all configurations are correct.
-
A cloud deployment engineer is modifying versions of the existing template image to instantiate new VMs. The engineer accomplishes this through the cloud self-service portal. After the version is changed and a new VM is successfully started, it does not have any connectivity, and all ping tests to other VMs fail. Which of the following would be the BEST approach to solve the problem?
- Start the console session to the VM; check network static routes; test the ping to default gateway and next hop; and reconfigure the gateway IP.
- Delete the VM; create a new flavor; turn on network service; add the new image to the template manager; and reinstantiate the VM using this new image.
- Delete the VM; check the IP assignment and planning; modify configuration in the deployment template; and instantiate the VM again using the new template.
- Assign new IPs to the newly created VMs by changing and running the deployment template; and check the connectivity on the cloud self-service portal afterward.
-
A cloud provider is evaluating an insider threat. A resource from the company operations team has access to the servers’ virtual disks. This poses a risk that someone could copy and move the virtual server image and have access to the data. Which of the following solutions would help mitigate this problem?
- Tokenization
- Encryption
- Virtual firewall
- Hashing
-
After monthly patching, a large number of users who are logged onto the network report that application links from a company’s intranet site, which previously opened directly into the website, are now prompting for logon information. Application administrators confirm that the websites in question are working properly. Which of the following is the MOST likely cause of the new behavior?
- SSO issues
- Password expiration
- Account lockout
- Certificate expiration
-
A cloud administrator is analyzing usage trends for a website housed within an IaaS cloud platform. The administrator notices that traffic and visitors to the site quadrupled from the normal baseline during the holiday season. The environment has a load balancer that uses standardized VMs to host the applications. Given this scenario, which of the following would be the MOST efficient, provide no downtime, and address the temporary spike in traffic?
- Implement an upward vertical scaling solution.
- Implement a downward vertical scaling solution.
- Implement an inward horizontal scaling solution.
- Implement an outward horizontal scaling solution.
-
A company is implementing a launchpad within an existing application that will point to an existing SaaS provider. One of the requirements is the user should not have to log on multiple times. SSO is in place. When the launchpad is used, the user is redirected to SaaS providers as designed, but is asked for login credentials. Which of the following is the MOST likely cause of this issue?
- Users do not exist within the SaaS provider.
- Group permissions are incorrect.
- Users do not exist in directory services.
- The federation is failing.
-
A cloud service administrator is consuming PaaS services and is performing baseline configuration tests. Which of the following is part of the PaaS consumer’s responsibility with respect to the baseline confirmation tests?
- Application versions
- CPU utilization
- RAM utilization
- Operating system versions
-
An engineer is configuring the monitoring for a new application server. During the day, the CPU on the server is baselined at approximately 30% utilization. At midnight, a batch job is scheduled to run that will drive the CPU utilization up to 75% for approximately an hour. Any time the CPU utilization is at 40% or higher for longer than ten minutes, administrators will receive an alert. Which of the following is the BEST method to ensure administrators do not experience message fatigue due to false alerts?
- Set a different threshold during the batch peak time.
- Increase the alert time threshold to 65 minutes.
- Increase the alert utilization threshold to 80%.
- Manually disable monitoring during the batch job.
-
A cloud administrator configures a new web server for the site https://companyname.com. The administrator installs a wildcard SSL certificate for *.companyname.com. When users attempt to access the site, a certificate error is received. Which of the following is the MOST likely cause of the error?
- Certificate misconfigured
- Certificate expired
- Certificate revoked
- Certificate not signed
-
A cloud service company is proposing a solution to a major sporting venue. The solution offers 99.999% availability during special events, which is proven through specialized testing. Which of the following techniques should be applied to confirm the high availability claimed by the company? (Select TWO.)
- Vulnerability testing
- Penetration testing
- Load testing
- Failover testing
- Integration testing
-
An organization is replacing its internal human resources system with a SaaS-based application. The solution is multi-tenant, and the organization wants to ensure ubiquitous access while preventing password replay attacks. Which of the following would BEST help to mitigate the risk?
- Implement destination resources authentication.
- Require and implement two-factor authentication.
- Remove administrator privileges from users’ laptops.
- Combine network authentication and physical security in one card/token.
Subscribe
0 Comments
Newest